HashiCorp Certified: Vault Associate Certification
Introduction to Vault
Benefits and Use Cases of Vault
HashiCorp Vault is a unified secrets management solution designed to secure, store, and tightly control access to tokens, passwords, certificates, encryption keys, and other sensitive resources. Organizations adopt Vault to:
| Benefit | Description |
|---|---|
| Consolidate static credentials | Store long-lived secrets (service accounts, API keys) centrally in Vault’s Key/Value engine. |
| Generate dynamic secrets | Issue short-lived, least-privileged credentials on demand and auto-revoke them after use. |
| API-driven automation | Leverage Vault’s HTTP API to integrate seamlessly with CI/CD pipelines (Jenkins, Terraform, etc.). |
| Identity-based access | Authenticate entities via trusted providers (AWS, Kubernetes) and issue scoped tokens. |
| Encryption as a service | Perform encrypt/decrypt operations via the Transit and Transform Engines. |
| Automated PKI | Programmatically generate, renew, and revoke X.509 certificates with the PKI Secrets Engine. |
Note
Vault’s unified approach replaces fragmented tools (1Password, KeePass, cloud vaults) with a single, auditable control plane.
Below we dive deeper into key Vault use cases, each backed by strong API support and enterprise-grade security policies.
Secure Data Management Use Cases
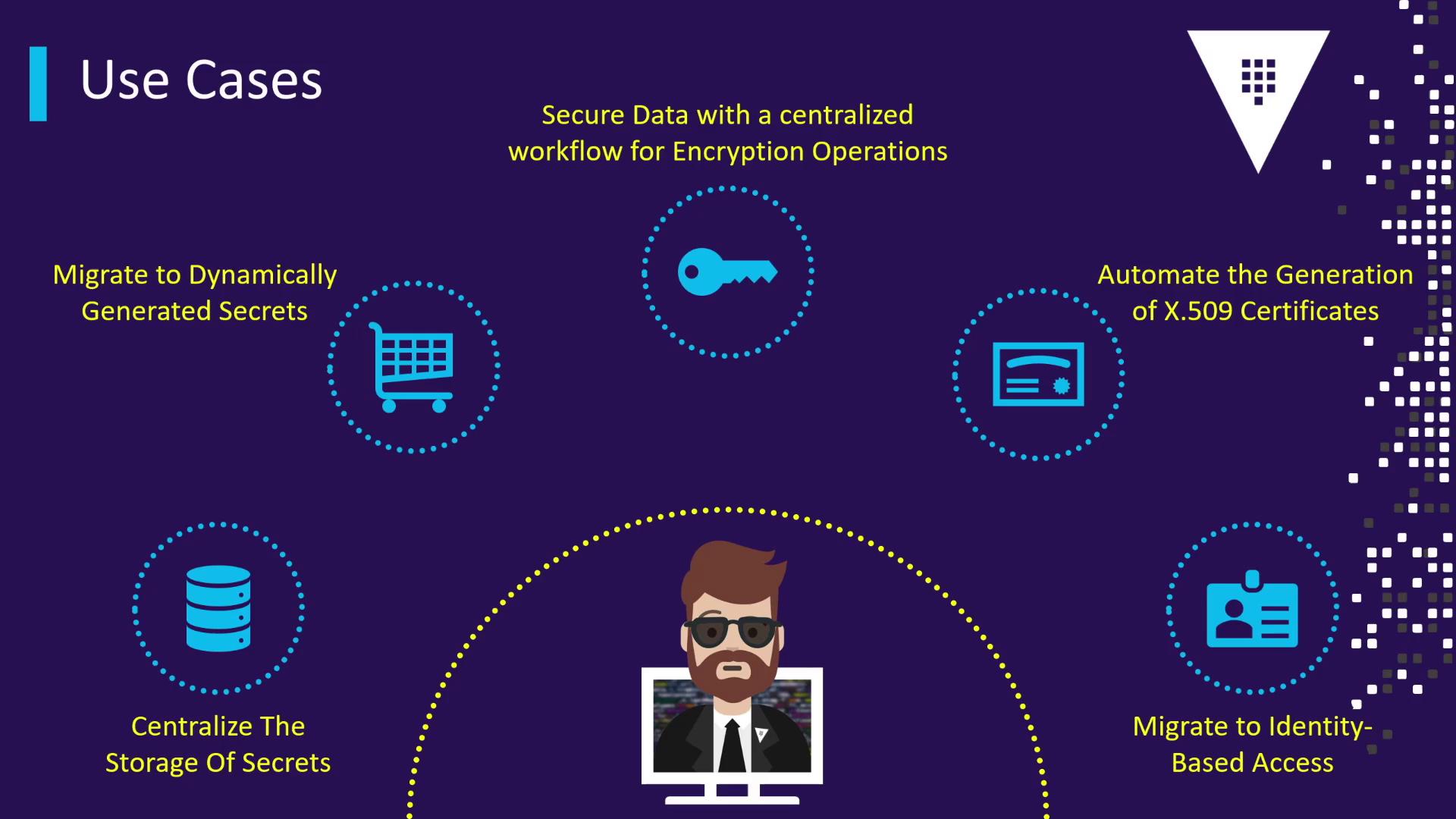
- Centralized secret storage
- Dynamic secret generation & renewal
- Encryption operations via central workflows
- Automated X.509 certificate issuance
- Identity-based access control
Note
Align these use cases with compliance standards (PCI-DSS, HIPAA, GDPR) by leveraging Vault’s audit logging and policy enforcement.
Centralizing Secret Storage
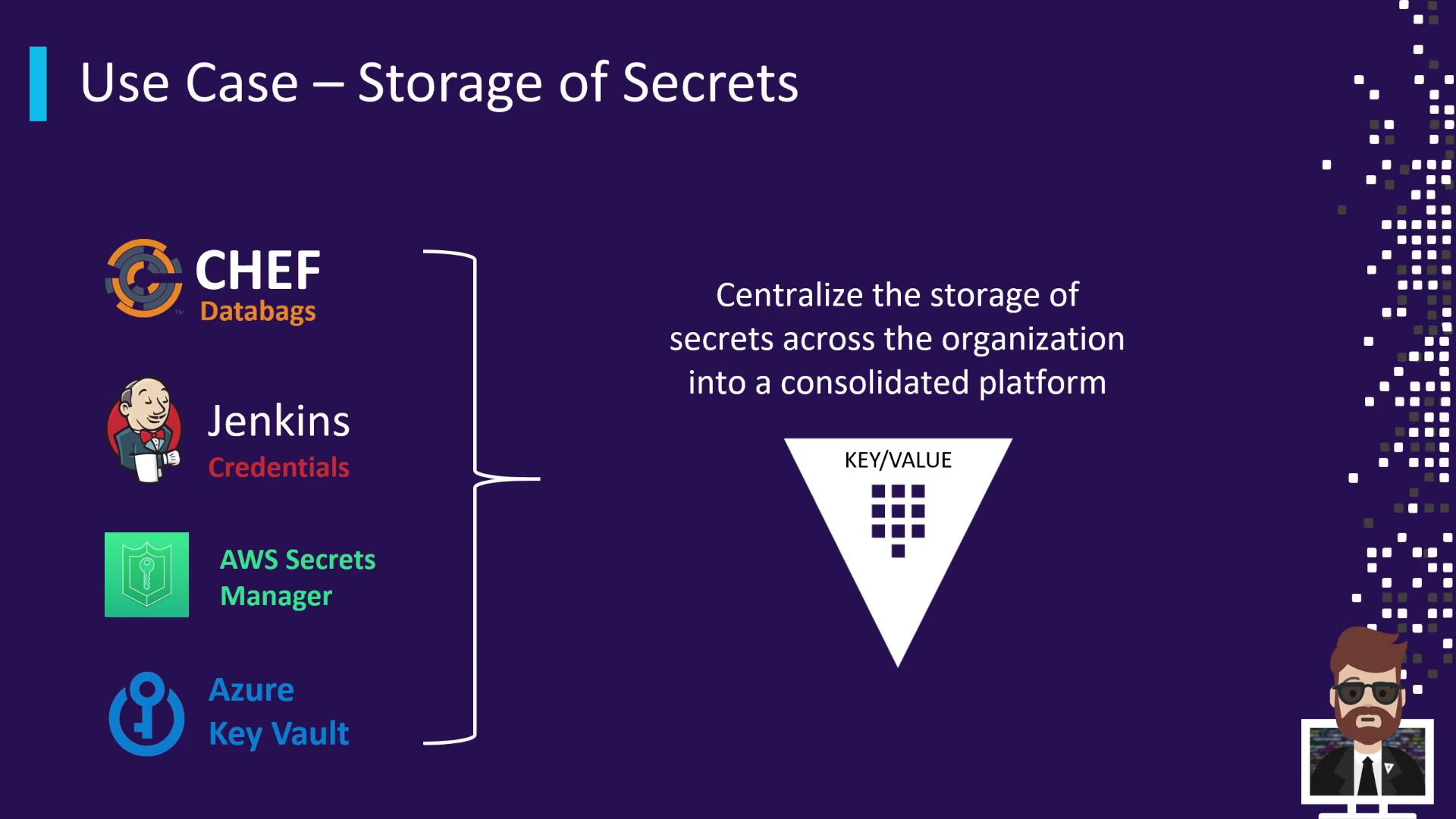
Many teams scatter secrets across Chef, Jenkins, AWS Secrets Manager, Azure Key Vault, and more. Vault’s Key/Value Secrets Engine consolidates all static credentials in a single namespace, simplifying policy management and audits.
Warning
Never commit Vault tokens or raw credentials to source control. Always retrieve secrets at runtime via the Vault API.
Migrating to Dynamic Secrets
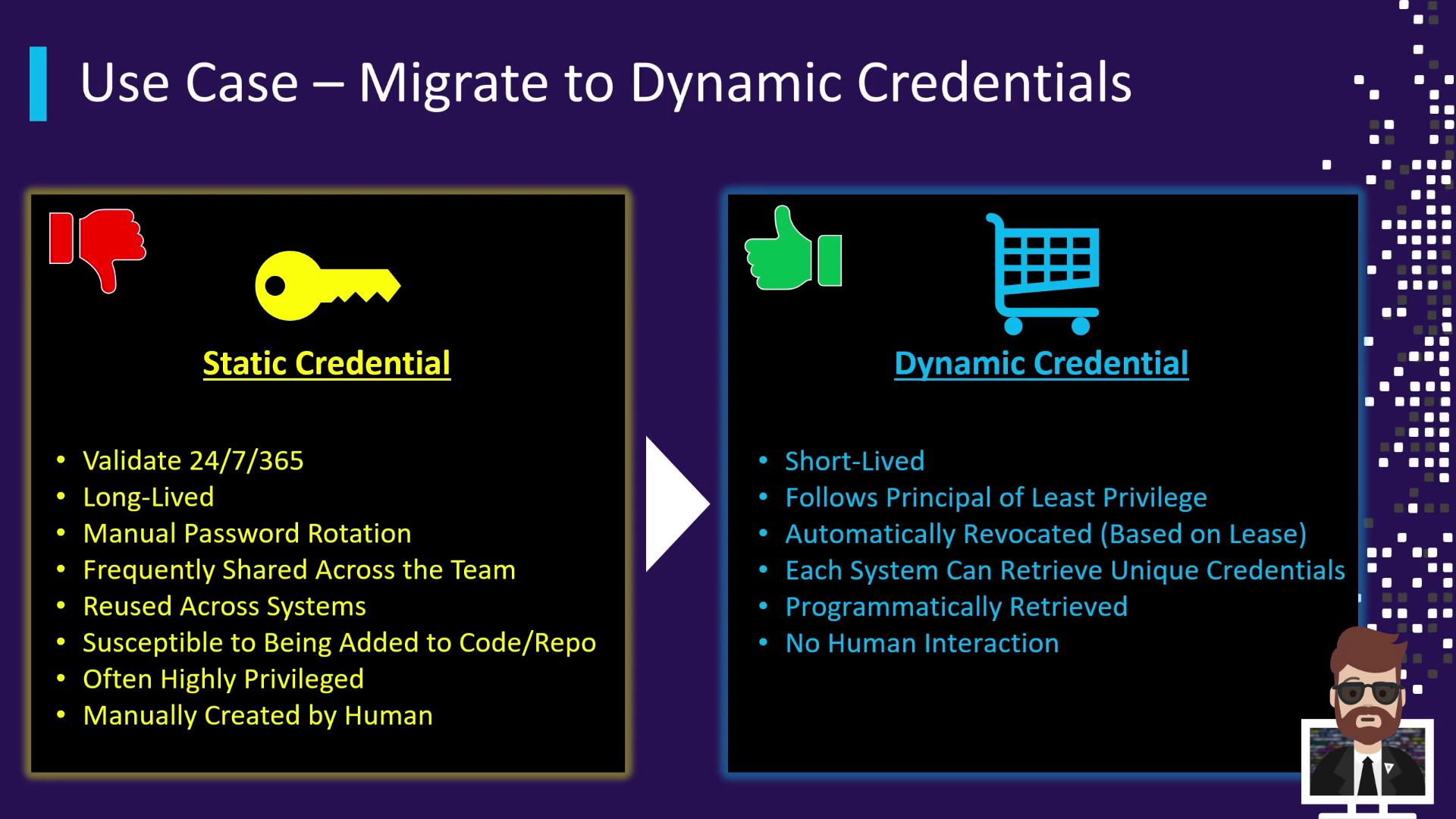
Dynamic secrets are generated on demand and have a defined lease time:
- Short-lived (e.g., 4-hour AWS credentials)
- Auto-rotated and programmatically retrieved
- Scoped by roles for least-privilege
- Auto-revoked at lease expiry
- Unique per requester
Moving from permanent credentials to dynamic secrets reduces blast radius and eliminates manual rotation tasks.
Warning
Ensure robust lease management: monitor and renew active leases to avoid service disruptions.
Encrypting Data with a Centralized Workflow
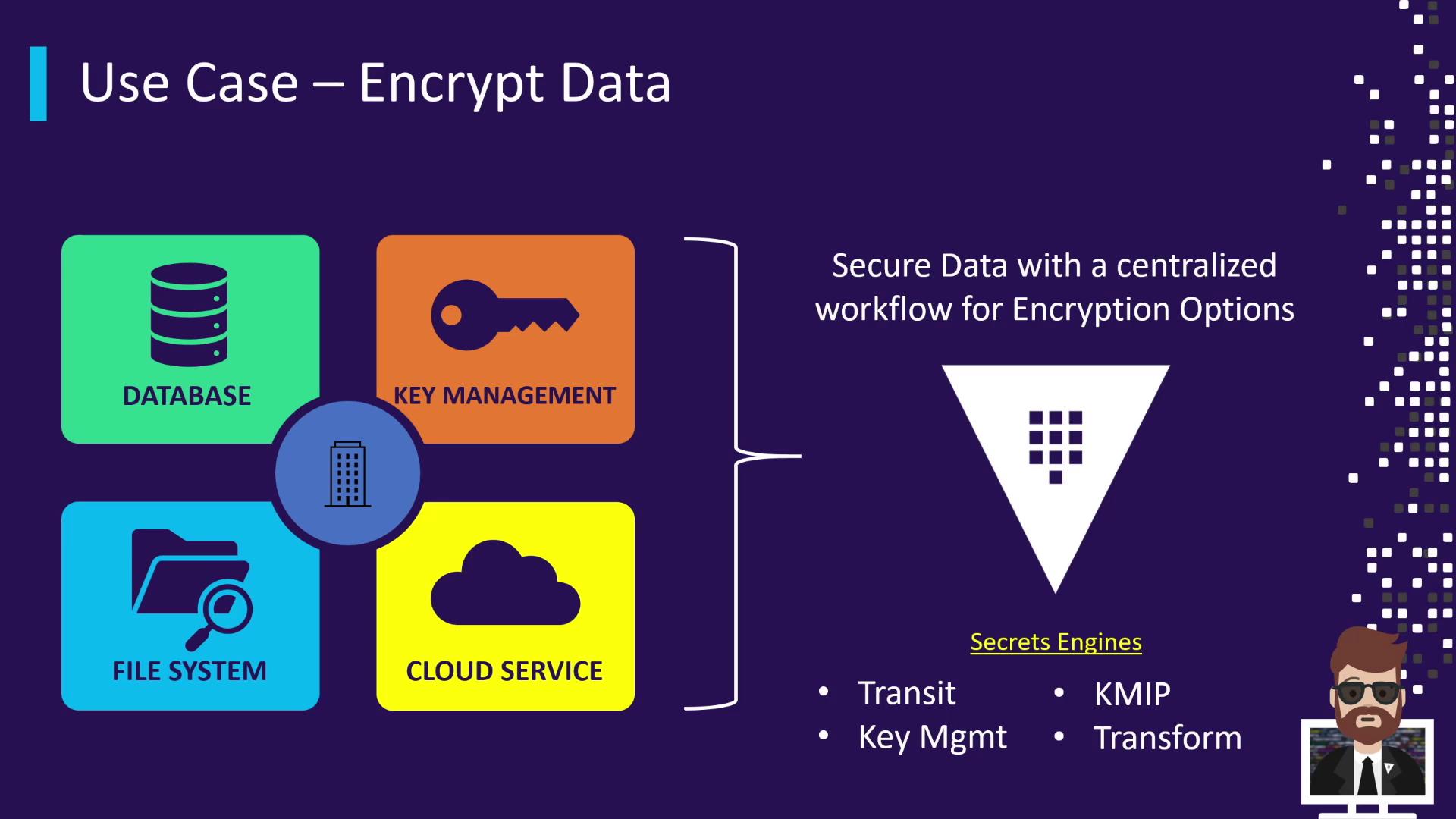
Vault’s Secrets Engines for encryption include:
| Engine | Capabilities |
|---|---|
| Transit | Encrypt/decrypt, rewrap, sign/verify via API |
| Transform | Format-preserving encryption for structured data |
| KMIP | Act as a KMIP-compliant key manager |
| KMS | Proxy cloud-native KMS (AWS, Azure, GCP) |
Route all encryption calls through Vault to decouple cryptographic logic from applications, ensure compliance, and centralize key management.
Note
The Transit Engine integrates with hardware security modules (HSMs) for FIPS-compliant encryption.
Automated X.509 Certificate Management
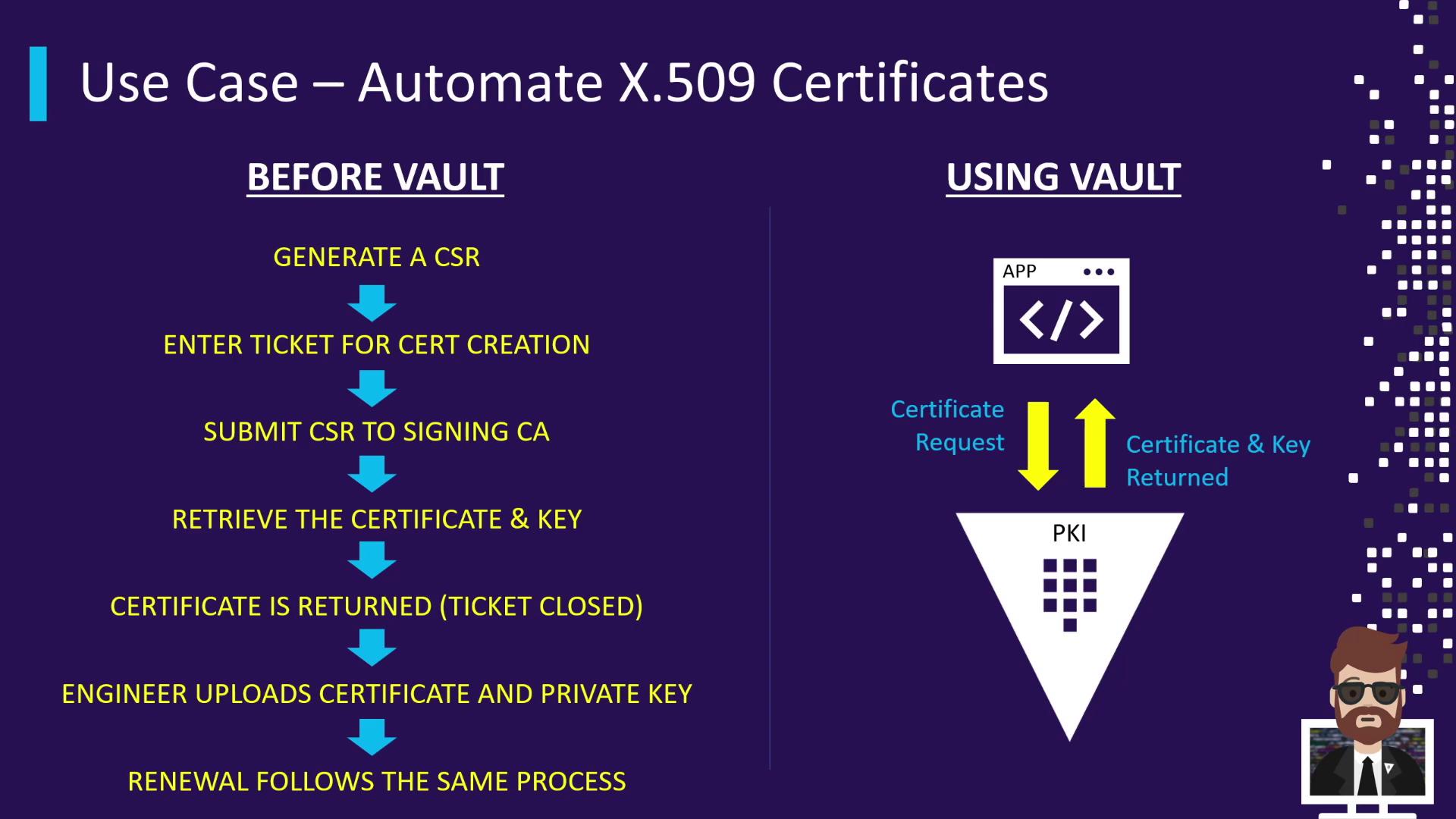
Vault’s PKI Secrets Engine offers:
- CSR submission via API
- Programmatic issuance of certificates and private keys
- Automated renewals and revocations
- No manual ticketing or key distribution
This fully automates TLS workflows and scales certificate management across microservices and edge devices.
Note
See the PKI Secrets Engine documentation for CA setup and role configuration.
Migrating to Identity-Based Access
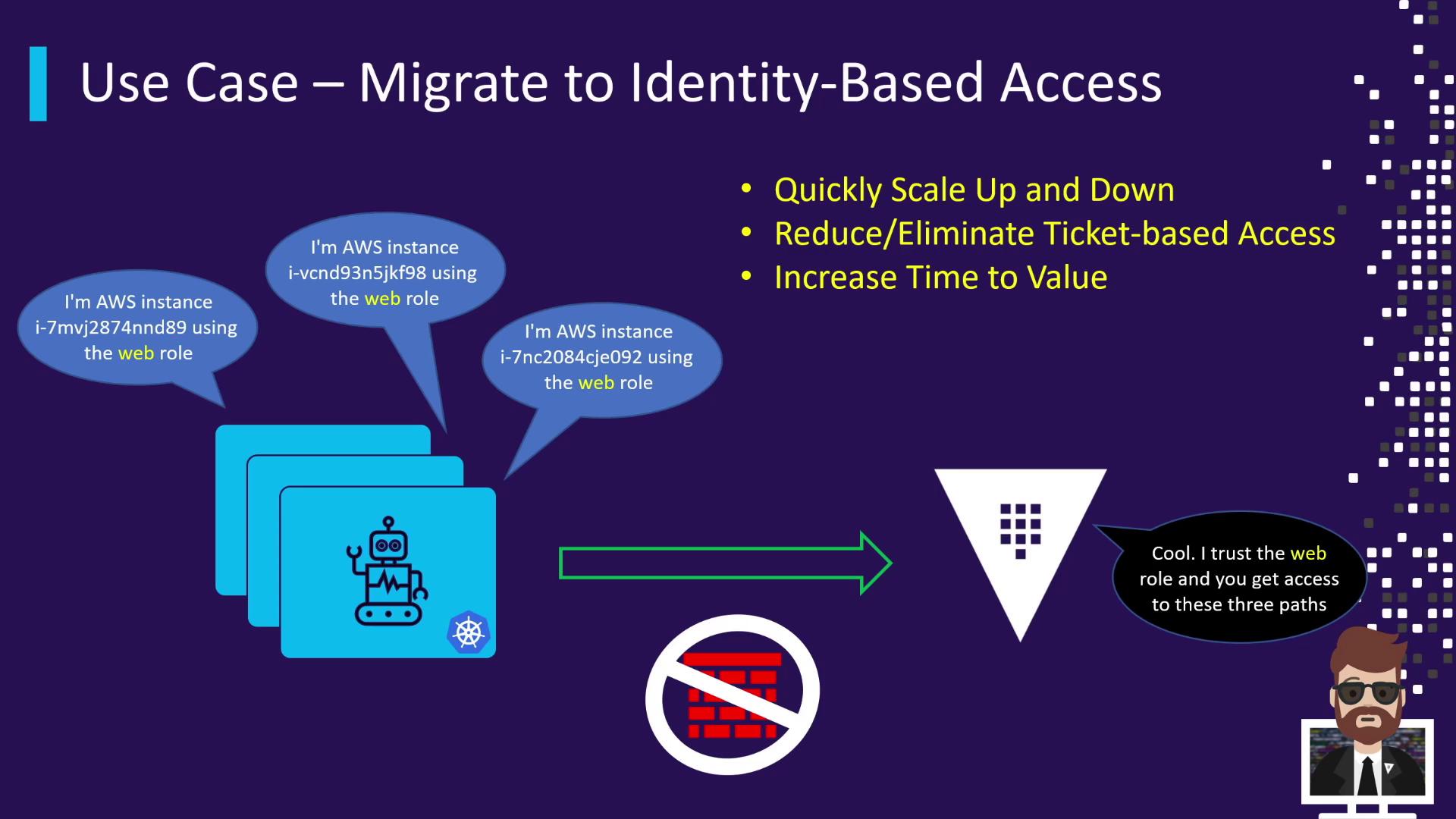
Instead of IP allow-lists or shared credentials, Vault leverages auth methods:
- AWS IAM, Kubernetes, GCP, Azure, LDAP, OIDC
- Entities present identity tokens (e.g., AWS instance metadata)
- Vault validates and issues scoped tokens
- Access is bound to specific paths and policies
This model eliminates firewall churn, automates onboarding, and secures ephemeral workloads.
Note
Review the Identity & Access methods to choose the right integration for your environment.
Links and References
- Vault Overview
- Transit Secrets Engine
- Transform Secrets Engine
- PKI Secrets Engine
- Auth Methods
- Vault GitHub Repository
Watch Video
Watch video content