HashiCorp : Terraform Cloud
Terraform Cloud Workspaces
Lab Solution Remote Execution
In this guide, we’ll convert an existing Terraform Cloud workspace (devops-aws-myapp-dev) from local to remote execution. You’ll learn how to rename variable files, configure the remote backend, authenticate, and manage runs in Terraform Cloud—all while securely handling AWS credentials.
1. Log in and Select Your Workspace
- Navigate to https://app.terraform.io/ and log in.
- Choose your organization Mastering-Terraform-Cloud.
- Under Workspaces, click devops-aws-myapp-dev.

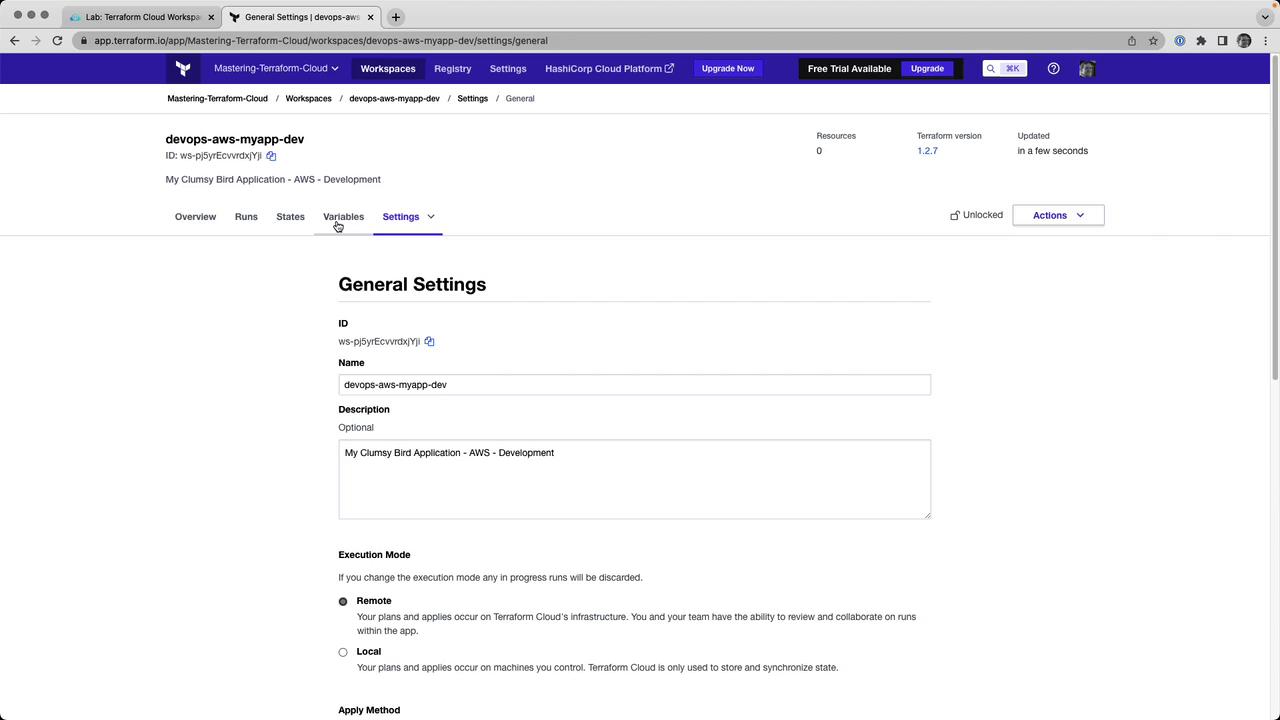
2. Enable Remote Execution
- Go to Settings → General.
- Change Execution Mode from Local to Remote.
- Click Save settings.
3. Rename Your Variables File
Terraform Cloud automatically loads any file ending in .auto.tfvars. Rename your local terraform.tfvars to:
mv terraform.tfvars terraform.auto.tfvars
Example contents of terraform.auto.tfvars:
prefix = "app"
project = "clumsy-bird"
environment = "development"
instance_type = "t2.micro"
Note
Files with the *.auto.tfvars suffix are auto-loaded by Terraform Cloud—no manual variable uploads required.
4. Configure the Remote Backend
In your Terraform configuration (e.g., backend.tf), point to your Terraform Cloud organization and workspace:
terraform {
cloud {
organization = "Mastering-Terraform-Cloud"
workspaces {
name = "devops-aws-myapp-dev"
}
}
}
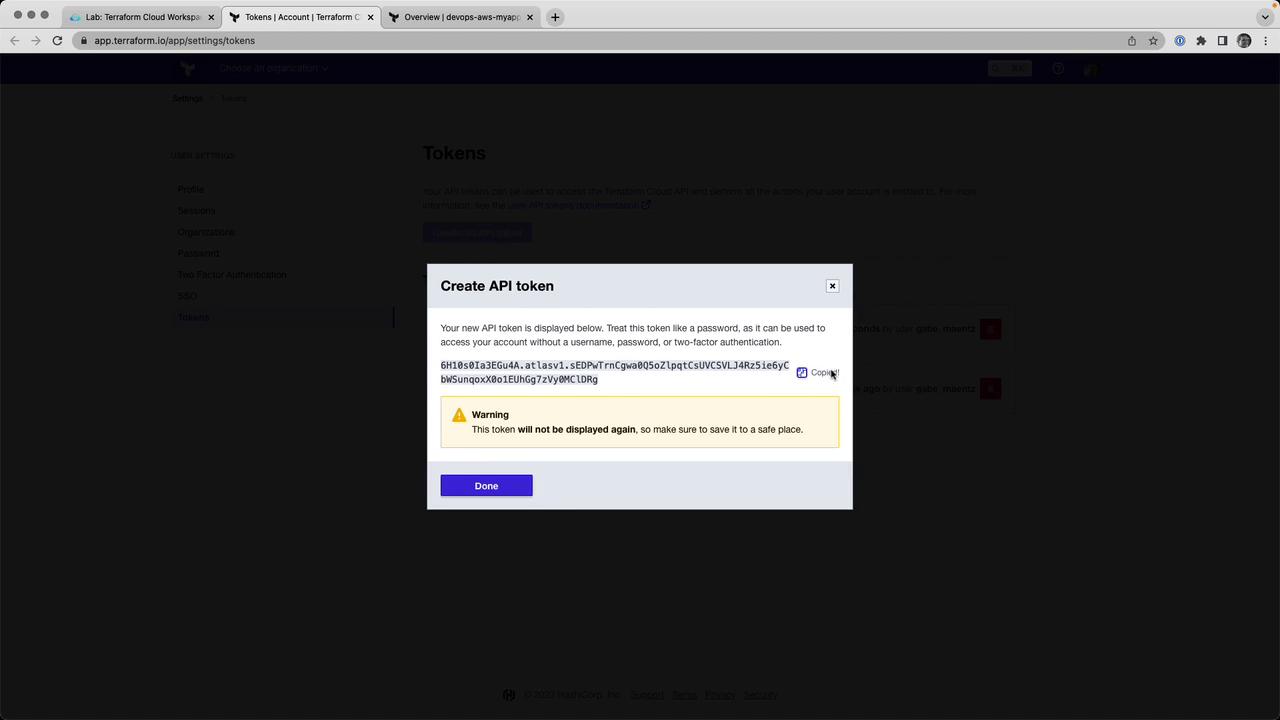
5. Authenticate with Terraform Cloud
Run the login command to link your CLI to Terraform Cloud:
terraform login
When prompted, paste your API token. Generate or copy it from User Settings → Tokens in the web UI.
6. Initialize Terraform
Initialize the backend, providers, and modules. This will register your workspace with Terraform Cloud:
terraform init
Example output:
Initializing modules...
Downloading registry.terraform.io/terraform-aws-modules/vpc/aws 3.14.4 for vpc...
...
Terraform Cloud has been successfully initialized!
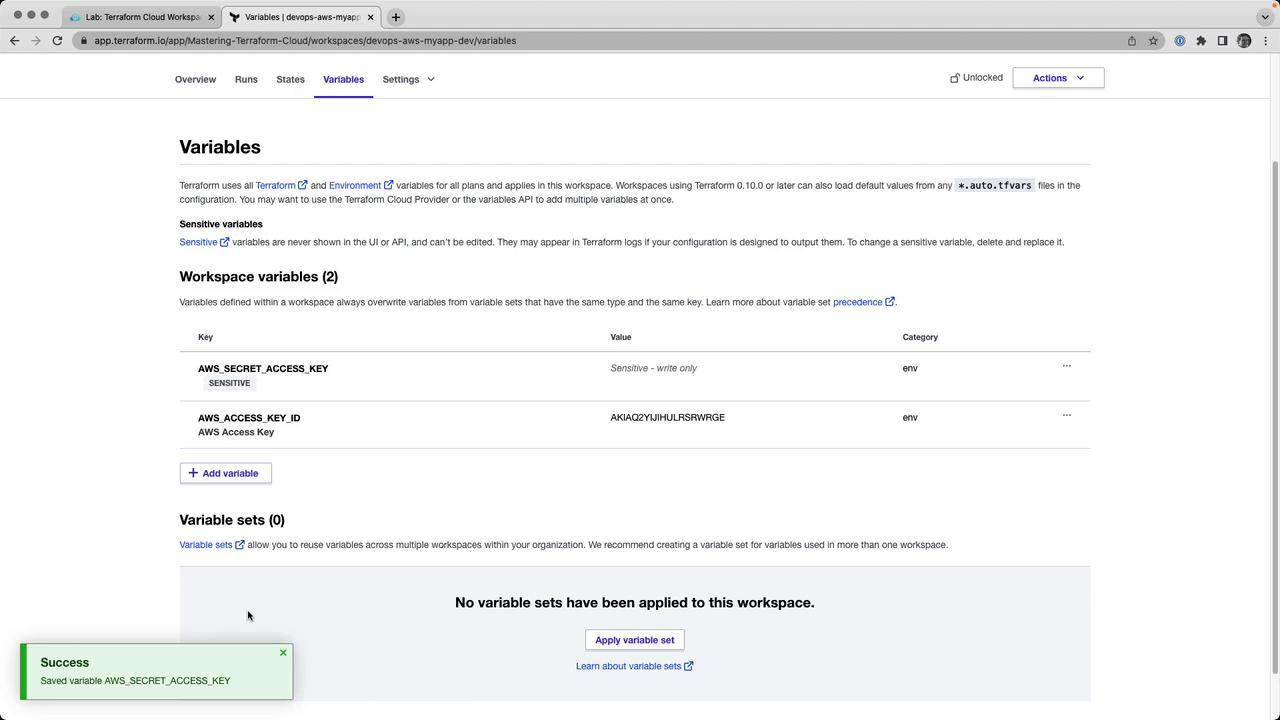
7. Set Environment Variables in the Workspace
In the Terraform Cloud UI, go to Variables and add:
| Variable Name | Category | Sensitive |
|---|---|---|
| AWS_ACCESS_KEY_ID | Environment | No |
| AWS_SECRET_ACCESS_KEY | Environment | Yes |
Warning
Mark AWS_SECRET_ACCESS_KEY as Sensitive to prevent it from being exposed in logs or state files.
8. Run a Remote Plan
From your CLI, execute:
terraform plan
The plan will run remotely in Terraform Cloud and stream logs back to your terminal:
Running plan in Terraform Cloud. Output will stream here...
Preparing the remote plan...
To view this run in a browser, visit:
https://app.terraform.io/app/Mastering-Terraform-Cloud/devops-aws-myapp-dev/runs/run-HCZ7HSw
...
You can also watch progress in the UI:

At the end, you’ll see:
Plan: 23 to add, 0 to change, 0 to destroy.
Changes to Outputs:
clumsy-bird-ip = (known after apply)
clumsy-bird-url = (known after apply)
9. Apply the Run
Approve and apply your plan:
CLI:
terraform applyType
yeswhen prompted.UI: Click Confirm & Apply in the Runs tab.
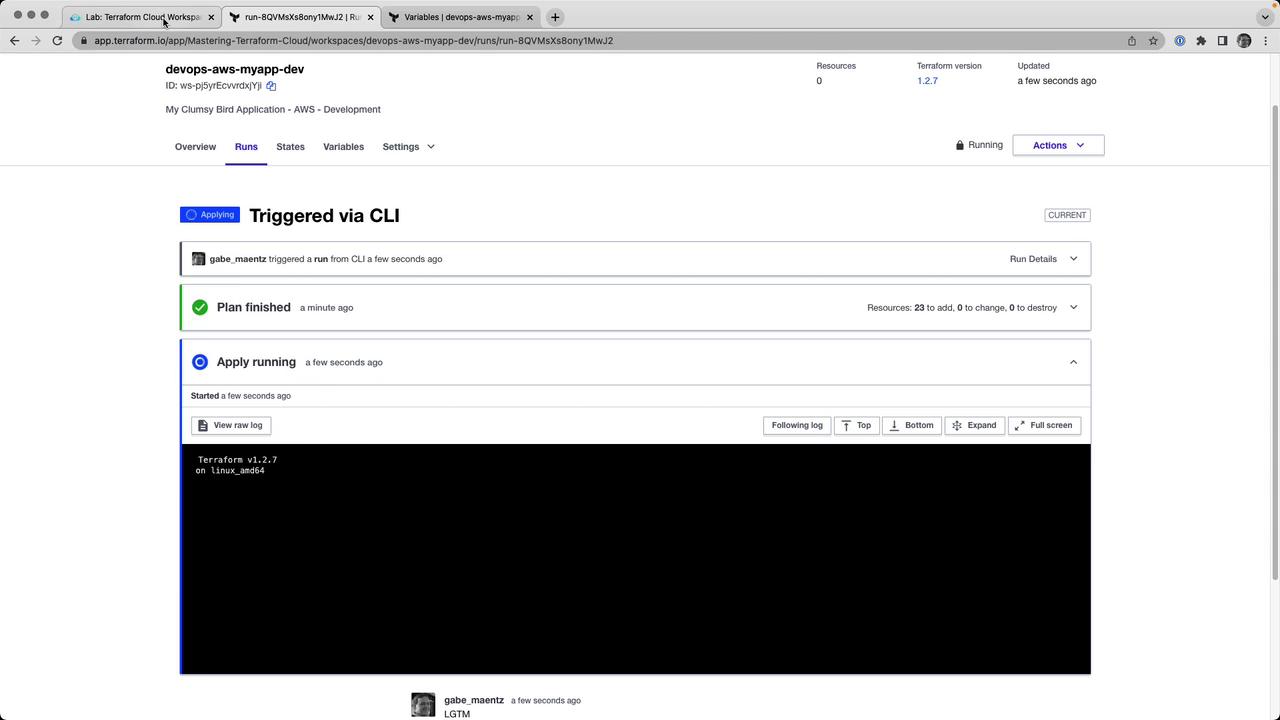
Once complete, outputs appear:
clumsy-bird-ip = "http://50.16.35.225:8001"
clumsy-bird-url = "http://ec2-50-16-35-225.compute-1.amazonaws.com:8001"
10. Inspect State Versions
Terraform Cloud automatically versions your state. Under States, you can browse previous versions or view the latest state JSON:
{
"version": 4,
"terraform_version": "1.2.7",
"serial": 2,
"outputs": {
"clumsy_bird_ip": {
"value": "http://50.16.35.225:8001",
"type": "string"
},
"clumsy_bird_url": {
"value": "http://ec2-50-16-35-225.compute-1.amazonaws.com:8001",
"type": "string"
}
},
"resources": []
}
11. Teardown (Optional)
To destroy all resources managed by this workspace:
terraform destroy
You can confirm via CLI or by clicking Confirm & Apply in the Runs tab of Terraform Cloud.
Congratulations! You’ve successfully switched your Terraform Cloud workspace to remote execution, centralized state and runs, and managed sensitive variables securely.
Links and References
- Terraform Cloud Remote Operations
- Terraform Cloud Workspaces
- Managing Variables in Terraform Cloud
- AWS CLI Documentation
Watch Video
Watch video content
Practice Lab
Practice lab