Certified Jenkins Engineer
Automation and Security
Demo Authorization Matrix Authorization Strategy
Unlock fine-grained access control in Jenkins using the Matrix Authorization Strategy plugin. In this tutorial, you’ll learn to:
- Install the plugin
- Compare project-based vs global matrix strategies
- Configure role-based permissions
- Validate access with sample user accounts
Prerequisites
- A running Jenkins instance
- Admin credentials (e.g., Barahalikar Siddharth)
1. Install the Matrix Authorization Strategy Plugin
- Sign in as admin.
- Navigate to Manage Jenkins → Manage Plugins → Available.
- Search for Matrix Authorization Strategy and click Install without restart.
This plugin supports both global and project-level access matrices.

2. Project-Based Matrix Authorization
- Go to Manage Jenkins → Configure Global Security.
- Under Authorization, select Project-based Matrix Authorization Strategy and click Apply.
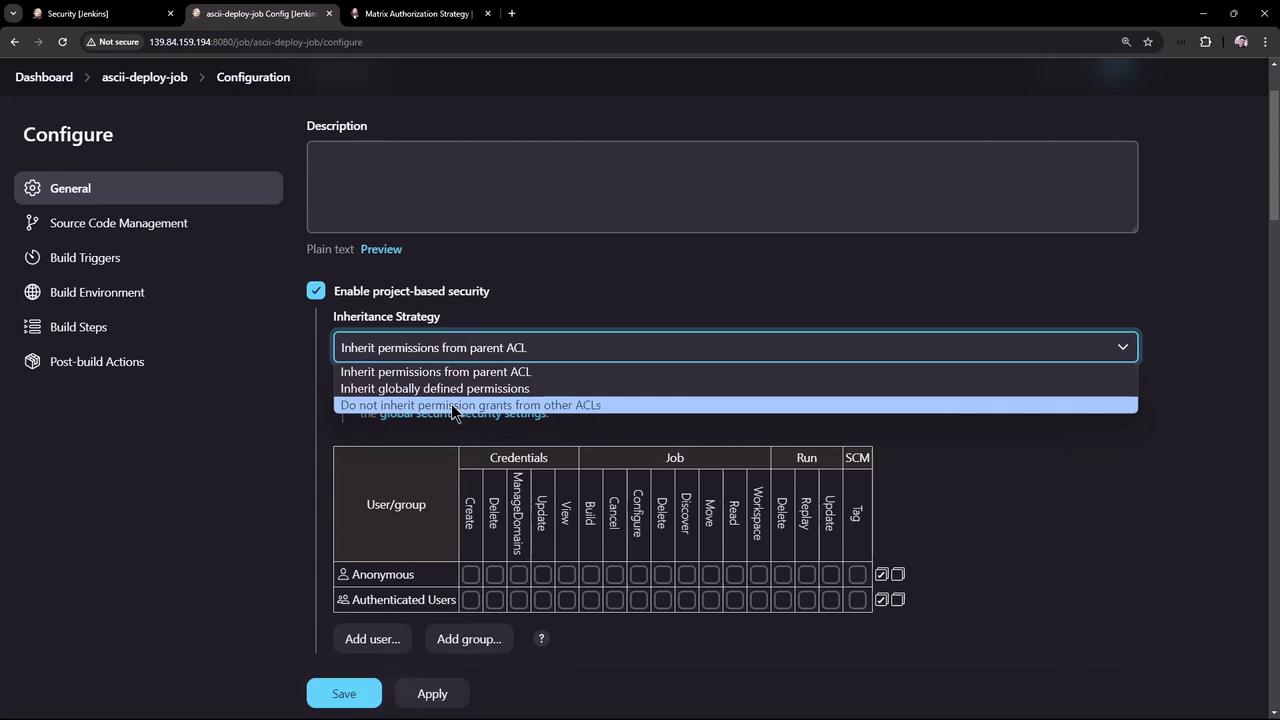
- Open a job (e.g., ascii-deploy-job), choose Configure, then enable Project-based security.
- Decide whether to inherit global permissions or define a custom ACL for this job.
Note
If you only need instance-wide controls, return to Configure Global Security and choose Matrix-based Security instead.
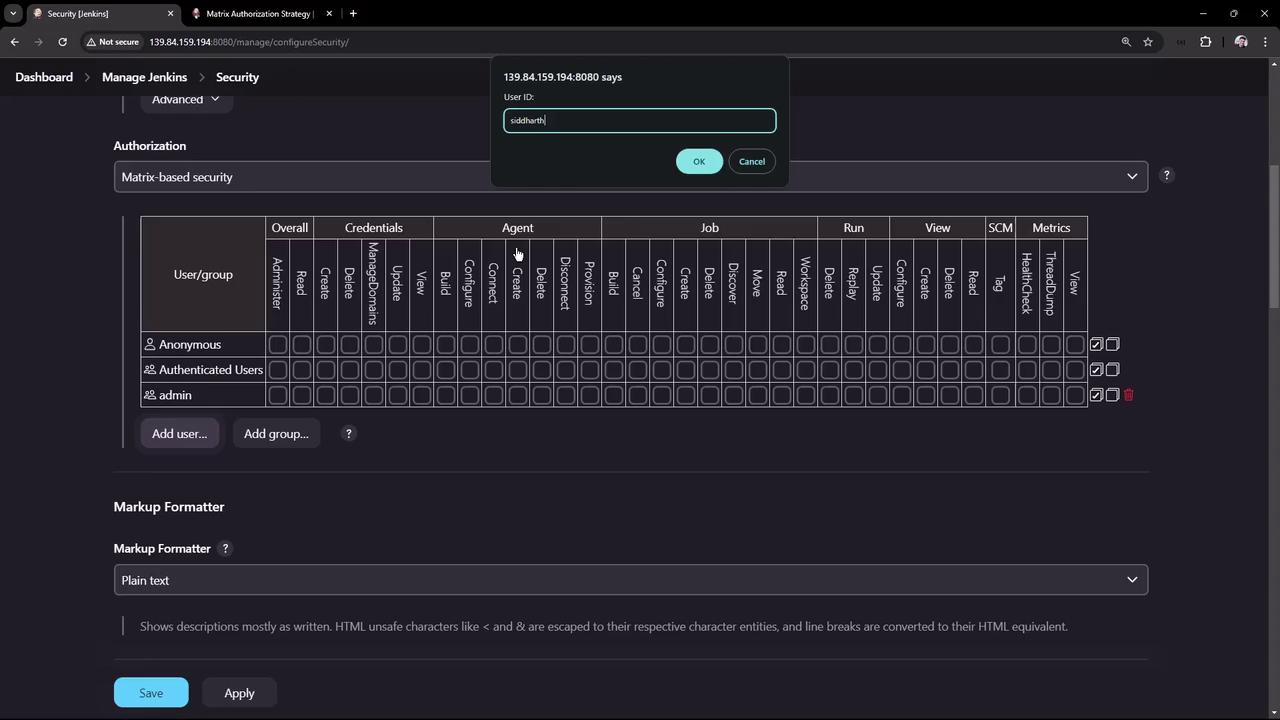
3. Global Matrix-Based Security
- Open Manage Jenkins → Configure Global Security.
- Select Matrix-based Security in the Authorization section.
- Strip all permissions from anonymous. Leave authenticated unchecked (we’ll grant Overall Read later).
- Click Add user or group, enter each name, and confirm. Jenkins will warn if the user/group doesn’t exist.
3.1 Define Group Permissions
Configure these four groups:
| Group | Permissions |
|---|---|
| admin | Overall → Administer |
| manager | Overall: Read<br>Job: Read<br>View: Read<br>Metrics: Read |
| QA | Job: Read, Build |
| developer | Overall: Read<br>Credentials: Create, Update, View<br>Agent: Provision<br>Job: All except Delete<br>View: Create, Read, Configure<br>Metrics: Read |
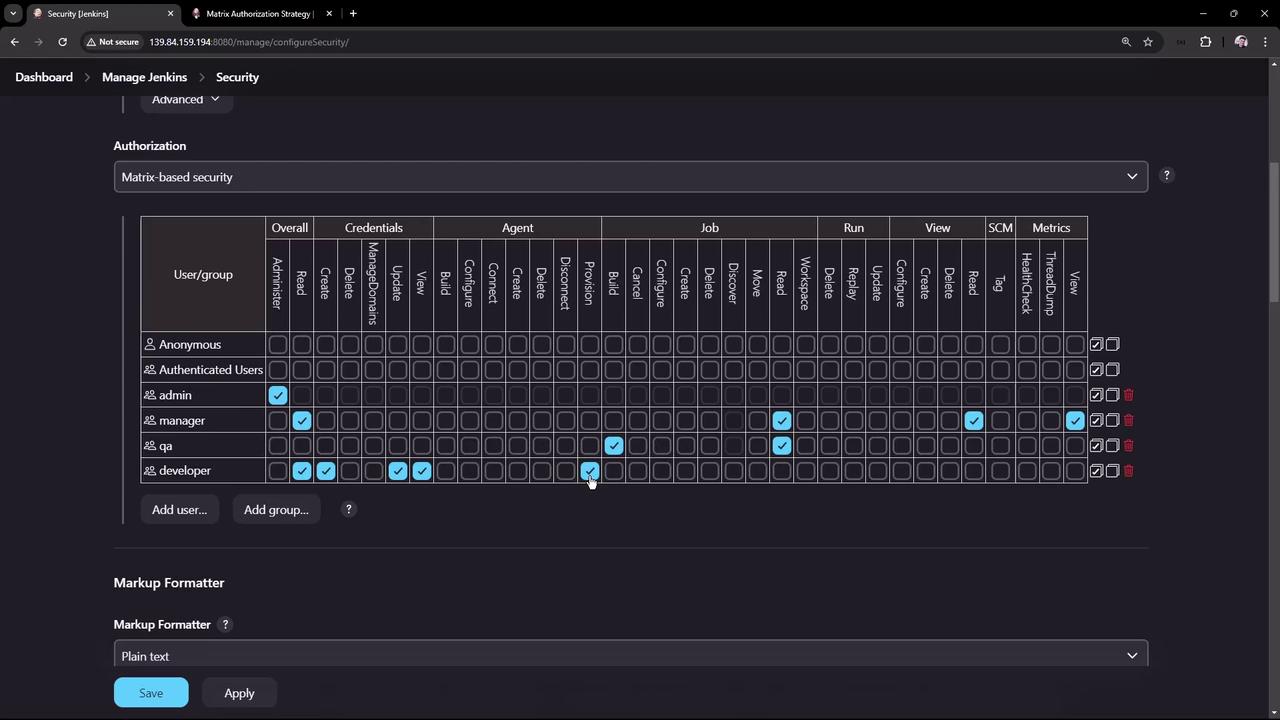
Once permissions are set, click Save to apply.

4. Test Role-Based Access
4.1 Admin: Full Control
As admin, verify you can view, configure, build, and delete the ascii-deploy-job.
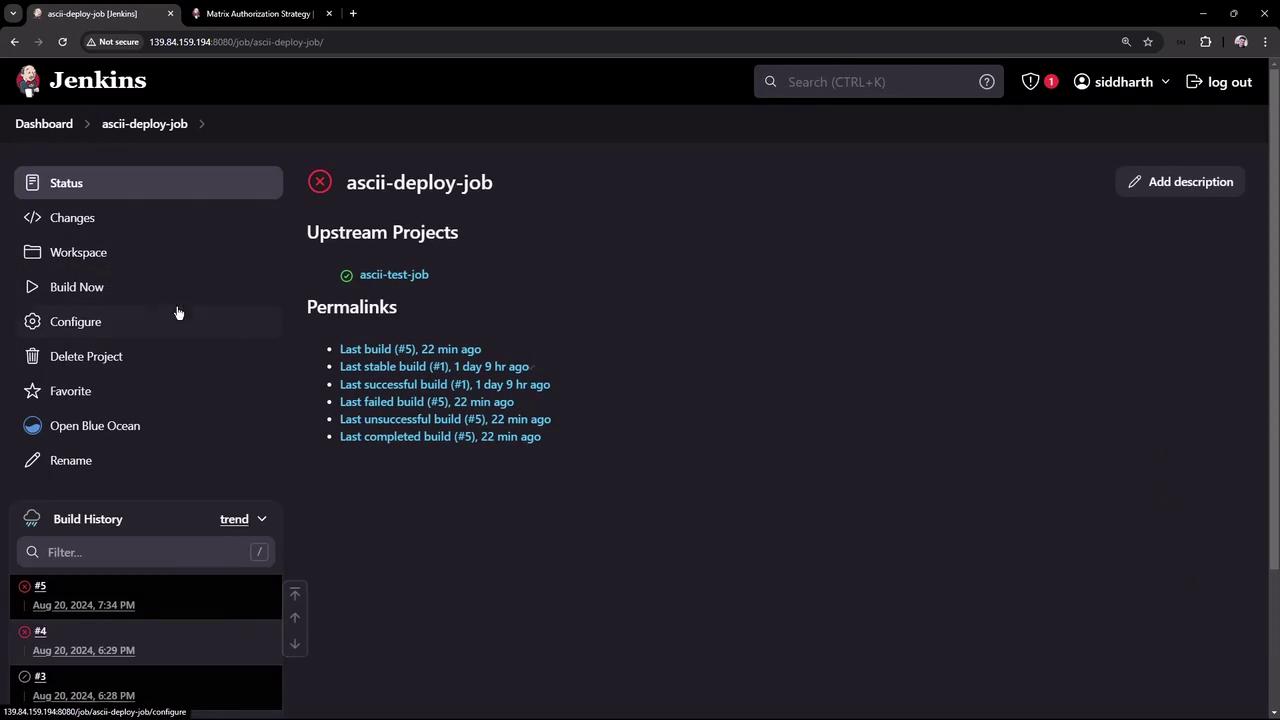
4.2 Tina (QA + Developer)
Log in as Tina:
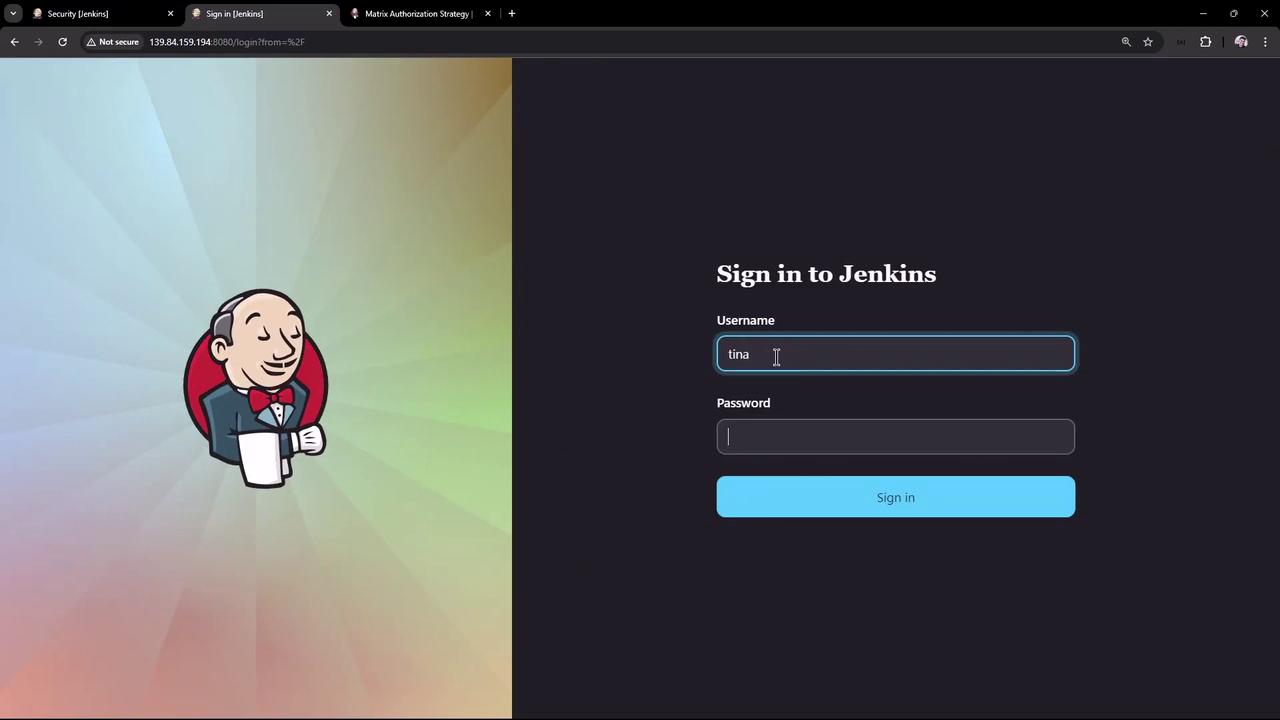
- Jobs: Delete is hidden
- Credentials: Create, View, Update (no delete)
- Manage Jenkins: Not accessible
4.3 Bob (QA Only)
Initially, Bob is denied access (no Overall Read). To fix:
- Log in as admin.
- Grant authenticated or QA the Overall Read permission.
- Re-login as Bob.
Now Bob can view and build jobs but cannot delete or manage credentials.
4.4 Ali (Manager)
Log in as Ali (manager):
- Overall: Read
- Job & View: Read
- Metrics: Read
Ali can open jobs and view logs but cannot build, configure, or delete.
You’ve now secured your Jenkins instance with Matrix Authorization Strategy. Adjust role permissions as your team and security requirements evolve.
References
Watch Video
Watch video content