Kubernetes and Cloud Native Security Associate (KCSA)
Compliance and Security Frameworks
Threat Modelling Frameworks
In this lesson, we’ll dive into popular threat modeling frameworks that guide security teams on how to secure systems by identifying threats, visualizing attack paths, and suggesting mitigations. We’ll contrast these with compliance frameworks that focus on what to achieve to meet legal or industry standards.
Compliance Frameworks vs Threat Modeling
Compliance frameworks—such as GDPR, HIPAA, PCI DSS, NIST, and CIS Benchmarks—define what security controls and processes are required for regulatory or industry compliance:
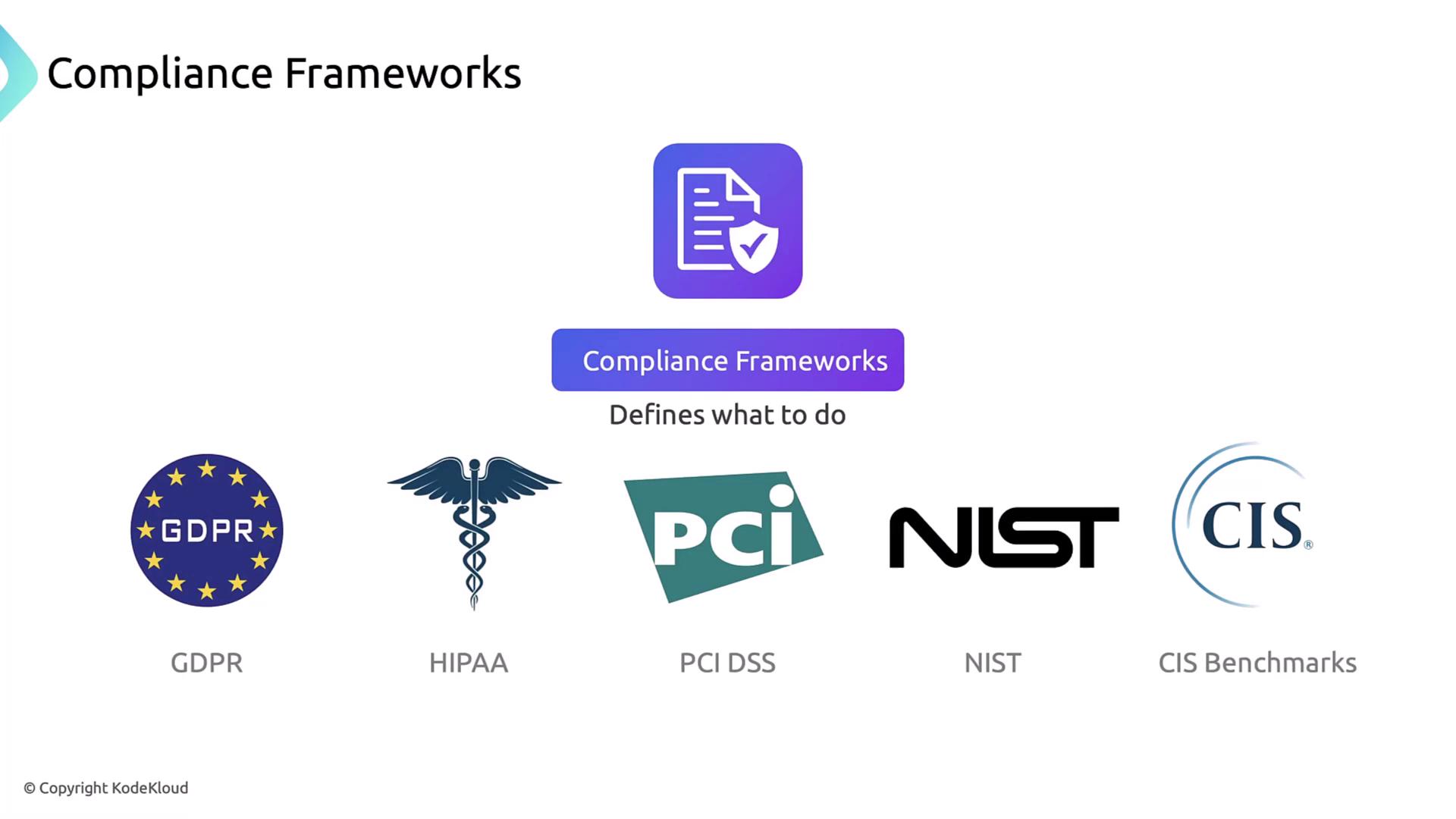
For instance, GDPR mandates protecting personal data against unauthorized access but does not prescribe how to implement those safeguards:

Threat modeling frameworks fill this gap by offering structured methods—like attack trees or matrices—to discover potential attacks and recommend specific countermeasures. Two widely adopted models are:
- STRIDE (Microsoft)
- MITRE ATT&CK (Global knowledge base)
STRIDE: Six Threat Categories
STRIDE breaks down threats into six distinct types, helping teams audit applications or infrastructure end to end:
| Threat Type | Definition | Common Mitigation |
|---|---|---|
| Spoofing | Impersonation of a legitimate user or system | Multi-factor authentication, certificate-based auth |
| Tampering | Unauthorized modification of data in transit or at rest | Encryption, digital signatures |
| Repudiation | Denial of actions performed (e.g., transactions) | Comprehensive logging, non-repudiation techniques |
| Information Disclosure | Exposure of sensitive data | TLS for transit, disk encryption |
| Denial of Service | Resource exhaustion or service disruption | Rate limiting, resource quotas, autoscaling policies |
| Elevation of Privilege | Unauthorized gain of higher-level permissions | Role-Based Access Control (RBAC), least privilege |
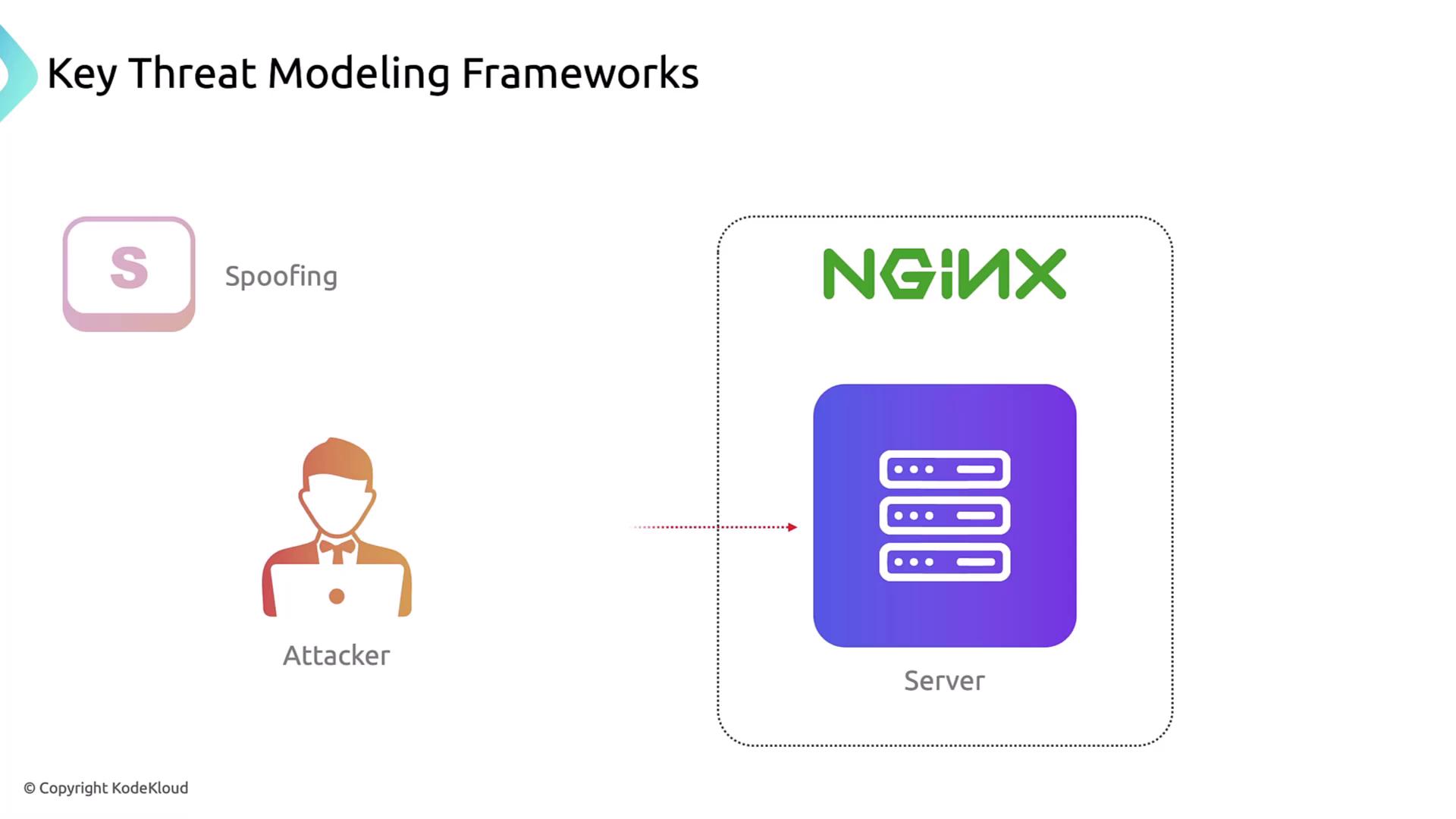
1. Spoofing
An attacker forges credentials to access the front end (e.g., NGINX).
Mitigation: enforce strong authentication and certificate validation.
2. Tampering
An adversary alters data either in flight or at rest on backend services.
Mitigation: apply end-to-end encryption and use checksums or digital signatures.
3. Repudiation
Users or attackers deny performing specific actions (e.g., financial transfers).
Mitigation: implement immutable audit logs and digital-signature-based non-repudiation.
![]()
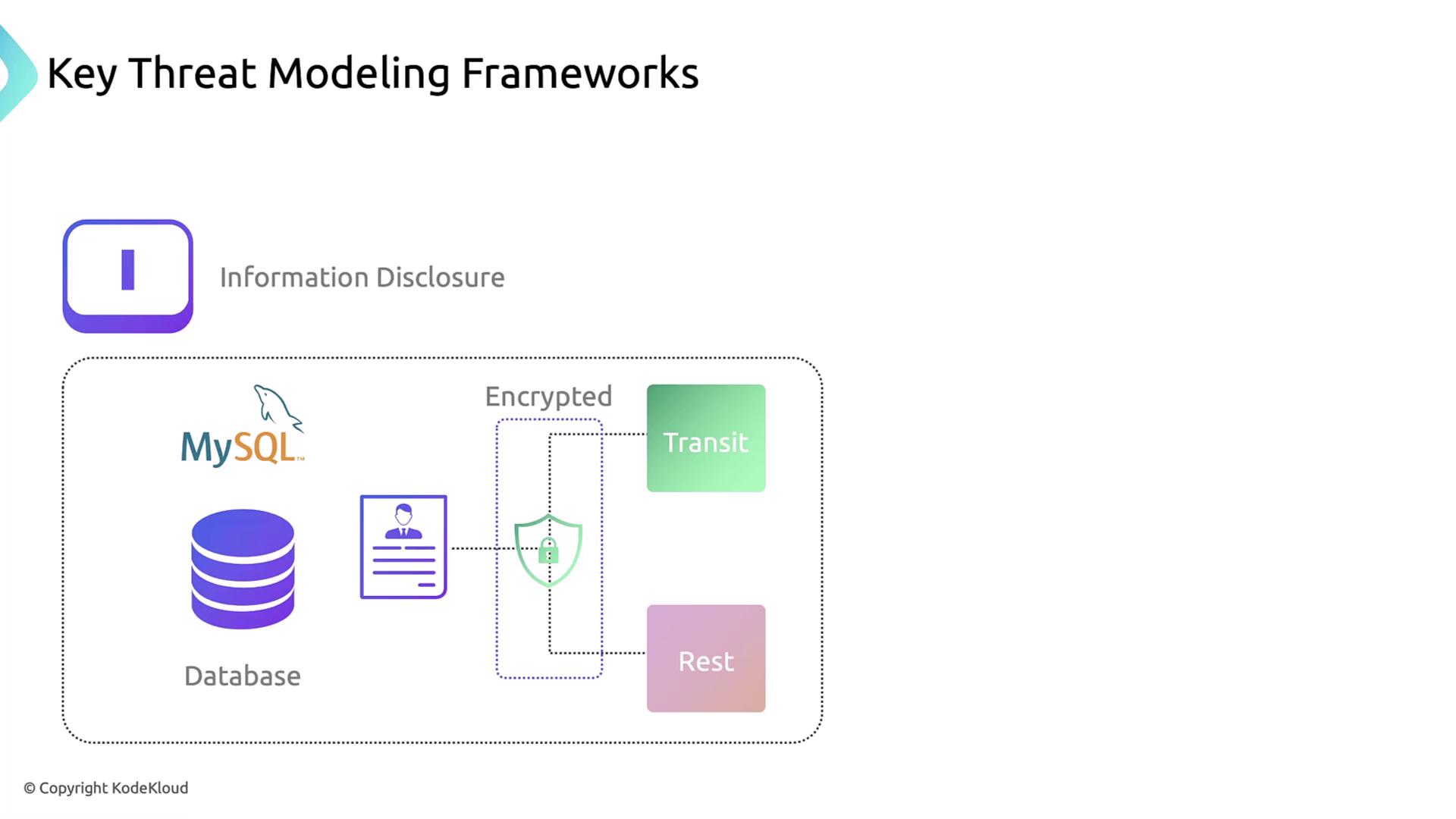
4. Information Disclosure
Sensitive information (e.g., customer PII in a MySQL database) becomes exposed.
Mitigation: encrypt data at rest and enforce TLS/TCP encryption in transit.
5. Denial of Service
Attackers flood the application, overwhelming resources and causing outages.
Mitigation: configure rate limits, implement resource quotas in Kubernetes, and deploy autoscaling.
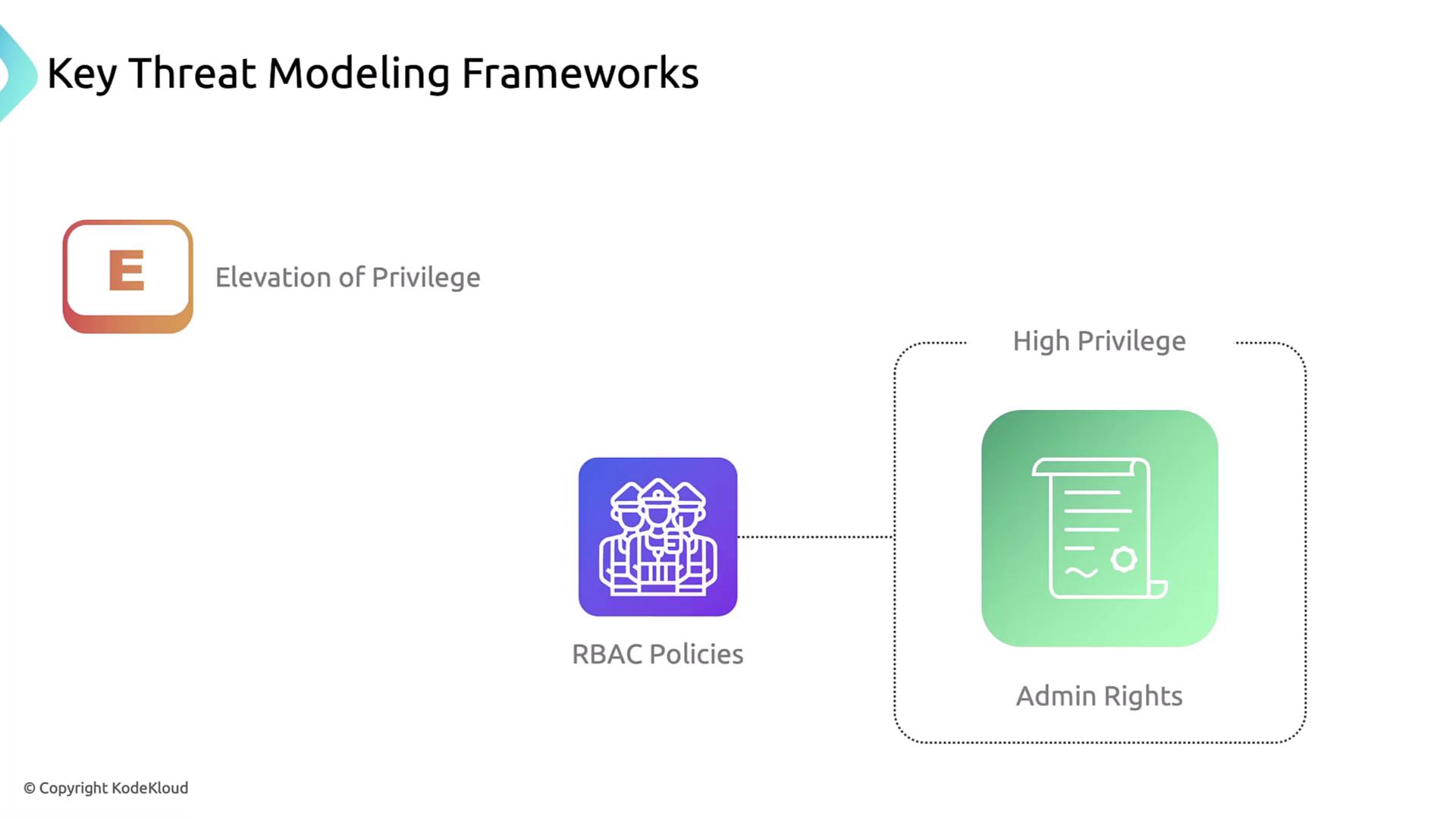
6. Elevation of Privilege
An unauthorized principal gains admin-level rights within the cluster.
Mitigation: enforce strict RBAC policies and conduct regular privilege reviews.
Note
Integrating STRIDE early in your design process uncovers gaps before production deployment.
MITRE ATT&CK: Real-World Tactics & Techniques
The MITRE ATT&CK framework catalogs adversary tactics (goals) and techniques (methods) observed in the wild. For Kubernetes environments, these techniques map to cluster-specific scenarios:
- Initial Access: Exploit weak authentication, compromise cloud credentials
- Execution: Deploy malicious containers or init-hooks
- Persistence: Create backdoor user accounts, install rogue controllers
- Privilege Escalation: Abuse misconfigured RBAC or admission controllers
- Defense Evasion: Disable logging, tamper with audit trails

MITRE Kubernetes Threat Matrix
Microsoft’s Kubernetes threat matrix adapts ATT&CK to cluster contexts, enabling teams to visualize attacker pathways and design targeted mitigations:
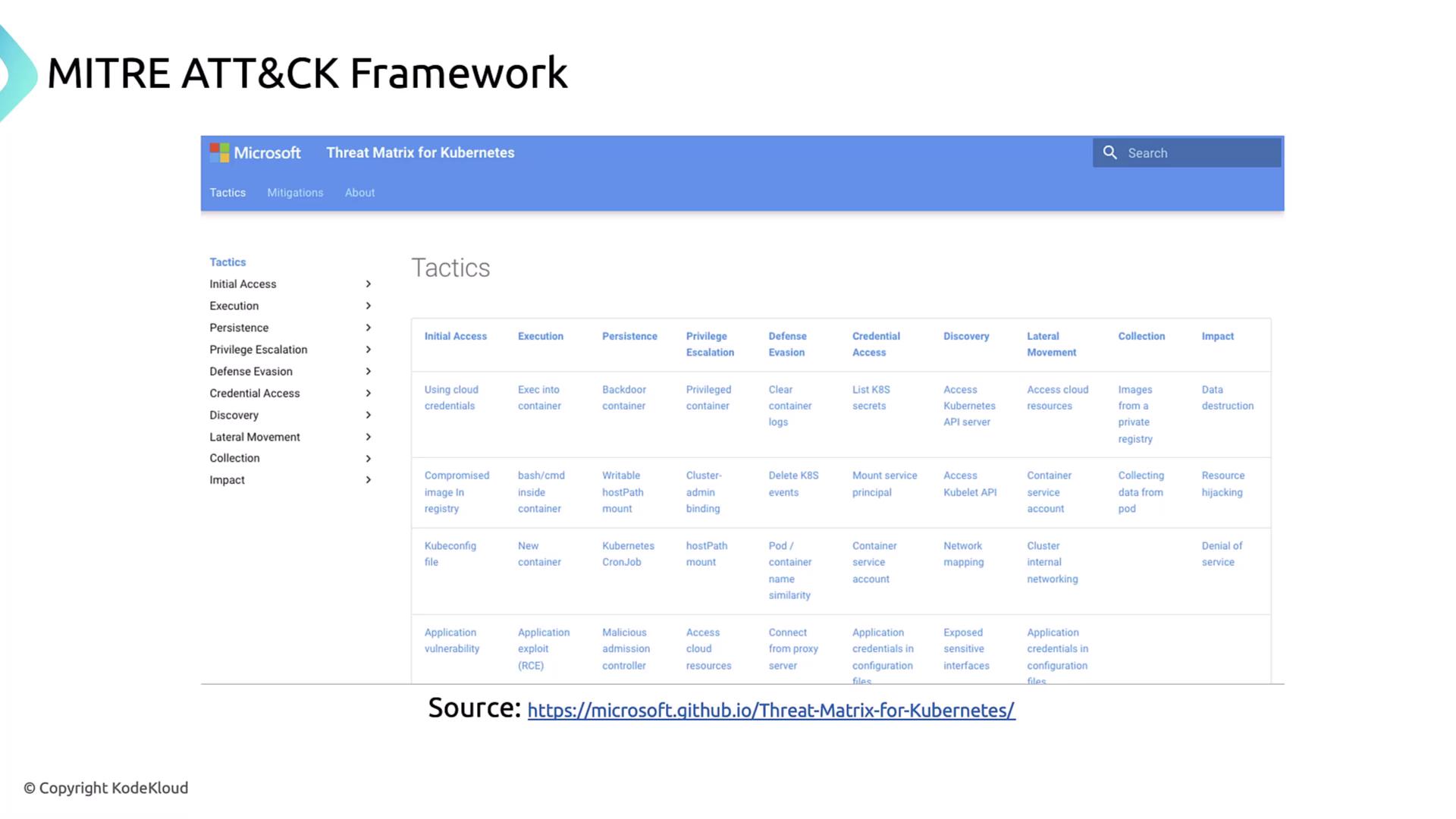
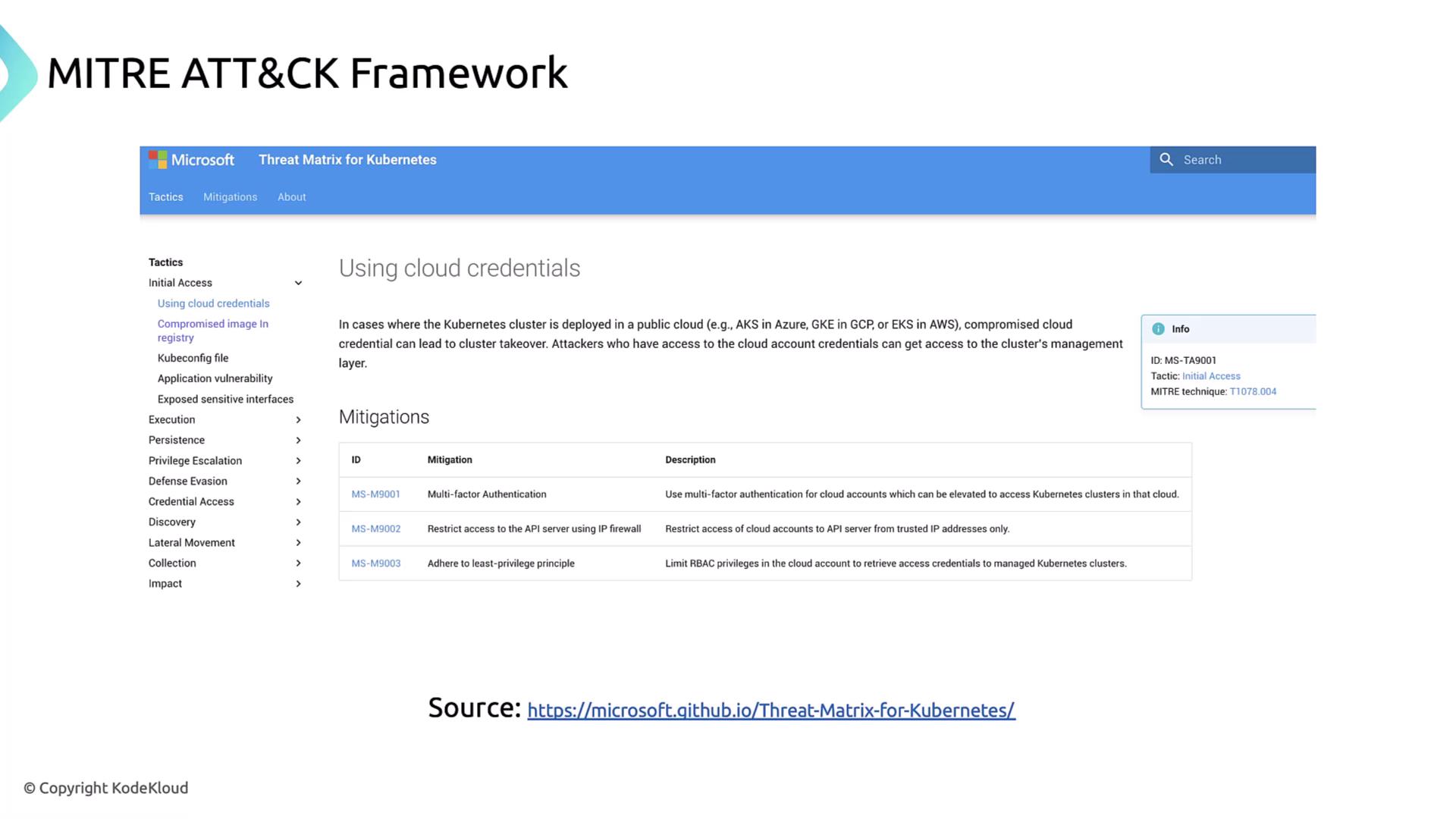
Under Using Cloud Credentials (Initial Access), ATT&CK recommends:
- Enabling multi‐factor authentication
- Restricting API server exposure with IP allowlists
- Applying least‐privilege principles to service accounts
Warning
Neglecting to map MITRE techniques to your Kubernetes deployment can leave critical attack paths unaddressed.
Summary
By combining compliance frameworks (GDPR, HIPAA, NIST) with threat modeling (STRIDE, MITRE ATT&CK), security teams can:
- Understand what requirements apply to your environment.
- Determine how to implement controls that mitigate real-world threats.
- Continuously refine defenses through structured threat analysis.
Integrate these models into your SDLC to identify risks early and build resilient, secure systems.
Links and References
- STRIDE Threat Model (Microsoft)
- MITRE ATT&CK Framework
- Kubernetes RBAC Documentation
- GDPR Compliance Guide
Watch Video
Watch video content