OpenShift 4
Openshift Security
Secrets Overview
In Kubernetes, Secrets offer a robust way to manage sensitive information such as passwords, connection strings, API tokens, and even simple text messages. Although it might seem unusual to store a casual "hello world" message as a Secret, Kubernetes provides the flexibility to manage any string you choose securely.
Whenever you need to protect sensitive data—like usernames, passwords, or API keys—a Secret is the ideal solution to prevent unauthorized access.
By default, Kubernetes encodes Secrets using base64 encoding. However, this encoding does not encrypt the data. Unless encryption at rest is explicitly configured, these Secrets are stored as plain text in the cluster's etcd datastore. Although data is handled securely during transmission to a Pod, be aware that it may remain unencrypted when stored.
Security Warning
Without additional encryption measures, your base64 encoded data in etcd could be vulnerable. Always consider integrating advanced security solutions for production environments.
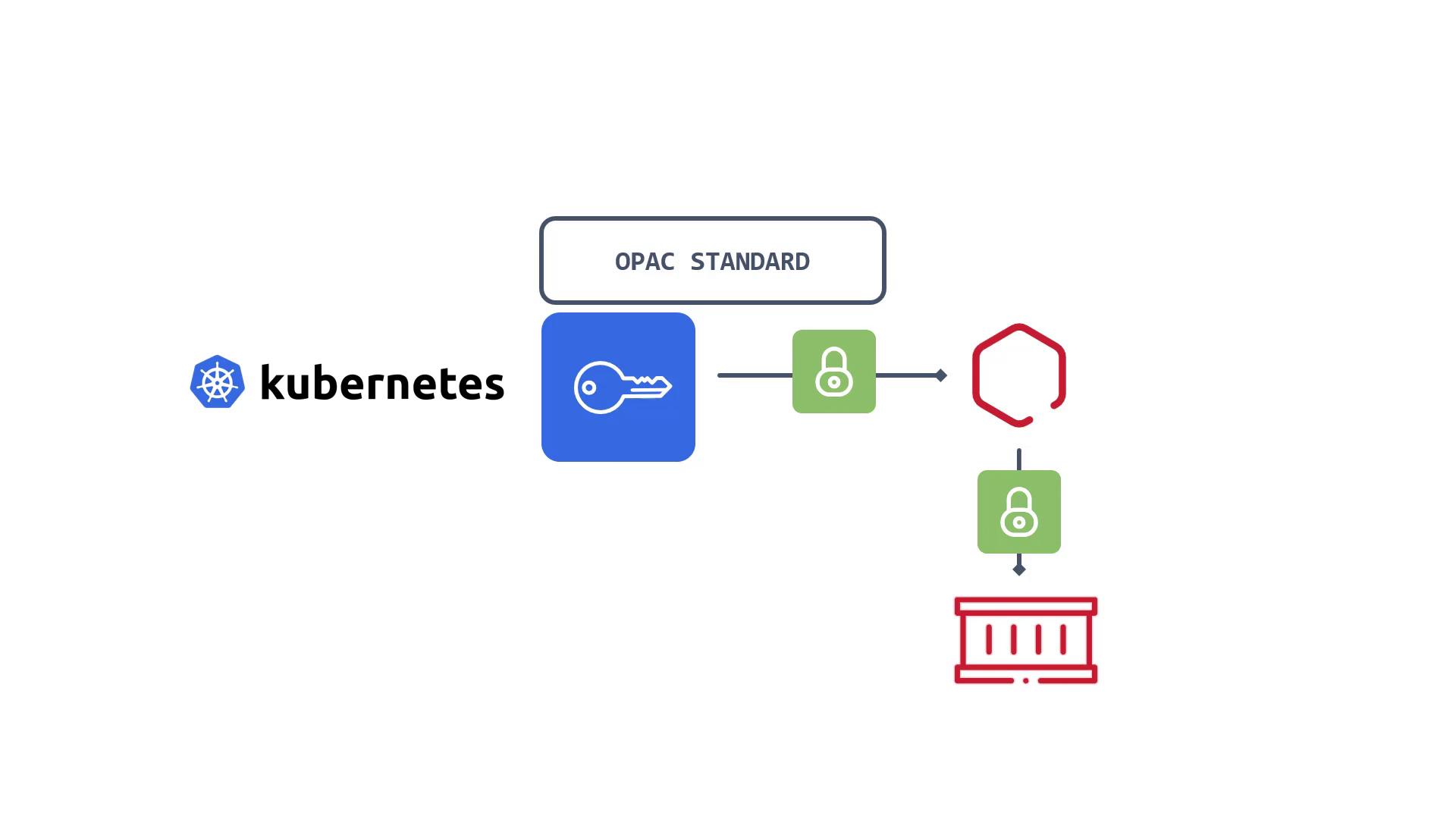
In many production environments, administrators choose to enhance security by leveraging advanced secret management solutions. These may include:
- HashiCorp Vault for dynamic secrets and access control.
- AWS Secrets Manager and Azure Key Vault for cloud-native secret management.
- Managed Kubernetes service tools available in platforms such as AWS EKS and Azure Kubernetes Service.
![]()
Even if your current setup does not require advanced secret management, or if you want to experiment with different security configurations, understanding how to create and use Secrets in Kubernetes is essential.
Demo Overview
In the upcoming demo, we will walk you through the process of creating a Secret and integrating it into your Deployments and Pods. This demonstration will help solidify your understanding of managing sensitive information within your Kubernetes environment.
Watch Video
Watch video content