Configuring MFA for an IAM User
- Sign in to the AWS Management Console and open the IAM dashboard.
- Select Users in the navigation pane to view all IAM accounts.
- Click on the user John, then open the Security credentials tab.
- Under Multi-Factor Authentication (MFA), click Assign MFA device.
- Provide a Device label (for example, “MFA”) and choose your device type from the table below:
| Device Type | Description |
|---|---|
| Virtual MFA device | Software authenticator (Google Authenticator, Authy, Duo Mobile) |
| Security key | FIDO2/WebAuthn hardware key |
| Hardware TOTP token | Physical token generating time-based codes |
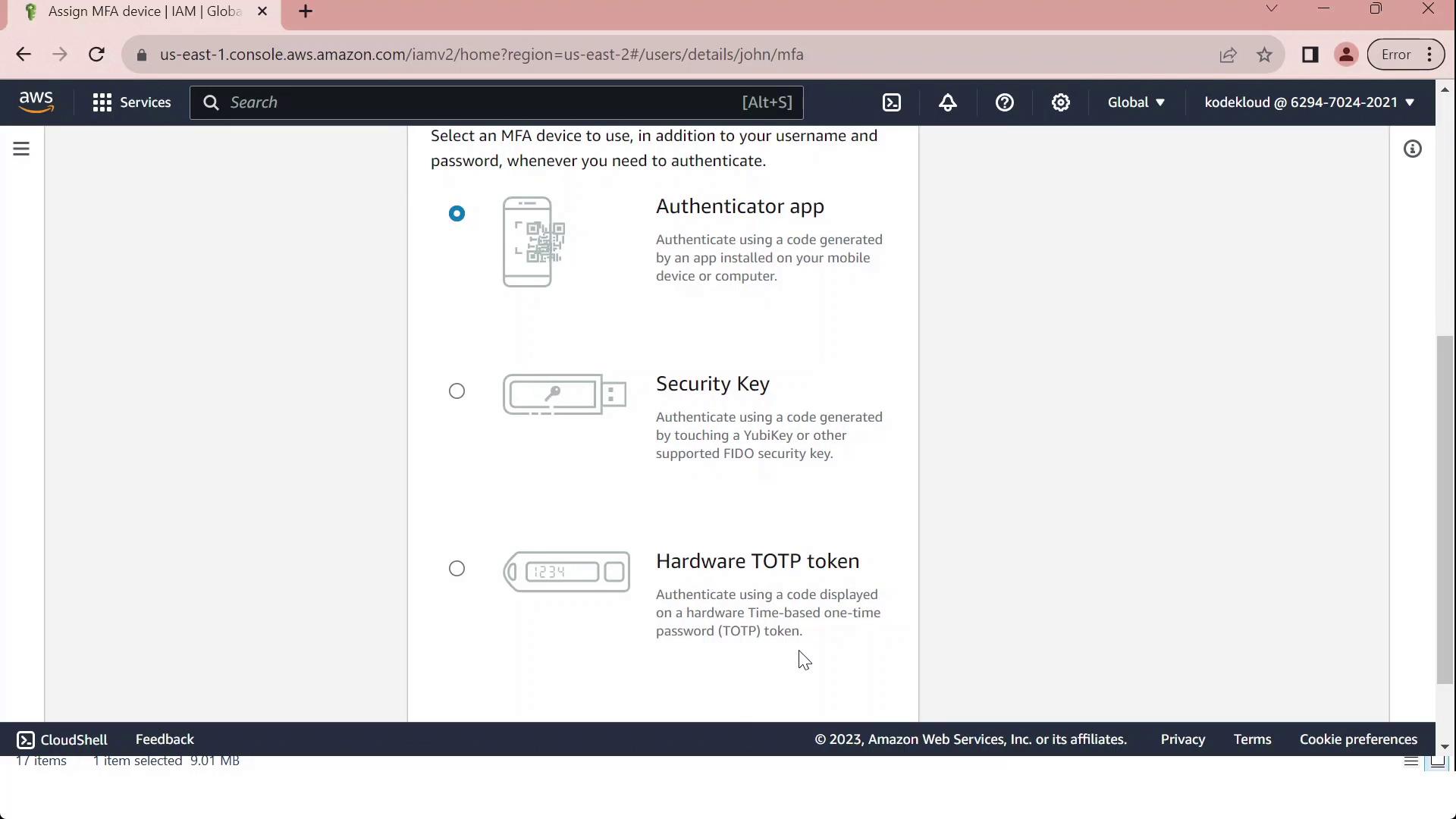
Make sure your chosen authenticator app supports Time-based One-Time Passwords (TOTP).
- To set up a Virtual MFA device:
- Install and open a compatible authenticator app.
- Scan the QR code displayed in the console.
- Enter the two consecutive codes from your app (MFA Code 1 and MFA Code 2).
- Click Assign MFA to finalize.
If you lose access to your MFA device and haven’t saved the seed key, you may need to contact your AWS account administrator or use your root credentials to regain access.
Customizing Password Policies
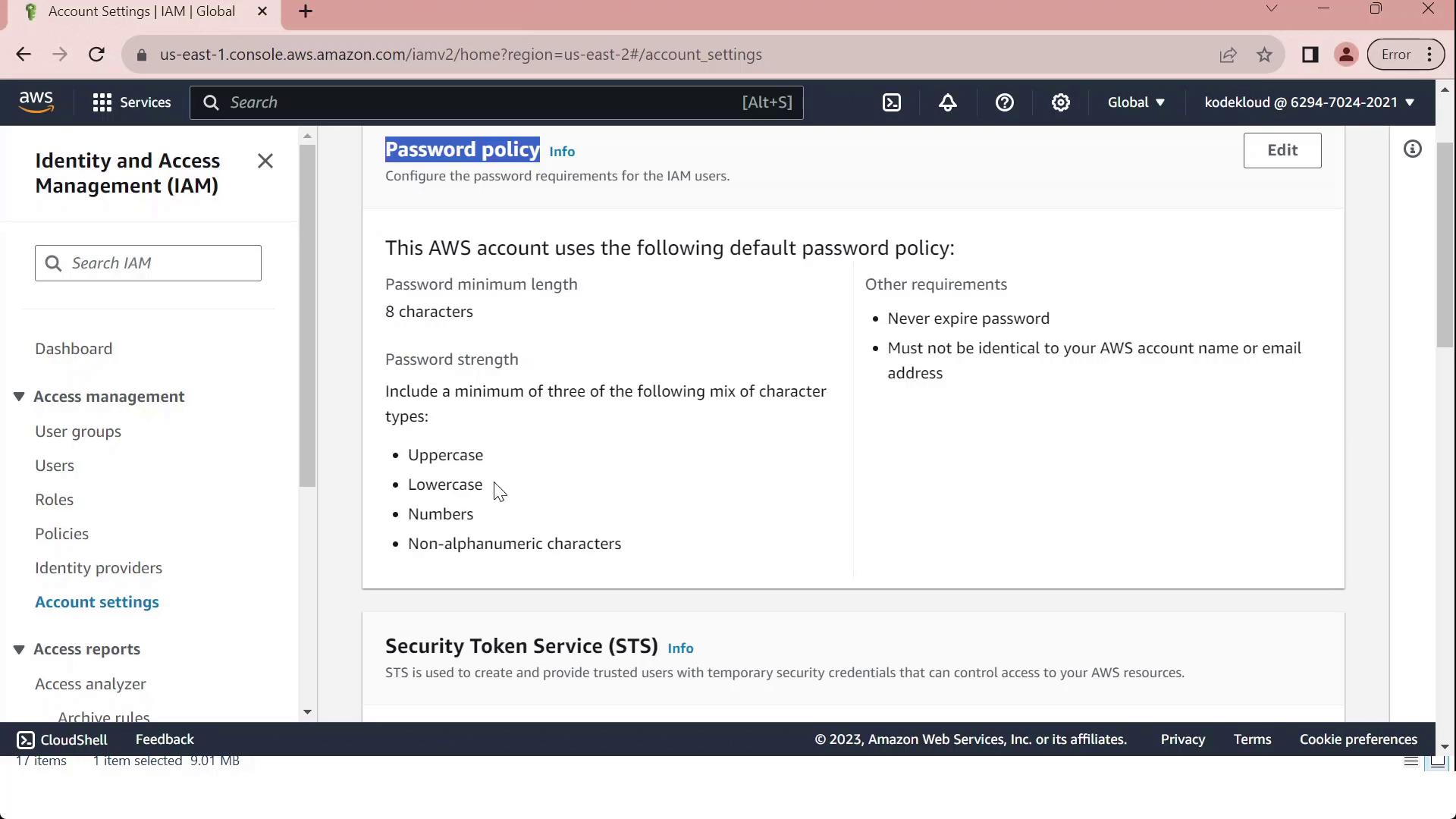
- In the IAM console, select Account settings to view the Password policy section.
- Review the default requirements, which ensure basic password strength:
| Requirement | Default Setting |
|---|---|
| Minimum length | 8 characters |
| Character categories | At least 3 of: uppercase, lowercase, numbers, special characters |
| Exclusions | Cannot match username or email address |
| Password expiration | Disabled |
| Password reuse prevention | None |
- Click Edit, select Custom, and modify settings such as:
- Minimum password length
- Maximum password age
- Required character types
- Prevent password reuse
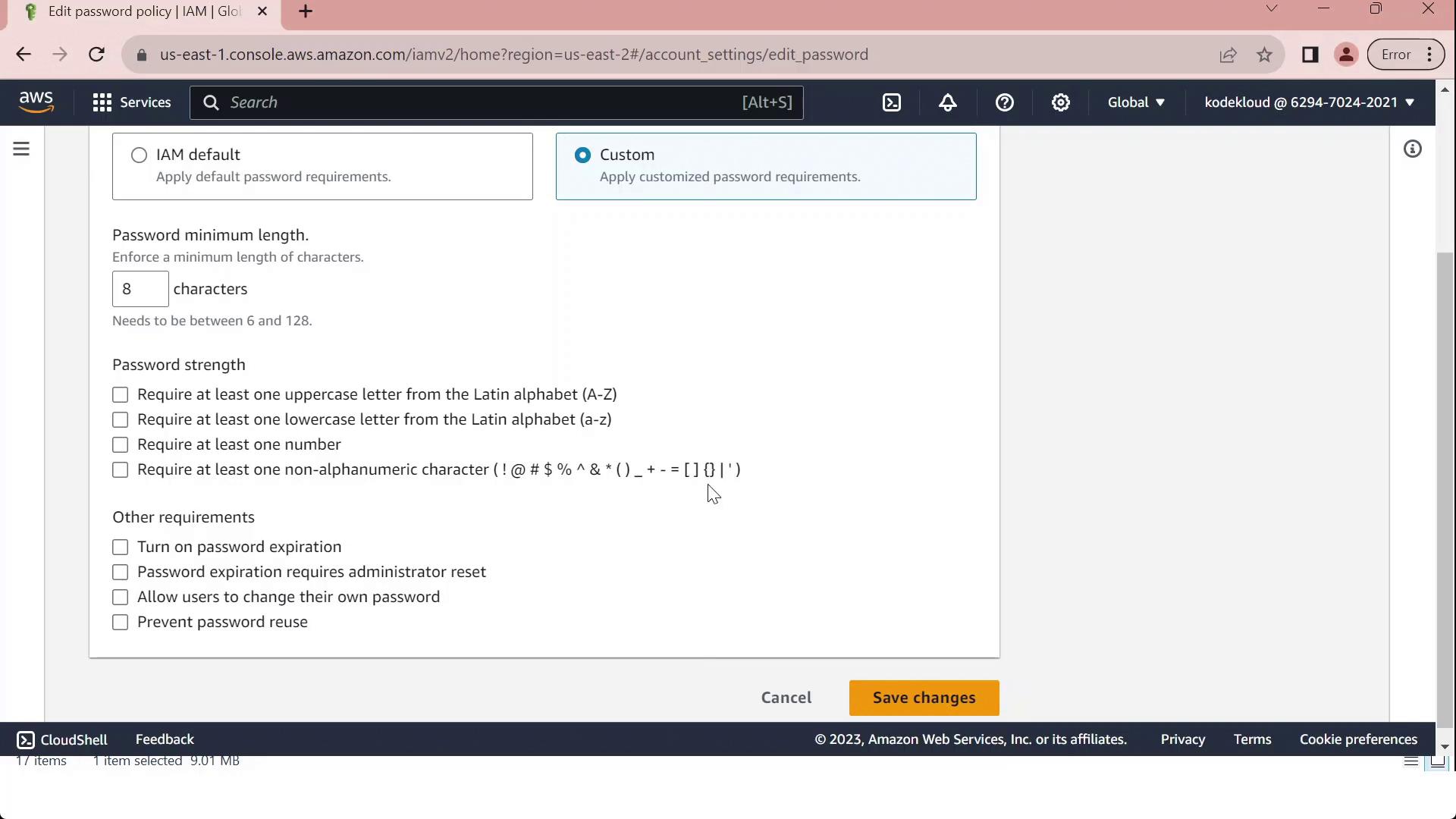
- Once you’ve tailored the policy to your organizational standards, click Save changes. All IAM users will now be subject to the updated policy.