- Individual Azure Active Directory (AD) identity
- Admin user (built into the registry)
- Azure AD service principal
- Managed identity for Azure resources
- AKS cluster managed identity
- AKS cluster service principal
- Repository-scoped access tokens
Individual Azure Active Directory Identity
Using your individual AD identity allows for interactive authentication via Azure CLI or Azure PowerShell. This method is particularly useful for developers or testers who manually push or pull images. It supports Azure Role-Based Access Control (RBAC); however, note that the AD token must be renewed every three hours. If you log out, reauthentication is required. Commands:Make sure to keep track of token renewal to avoid authentication failures during your session.
Admin User
Every container registry includes a built-in admin user independent of your Azure AD administrator account. When enabled, you can authenticate using the Docker CLI. This method is suitable for both interactive operations and unattended pulls by systems or external devices. Key Considerations:- Azure RBAC is not supported since the credentials are managed outside Azure Resource Manager.
- Only one admin account exists per registry. Sharing these credentials makes it difficult to trace individual user activities.
If you encounter an error about the admin user not being enabled, navigate to the ACR access keys section in the Azure portal to enable it.
Azure AD Service Principal
An Azure AD service principal can provide authentication across multiple tools, such as Docker CLI, Azure CLI, PowerShell, REST API, or even Kubernetes pull secrets. This method is ideal for unattended scenarios like CI/CD pipelines or external services. Benefits & Limitations:- Supports RBAC since it is tied to Azure Resource Manager.
- The default service principal password expires after one year. You must renew it in Azure Active Directory and update all affected pipelines or services.
Managed Identity for Azure Resources
Managed identities are designed to simplify authentication for Azure resources such as Function Apps or App Services. When using managed identities, you no longer need to manage explicit credentials for unattended push or pull operations. Common Commands:Ensure that the Azure resource you are using supports managed identities.
AKS Cluster Managed Identity
When working with an Azure Kubernetes Service (AKS) cluster, you can utilize the cluster’s managed identity to authenticate against ACR. This is achieved by attaching your container registry during the creation or update of the AKS cluster. Important Points:- This method does not support RBAC since the authentication is directly linked to the AKS cluster.
- Both the registry and the AKS cluster must reside within the same tenant; it cannot be used for cross-tenant authentication.
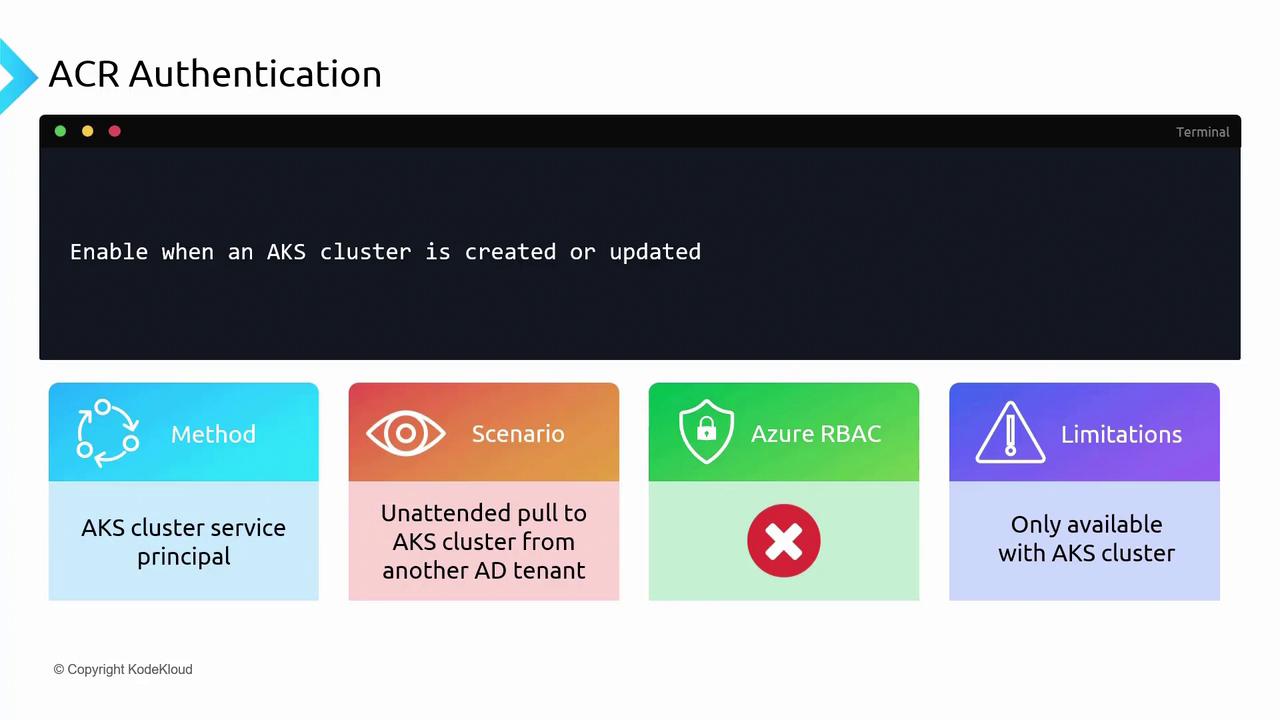
AKS Cluster Service Principal
Alternatively, you can integrate an Azure AD service principal with your AKS cluster during cluster creation or update. This method supports cross-tenant scenarios, which is beneficial if your AKS cluster and ACR reside in different tenants. Similar to the managed identity approach, it does not support RBAC.Repository-Scoped Access Tokens
Repository-scoped access tokens are designed to provide tokens for authenticating directly to ACR. They are suitable for both interactive push/pull operations by developers or testers and unattended pulls by external systems. These tokens support RBAC; however, they are generated externally and are not integrated with Azure AD identities. Authentication Commands:Demonstration: Using ACR with a Container Instance
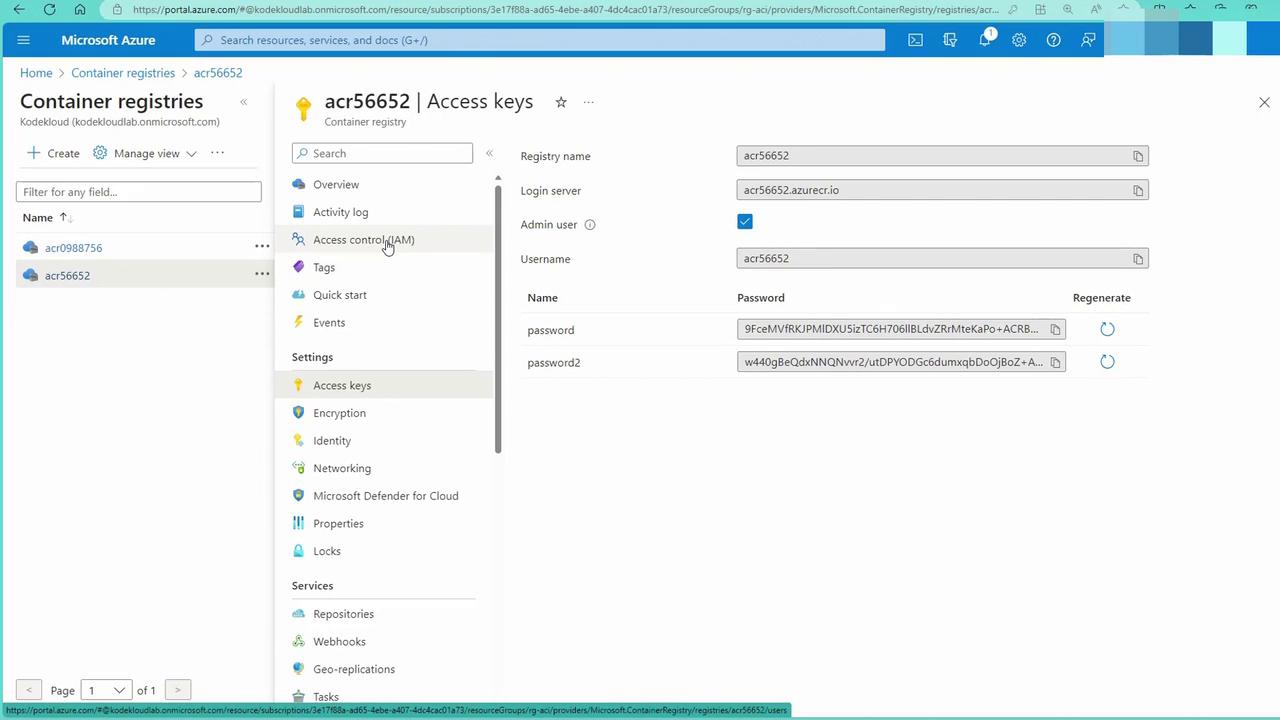
This section demonstrates how to use the admin account in ACR to pull an image into a container instance.- In the Azure portal, navigate to your container registry and select it.
- Go to the Access Keys section to enable the admin user. Once enabled, you will see a username and password which can be used with the Docker login command.
- Open the container registry access keys view:
-
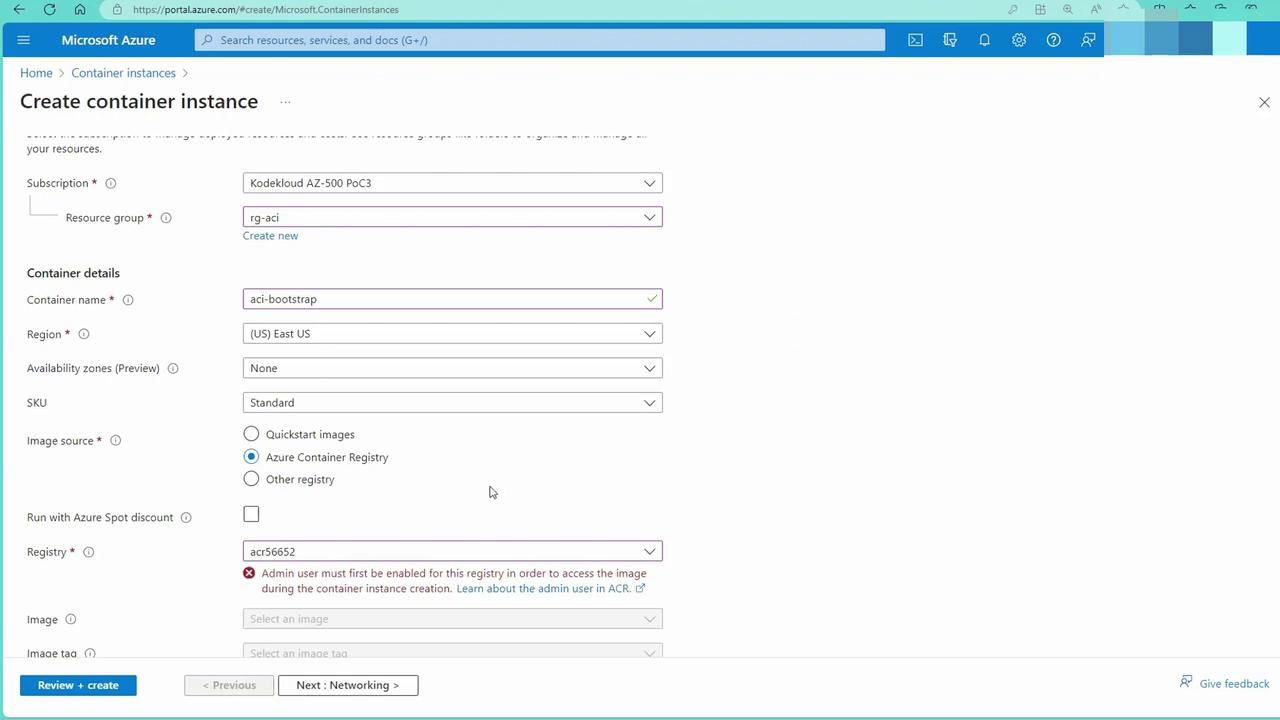
Create a container instance by following these steps:
- Navigate to Container Instances in the Azure portal.
- Create a new instance by selecting the previously configured container registry and using the admin credentials.
- Set container details (e.g., name, OS type, size) and configure the networking settings to expose port 80 publicly.
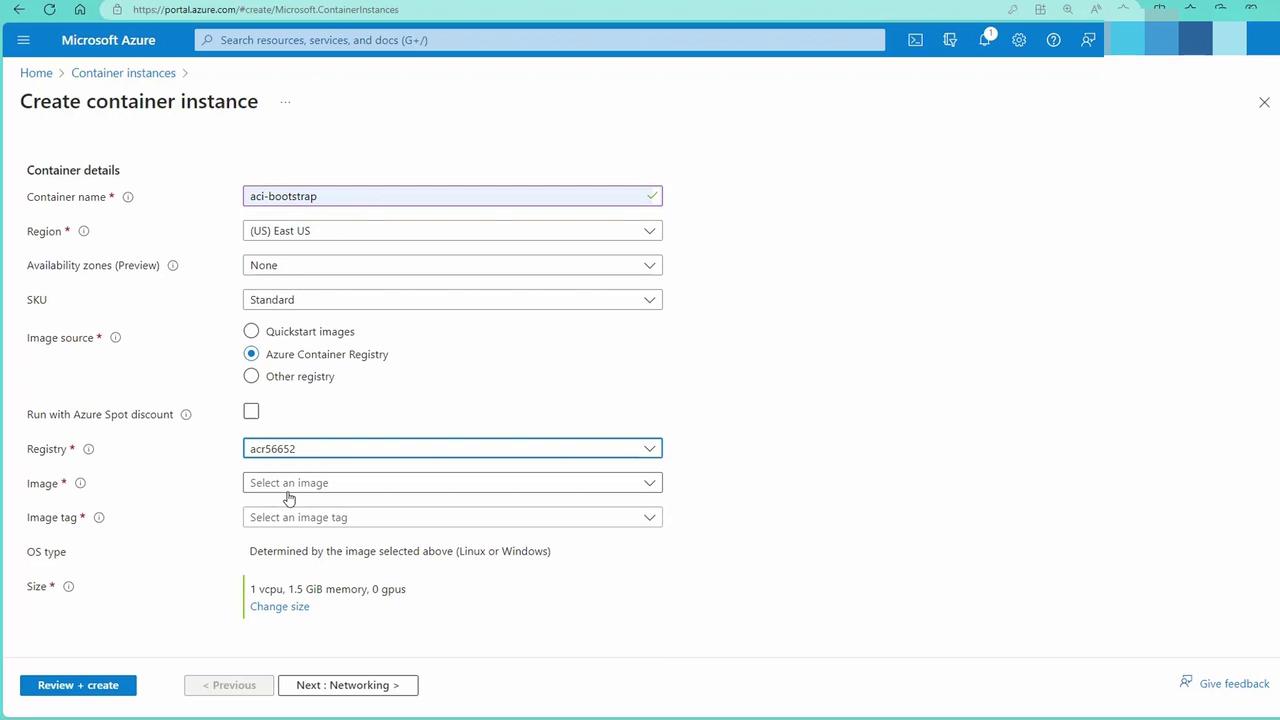
- Configure the networking options for the container instance:
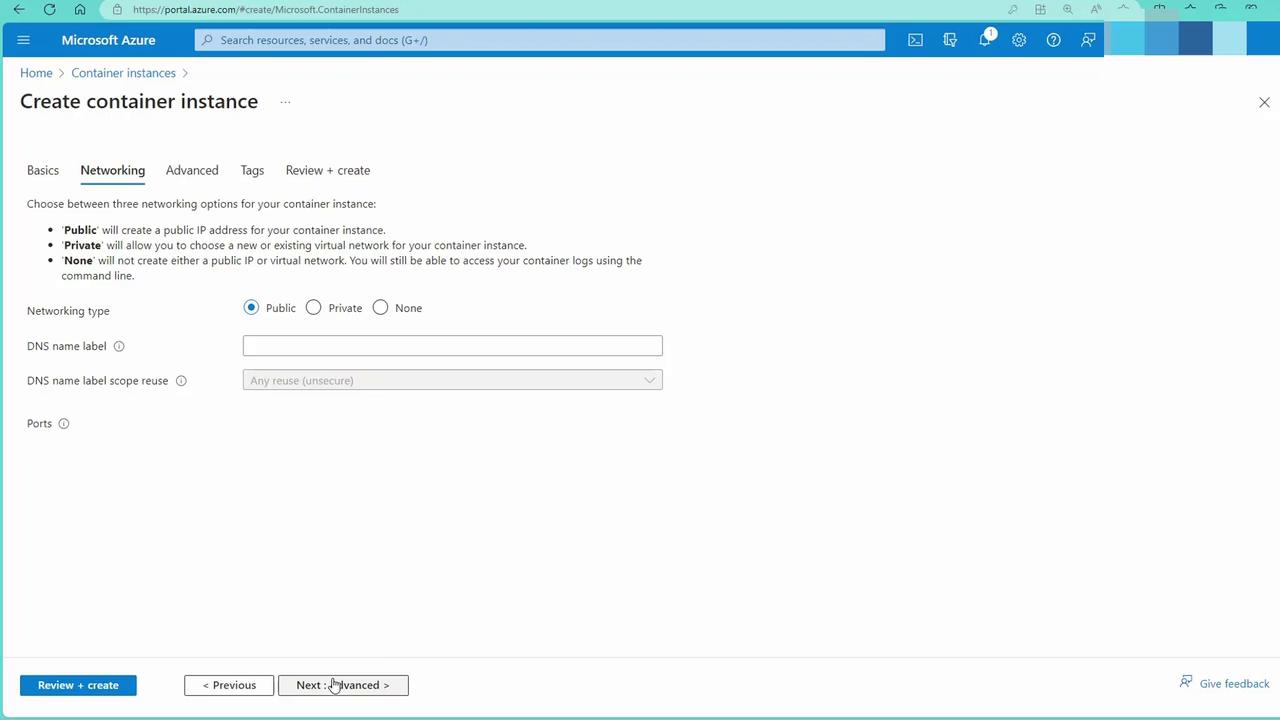
- Review all settings and click the “Create” button to deploy the container instance:
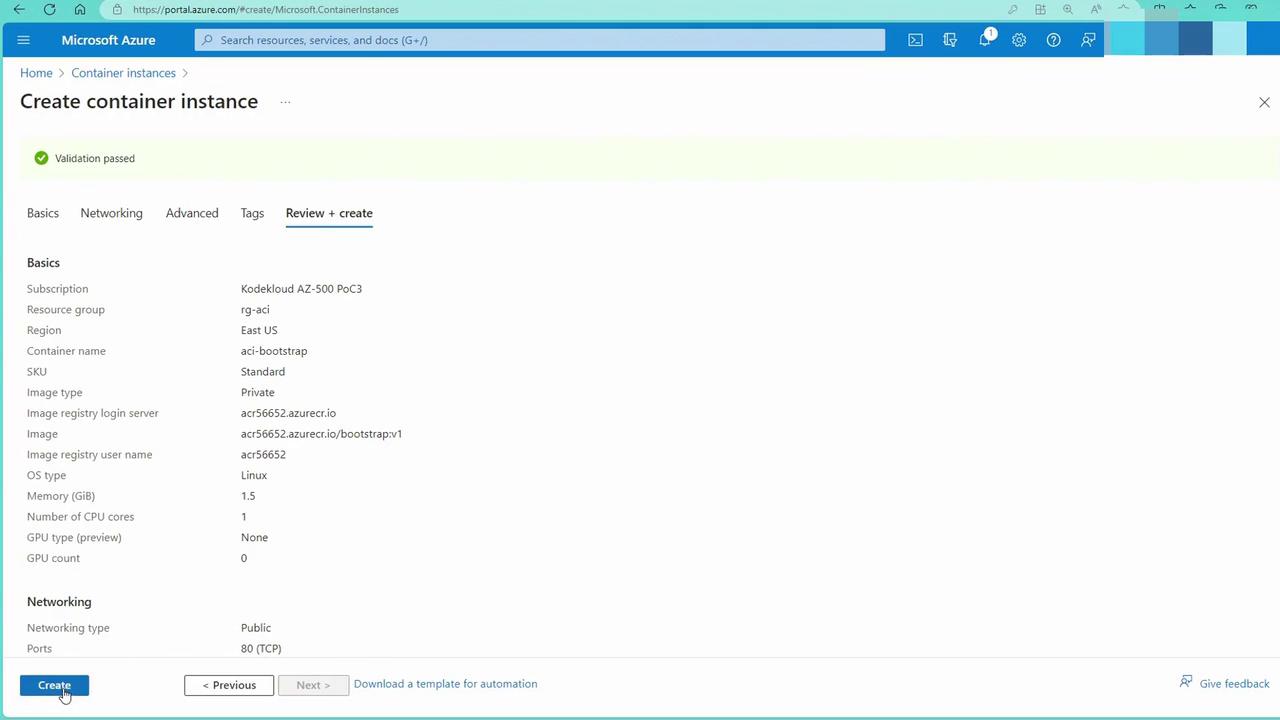
- After deployment, click “Go to Resource” to check the container details:
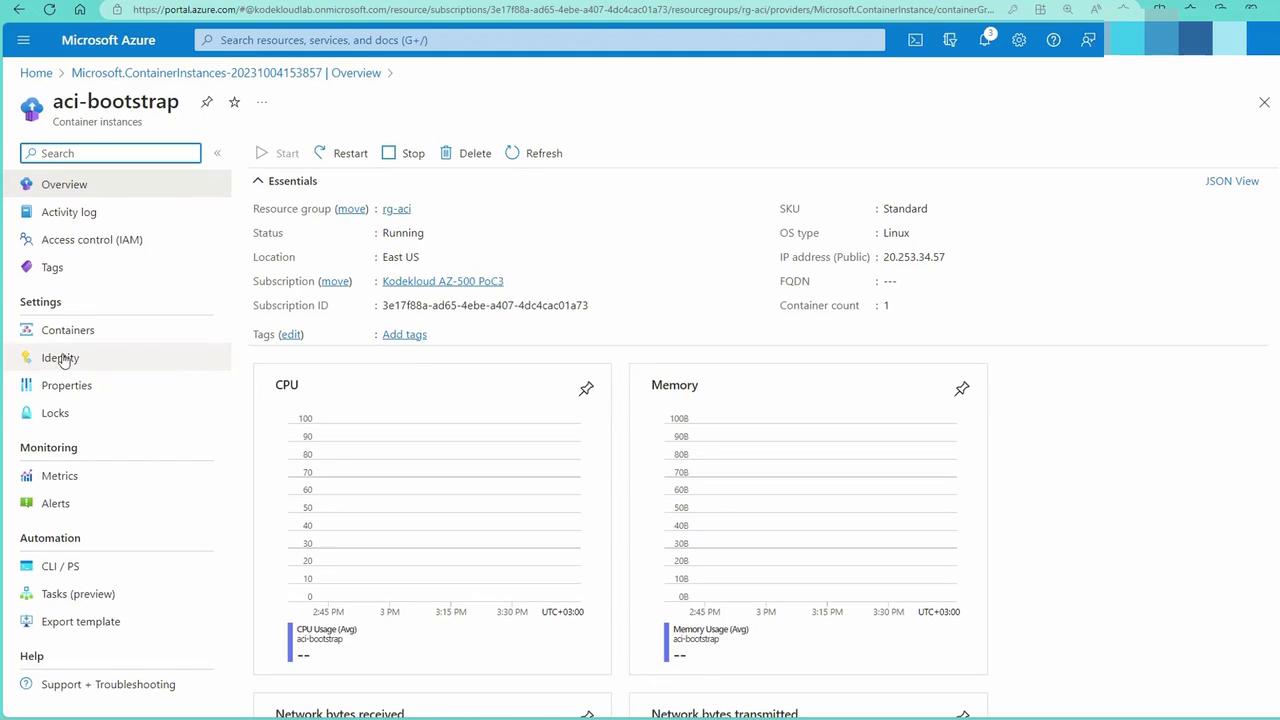
In this article, we covered the various authentication methods available for Azure Container Registry and demonstrated the use of the admin account with container instances. Stay tuned for more details on integrating ACR with Azure Kubernetes Service in future articles. Thank you.