AWS Certified AI Practitioner
Security Compliance and Governance for AI Solutions
Best Practices for Secure Data Engineering
In this lesson, we explore secure data engineering with best practices that help maintain security and data integrity in cloud environments. We focus on key AWS services and techniques tailor-made for data engineering, ensuring both practical applications and exam readiness.
Overview
This lesson covers secure cloud configurations, data privacy, network security, and access controls, ensuring robust protection for sensitive data and compute resources.
Our agenda includes:
- Secure cloud configurations using Virtual Private Clouds (VPCs)
- Data privacy assurance with tools like Amazon Macie
- Effective access controls using AWS Identity and Access Management (IAM)
- Data integrity practices including encryption, version control, and auditing
- Evaluating data quality for Machine Learning (ML) models
Securing Compute Resources and Cloud Infrastructure
To secure compute resources, leverage Virtual Private Clouds (VPCs) to isolate your workloads. For example, Amazon Macie scans S3 buckets for PII, while SageMaker security is enhanced by managing access permissions. AWS also offers robust auditing tools like CloudTrail and firewall configurations to ensure a secure environment.
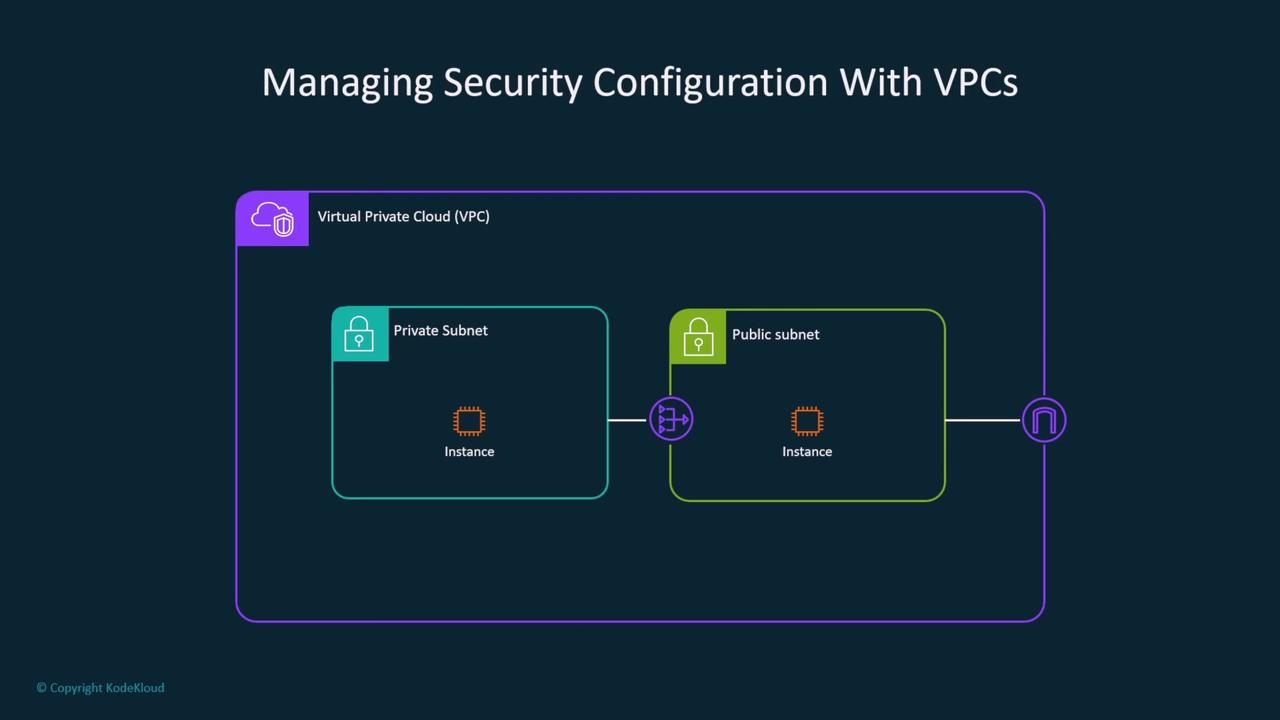
Securing Cloud Infrastructure with VPCs
When configuring a VPC, it is best practice to deploy instances within private subnets. Follow these guidelines:
- Configure instance-level firewalls (security groups) and network-level firewalls (network access control lists).
- Utilize VPC interface endpoints to privatize traffic, enforce encryption, or establish secure VPN or Direct Connect links using MACsec.
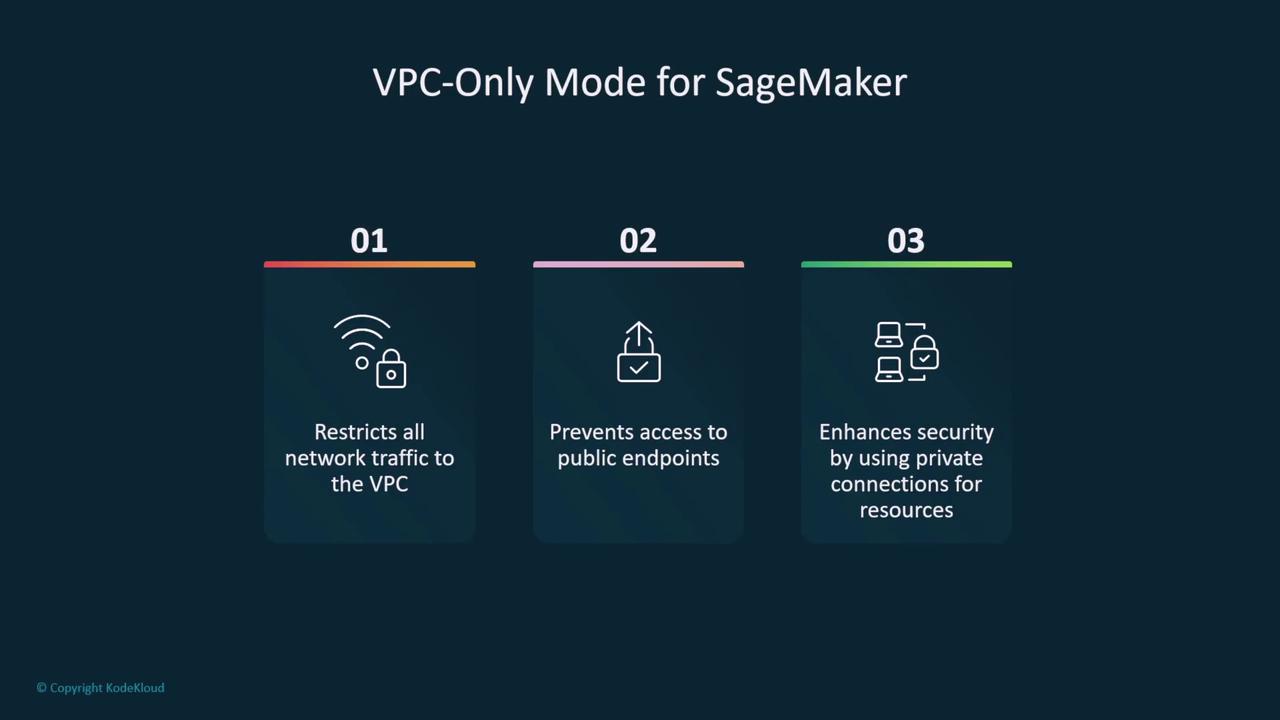
- Always select a private subnet with an appropriate security group for launching SageMaker notebooks to restrict direct internet access.
Ensure network access control lists (ACLs) work in tandem with security groups. VPC endpoints help maintain traffic on the AWS backbone, reducing exposure to the public internet.
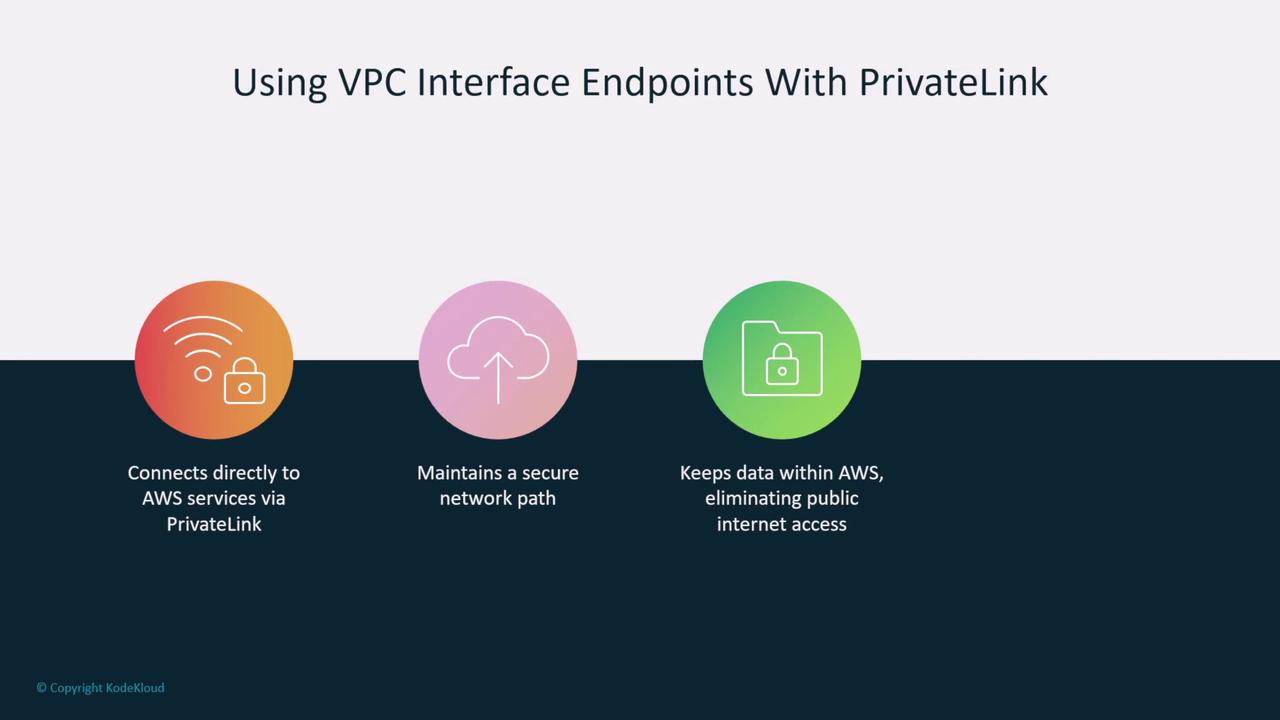
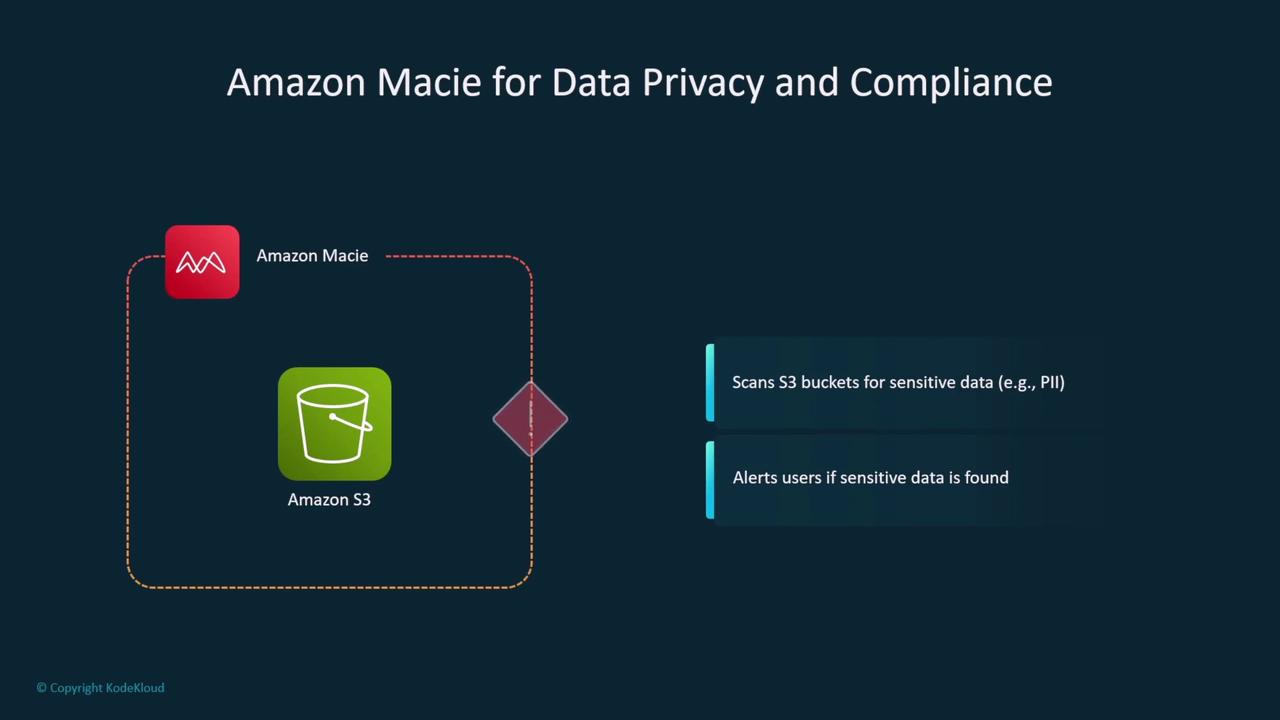
Data Privacy and PII Protection
For robust data privacy, especially when handling sensitive information, use Amazon Macie to scan for PII in your S3 buckets. Configure AWS Config to trigger additional preventative actions—like locking a bucket when PII is detected—ensuring continuous compliance and data protection.
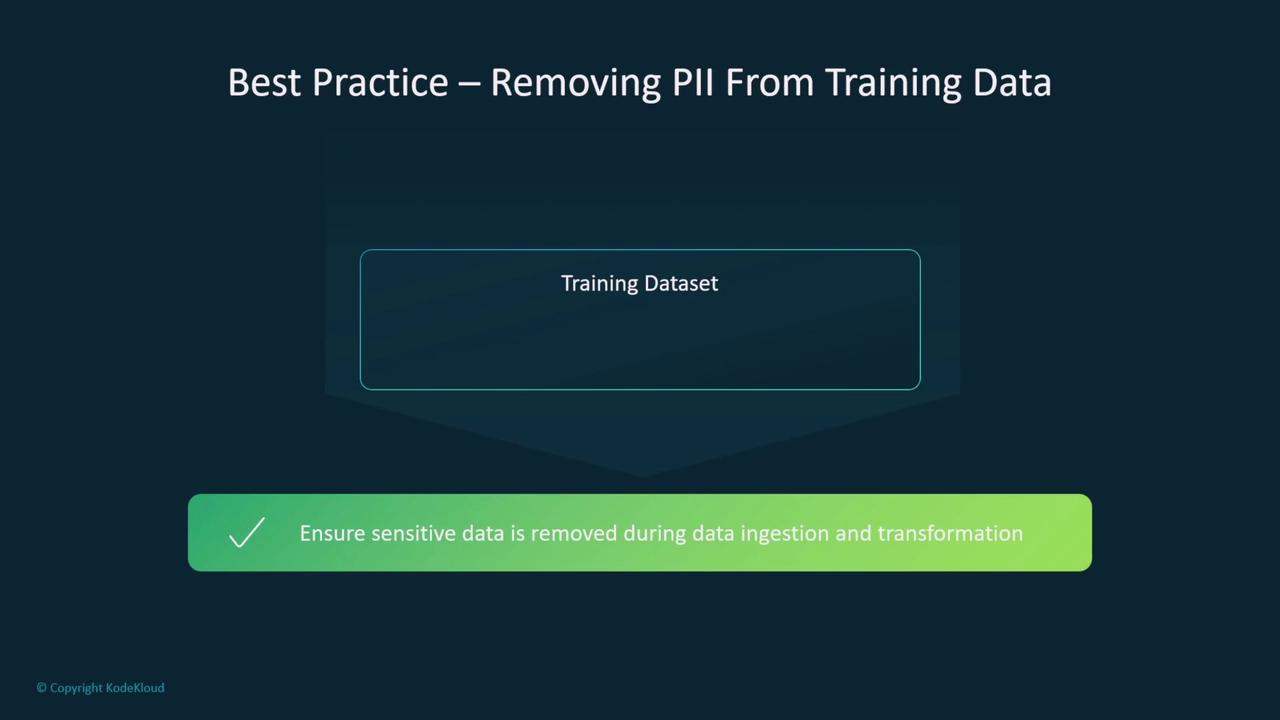
When preparing training datasets or performing feature engineering, remove any Personally Identifiable Information (PII) unless required. Secure data processing during ingestion and transformation minimizes the risk of exposing sensitive information.


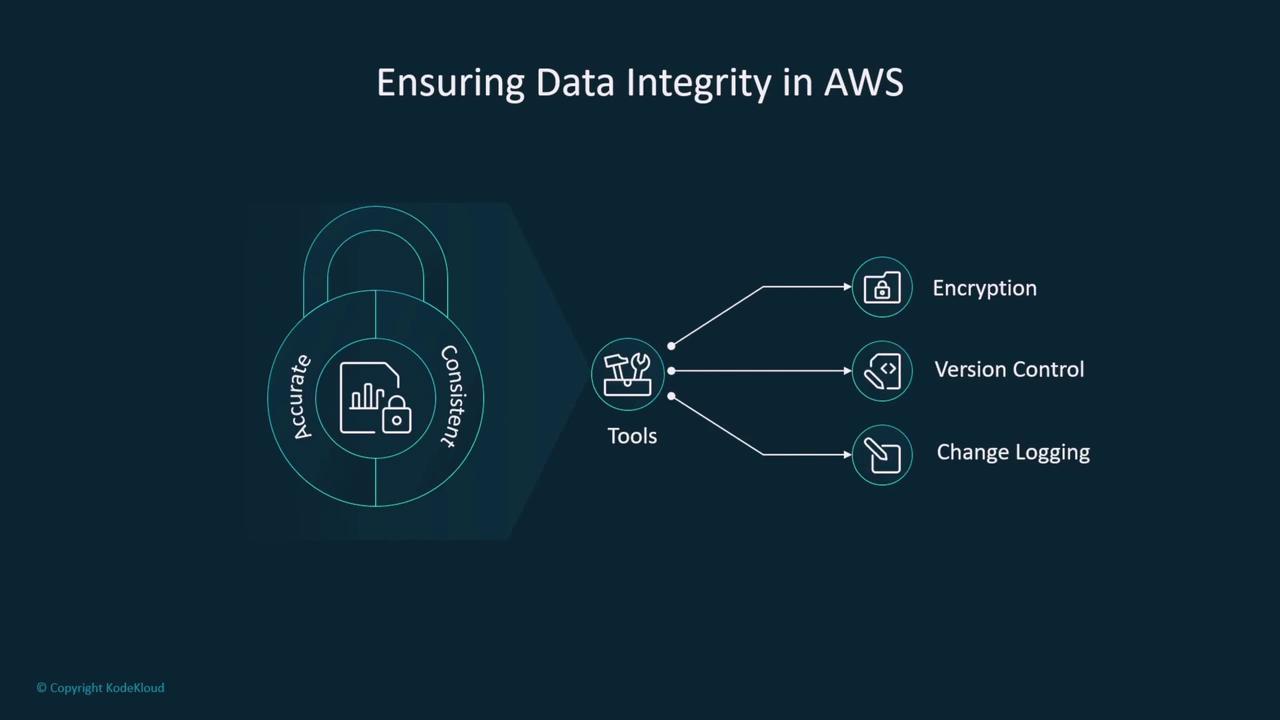
Access Control and Data Integrity
Implement robust access controls using AWS IAM to manage users, groups, roles, and permissions. Combined with security groups and network ACLs, IAM ensures that only authorized personnel have access to critical data and services.
To secure data integrity on AWS, use encryption, version control, and detailed auditing via change logging. These measures help maintain accurate and consistent data, which is essential for training ML models and supporting data-driven operations.
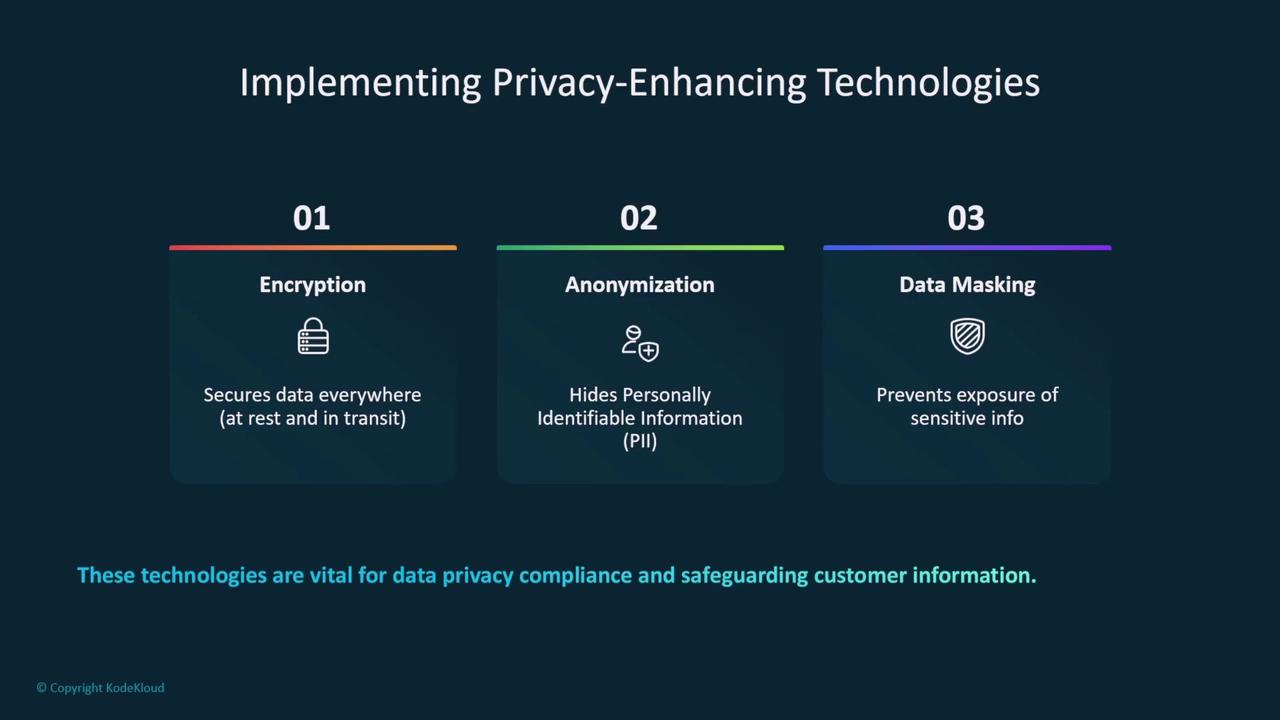
Additional measures to enhance data privacy include:
- End-to-End Encryption
- Data Anonymization
- Data Masking
These privacy-enhancing technologies offer an extra layer of security, ensuring that sensitive information is accessible only to authorized users.
Assessing Data Quality for Machine Learning
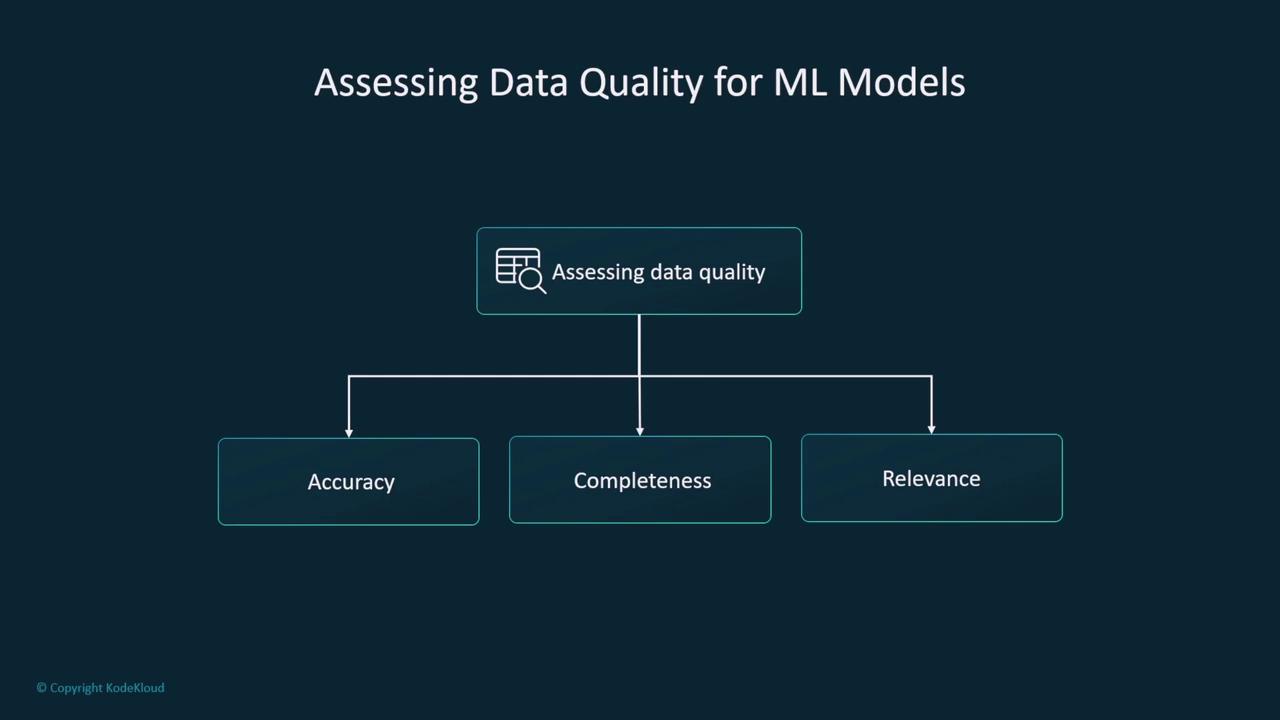
High data quality is fundamental to the success of ML models, including Generative AI in Practice: Advanced Insights and Operations. Consider these quality metrics:
| Data Quality Metric | Description | Importance |
|---|---|---|
| Accuracy | Data reflects the correct values | Avoids bias in ML outcomes |
| Completeness | All required data is present | Ensures comprehensive model training |
| Relevance | Data is applicable to the problem | Focuses on significant features |
Make sure your data is error-free, properly formatted, and free from missing or disproportionate values that might skew results.
Conclusion
By implementing these best practices for secure data engineering on AWS—from secure network configurations and access controls to robust data privacy and integrity measures—you can elevate the security of your data environment. These strategies not only secure your infrastructure but also ensure that your data remains reliable and compliant at every stage.
We look forward to deepening our exploration of secure and efficient cloud data practices in our next lesson.
Watch Video
Watch video content