Group Types
Azure AD supports two primary group types:-
Security Groups
Security groups function like virtual fortresses that simplify access and permission management. They enable you to bundle users together based on roles, streamlining authentication and resource management. -
Microsoft 365 Groups
These groups are designed for collaboration. In addition to security features, they provide shared resources such as inboxes, calendars, files, SharePoint sites, OneDrive, and more. Choose Microsoft 365 groups when you need group membership combined with robust collaboration tools.
Membership Types
Azure AD offers three types of group membership assignments:1. Assigned Membership
With assigned membership, users are added to groups manually. For example, a new employee can be added to a designated HR group. The user remains in the group until manually removed or deleted. While this method is straightforward, it requires ongoing administrative intervention for role changes or reassignment.2. Dynamic User Membership
Dynamic user groups update their membership automatically based on predefined rules using user attributes such as job title, department, or manager. For instance, if you set a rule to include all users with a manager named “Chris,” any new employee with that manager will be added automatically. If their manager changes, the rule triggers their removal. This automation keeps group membership current without manual updates.3. Dynamic Device Membership
Dynamic device groups work similarly but are based on device-specific attributes like device type, operating system, or device version. Note that dynamic device membership is available only in security groups because devices typically do not require collaboration tools such as SharePoint or shared mailboxes. Use this option when you need to group devices for policy applications, like grouping older Windows 10 machines for targeted notifications.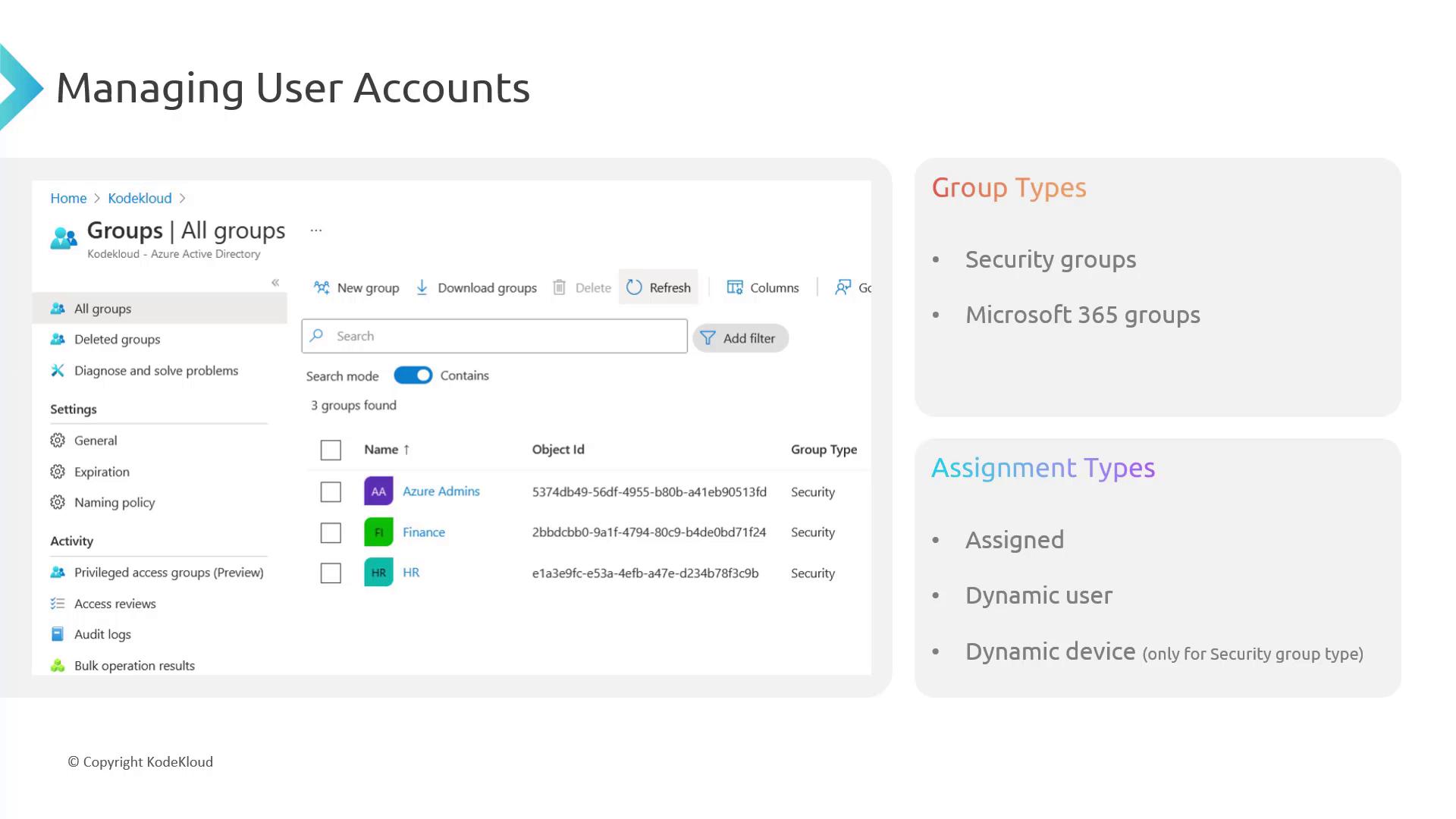
Creating Groups in the Azure Portal
To create groups, navigate to Azure Active Directory in the Azure portal, then select Groups (located below Users).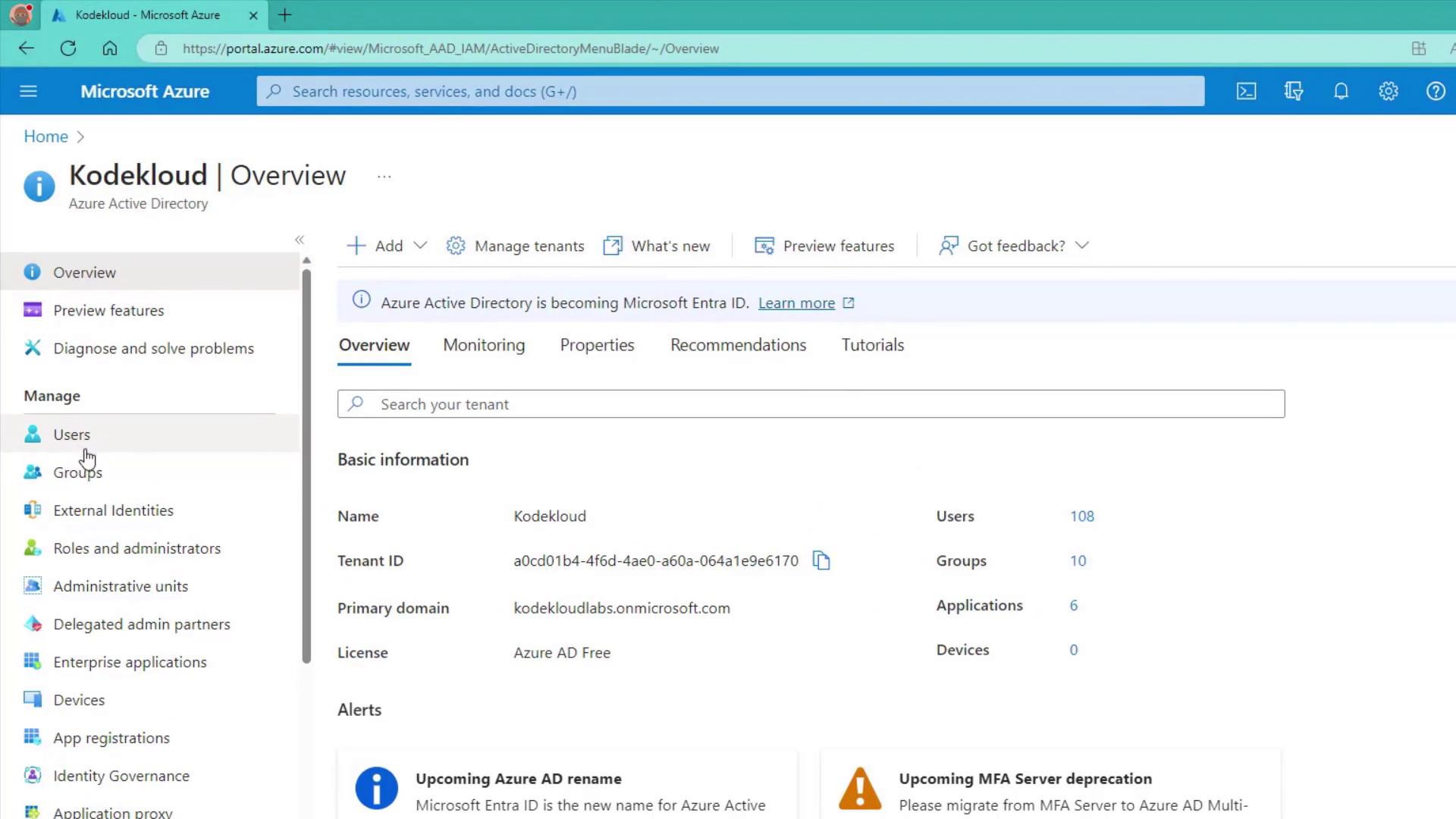
The dynamic membership option may not be available if you do not have the required license. To enable dynamic groups, ensure you have an appropriate P1 or P2 license. In the Azure portal, navigate to Azure Active Directory > Licenses > License features and search for “dynamic” to view available features. New tenants might also activate a free trial (typically 30 to 90 days).
Bulk User Operations
Before testing group features, verify that your tenant contains test users. Bulk user creation is an efficient way to achieve this:- Download Existing Users
In the source tenant, download all user data. If you’re familiar with bulk operations, you can skip the detailed steps; otherwise, follow along.

-
Modify the CSV File
Open the CSV file in Excel and update the User Principal Name (UPN) as needed—using the find and replace tool—to ensure it aligns with the new tenant’s domain. -
Bulk Create Users in the New Tenant
In the new tenant, navigate to Azure Active Directory > Users > Bulk create. Download the provided template and complete the required fields:- Name
- User Principal Name (UPN)
- Initial Password
- Block sign-in (specify whether the account is enabled)
Testing Groups
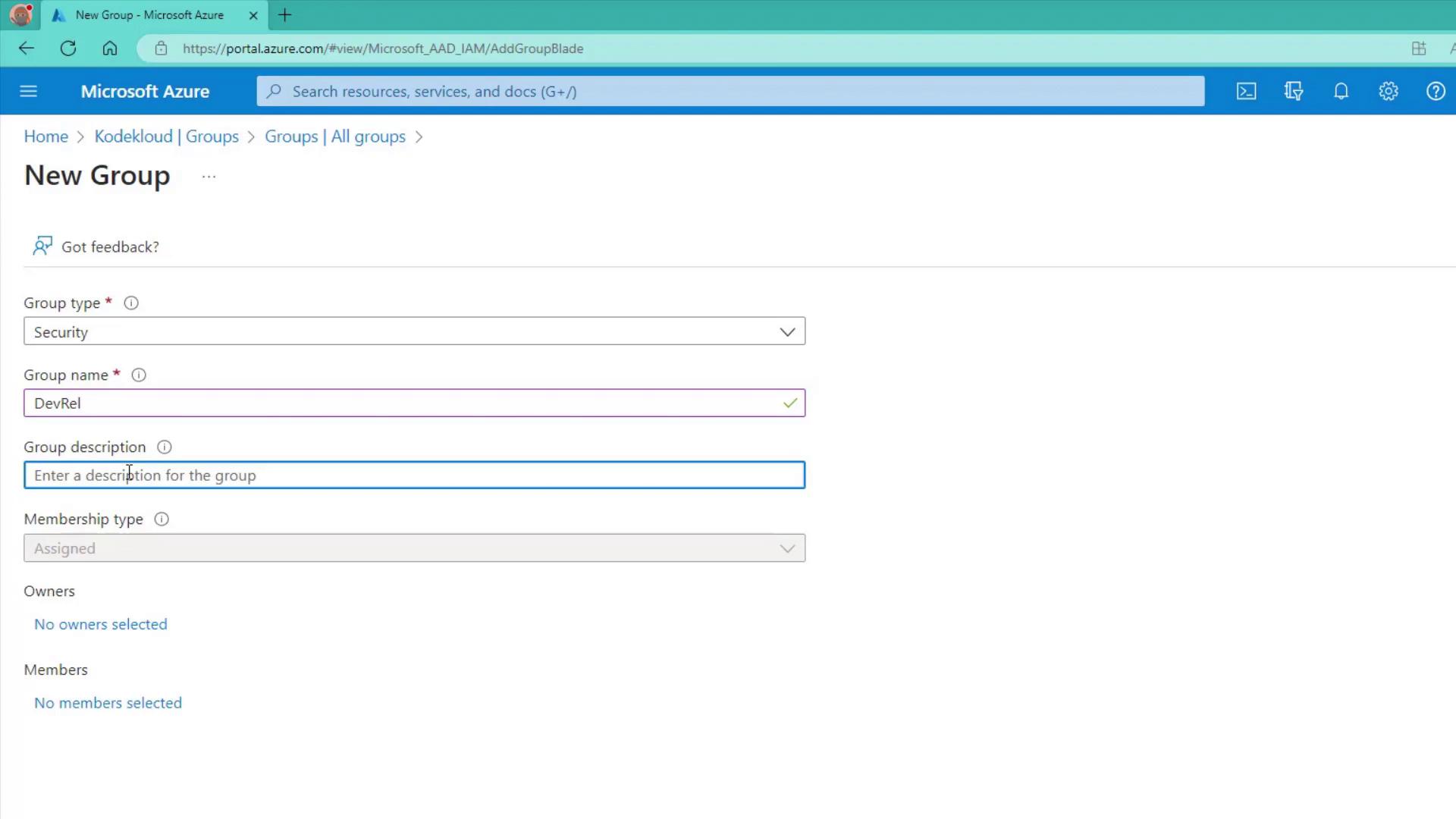
Creating an Assigned Membership Group
- Navigate to Groups in the Azure portal.
- Create a new group with the following details:
- Name: DevRel
- Description: Developer Relations


Creating a Dynamic User Group
Next, create a dynamic Microsoft 365 group called DevRelInfo. This group will include a designated group email address (e.g., devrel@kodekloudlab.onmicrosoft.com) and will use a dynamic membership rule instead of manual additions. Click on the dynamic query option and configure a rule based on user attributes. For example, to include users whose department equals “DevRel,” enter the following expression: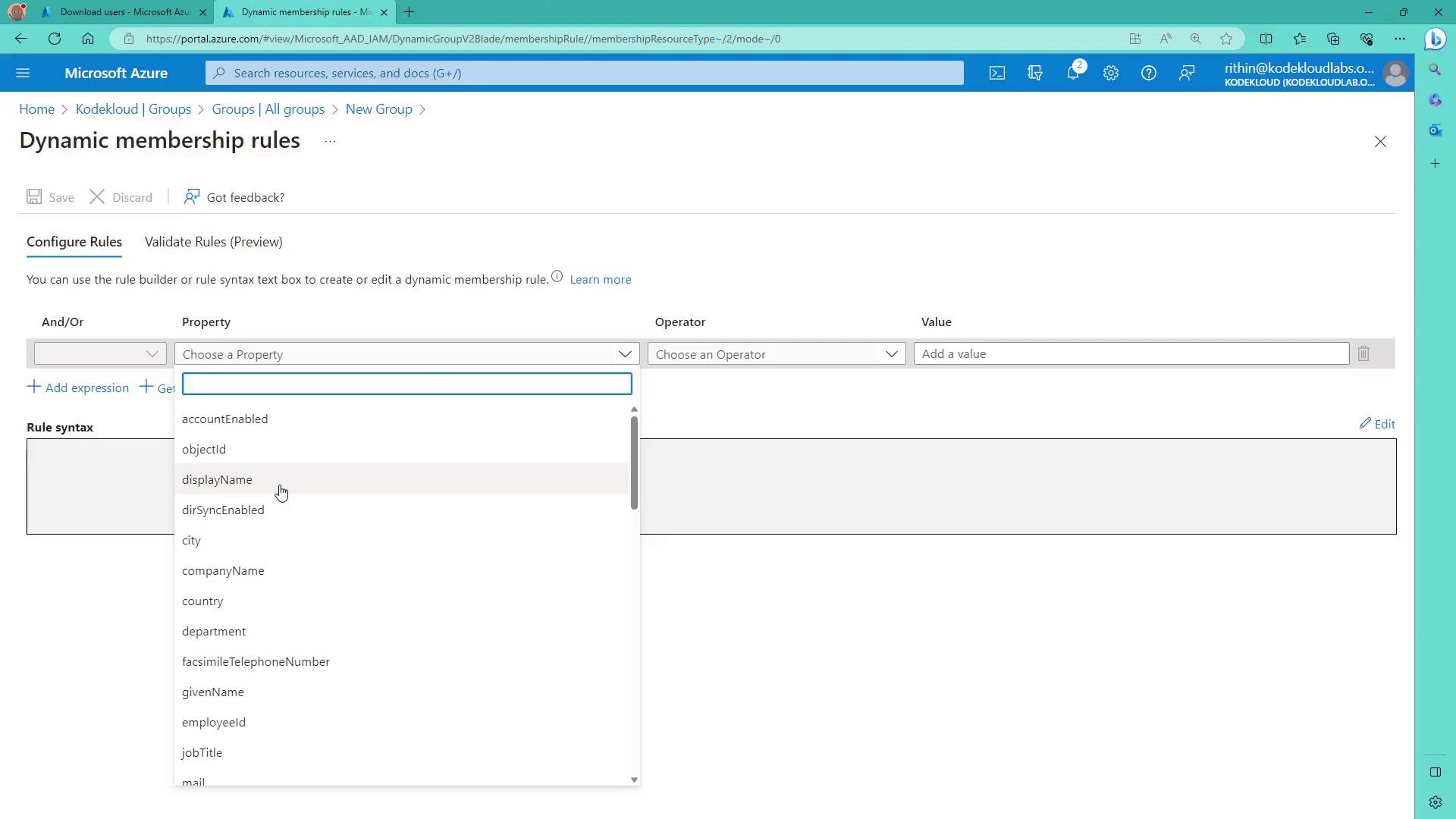
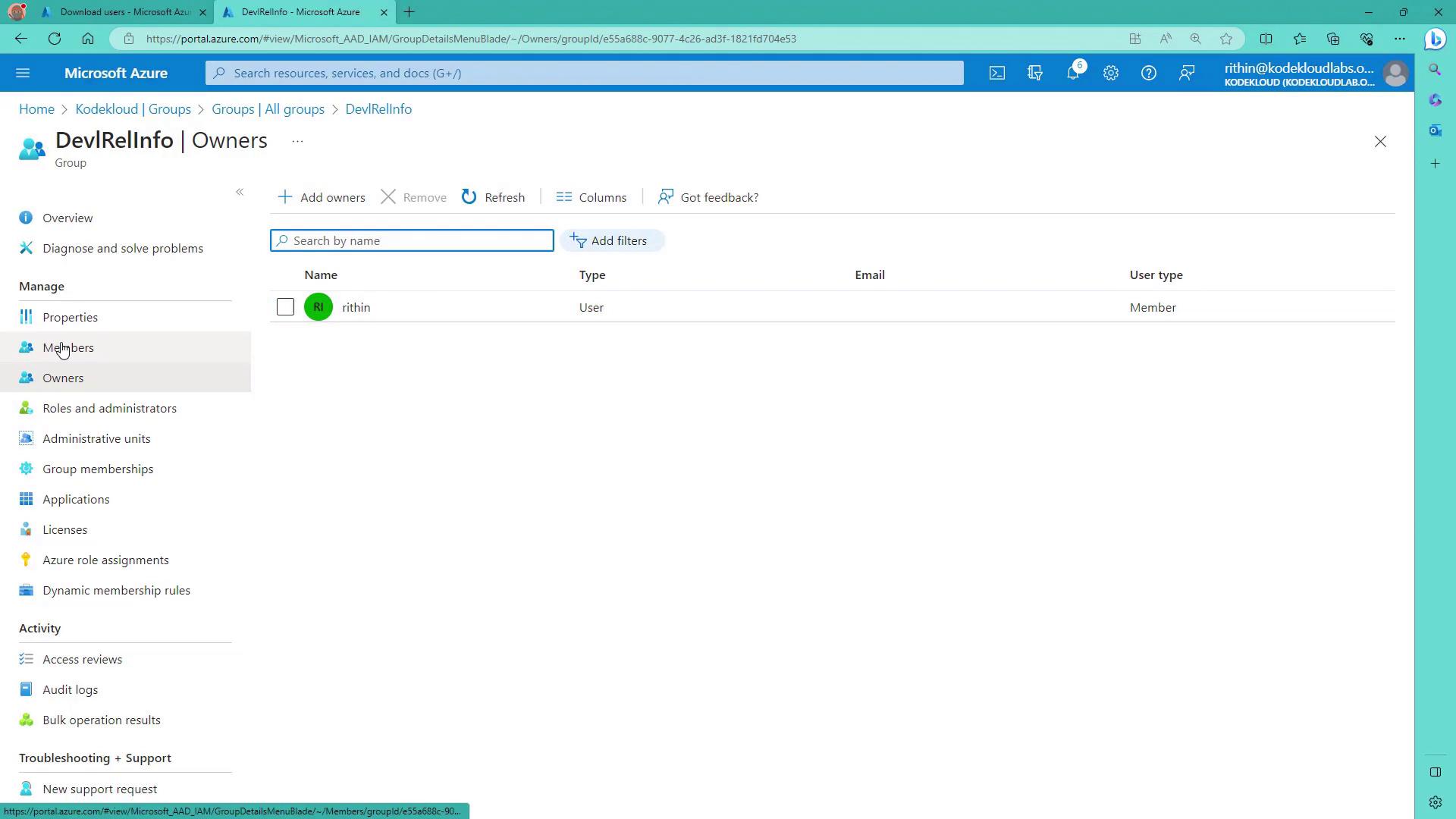
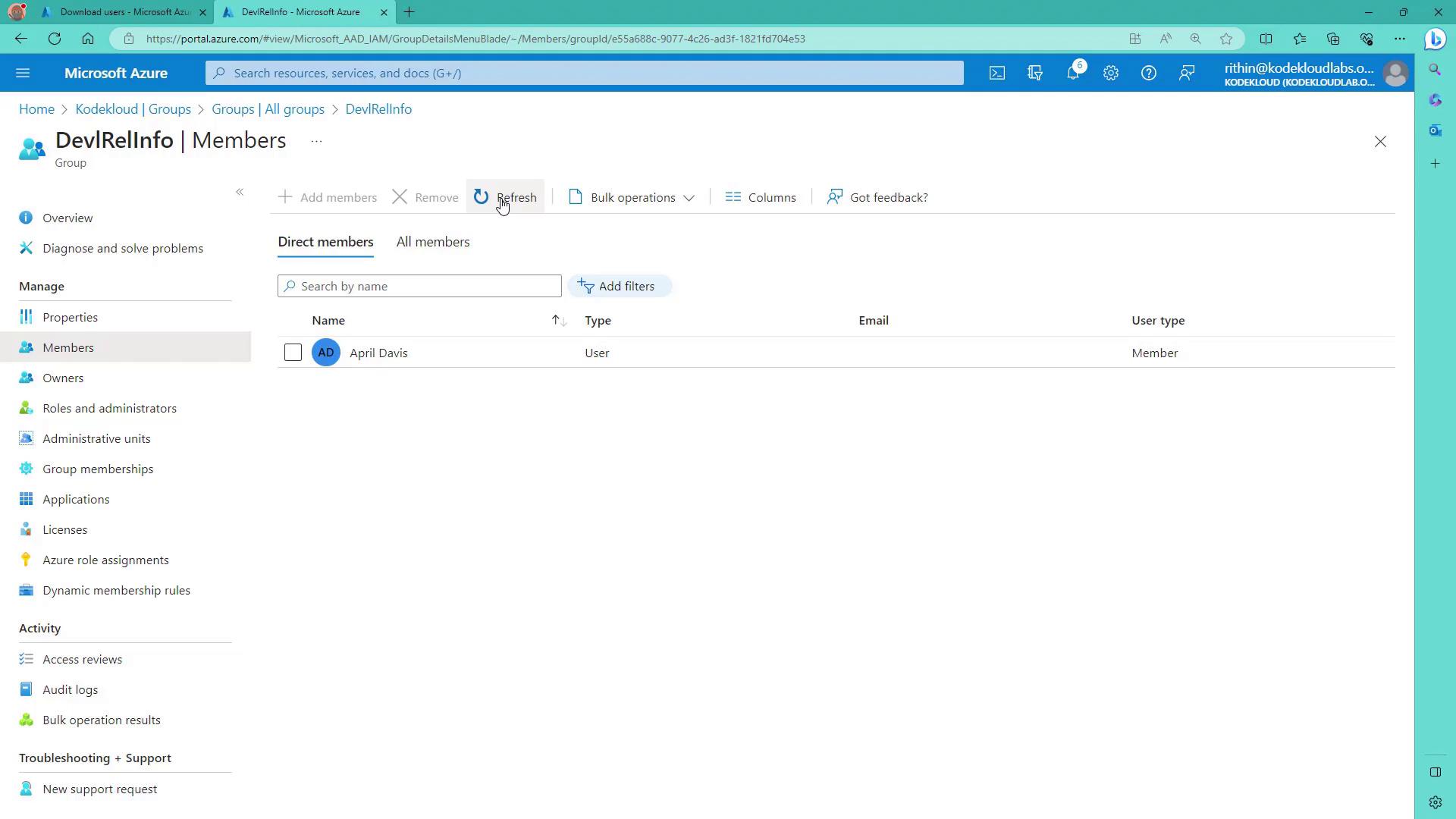
Dynamic Device Groups
Dynamic device groups function in a similar manner to dynamic user groups but use device attributes (such as device model, manufacturer, OS type, and OS version). Note that dynamic device membership is supported only for security groups since devices typically do not require collaborative features.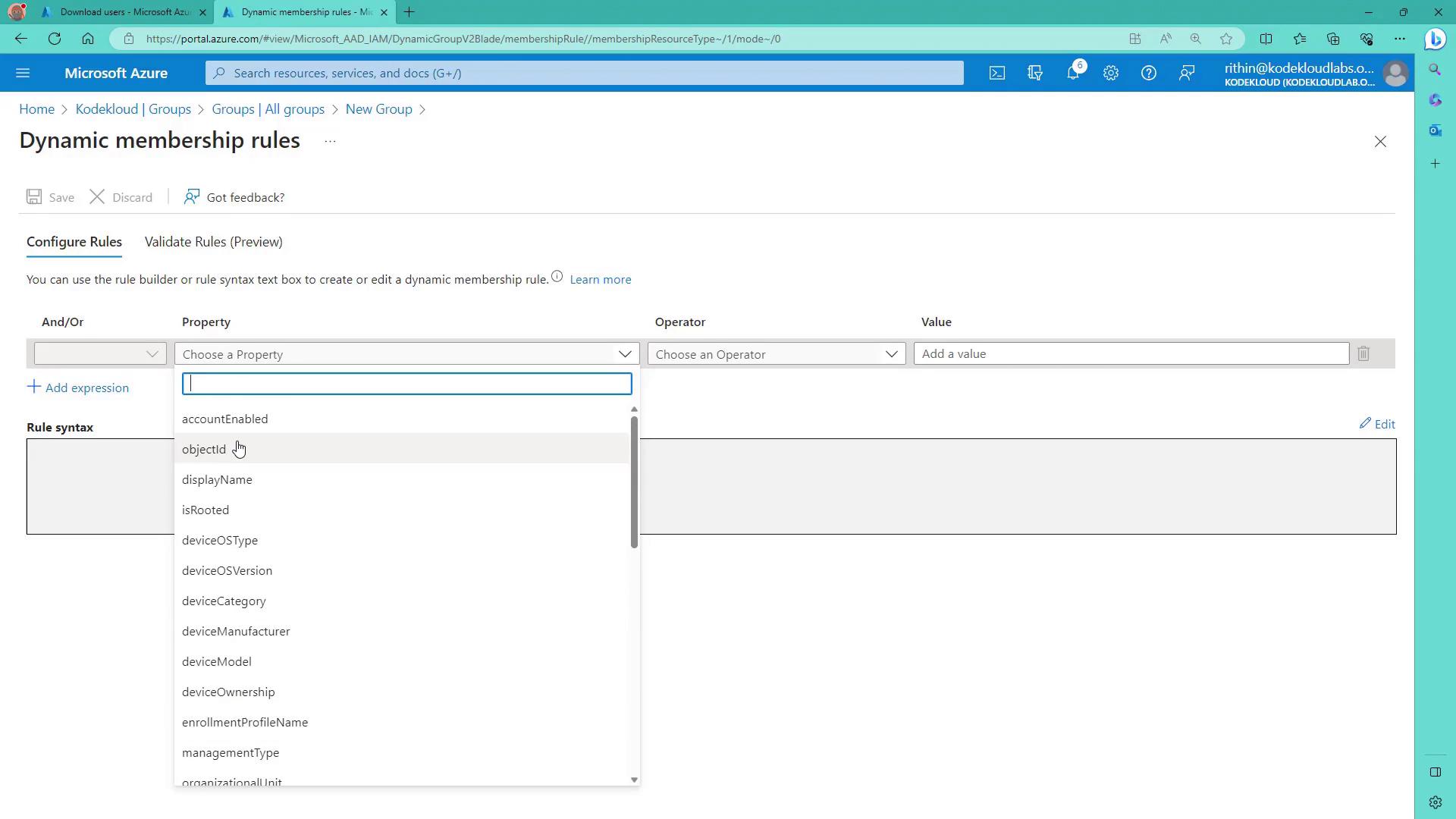
Summary
In this article, we covered the following:- The differences between Security Groups and Microsoft 365 Groups.
- Various group membership options, including assigned, dynamic user, and dynamic device memberships.
- Step-by-step creation, configuration, and validation of groups in the Azure portal using both manual and dynamic membership rules.
- Bulk user operations to facilitate testing of group functionalities.