Jenkins
Exploring the Jenkins UI
Managing the system and credentials
In this guide, we explore the essential configurations within Jenkins that control system-wide settings and credentials management. By understanding these configurations, you can optimize your Jenkins environment for stability, security, and seamless integration with external systems.
Configuring the System
The "Configure System" page in Jenkins is pivotal for setting up the server’s operational parameters. Here, you define critical settings such as the home directory (e.g., /var/live/Jenkins), system messages, number of executors, labels, and usage options. These configurations determine where Jenkins is installed, its performance behavior, and how it interacts with external networks—for example, assigning a DNS name to the public IP (e.g., "Jenkins 01" or "Organization Jenkins 01").
Scrolling further down reveals additional global properties, including pipeline speed and durability settings. All overarching configurations of Jenkins are managed through these "Configure System" settings.
GitHub and Source Control Integration
Jenkins offers robust integration with GitHub and other source control systems. In the configuration, you can set up GitHub servers and tailor usage rate limiting strategies for both pull and push requests. This section also supports the integration of GitHub Enterprise servers and the management of pipeline libraries, ensuring that Jenkins communicates effectively with external repositories.
Furthermore, Jenkins allows you to configure the Git global settings, including the user email used for build notifications and other communications.
Email Notification Settings
Effective communication during build failures or pipeline errors is crucial. Jenkins can automatically dispatch email notifications when issues occur. Within these settings, you can configure SMTP servers (such as Google, Office 365, or a personal SMTP server) and specify the intended recipients. Typically, this configuration is customized per department to ensure that the right teams receive updates.
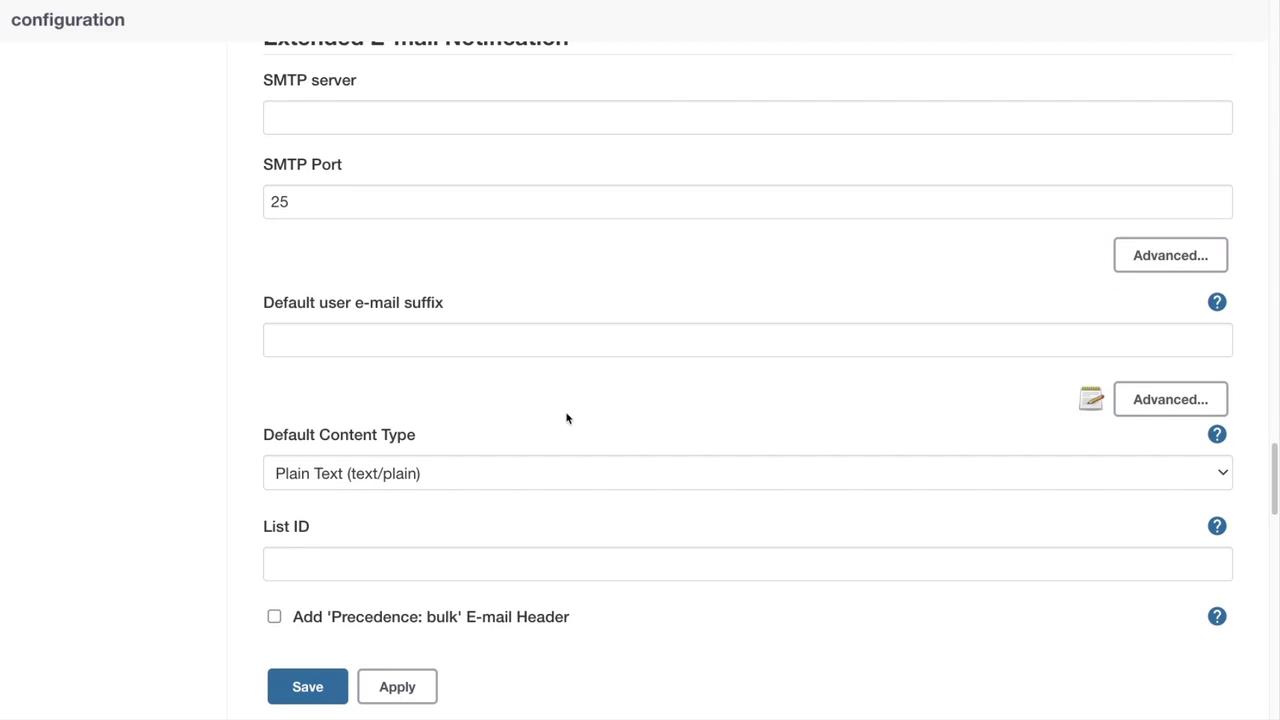
Additional options allow you to define default recipients, reply-to addresses, emergency reroutes, allowed domains, and content details. This ensures important information—like project name, build number, and build status—is always communicated effectively.
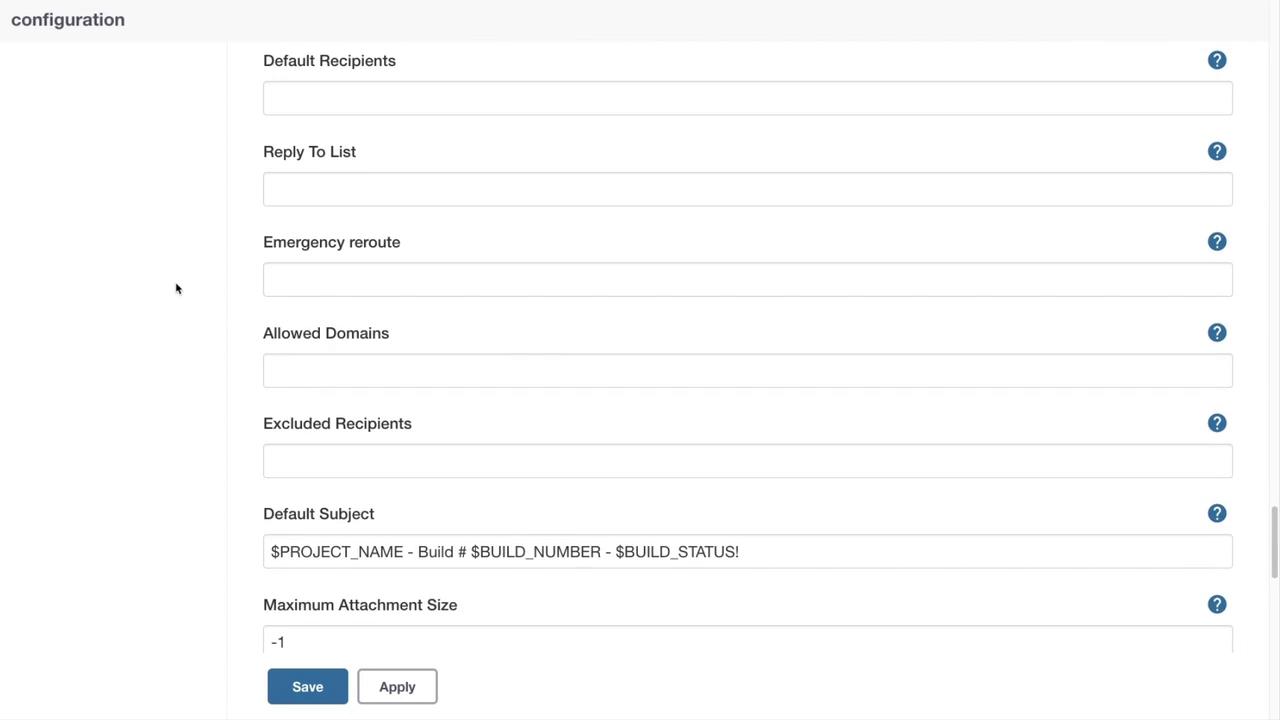
When a CI/CD pipeline runs, Jenkins uses predefined variables for notifications. For example, a typical message might appear as follows:
$PROJECT_NAME - Build # $BUILD_NUMBER - $BUILD_STATUS:
Check console output at $BUILD_URL to view the results.
Global Security Configuration
Security is paramount in any CI/CD environment. The "Configure Global Security" section in Jenkins houses settings that are critical for ensuring system integrity. This section is likely of high interest to your security team or CISO.
Security Realm
The Security Realm determines how user authentication is managed within Jenkins. Options include:
- Delegation to servlet containers
- Jenkins' built-in user database
- Integration with LDAP or Unix user and group databases
- Disabling authentication (not recommended)
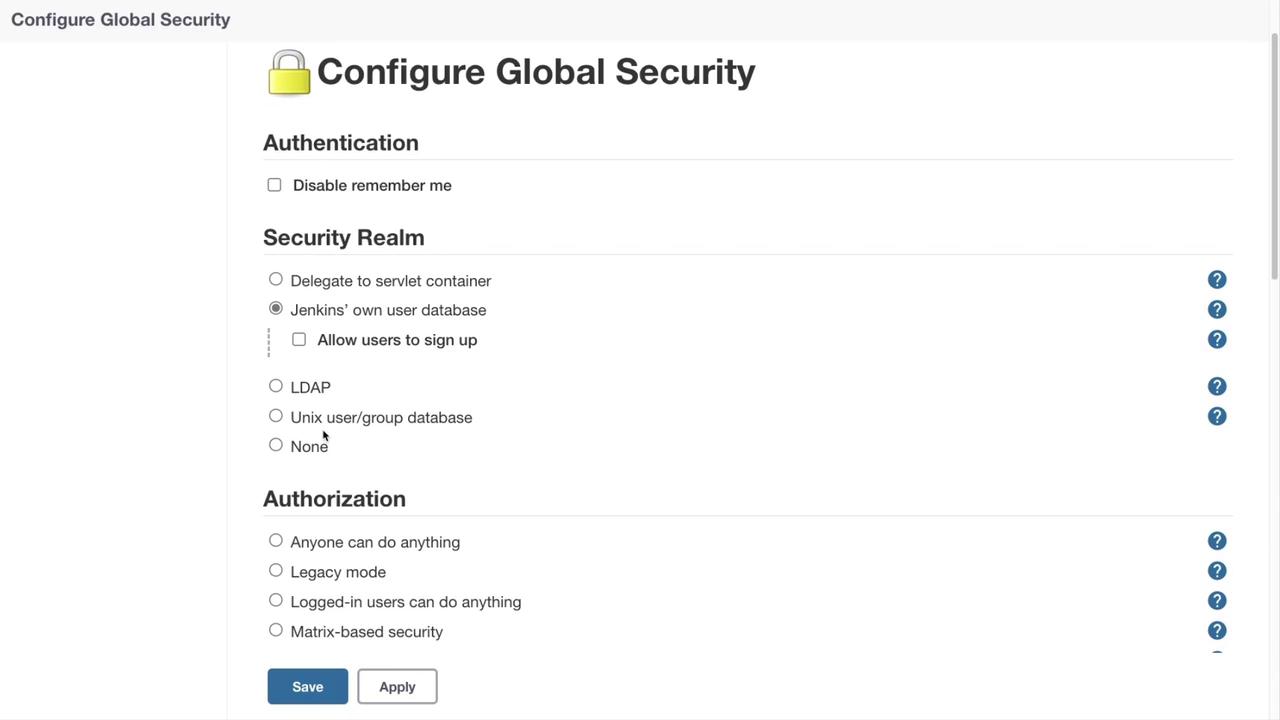
Authentication and Authorization
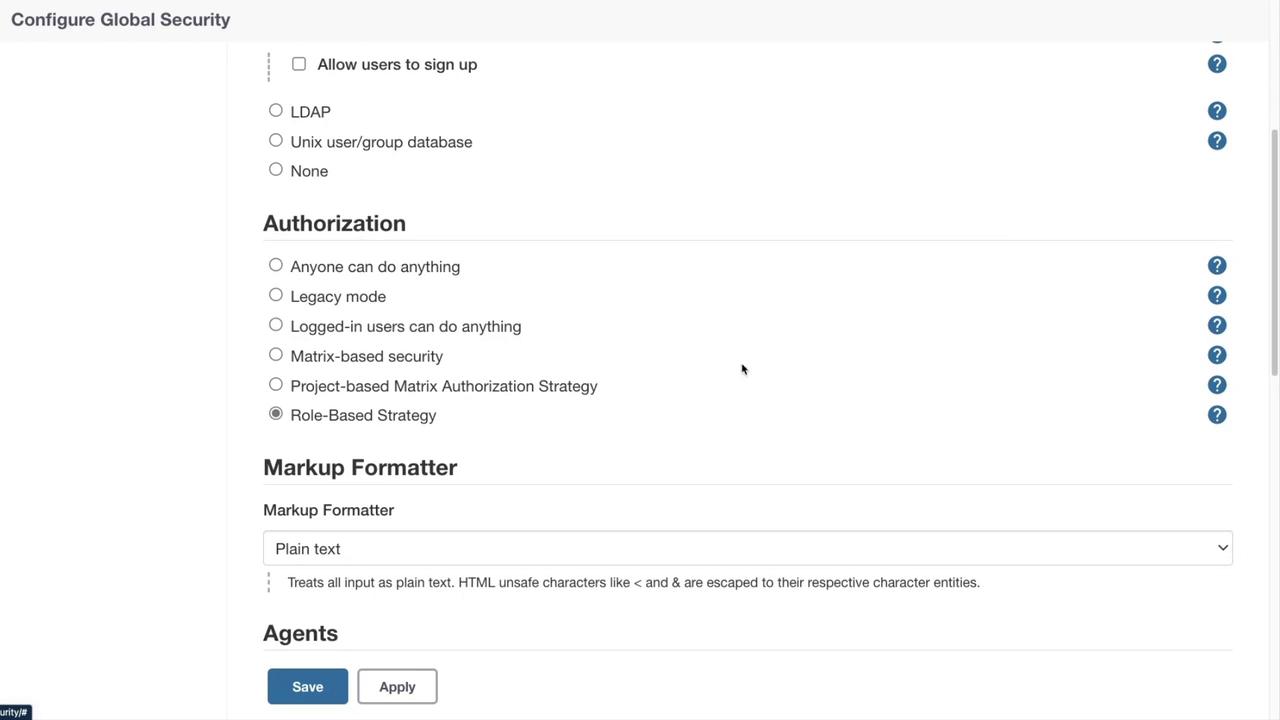
For enhanced security, you can disable the "remember me" functionality to avoid automatic logins. Jenkins supports various authorization strategies, including a role-based strategy provided via a plugin, which offers more granular permissions compared to legacy models.
Agent and Controller Security
Managing how build agents interact with the Jenkins controller is another critical aspect. If inbound agents are not in use, it is recommended to disable the related communication options. When agents are required, ensure that the proper ports are open and configured for secure communication.
Additional settings suppress security warnings from update sites, manage API token creation (with best practices advising against legacy API tokens), and secure the communication between agents and the controller.
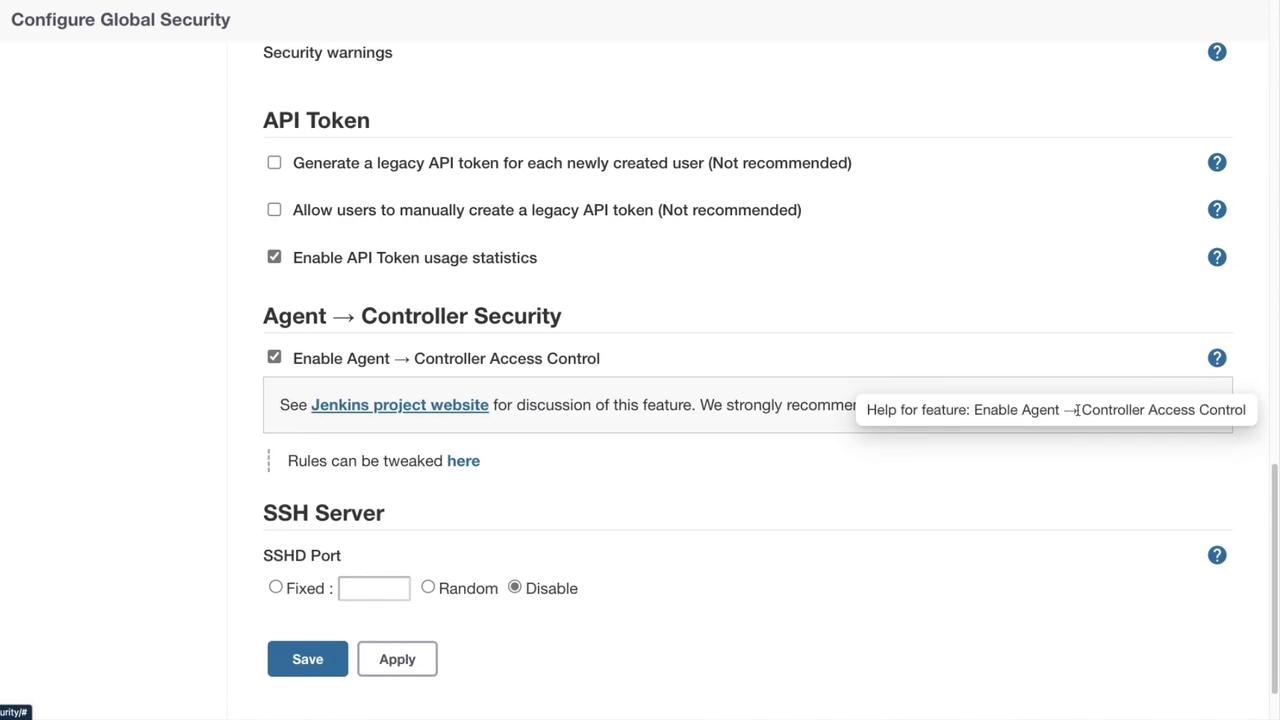
SSH Server for CLI Commands
Jenkins can also operate as an SSH server to process a subset of CLI commands, allowing centralized management of CLI operations directly through the Jenkins server.
Note
Ensure that SSH configurations are secured and that access is limited to trusted users to prevent unauthorized actions.
Conclusion
This guide covered the primary configuration areas within Jenkins—from system settings and source control integration to email notifications and security configurations. Exploring and fine-tuning these settings in your Jenkins instance will help you create a secure, efficient, and industry-compliant CI/CD environment.
For further details, consider reviewing additional resources:
Happy configuring!
Watch Video
Watch video content
Practice Lab
Practice lab