HashiCorp Certified: Vault Associate Certification
Compare Authentication Methods
Differentiate Human vs
Understanding the distinction between human-based and system-based authentication methods in Vault helps you choose the right approach for users, administrators, and applications. Vault supports a wide range of auth methods—some designed for interactive logins, others optimized for machine-to-machine workflows.
Human-Based Authentication Methods
Human-based methods rely on interactive flows and integrate with identity providers (IdPs) for seamless user login. These are ideal for administrators, operators, and any scenario where a person needs to initiate and control the session.
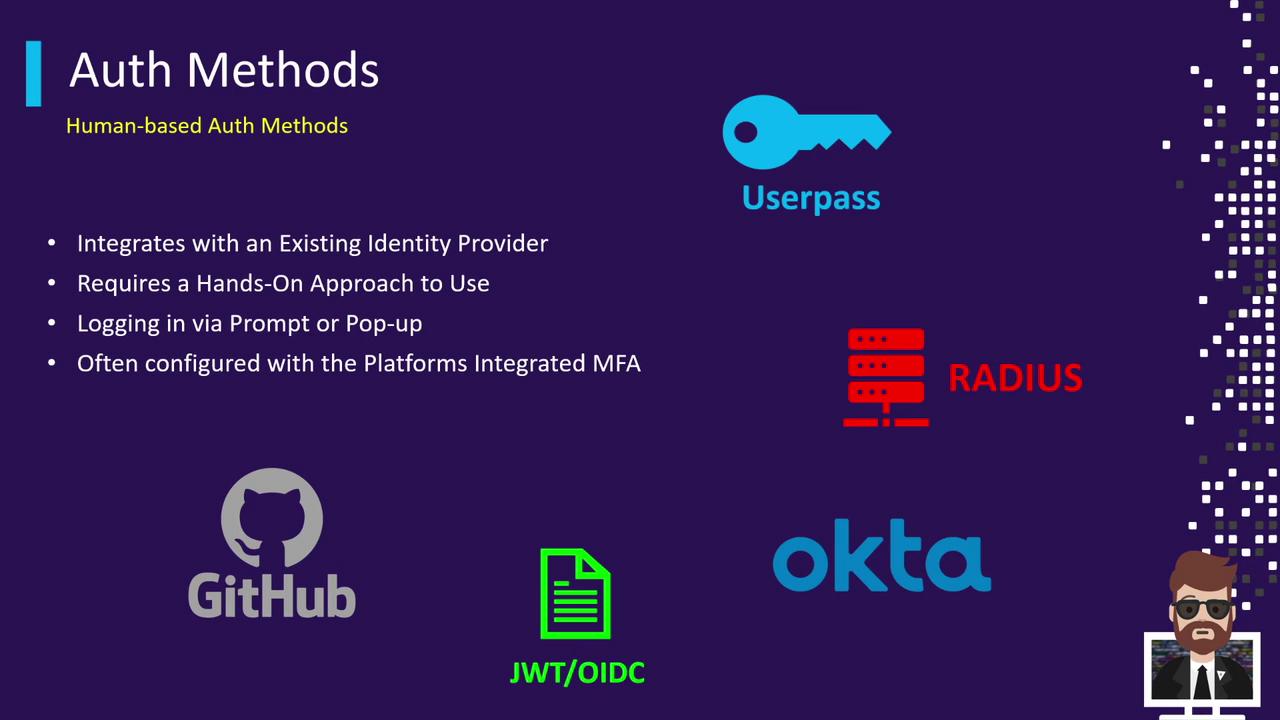
- Login via browser or CLI:
vault login -method=userpass username=alice - Supported methods:
- Userpass
- RADIUS
- GitHub
- JWT/OIDC
- Okta
- Features:
- Multi-factor authentication (MFA)
- Custom policies per user or group
- Session tokens scoped to user identity
Note
OIDC flows typically redirect you to your IdP (e.g., Azure AD, PingFederate) to authenticate and then return a JWT to Vault.
System-Based Authentication Methods
System-based methods are non-interactive and tailored for workloads needing to authenticate without human intervention. These methods verify platform-specific metadata or credentials and issue tokens for applications and services.

- Typical credentials:
- TLS certificates
- Cloud platform metadata
- Service account tokens
- Common integrations:
- AWS IAM (
vault login -method=aws) - Azure Managed Identity
- GCP Service Account
- Kubernetes ServiceAccount
- Kerberos, Cloud Foundry, Oracle Cloud, Alibaba Cloud
- AWS IAM (
vault login -method=aws role=my-role \
header_value=$(curl http://169.254.169.254/latest/meta-data/instance-id)
Warning
Ensure your IAM roles, service accounts, and instance profiles have least-privilege policies. Overly broad permissions increase security risks.
Summary Table
| Authentication Type | Intended For | Examples |
|---|---|---|
| Human-Based | Admins, Operators (interactive) | userpass, GitHub, Okta |
| System-Based | Applications, Services (non-interactive) | AWS, Azure, GCP, Kubernetes |
Best Practices
- Use human-based methods for personnel who need direct control and MFA.
- Use system-based methods for services, CI/CD pipelines, and microservices.
- Regularly rotate credentials and review policies to maintain least privilege.
Links and References
Watch Video
Watch video content