AWS Certified SysOps Administrator - Associate
Domain 4 Security and Compliance
Demo Exploring the VPCs Security Groups and NACLs
Welcome to this lesson. In this session, Michael Forrester guides you through the key aspects of AWS VPC configurations along with their security components. You’ll learn about lab VPC settings, the difference between stateless Network ACLs and stateful Security Groups, and how these elements interact to secure AWS environments.
Lab VPC Overview
Our lab uses a specifically provisioned VPC—not the default one—with the CIDR block 10.0.0.0/16. This means the first two octets (10.0) define the network portion, while the rest designate hosts.
Below is an image of the AWS VPC dashboard displaying essential details like VPC ID, state, and IP address ranges:
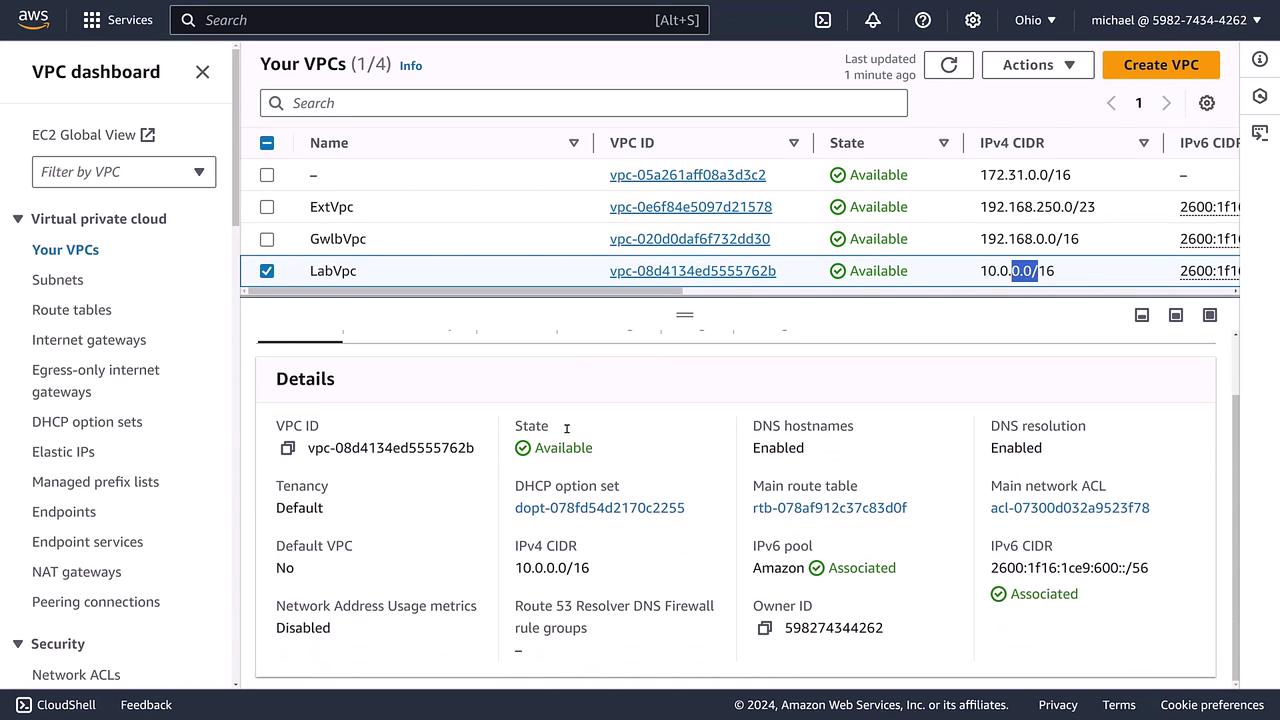
Key configuration points include:
- IPv4 addressing per the defined CIDR block.
- Optional IPv6 addressing with a dedicated pool.
- Features such as DNS hostnames, default shared tenancy, and DHCP configurations.
- A primary route table and an associated access control list (ACL) for security management.
In this lesson, our focus is on security, specifically the Network ACLs (NACLs) and Security Groups tied to this VPC.
Network ACLs in the VPC
Within the lab VPC, a Network ACL is linked with eight subnets. Acting as a rule-based firewall at the subnet level, these ACLs process rules sequentially from highest to lowest priority. By default, the inbound rules permit all IPv4 and IPv6 traffic using explicit allow rules that conclude with a deny rule.
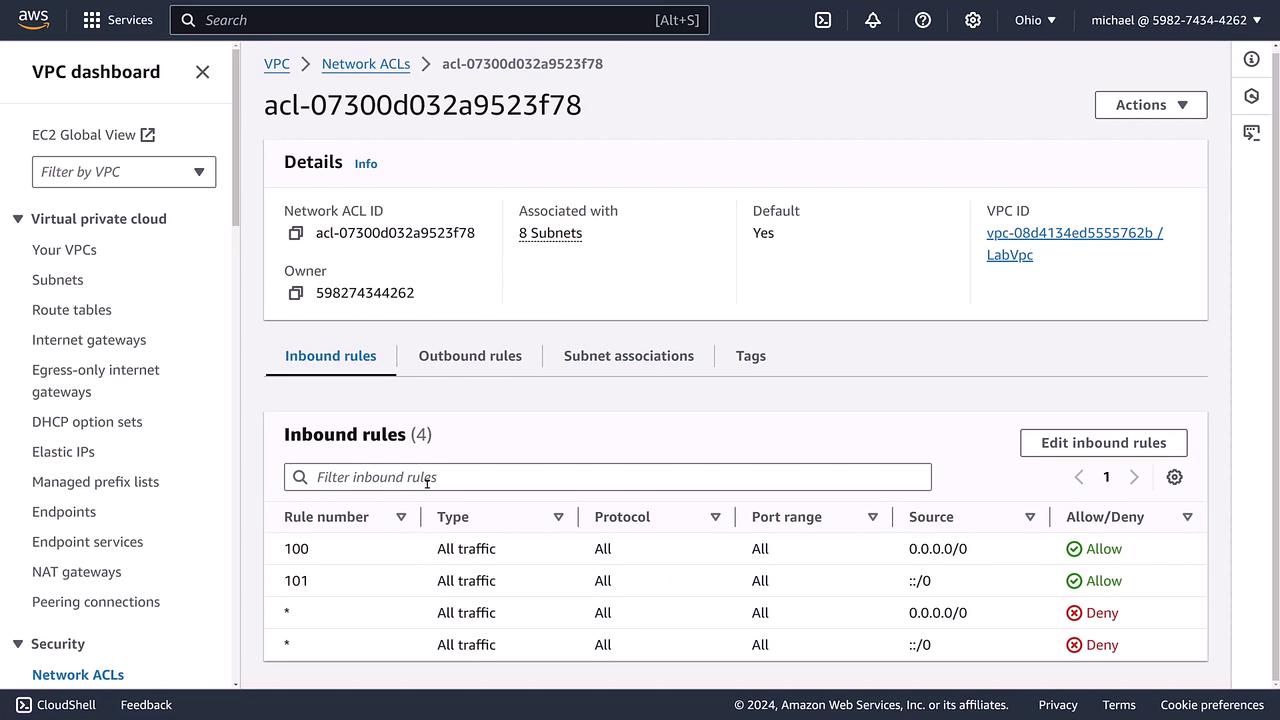
You can modify these ACLs to tailor traffic control. For example, to restrict access to a web server, you might add deny rules for specific source IP addresses. Typically, each inbound rule is paired with a corresponding outbound rule to manage the return traffic.
The following image displays the outbound rules for the ACL, which similarly outline permissions with both allow and deny entries:
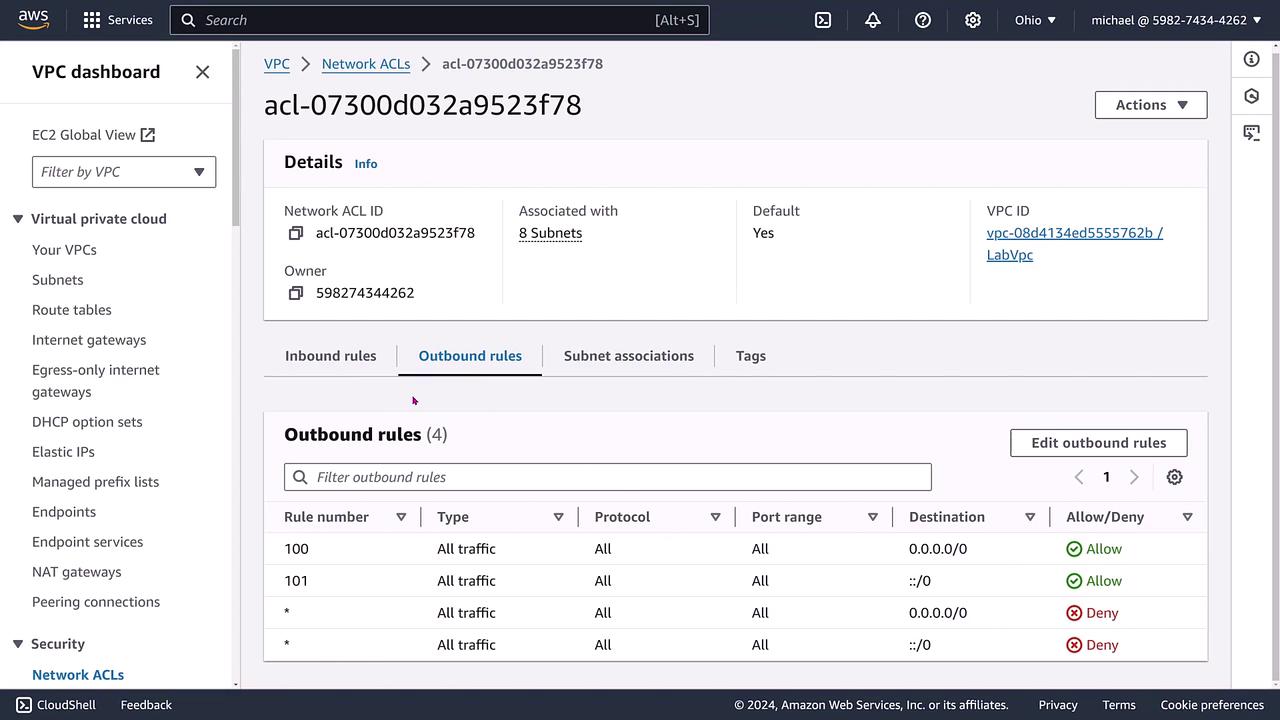
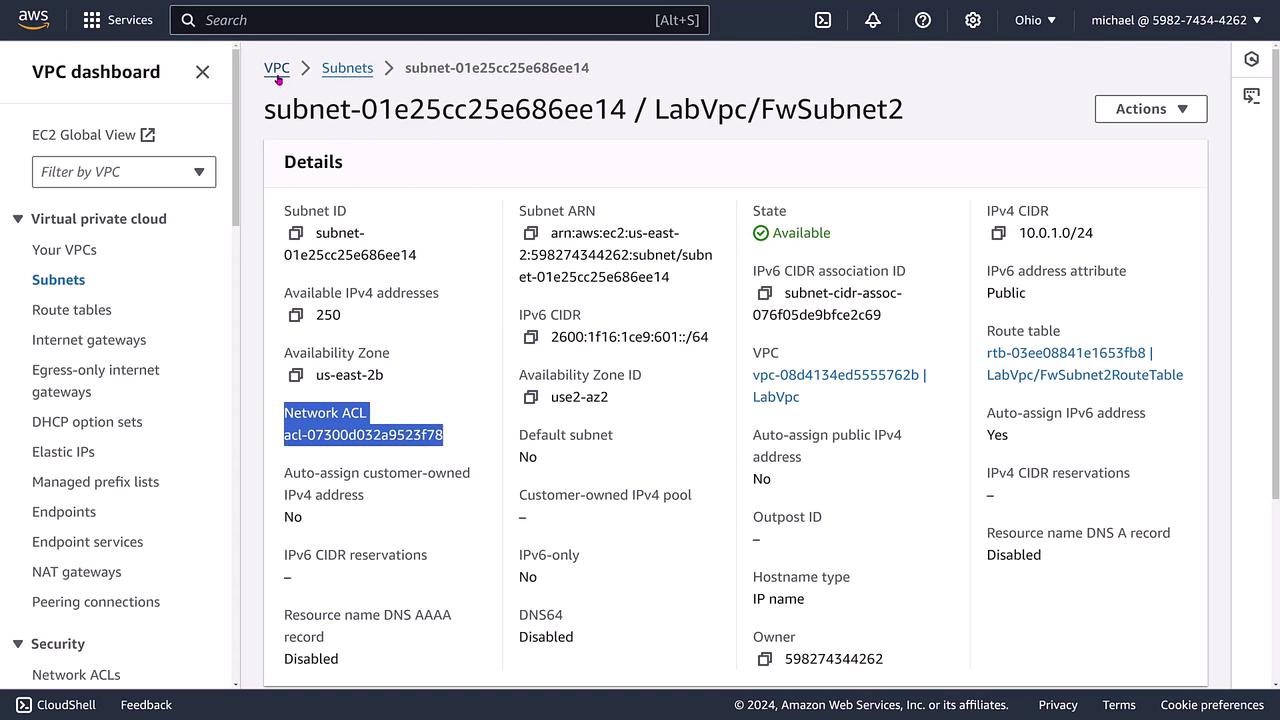
Additionally, you can review the network ACL’s subnet associations. In our lab setup, these include public, private, and endpoint subnets. While subnets typically inherit the VPC's default ACL, you have the option to assign a different ACL to an individual subnet.
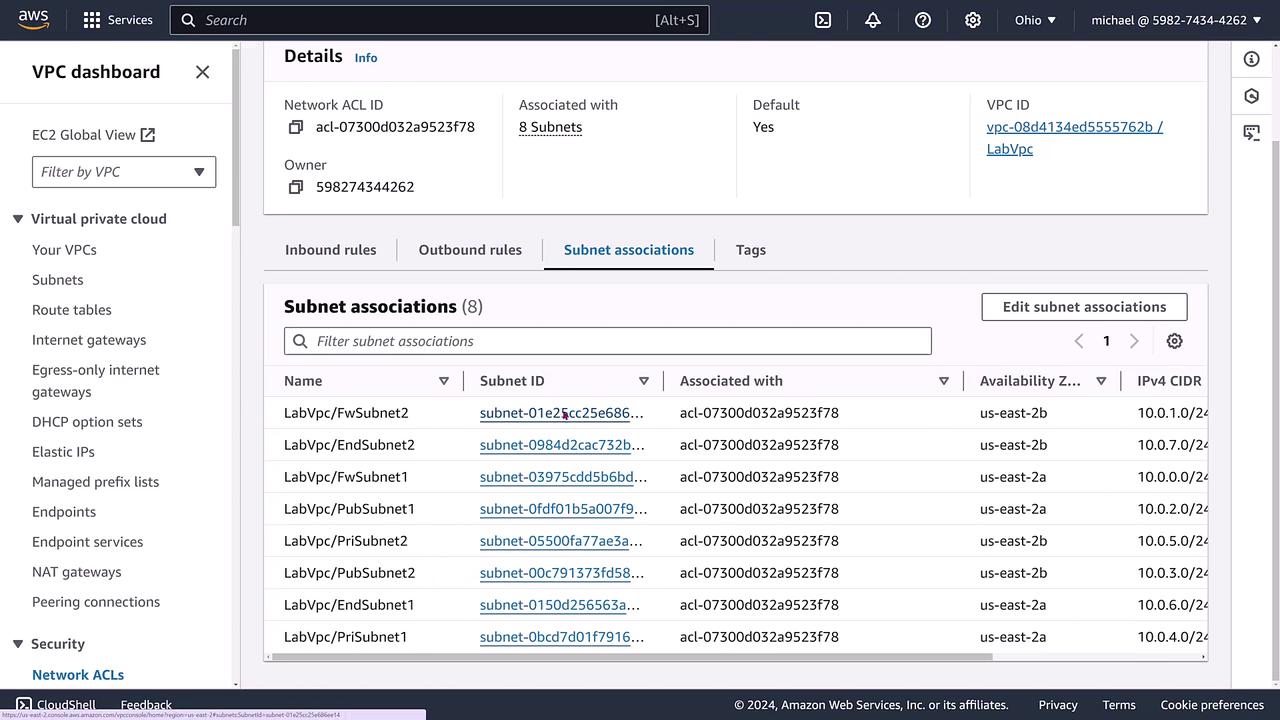
The image below highlights the details of a specific subnet and its associated ACL:
Tip
Remember, Network ACLs are stateless, so rules must be defined separately for inbound and outbound traffic.
Security Groups: The Stateful Firewall for EC2 Instances
Security Groups serve as stateful firewalls for EC2 instances and other AWS resources. They automatically track connection states, meaning that once an inbound request is allowed, the corresponding outbound response is automatically permitted.
Consider these aspects of security groups:
- By default, all traffic is denied unless explicitly allowed.
- A security group might, for example, allow inbound HTTP requests while enabling outbound HTTP and HTTPS traffic.
- Even if an outbound rule is removed, statefulness ensures that legitimate inbound connections can still receive a response.
The image below shows a Security Group in the AWS Management Console with its outbound rules configured for HTTP and HTTPS protocols:
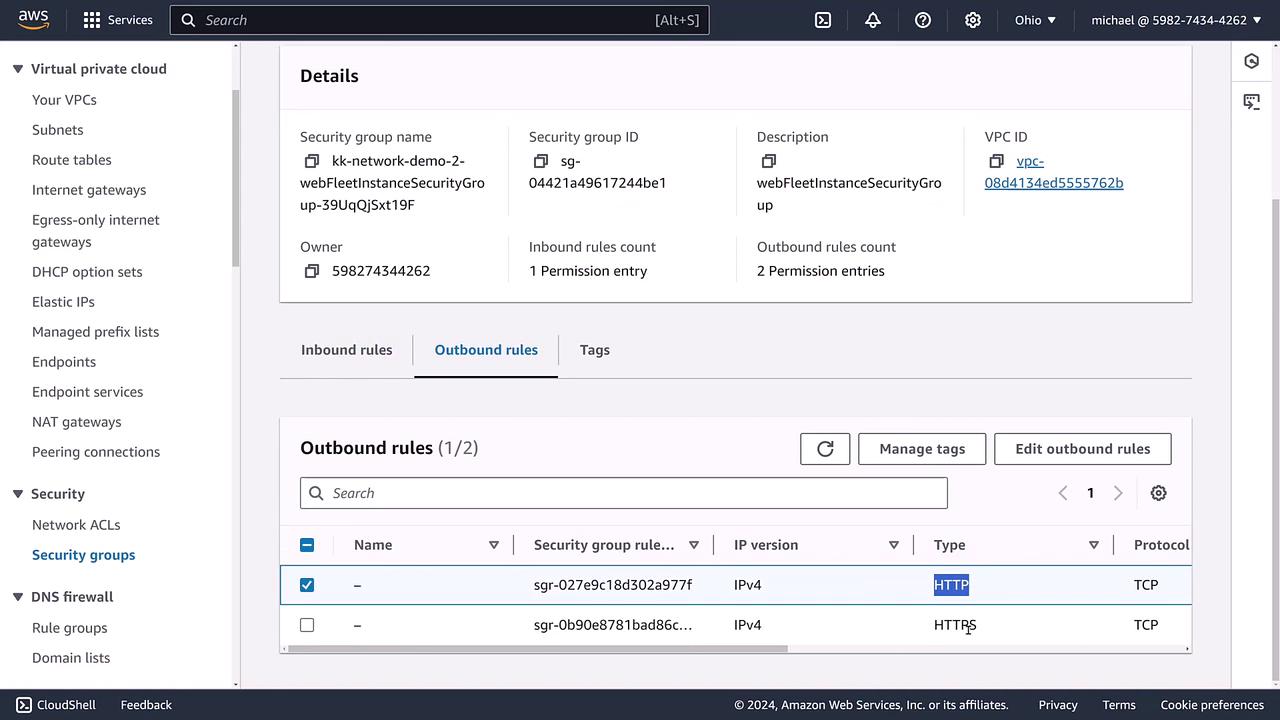
Security Groups are attached directly to network interfaces across various AWS services such as EC2, RDS, EMR, Lambda, and even VPC endpoints. Unlike ACLs, which are applied at the subnet level, Security Groups are assigned on a per-resource basis. Notably, an EC2 instance can be associated with multiple security groups.
Key Takeaway
- Network ACLs: Stateless and applied to subnets.
- Security Groups: Stateful and applied to individual network interfaces.
Summary
This lesson provided an overview of the interaction between VPCs, subnets, and their security configurations:
- VPCs form the backbone of your network infrastructure.
- Network ACLs are stateless firewalls that require explicit inbound and outbound rules at the subnet level.
- Security Groups are stateful firewalls that simplify traffic management on individual resources.
Understanding these distinctions is essential to effectively managing and securing your AWS infrastructure. For more detailed information on AWS networking, consider exploring the AWS Documentation.
Happy learning, and we’ll see you in the next lesson!
Watch Video
Watch video content
Practice Lab
Practice lab