Default Consul Ports
Consul exposes several ports by default. Ensure that clients and applications can reach these ports on every node:| Interface | Protocol | Port | Purpose |
|---|---|---|---|
| HTTP API | TCP | 8500 | RESTful HTTP API |
| LAN gossip | TCP/UDP | 8301 | Cluster membership and gossip |
| DNS interface | TCP/UDP | 8600 | Service discovery via DNS |
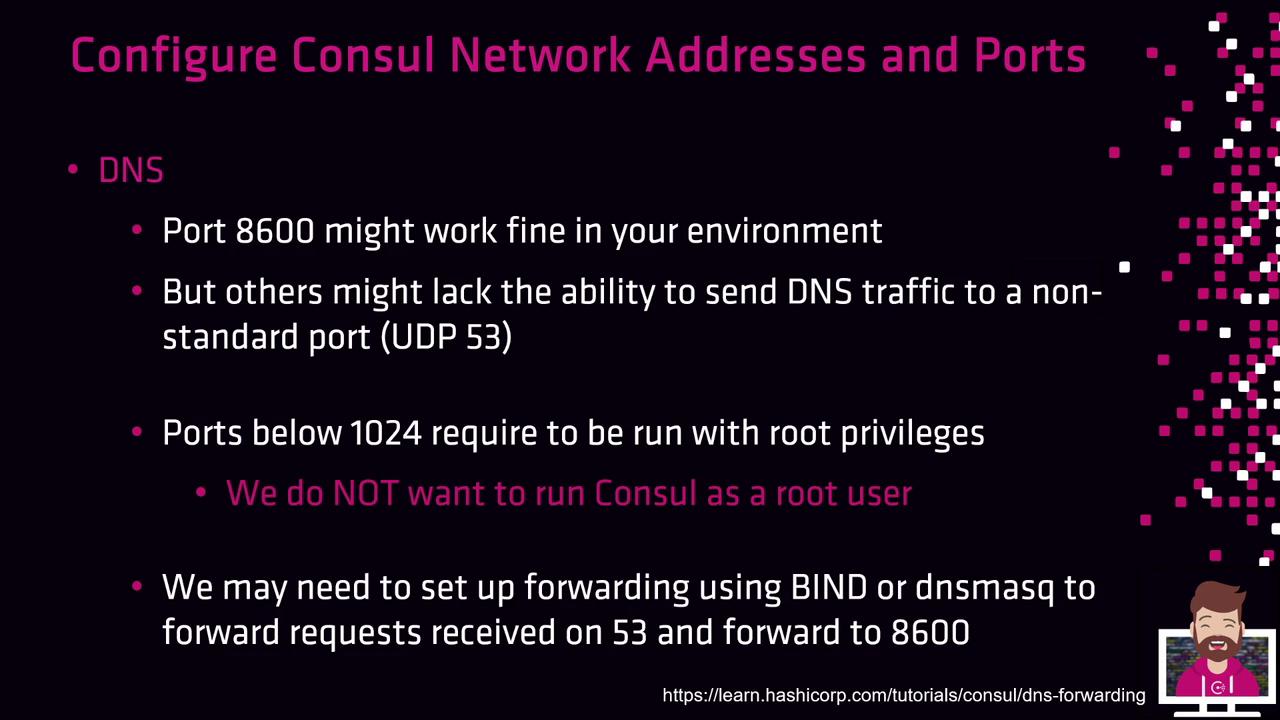
DNS Port Considerations
By default, Consul listens on port 8600 for DNS queries. In environments where DNS is restricted to UDP/TCP port 53, it’s better to redirect traffic rather than run Consul as root.Binding to ports below 1024 requires root privileges. Instead, redirect DNS requests with
iptables, firewalld, or dnsmasq to maintain security.Redirecting DNS Traffic with iptables
bind_addr vs. advertise_addr
Consul uses two key settings for network configuration:- bind_addr: The local network interface on which Consul listens for cluster communications (gossip, RPC).
- advertise_addr: The address other agents and external clients use to reach this node.

Example: NAT Scenario
Imagine a Consul server behind NAT:- Private interface (LAN gossip/RPC):
10.0.4.56 - Public (NAT) address:
10.0.9.32
config.hcl like this:
- The agent listens on
10.0.4.56for internal cluster traffic. - Other agents and clients connect to
10.0.9.32.