What Is Malicious Code Execution?
Malicious code execution occurs when an adversary leverages a vulnerability in your application or cluster configuration to run unauthorized commands or binaries inside a container or on the host system. This can lead to privilege escalation, data exfiltration, or full cluster compromise.Attack Vectors and Threat Model
Attackers may use one or more of the following methods:| Attack Vector | Description | Potential Impact |
|---|---|---|
| Import Tools or Scripts | Containers with curl, wget, or package managers download extra payloads. | Arbitrary code execution inside pods. |
| Modify Host Files | Mounted host filesystem allows tampering with config files or startup scripts. | Persistence and stealthy backdoors. |
| Host-Level Process Injection | Abusing host PID namespace or SYS_PTRACE to trace/inject into host processes. | Host compromise and lateral movement. |
Granting
SYS_PTRACE or enabling host PID namespaces is highly risky. Review Kubernetes Pod Security Standards before enabling any privileged capabilities.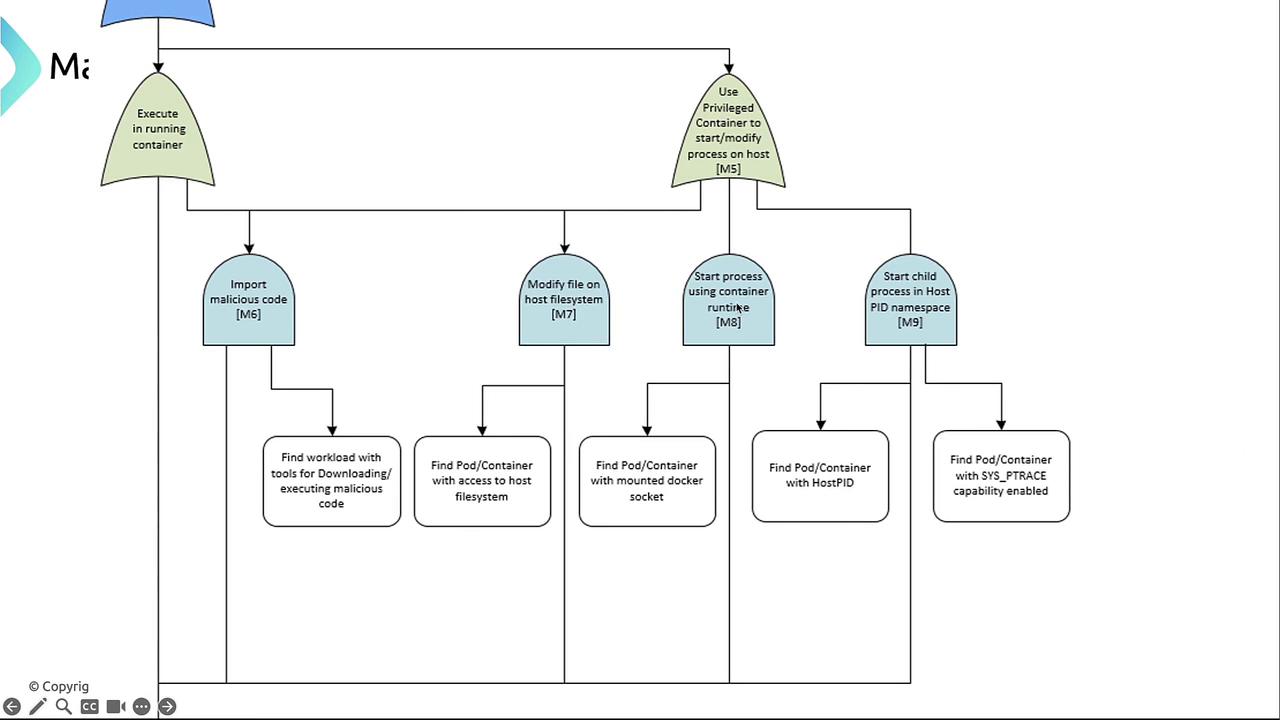
Post-Compromise via Kubernetes API
Once inside the container, an attacker can call the Kubernetes API to spawn new pods, trigger Denial of Service, or harvest credentials.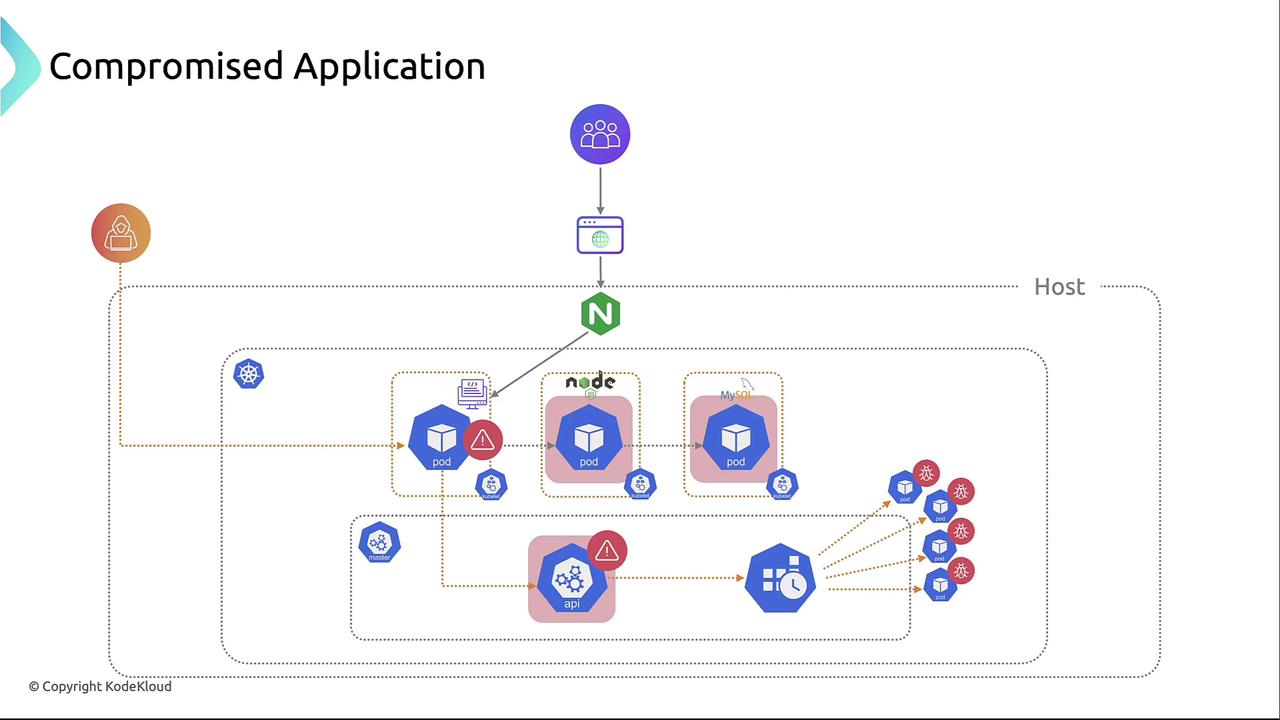
Poisoning the Image Repository
If attackers obtain an image pull secret, they can push backdoored images to your registry. Subsequent deployments that pull these images will run malicious containers.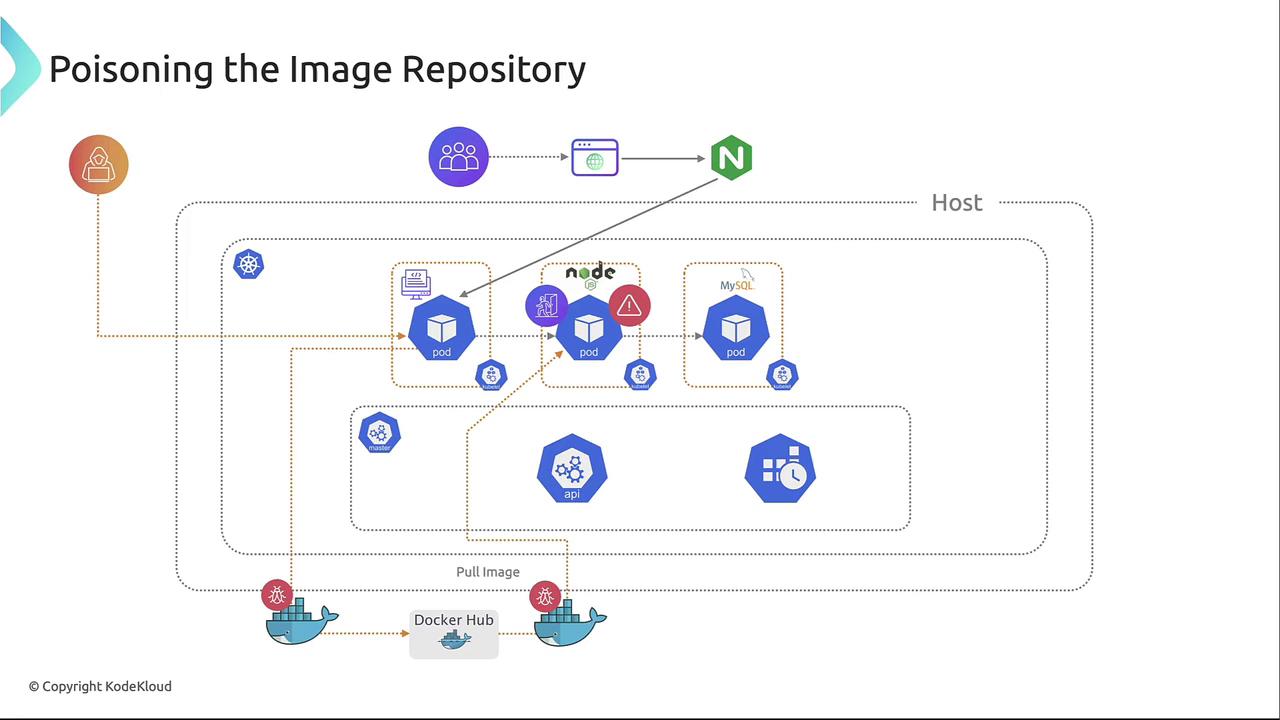
Mitigation Strategies
1. Scan and Patch Vulnerabilities
Regularly scan container images and host OS for CVEs. Integrate vulnerability scanners like Trivy in your CI/CD pipeline and apply security patches promptly.
Automate image scanning with every build. Block deployments if high-severity vulnerabilities are found.
2. Restrict API Server Access
Enforce strong authentication and granular RBAC policies so that only trusted identities can call sensitive API endpoints.
3. Secure Image Repositories and Pull Secrets
Store your image pull secrets in encrypted vaults (e.g., HashiCorp Vault). Limit service accounts that can reference them and enforce image signing to verify integrity.4. Monitor and Alert
Use audit logs and monitoring tools to detect exec calls, secret changes, or anomalous API usage. For Kubernetes clusters with Prometheus:5. Audit and Review
Periodically review RBAC roles, service account permissions, and image registry policies. Conduct penetration tests to validate your security posture.
Summary of Container Security Measures
- Restrict API server access to authorized roles.
- Secure image registries and enforce signed images.
- Monitor audit logs and set up real-time alerts.
- Keep containers and hosts up to date with patches.
- Regularly audit RBAC, service accounts, and CI/CD pipelines.