Table of Contents
- Prerequisites
- Accessing AWS Config
- Configuring AWS Config
- Adding a Managed Rule
- Deploying a PCI DSS Conformance Pack
- Reviewing Compliance Results
- References
Prerequisites
- An AWS account with administrative or Config-related IAM permissions
- A designated S3 bucket for storing configuration snapshots
- Region set to US East (Ohio) (us-east-2)
Enabling AWS Config may incur charges for configuration recordings, S3 storage, and conformance pack evaluations. Review the AWS Config Pricing page before proceeding.
1. Accessing AWS Config
- Sign in to the AWS Management Console.
- In the search bar, type Config and select AWS Config.
- Confirm your region is US East (Ohio) (us-east-2).
- Click Config. If AWS Config isn’t set up yet, you’ll see the setup dashboard.
2. Configuring AWS Config
On General settings, choose All current and future resource types supported in this region. This enables comprehensive tracking.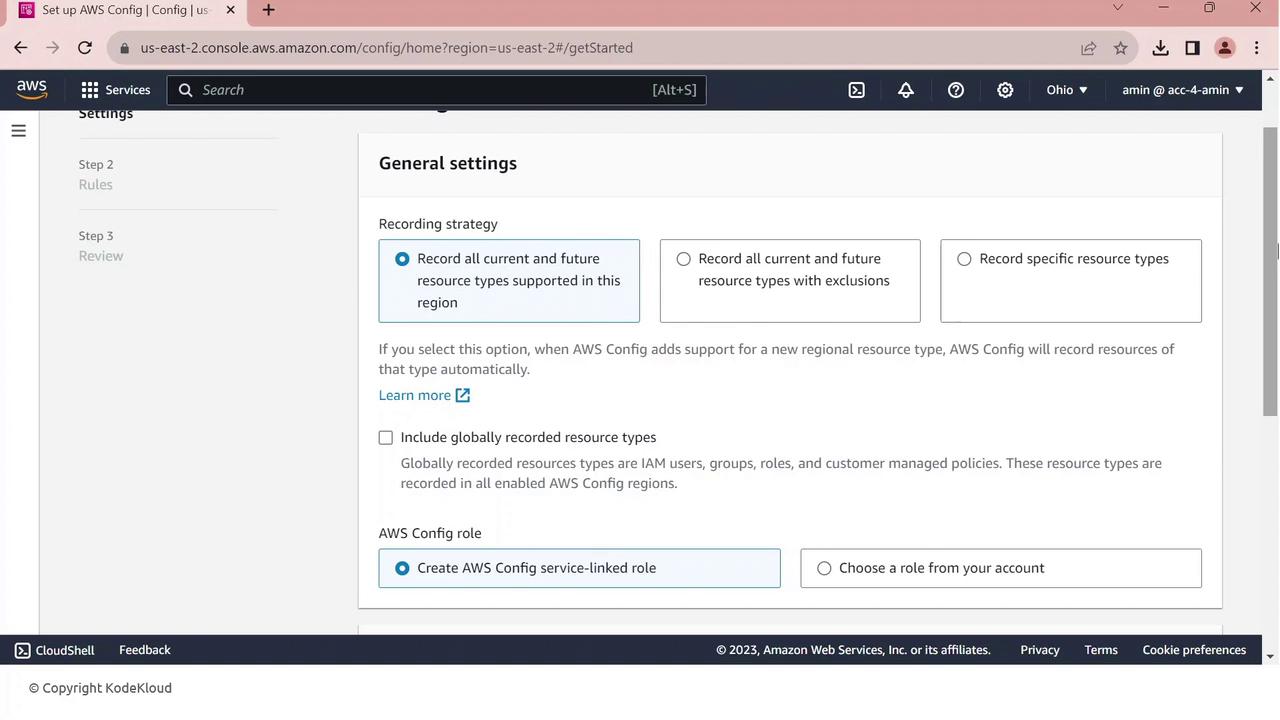
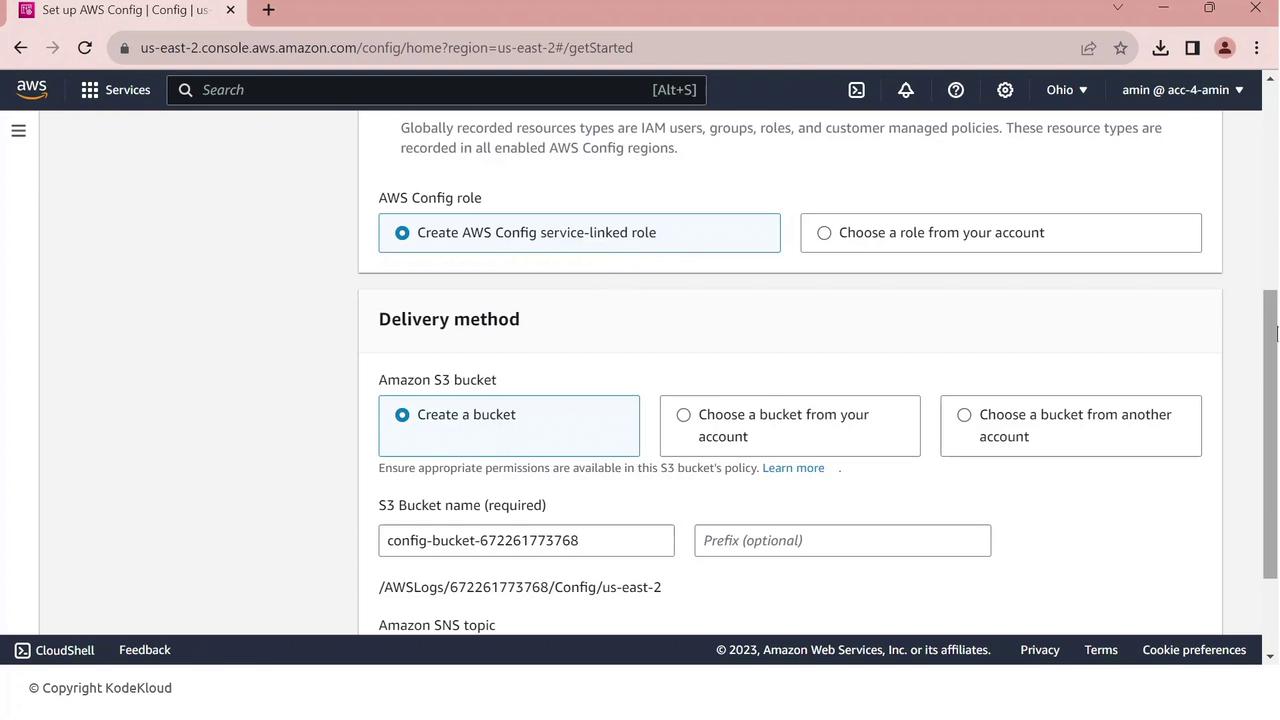
- S3 bucket: to store configuration snapshots and compliance histories
- IAM role: AWS Config uses this to write data to your bucket
3. Adding a Managed Rule
AWS Config includes a library of managed rules to enforce best practices. Let’s add the restricted-ssh rule:- In the console, go to Rules.
- Search for restricted-ssh—this rule ensures no security group permits 0.0.0.0/0 on port 22.
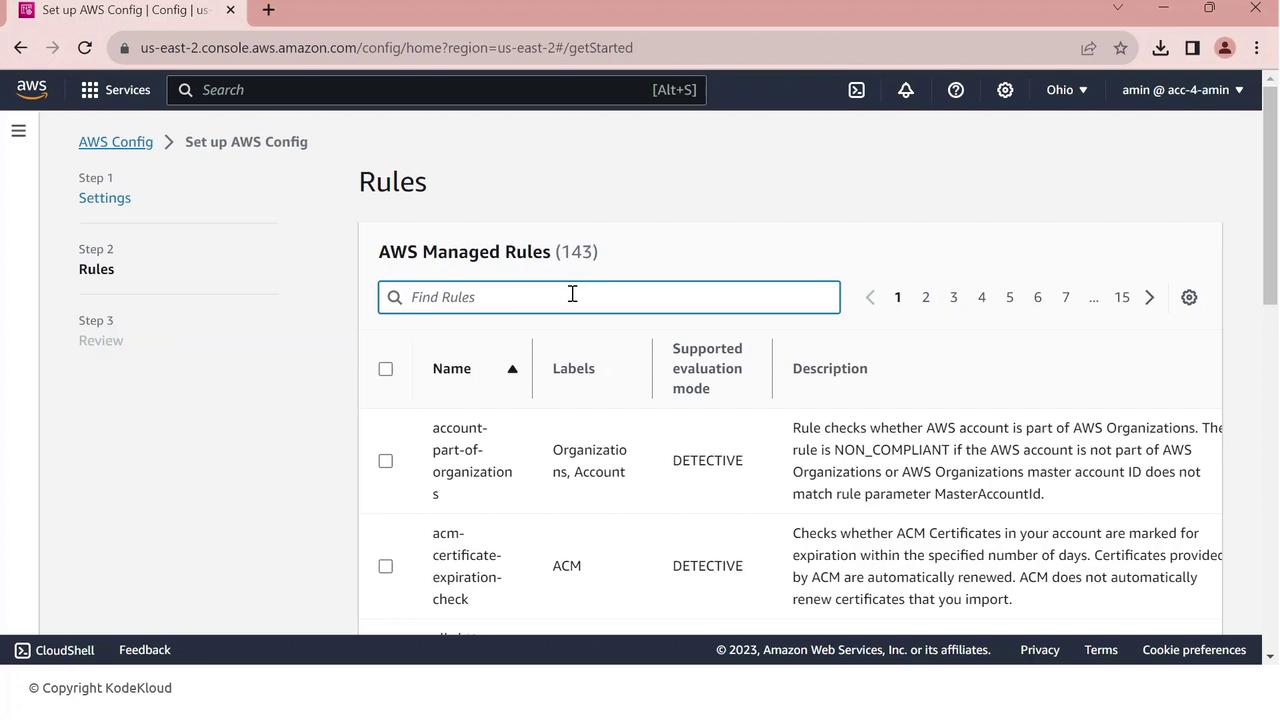
- Select restricted-ssh and click Next.
- Review the parameters and click Confirm.
4. Deploying a PCI DSS Conformance Pack
To scale compliance checks against PCI DSS requirements, deploy the AWS–provided conformance pack:- In AWS Config, navigate to Conformance packs.
- Click Deploy conformance pack.
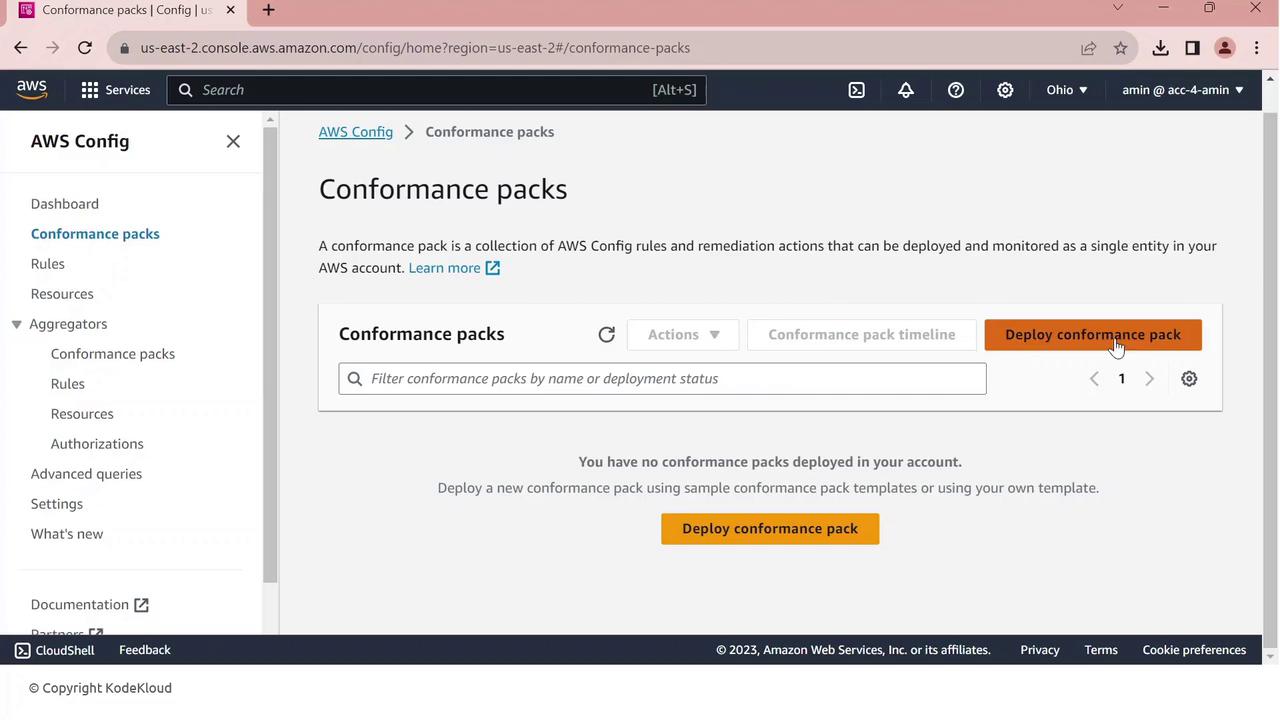
- Choose Use a sample template.
- From the dropdown, select Operational Best Practices for PCI DSS.
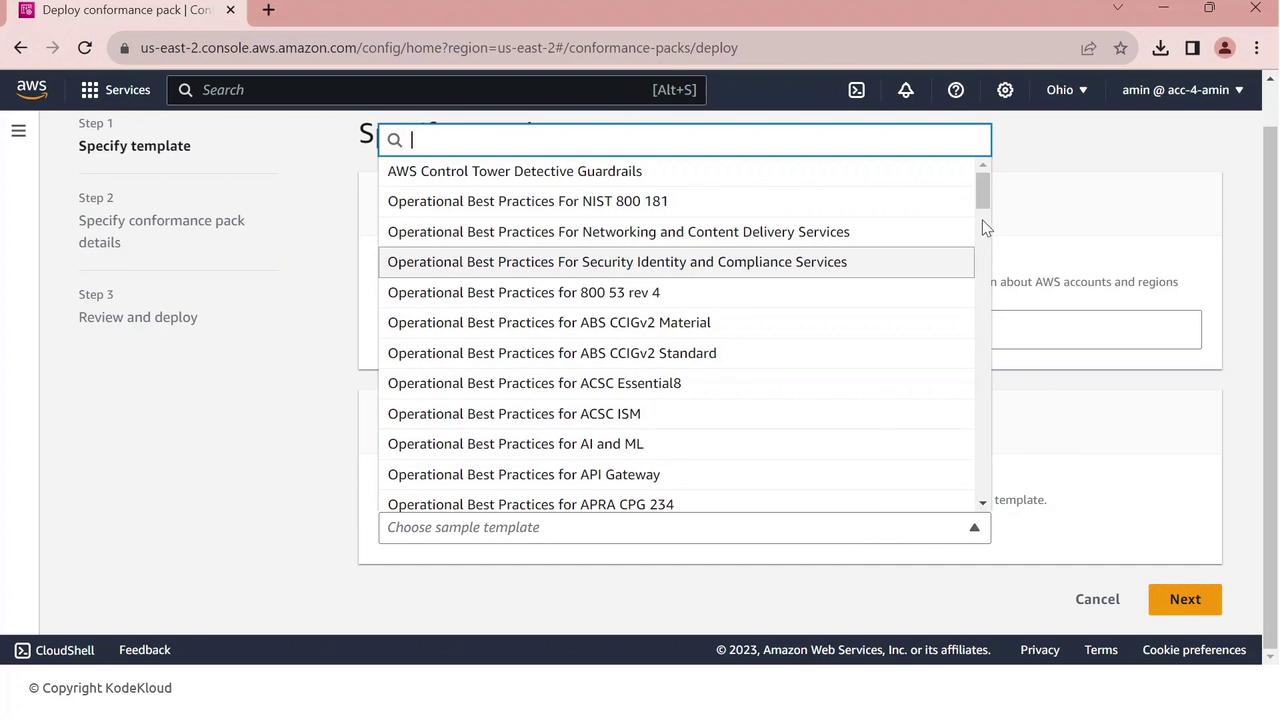
- Click Next, give your pack a name (e.g.,
PCI-Conformance-Pack), and proceed.
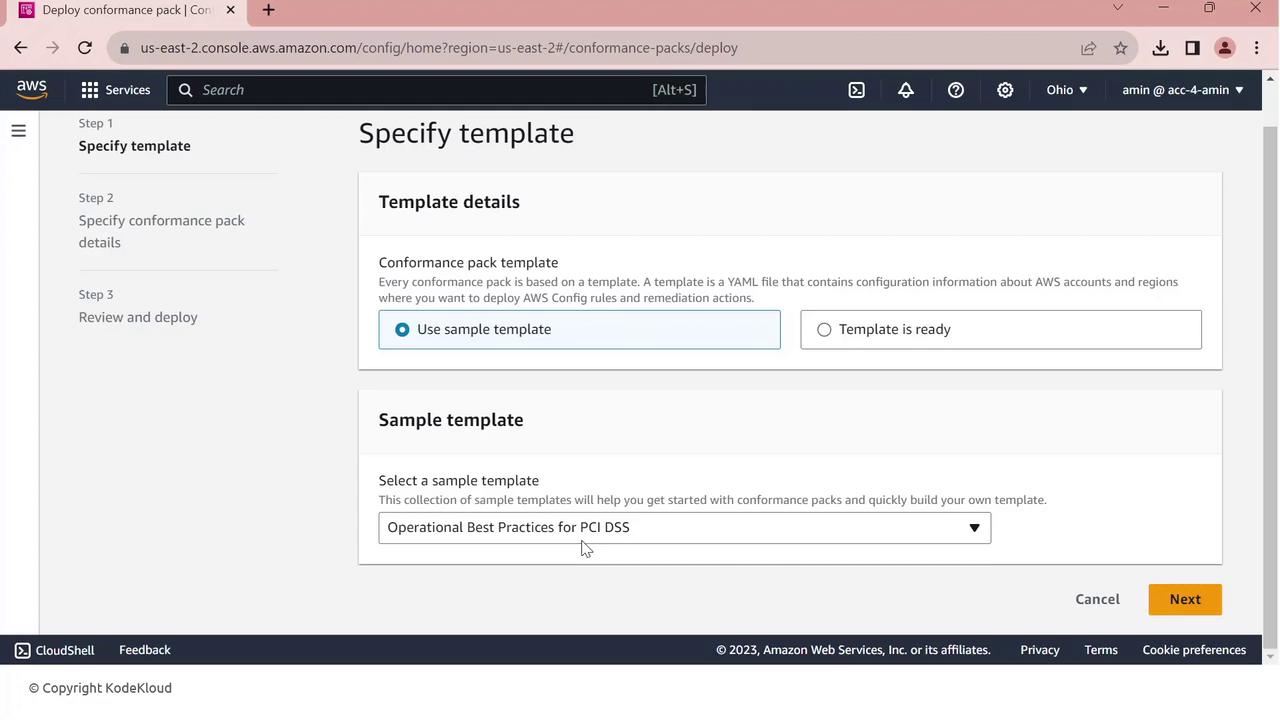
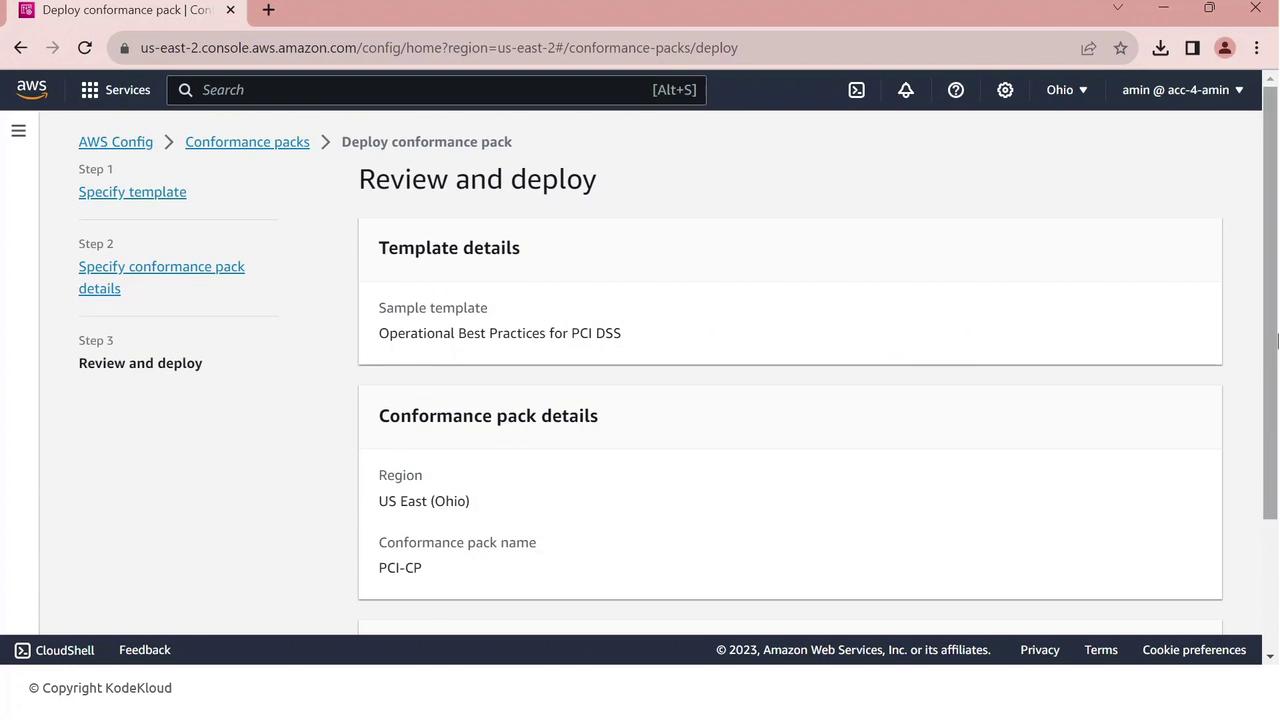
- Review the configuration and click Deploy.
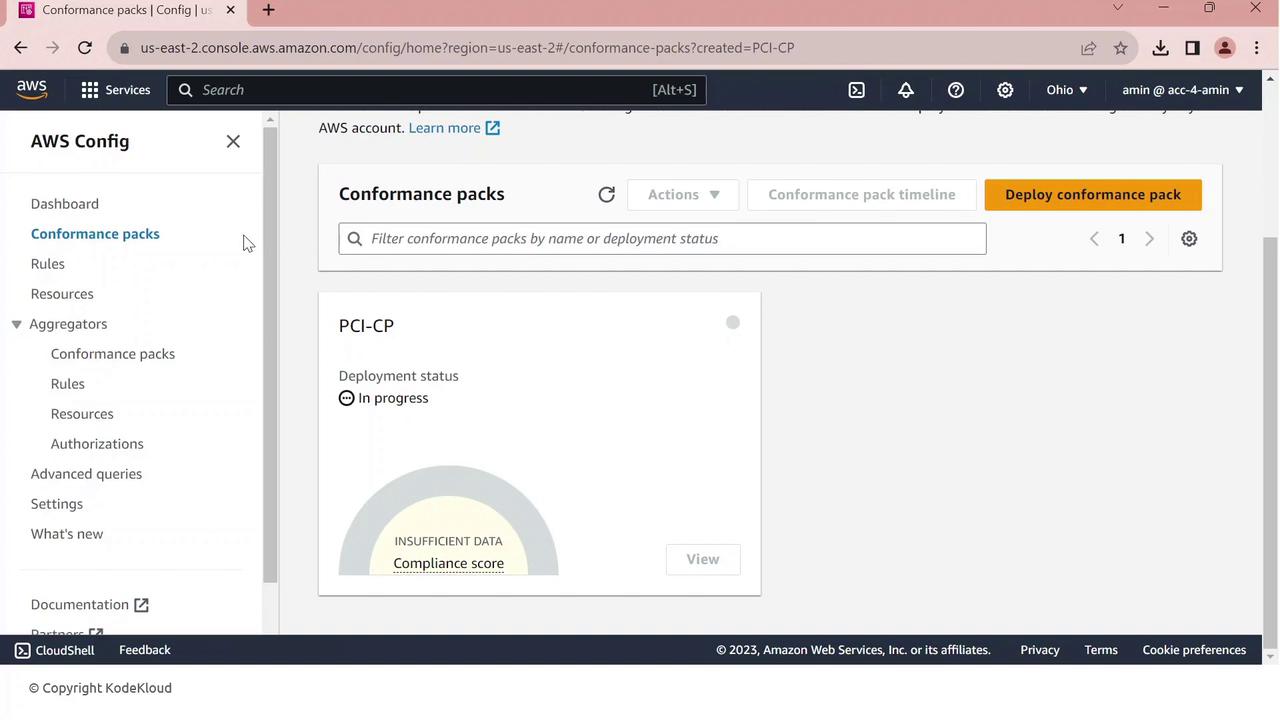
5. Reviewing Compliance Results
Once your conformance pack is deployed, view all rules and their statuses:- Go to Rules in the AWS Config console.
- You’ll see managed and conformance-pack rules listed with compliance indicators.
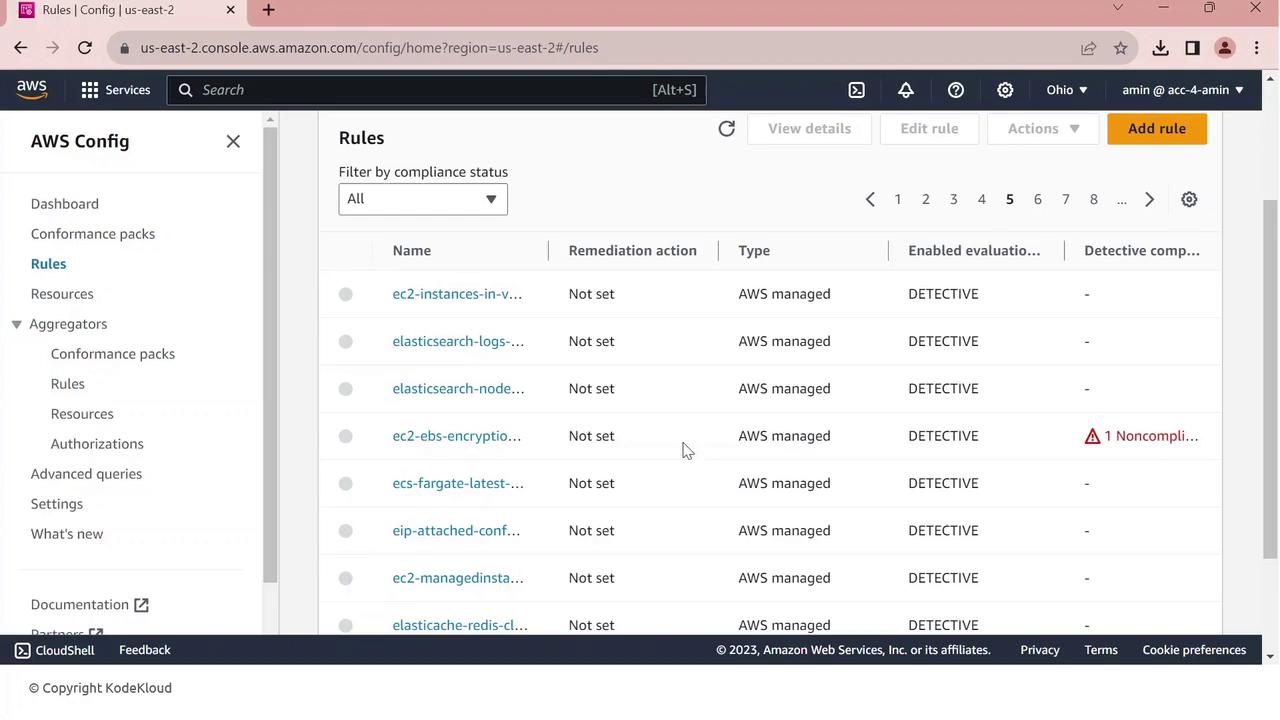
- Click the non-compliant rule to view details—resource IDs, configuration timeline, and remediation options.
