AZ-400: Designing and Implementing Microsoft DevOps Solutions
Implement Security and Validate Code Bases for Compliance
Architecting a Secure DevOps Pipeline
In this guide, we’ll walk through designing a DevSecOps pipeline that embeds security at every stage of the software delivery lifecycle. You’ll learn how version control, build automation, package management, source scanning, deployment, and monitoring work together to deliver high-quality—and vulnerability-free—software.
Key Stages & Tools
Below is a high-level overview of the major phases in a secure CI/CD pipeline. Each component plays a critical role in enforcing security policies and maintaining compliance from code commit to production.
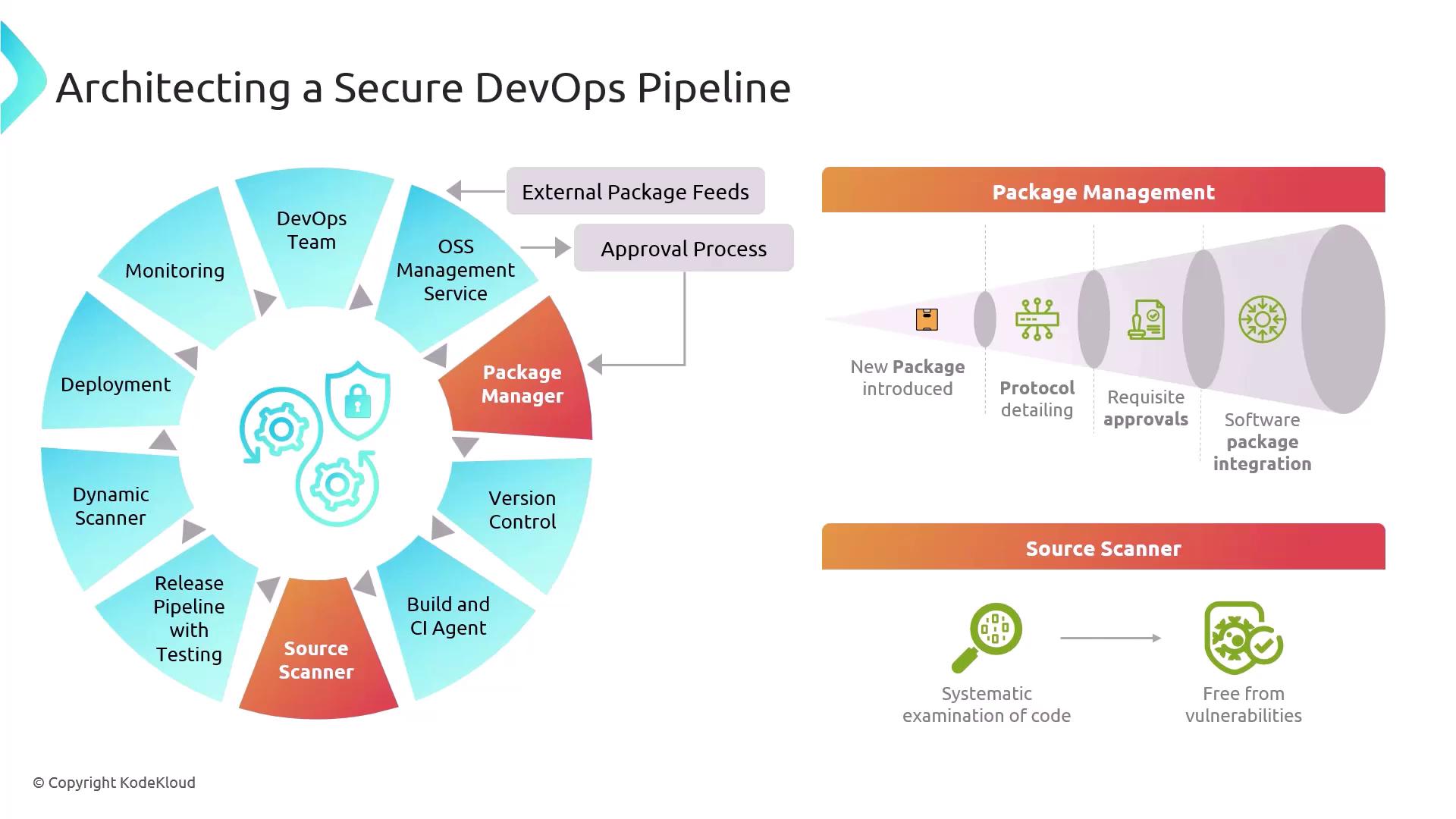
1. Problem Area: External Package Feeds
Open source libraries are invaluable, but they can introduce risks if packages aren’t properly vetted. A single compromised dependency can cascade into a serious breach.
Warning
Malicious or vulnerable open source packages can introduce critical security flaws if not vetted properly.
Mitigation strategies:
- Implement an approval workflow for any new package before it’s consumed.
- Use an OSS management service to track versions, licenses, and known CVEs.
- Maintain a curated feed of trusted packages to prevent unauthorized or unsafe dependencies.
2. Focus Area 1: Package Management Best Practices
Centralizing package control ensures that only approved artifacts enter your pipeline. Automate governance with these key policies:
| Policy | Description | Tool Support |
|---|---|---|
| Source Whitelisting | Restrict feeds to vetted registries | Azure Artifacts, GitHub Packages |
| Version Pinning | Approve and pin specific package versions | npm, NuGet, PyPI` |
| Role-Based Access | Limit publish/update rights to authorized personnel | Azure AD, GitHub Teams |
Note
Centralizing package governance helps maintain consistency and auditability across all teams.
3. Focus Area 2: Source Scanning
Automated scanning tools catch vulnerabilities early—long before they reach production. Integrate these scans as part of your CI/CD workflow:
| Scan Type | Trigger | Outcome |
|---|---|---|
| Static Code Analysis | Pull Request | Detailed report on code weaknesses |
| Dependency Scanning | Every Build | License checks & CVE alerts |
| Secrets Detection | Continuous | Blocks commits containing credentials |
By blocking merges or deployments until high-severity findings are resolved, you shift security left and reduce remediation costs.
Summary
A secure DevOps pipeline—or DevSecOps culture—hinges on rigorous package management and continuous source scanning. When you enforce consistent policies and automate security checks, you deliver reliable software that scales without compromising safety.
Links and References
Watch Video
Watch video content