- Basic experience with Jenkins, Linux, shell scripting, and DevOps workflows
- Familiarity with Kubernetes and Docker
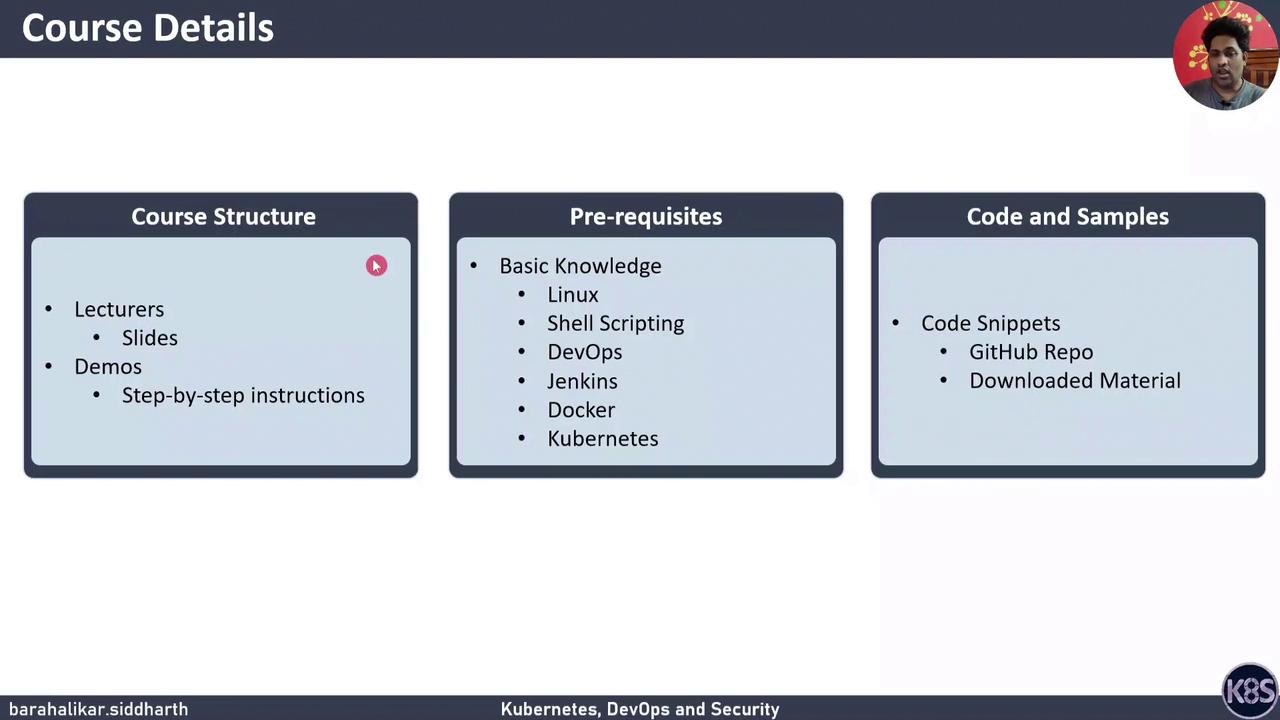
You should already have:
- A working shell environment
- A Docker installation
- Access to a Kubernetes cluster or the ability to provision one
Course Objectives
We’ve structured this course into four focused sections. Each section begins with an animated slide overview, followed by hands-on demonstrations you can follow at your own pace.| Section | Focus | Key Deliverables |
|---|---|---|
| 1 | Introduction to DevSecOps | Definition, SDLC integration, tools overview |
| 2 | Environment Setup & Pipelines | Cloud environment, tool installs, basic CI/CD |
| 3 | Building a DevSecOps Pipeline | Security checks, notifications, pipeline expansion |
| 4 | Advanced Kubernetes Security | Policy enforcement, monitoring, service mesh |
Section 1: Introduction to DevSecOps
In this section, we’ll define DevSecOps, explore its role in modern software delivery, and review the core tools and concepts used throughout the course.Section 2: Environment Setup and Simple DevOps Pipeline
We’ll set up your development environment in the cloud, install the necessary tools, deploy a Kubernetes cluster, and create a basic CI/CD pipeline using Jenkins.Section 3: Building a DevSecOps Pipeline
You’ll learn how to incorporate security checks and notifications into your workflow and extend the pipeline to handle more comprehensive automation.Section 4: Advanced Kubernetes Security
In the final section, we’ll cover advanced topics such as promoting workloads through different environments with enforced policies, monitoring and threat detection, and securing service-to-service communication with a service mesh.Next Steps and Additional Content
Future updates will introduce more advanced topics like runtime security and policy enforcement. Each chapter includes:- An animated slide overview
- Live demonstration lectures
- Hands-on exercises