Certified Jenkins Engineer
Automation and Security
Demo Jenkins CLI SSH Authentication
In this guide, you’ll learn how to configure Jenkins to use SSH key–based authentication for its CLI, replacing the default HTTP basic auth. This approach is more secure and integrates seamlessly with your existing SSH infrastructure.
Prerequisites
| Requirement | Description |
|---|---|
| Jenkins server | Running on http://localhost:8080 |
| SSH client | Installed on your local machine |
jenkins-cli.jar | Downloaded from your Jenkins server (Manage → Jenkins CLI) |
1. Discovering the Jenkins SSH Endpoint
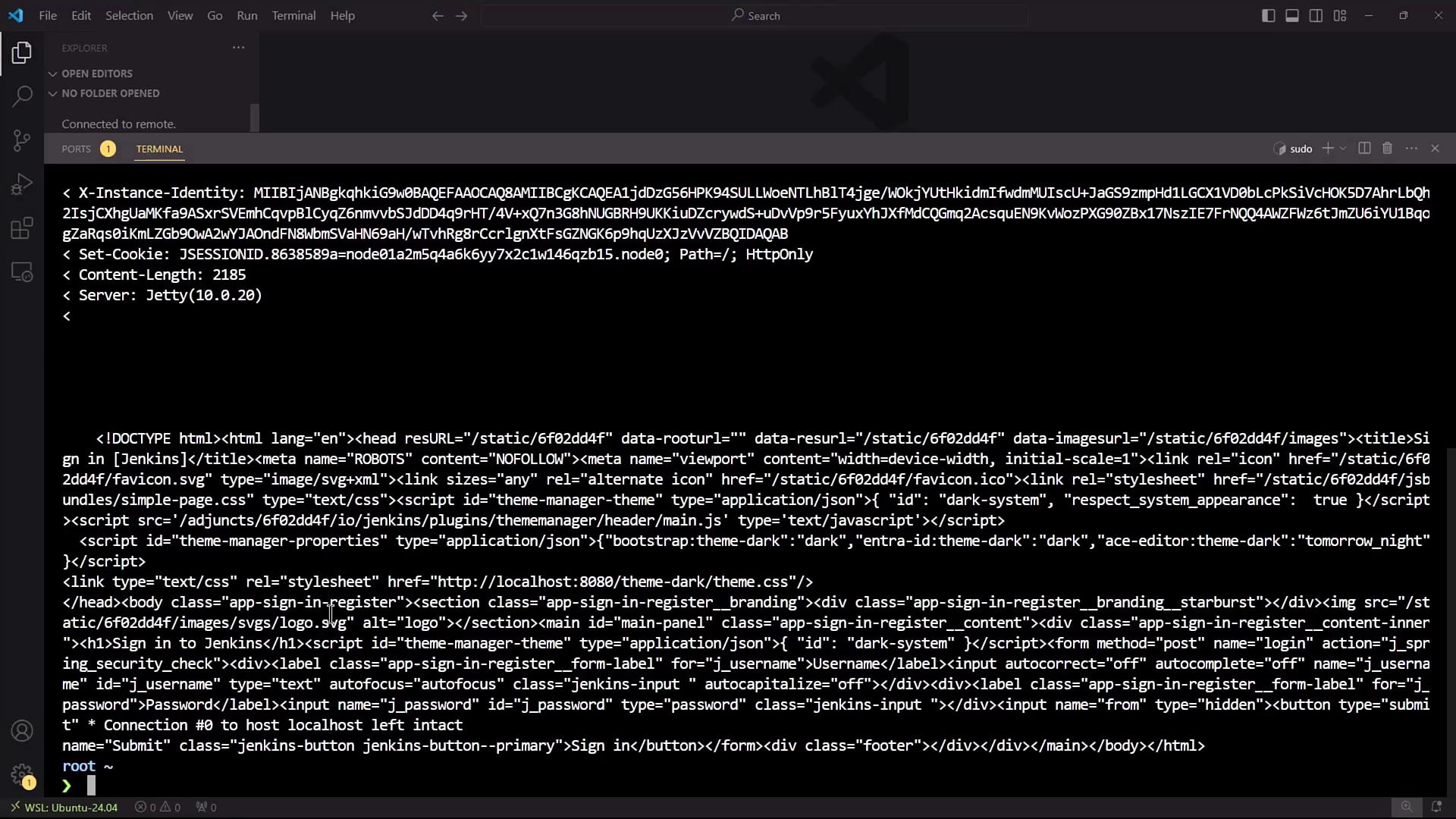
Jenkins exposes its CLI over SSH on a configurable port. To find the SSH endpoint before enabling it, query the /login endpoint:
curl -Lv http://localhost:8080/login 2>&1 | grep -i 'x-ssh-endpoint'
Note
By default, the SSH server is disabled in Jenkins, so you won’t see the X-SSH-Endpoint header until it’s enabled.
2. Enabling the Jenkins SSH Server
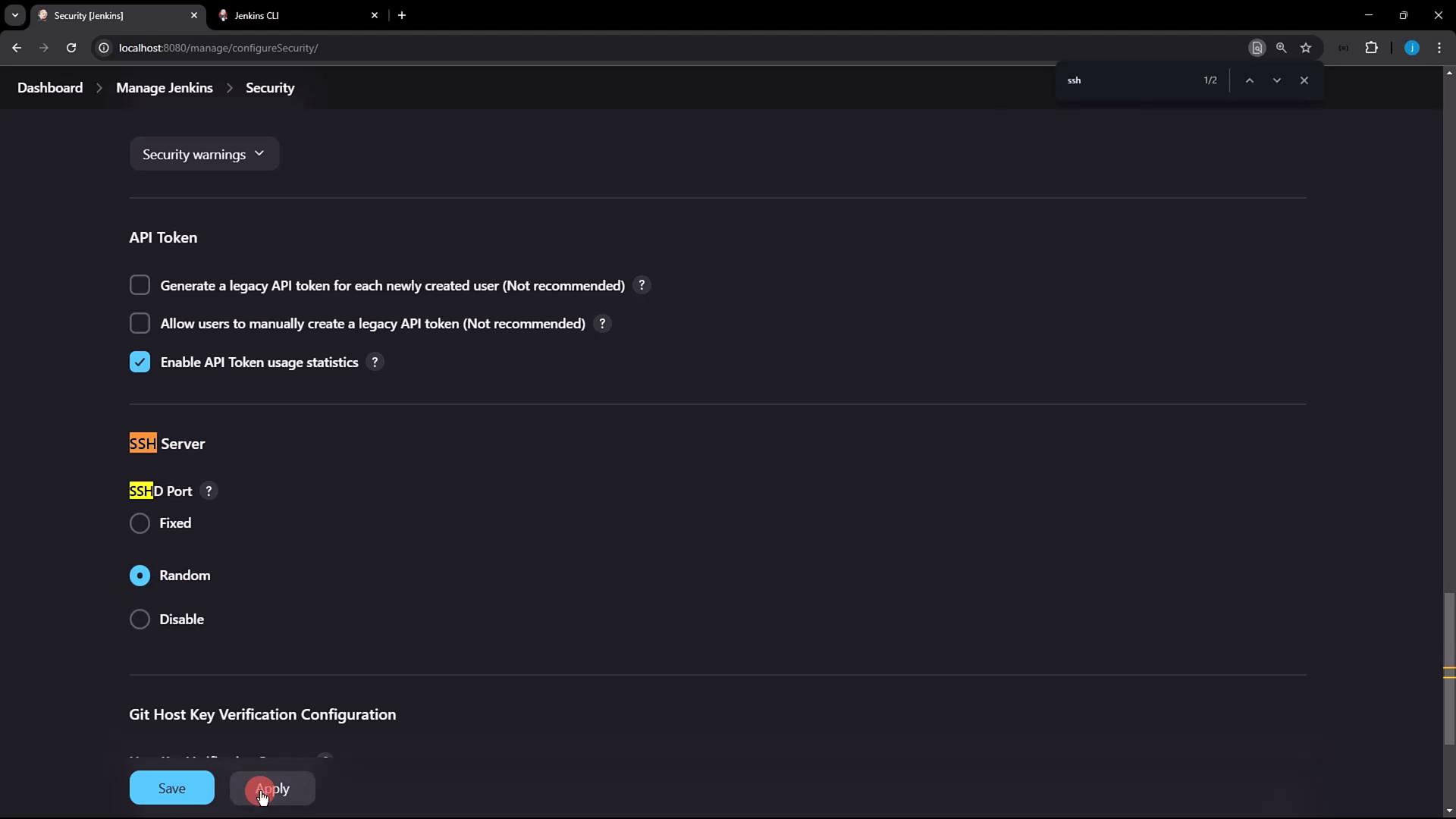
- In Jenkins, go to Manage Jenkins → Configure Global Security.
- Locate the SSH Server section and enable the SSH port. You can select Random or enter a fixed port (e.g.,
2222). - Click Apply to save changes.
Warning
If you choose a fixed port, make sure it’s open in your firewall and not in use by another service.
After applying, rerun the curl command:
curl -Lv http://localhost:8080/login 2>&1 | grep -i 'x-ssh-endpoint'
You should now see output similar to:
< X-SSH-Endpoint: localhost:4397
The SSH server is listening on port 4397.
3. Generating and Registering Your SSH Key
3.1 Generate an SSH Key Pair
If you don’t already have an SSH key, generate one:
ssh-keygen -t rsa -b 4096
Press Enter to accept the default file location (~/.ssh/id_rsa) and leave the passphrase empty if you prefer. Then display your public key:
cat ~/.ssh/id_rsa.pub
# ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC... root@host
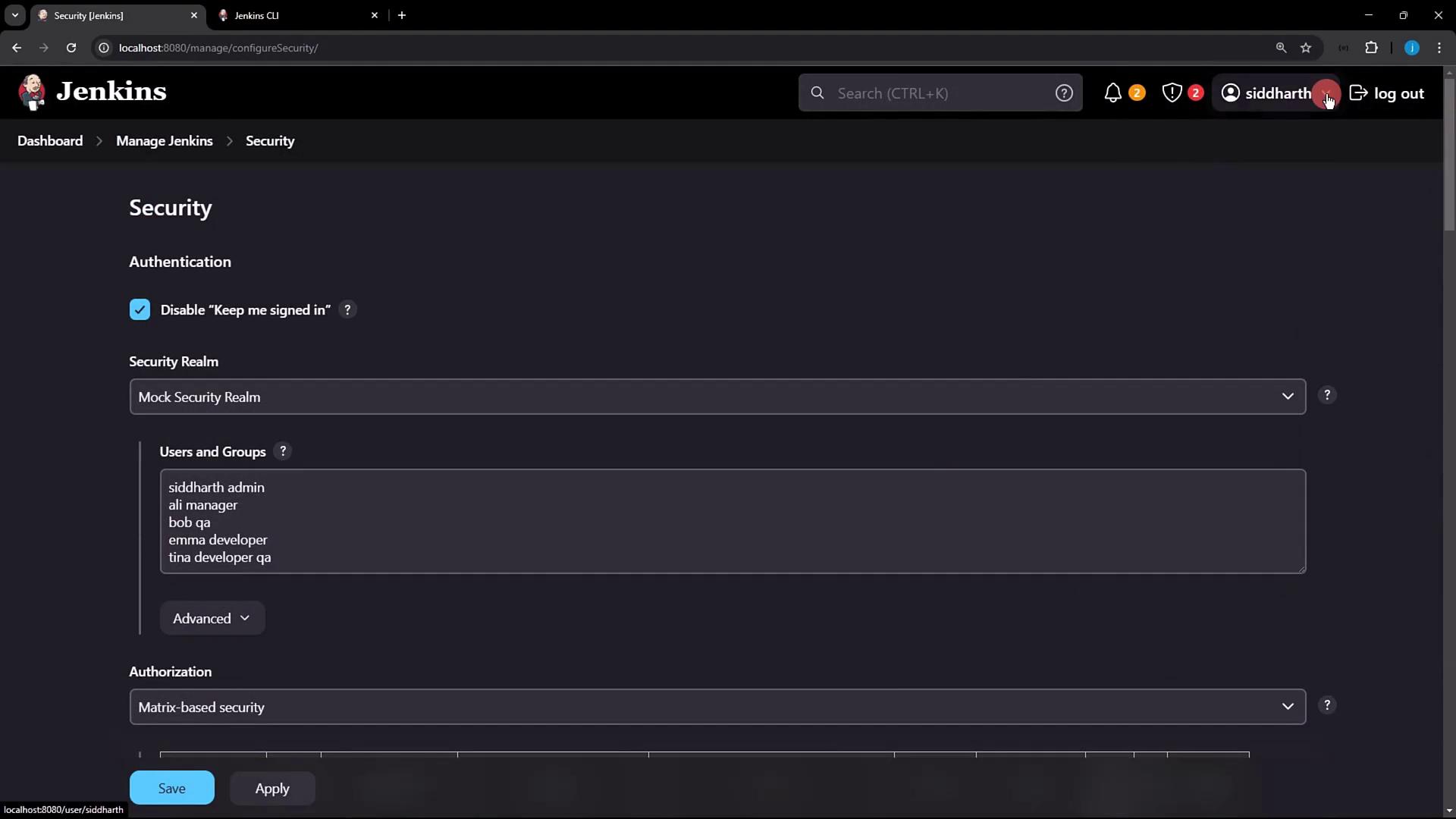
3.2 Add Your Public Key in Jenkins
- Click your Jenkins user name (e.g., siddharth) → Configure.
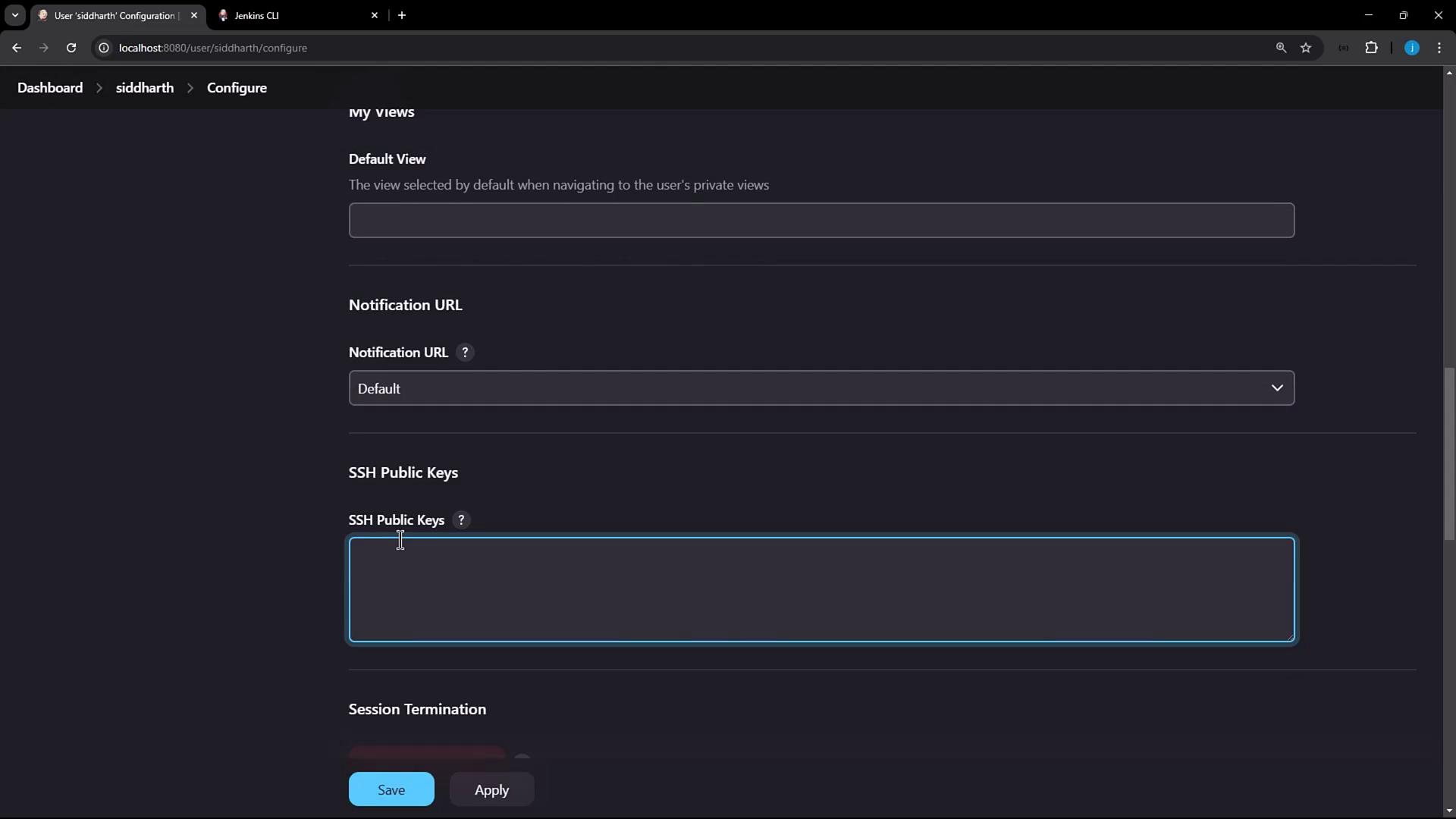
- Scroll to the SSH Public Keys section.
- Paste the contents of
~/.ssh/id_rsa.pubinto the text box. - Click Apply.
4. Connecting to Jenkins via SSH
Now that your public key is registered, connect to Jenkins over SSH and run CLI commands. Replace 4397 with the port reported by X-SSH-Endpoint:
ssh -l siddharth -p 4397 localhost help
Sample output:
add-job-to-view Adds jobs to view.
build Builds a job, and optionally waits until completion.
cancel-quiet-down Cancel the effect of the "quiet-down" command.
clear-queue Clears the build queue.
...
5. Using SSH Mode with the Jenkins CLI JAR
You can also invoke SSH mode directly via jenkins-cli.jar. For full details, see the Jenkins CLI documentation.
Example—list jobs over SSH:
java -jar jenkins-cli.jar \
-s http://localhost:8080 \
-ssh -user siddharth \
list-jobs
Expected output:
ascii-build-job
ascii-deploy-job
ascii-test-job
d-v-s-pipeline
Dasher_testJob
...
This confirms that authentication is performed via your SSH key pair instead of HTTP basic auth.
Authentication Methods Comparison
| Method | Port/Protocol | Complexity |
|---|---|---|
| HTTP Basic Auth | 8080 (HTTP) | Minimal |
| SSH Key Auth | Custom (SSH) | Moderate |
References
Watch Video
Watch video content