DevSecOps - Kubernetes DevOps & Security
DevOps Pipeline
Demo Jenkins Pipeline Checking Versions
In this guide, you’ll create a Jenkins Pipeline named checking-versions to verify that Jenkins can execute Git, Maven, Docker, and Kubernetes commands. This helps catch any environment issues before running your CI/CD workflows.
Table of Contents
- Prerequisites
- Create the Pipeline
- Inspect the Build Results
- Configure Kubernetes CLI Plugin
- Add the Kubeconfig Credential
- Update Pipeline with Kubeconfig
- Verify Success
- References & Links
Prerequisites
- Jenkins (v2.x or later) with Pipeline plugin
- Agents that have Git, Maven, Docker, and
kubectlinstalled - Admin access to Jenkins for managing credentials
Create the Pipeline
- In Jenkins, click New Item.
- Enter checking-versions as the name.
- Select Pipeline and click OK.
Scroll to the Pipeline section and replace the script with:
pipeline {
agent any
stages {
stage('Git Version') {
steps {
sh 'git --version'
}
}
stage('Maven Version') {
steps {
sh 'mvn -v'
}
}
stage('Docker Version') {
steps {
sh 'docker -v'
}
}
stage('Kubernetes Version') {
steps {
sh 'kubectl version --short'
}
}
}
}
Save and click Build Now.
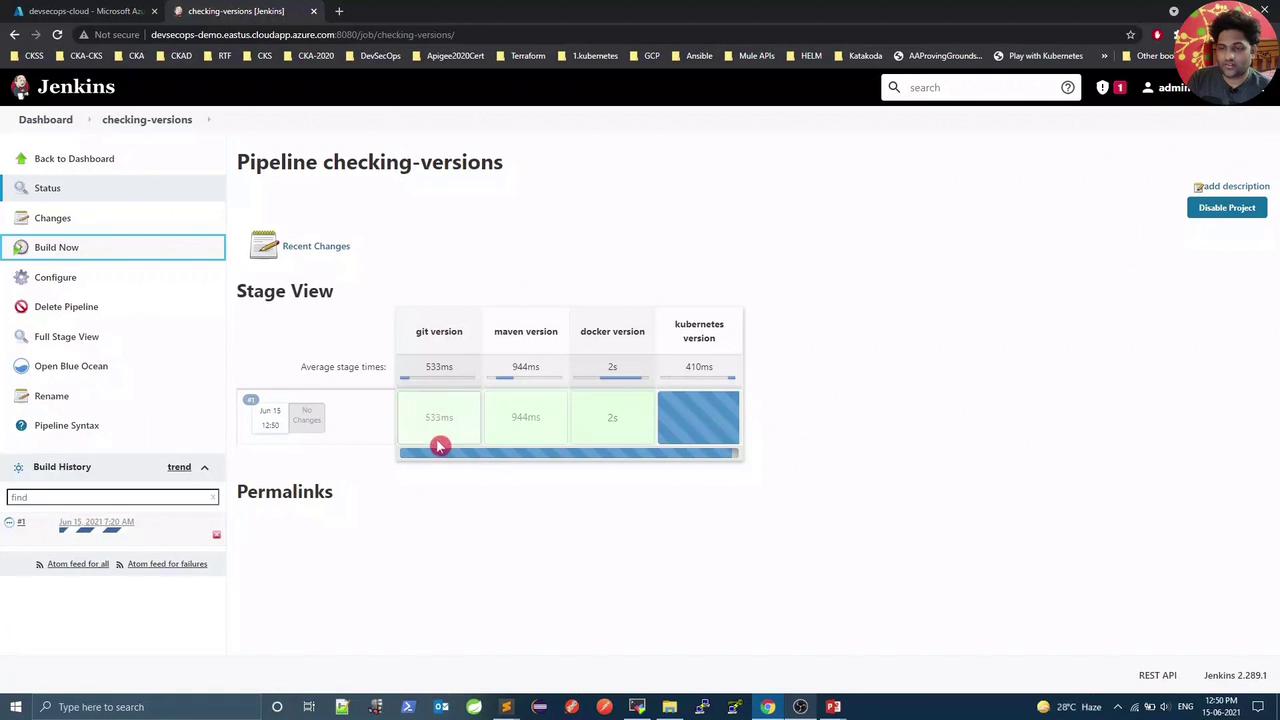
Inspect the Build Results
Once the job runs, the Pipeline view will display four stages. The first three should pass, but the Kubernetes stage may fail due to missing cluster credentials:
Open the console output:
[Pipeline] stage
[Pipeline] { (Git Version)
[Pipeline] sh
+ git --version
git version 2.17.1
[Pipeline] }
...
[Pipeline] stage
[Pipeline] { (Kubernetes Version)
+ kubectl version --short
Client Version: v1.21.0
Error from server (Forbidden): <html>…authentication required…
Note
The Kubernetes CLI ran locally but failed to authenticate with the API server.
Configure Kubernetes CLI Plugin
To inject a kubeconfig into your build, install and use the Kubernetes CLI Plugin.
Scripted Pipeline example:
node {
stage('List Pods') {
withKubeConfig([credentialsId: 'user1', serverUrl: 'https://api.k8s.my-company.com']) {
sh 'kubectl get pods'
}
}
}
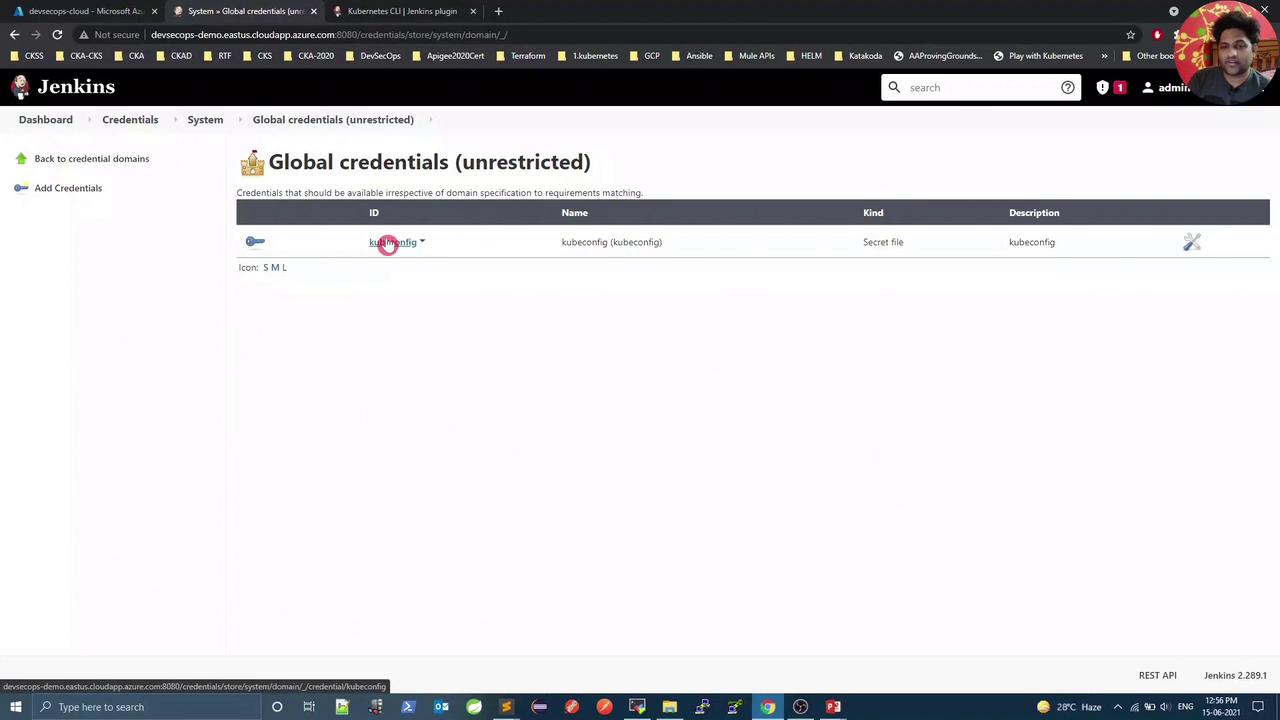
Add the Kubeconfig Credential
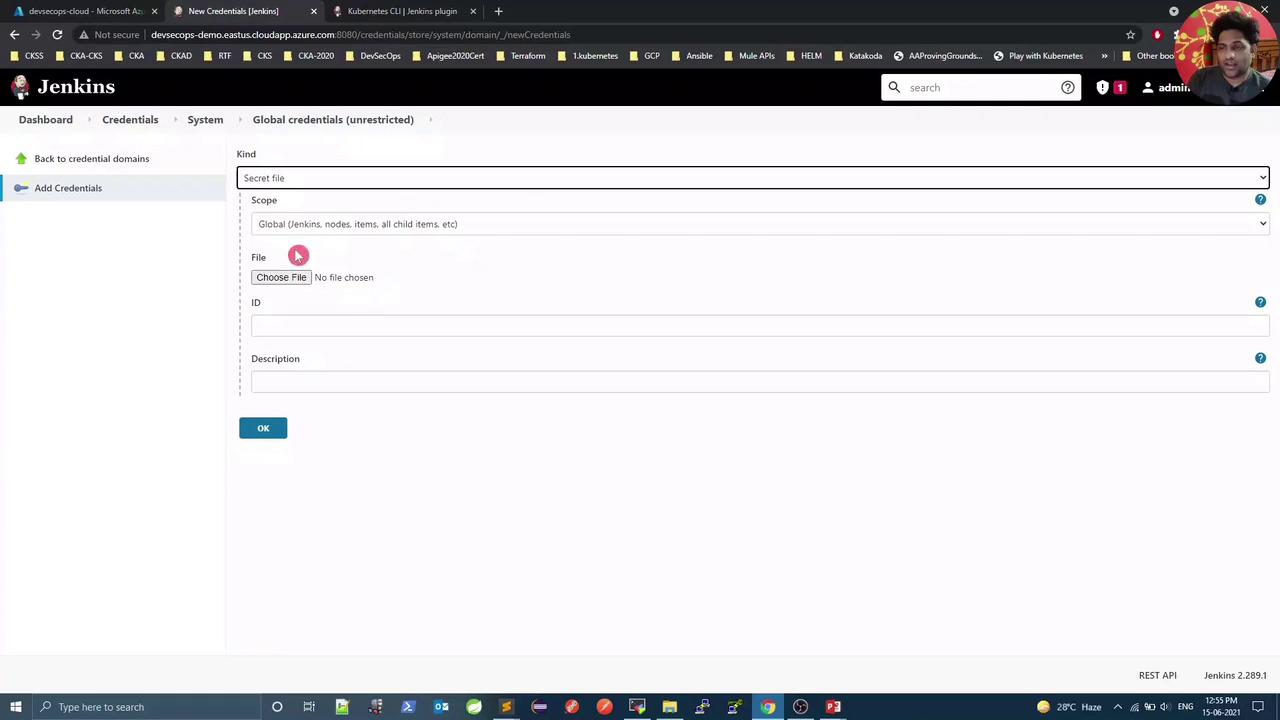
- Go to Manage Jenkins → Manage Credentials.
- Under Global, click Add Credentials.
- For Kind, select Secret file and upload your local
kubeconfig. - Set ID to
kubeconfig, add a description, then OK.
Confirm the credential appears in the list:
Update Pipeline with Kubeconfig
Edit the checking-versions Pipeline script. Wrap the Kubernetes stage with withKubeConfig:
pipeline {
agent any
stages {
stage('Git Version') {
steps { sh 'git --version' }
}
stage('Maven Version') {
steps { sh 'mvn -v' }
}
stage('Docker Version') {
steps { sh 'docker -v' }
}
stage('Kubernetes Version') {
steps {
withKubeConfig([credentialsId: 'kubeconfig']) {
sh 'kubectl version --short'
}
}
}
}
}
Save and Build Now again.
Verify Success
Now all four stages—including both Kubernetes client and server checks—should pass:
+ kubectl version --short
Client Version: v1.21.0
Server Version: v1.21.0
Warning
For production, avoid using a cluster-admin kubeconfig. Instead, create a ServiceAccount with minimal RBAC permissions for Jenkins.
References & Links
Watch Video
Watch video content
Practice Lab
Practice lab