
WebAssembly Security Features
Below is a quick overview of core WASM protections enforced by modern browsers:| Feature | Description | Browser Enforced |
|---|---|---|
| Sandbox & File System Limits | Modules run in a restricted environment with no direct access to the host file system. | Yes |
| Same-Origin Policy | Prevents cross-origin requests unless explicitly permitted by CORS or other headers. | Yes (MDN Docs) |
| Linear Memory Model | Each module has a contiguous memory block; out-of-bounds access is trapped automatically. | Yes (MDN Docs) |
| Digital Signatures | Optional code signing enables integrity checks before execution. | Depends on runtime |
Sandbox & File System Restrictions
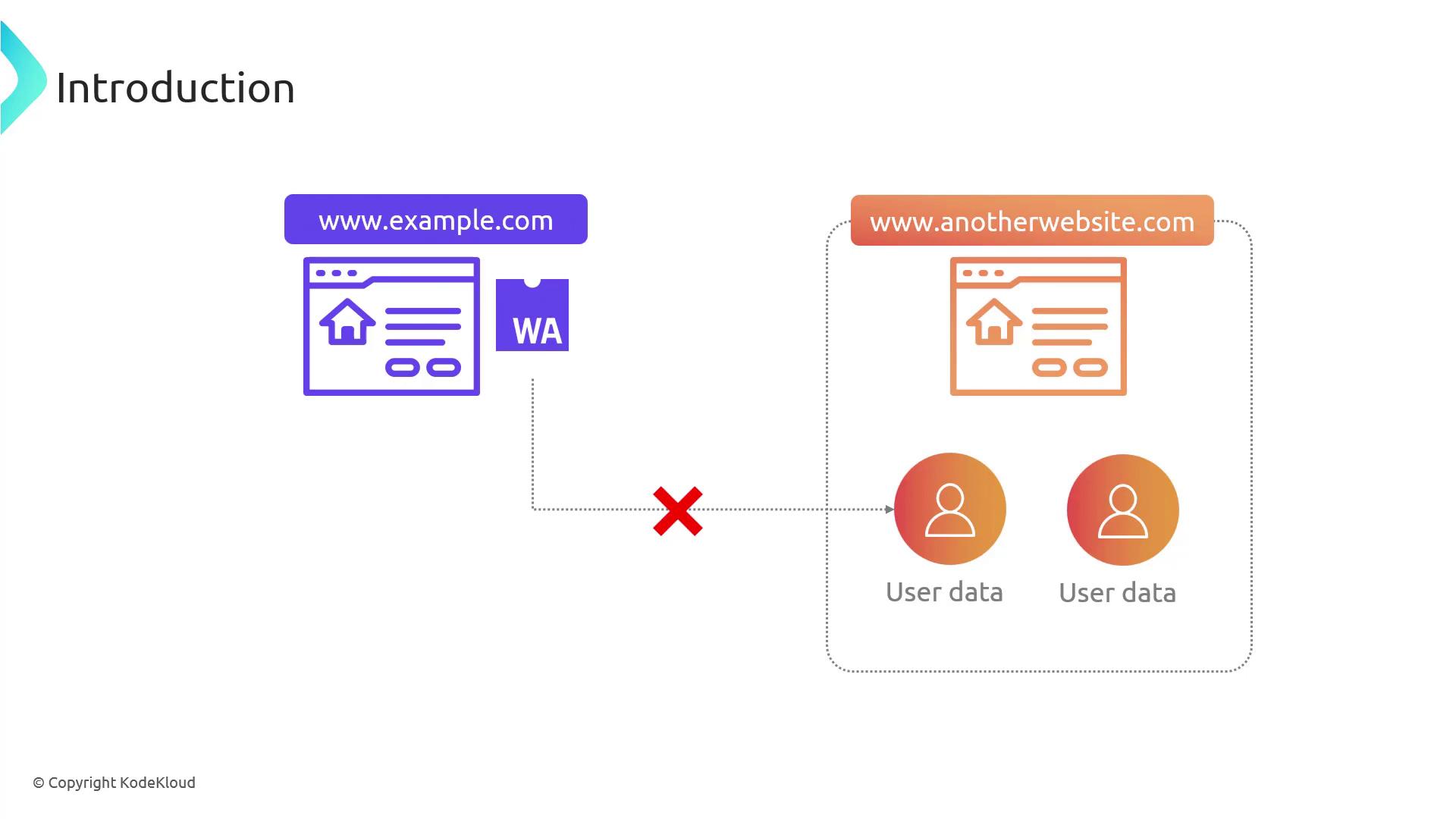
WASM modules cannot read or write host files directly:Same-Origin Policy Enforcement
A WASM module loaded fromexample.com cannot fetch data from anotherwebsite.com without proper CORS headers. This prevents unauthorized cross-site data leaks.
Linear Memory Model
WebAssembly’s memory is a single, contiguous array of bytes. Any attempt to access outside its allocated bounds is immediately trapped, mitigating buffer overflow exploits:Digital Signatures
To guarantee integrity, sign your.wasm artifacts and verify them at load time. A mismatched signature stops execution:

Best Practices for Secure WASM Coding
Beyond inherent sandboxing, follow these guidelines to further strengthen your modules:1. Validate Inputs
Ensure every external input adheres to expected types and ranges:Invalid or unchecked inputs often lead to overflows or unexpected behavior. Always validate early and fail fast.
2. Safe Memory Management
When allocating and manipulating memory, explicitly check boundaries and free resources when finished:3. Constant-Time Operations
Avoid leaking sensitive data via timing variations:4. Use Typed Arrays
Typed arrays enforce strict data layouts and reduce overflow risks:5. Restrict Imports
Only import required functions from vetted, trusted modules:6. Avoid Direct System Calls
Leverage mature libraries instead of crafting raw OS interfaces.Direct syscalls can introduce subtle memory and permission bugs. Prefer high-quality, well-audited libraries.