Kubernetes’s Flat Network Model
By default, Kubernetes implements a flat network where:- Each Pod receives a unique IP address.
- Containers within the same Pod share network namespace, IP, and port space.
- Pods communicate directly, without NAT.
- DNS resolves Services to enable Pod-to-Service calls.
- External traffic is routed through Ingress controllers or external LoadBalancers.
Running with an open, flat network model means any Pod can talk to any other Pod by default. Always apply security controls before deploying production workloads.
Network Security Focus Areas
| Security Area | Tooling/Feature | Purpose |
|---|---|---|
| Pod-to-Pod Traffic Control | Network Policies | Restrict ingress/egress at the Pod level |
| Service-to-Service Communication | Service Mesh (Istio, Linkerd) | Enforce mTLS, advanced routing, observability |
| Node-to-Node Encryption | Calico with IPsec / WireGuard | Encrypt inter-node traffic |
| Workload Isolation | Namespaces & Network Policies | Limit blast radius through segment isolation |
1. Restricting Pod Communication with Network Policies
By default, all Pod-to-Pod traffic is permitted. To establish a secure baseline, use a deny-by-default policy:default namespace. You can then layer on additional policies to explicitly allow necessary connections.
After applying a deny-all policy, define granular allow rules for DNS, API server access, and any other required services.
2. Service-to-Service Security with a Service Mesh
Deploying a service mesh such as Istio or Linkerd adds powerful features: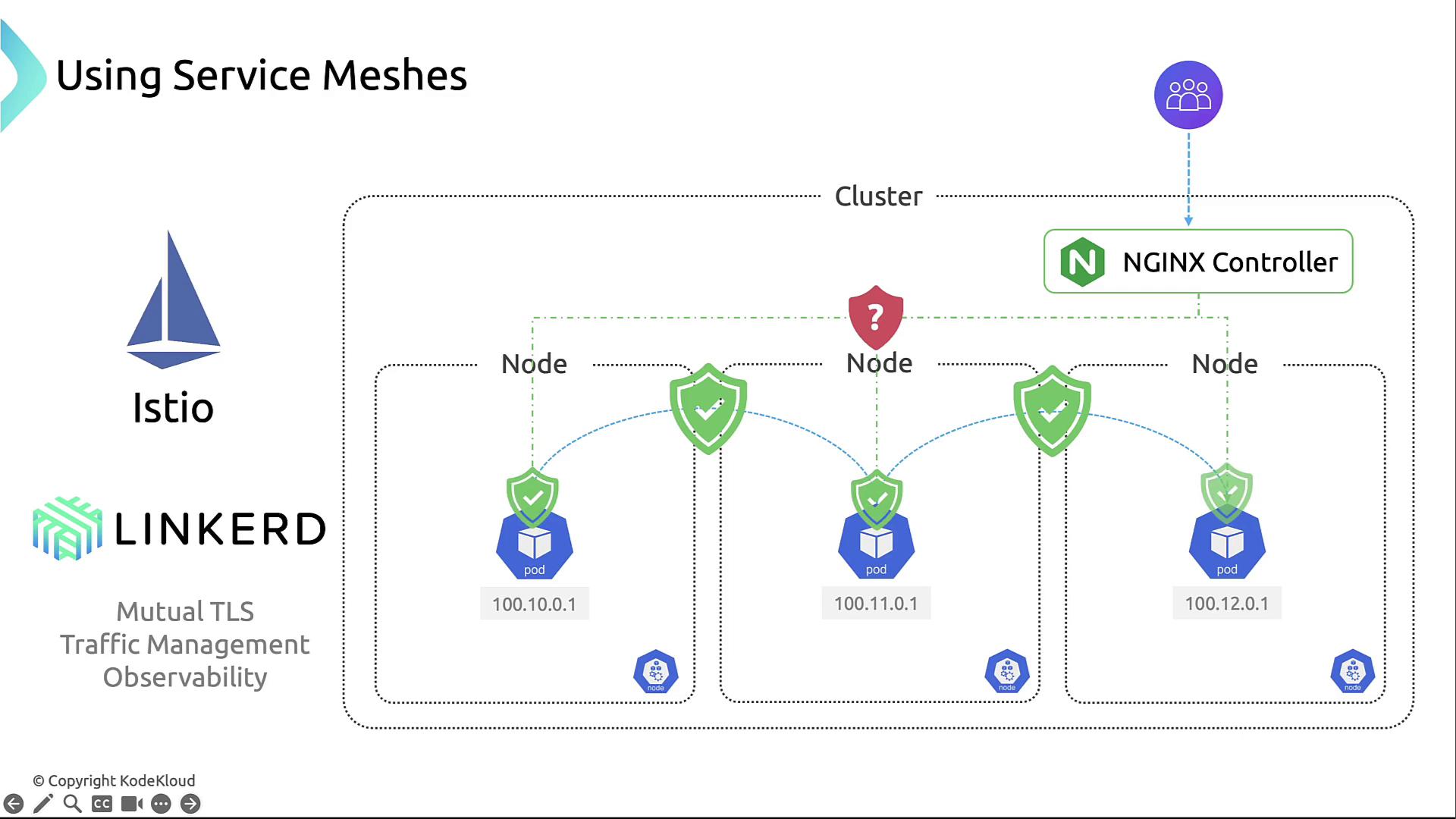
- Mutual TLS (mTLS) encrypts and authenticates service-to-service calls.
- Fine-grained traffic management: retries, timeouts, and routing rules.
- Built-in telemetry, metrics, and logs for full observability.
3. Encrypting Network Traffic Between Nodes
Protect data in transit at the network layer by enabling encryption with CNI plugins like Calico: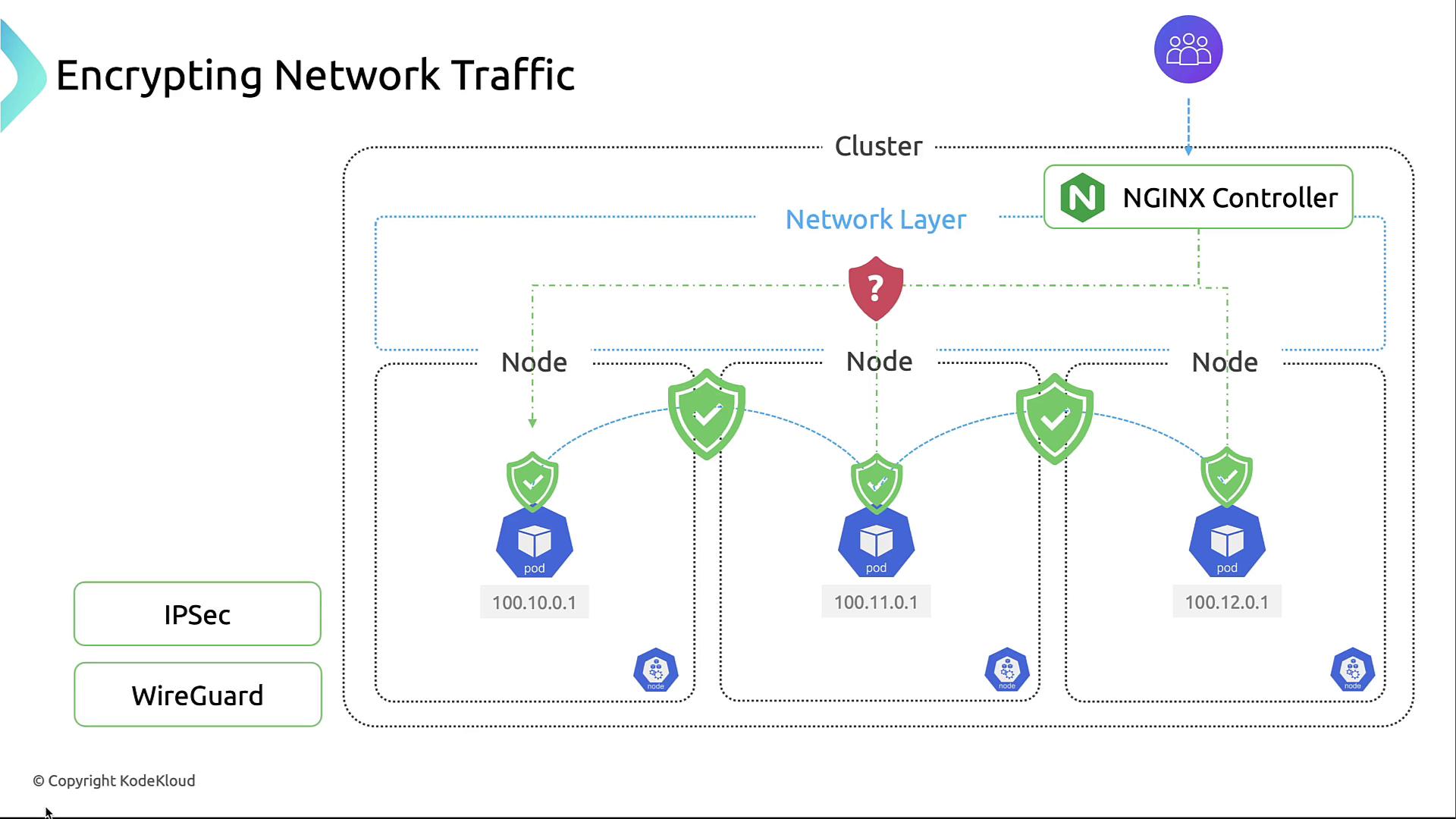
- Calico + IPsec: Encrypts all inter-node traffic without requiring additional hardware.
- WireGuard: A lightweight, high-performance VPN alternative.
4. Isolating Sensitive Workloads
Segregate critical applications into dedicated namespaces and apply strict policies to reduce lateral movement: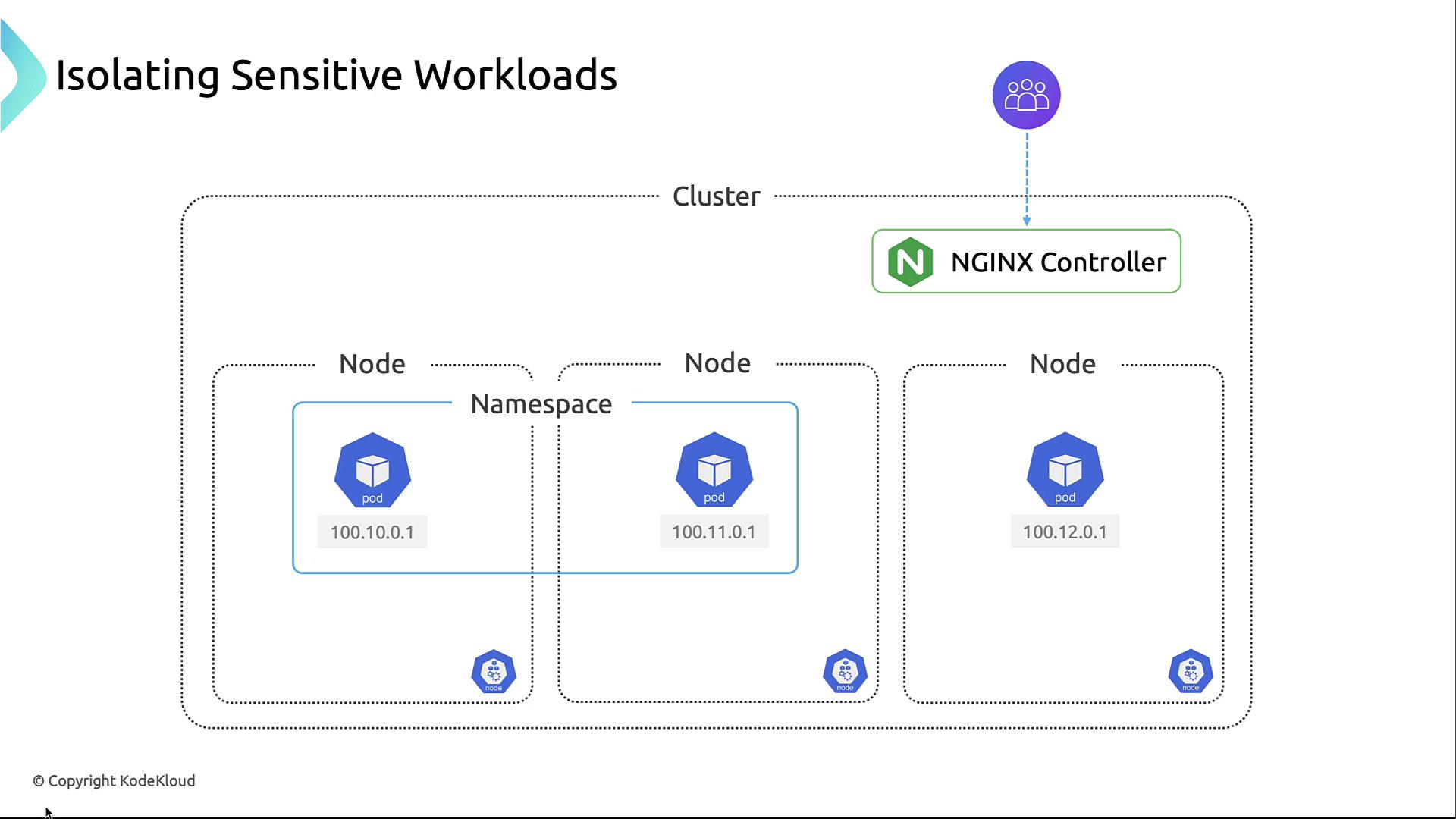
Summary
- Define Network Policies to control Pod-level traffic.
- Deploy a Service Mesh for mTLS and advanced routing.
- Encrypt inter-node traffic with IPsec or WireGuard.
- Use Namespaces and strict policies to isolate workloads.