Certified Jenkins Engineer
Code Quality and Testing
Demo SAST Analysis
Perform Static Application Security Testing (SAST) on your JavaScript (Node.js) code using SonarQube. We assume SonarQube is running at http://<host>:9000.
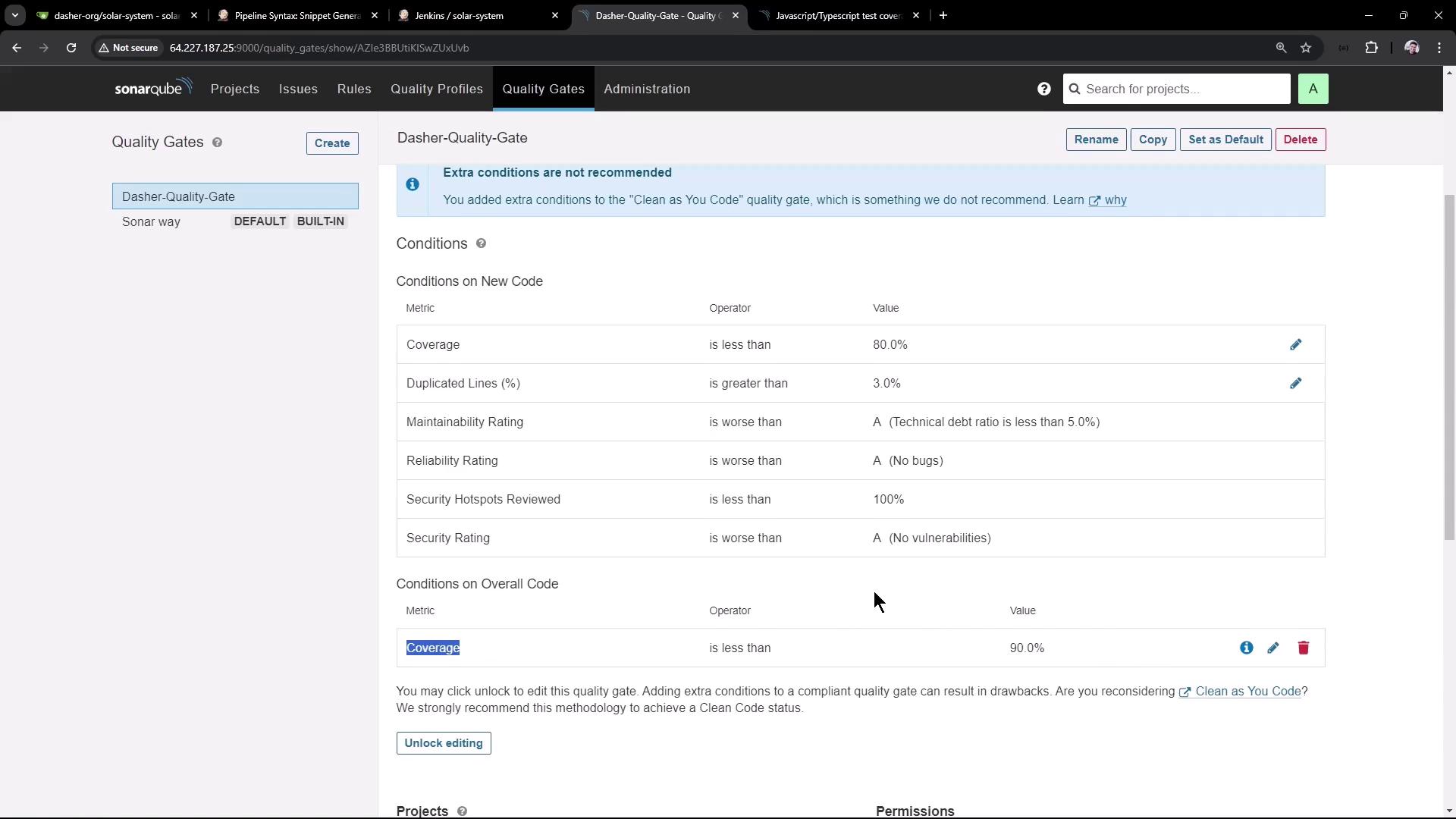
1. Configure the Default Quality Gate
- Log in to SonarQube and navigate to Quality Gates.
- Select Dasher-Quality-Gate and click Set as default.
- Verify the key condition: Overall Coverage < 90%.
Note
Quality Gates enforce your code quality standards automatically. Failing criteria (e.g., coverage, duplications, maintainability) will mark the gate as failed.
2. Create a New Project
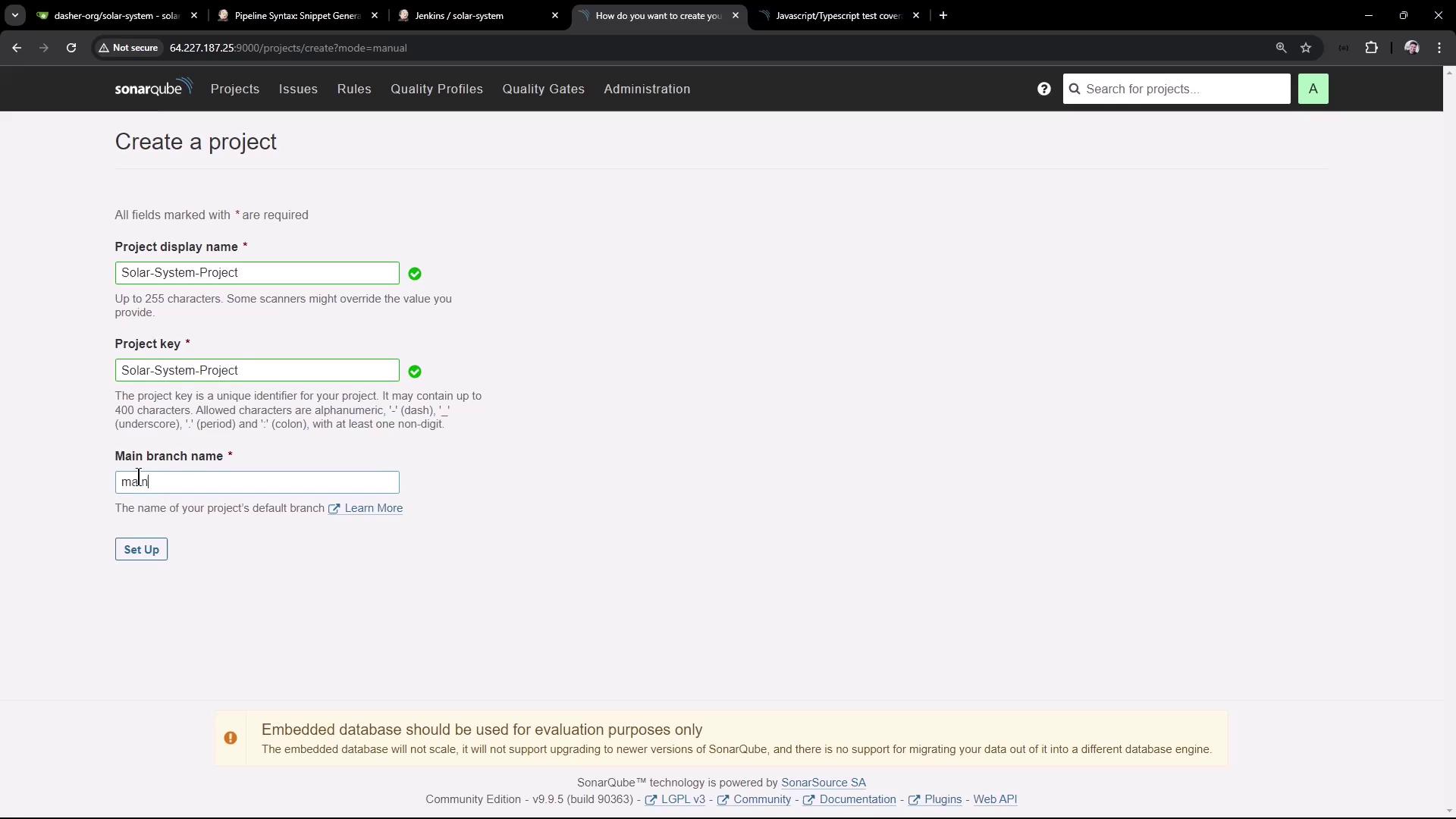
2.1. Define Project Basics
- Click Create Project → Manually.
- Fill in the form:
- Project Display Name:
Solar-System-Project - Project Key:
Solar-System-Project - Main Branch Name:
main
- Project Display Name:
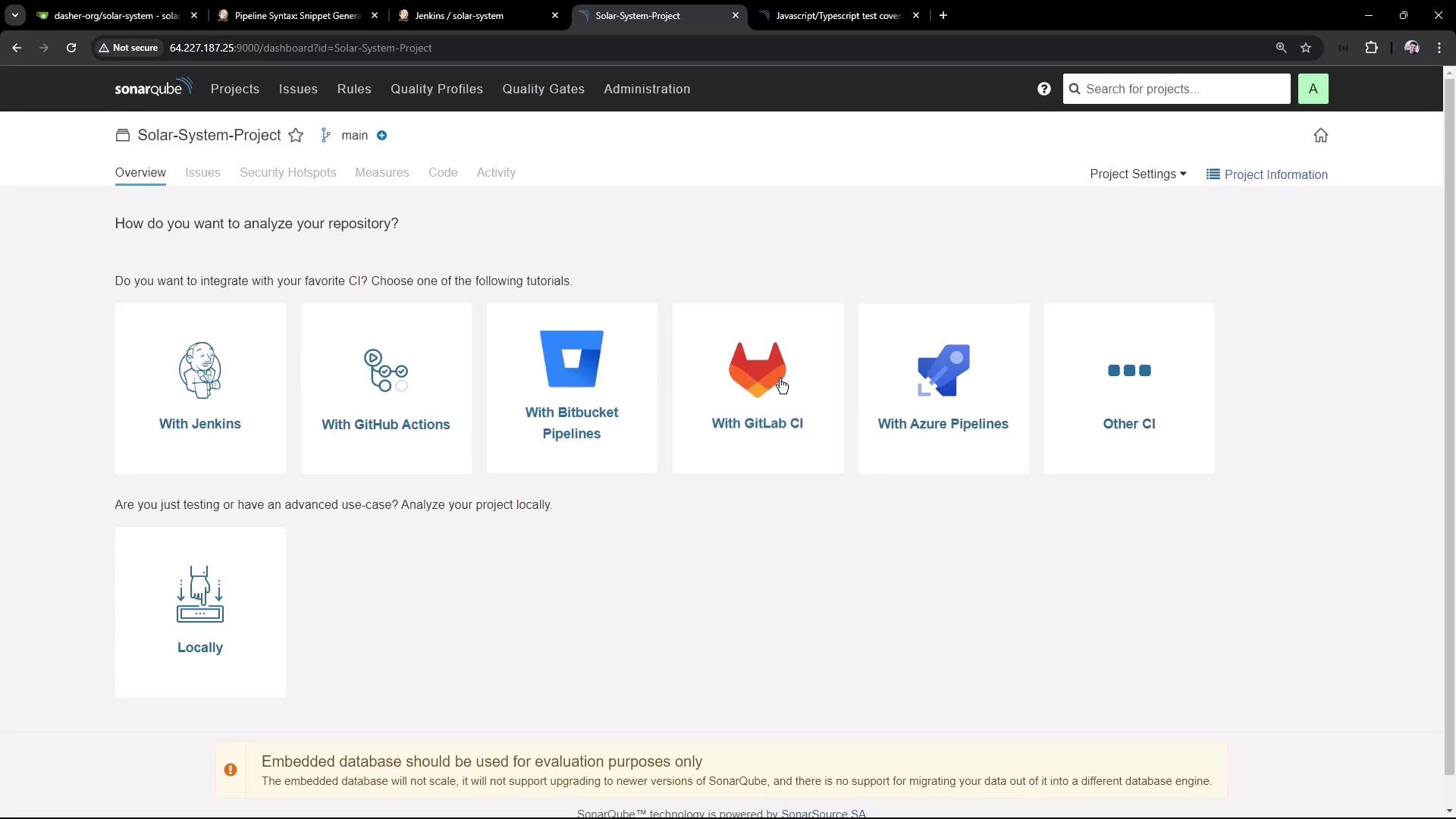
2.2. Select Technology and OS
- Under Technology, choose Other.
- For Operating System, select Linux.
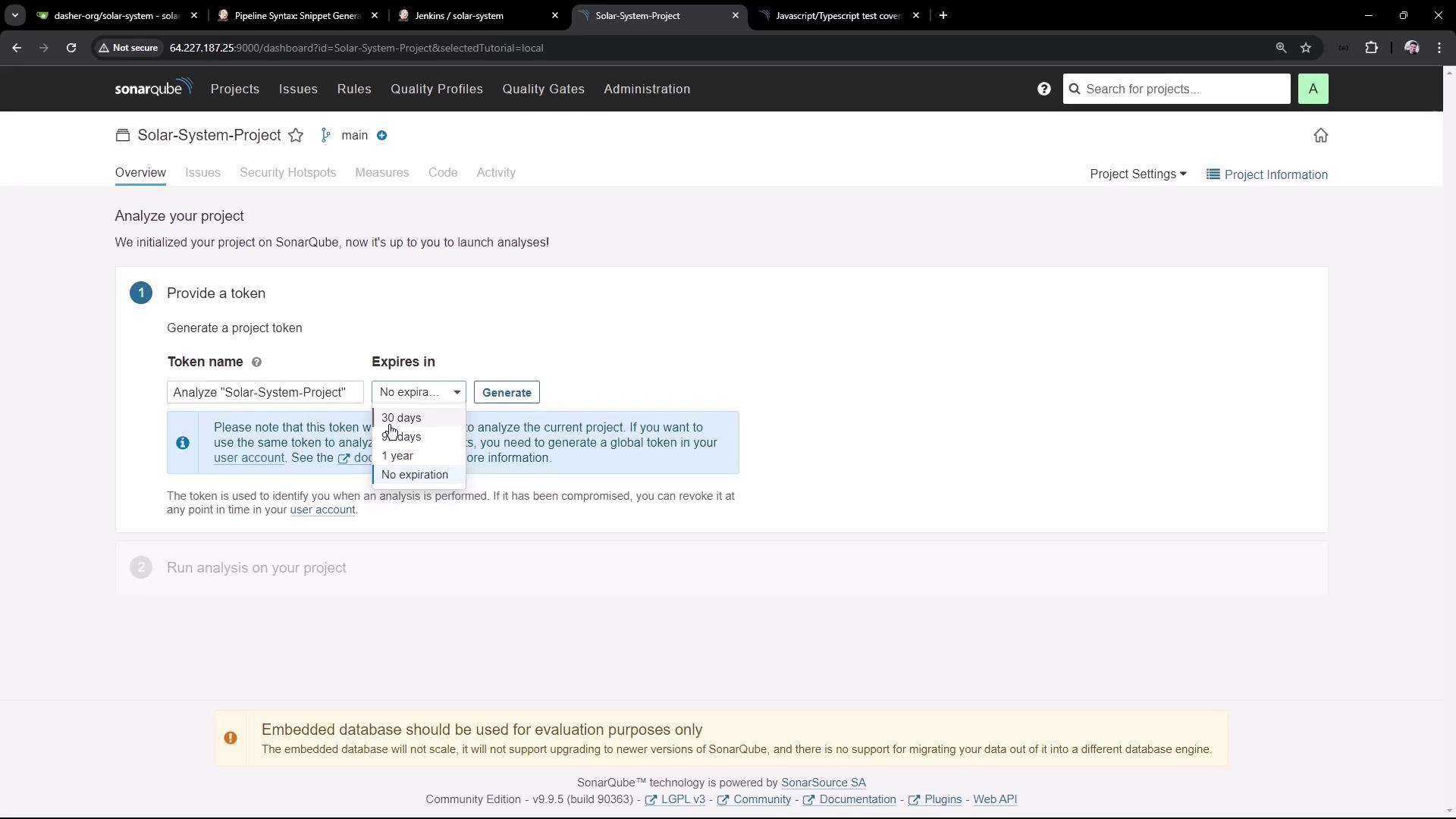
2.3. Generate an Authentication Token
- In the project dashboard, click Generate Token.
- Provide a name and select No expiration (for demo only).
Warning
Avoid using tokens without expiration in production. Rotate your tokens regularly.
3. Local Analysis with sonar-scanner
Install the SonarQube Scanner locally or via your package manager. Then run:
sonar-scanner \
-Dsonar.projectKey=Solar-System-Project \
-Dsonar.sources=. \
-Dsonar.host.url=http://<host>:9000 \
-Dsonar.login=<YOUR_TOKEN>
4. Jenkins Pipeline Configuration
Integrate SAST into your CI by adding a SonarQube stage to your Jenkinsfile:
pipeline {
agent any
environment {
SONAR_SCANNER_HOME = tool 'sonarqube-scanner-6.1.0'
}
stages {
stage('Installing Dependencies') { steps { /* ... */ } }
stage('Dependency Scanning') { steps { /* ... */ } }
stage('Unit Testing') { steps { /* ... */ } }
stage('Code Coverage') { steps { /* ... */ } }
stage('SAST - SonarQube') {
steps {
sh 'echo $SONAR_SCANNER_HOME'
sh """
$SONAR_SCANNER_HOME/bin/sonar-scanner \
-Dsonar.projectKey=Solar-System-Project \
-Dsonar.sources=app.js \
-Dsonar.host.url=http://<host>:9000 \
-Dsonar.login=<YOUR_TOKEN>
"""
}
}
}
}
For more options, see the Jenkins Pipeline Syntax guide.
5. Installing SonarScanner in Jenkins
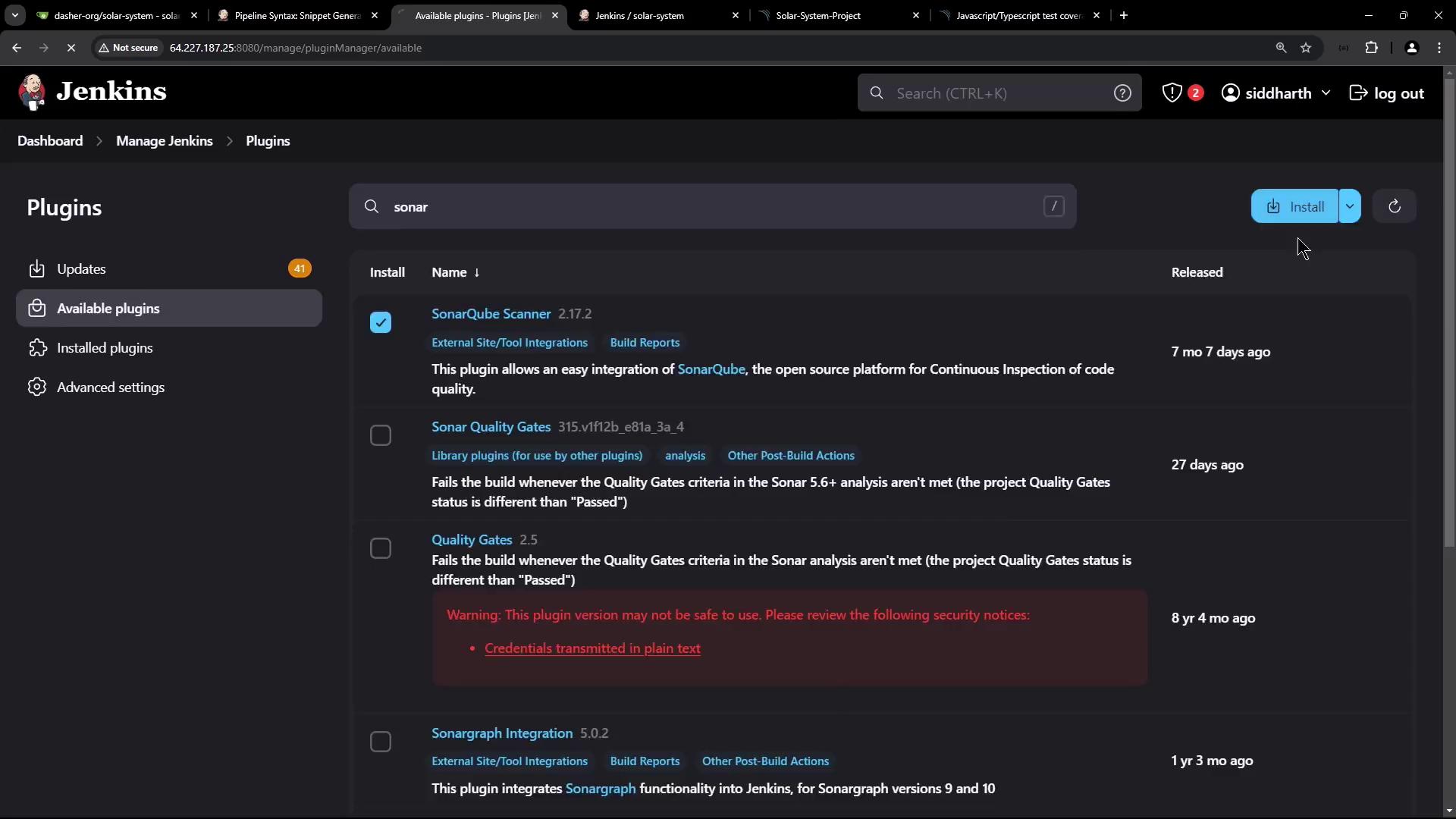
- Go to Manage Jenkins → Manage Plugins.
- Under Available, search for
sonarand install SonarQube Scanner. Restart Jenkins.
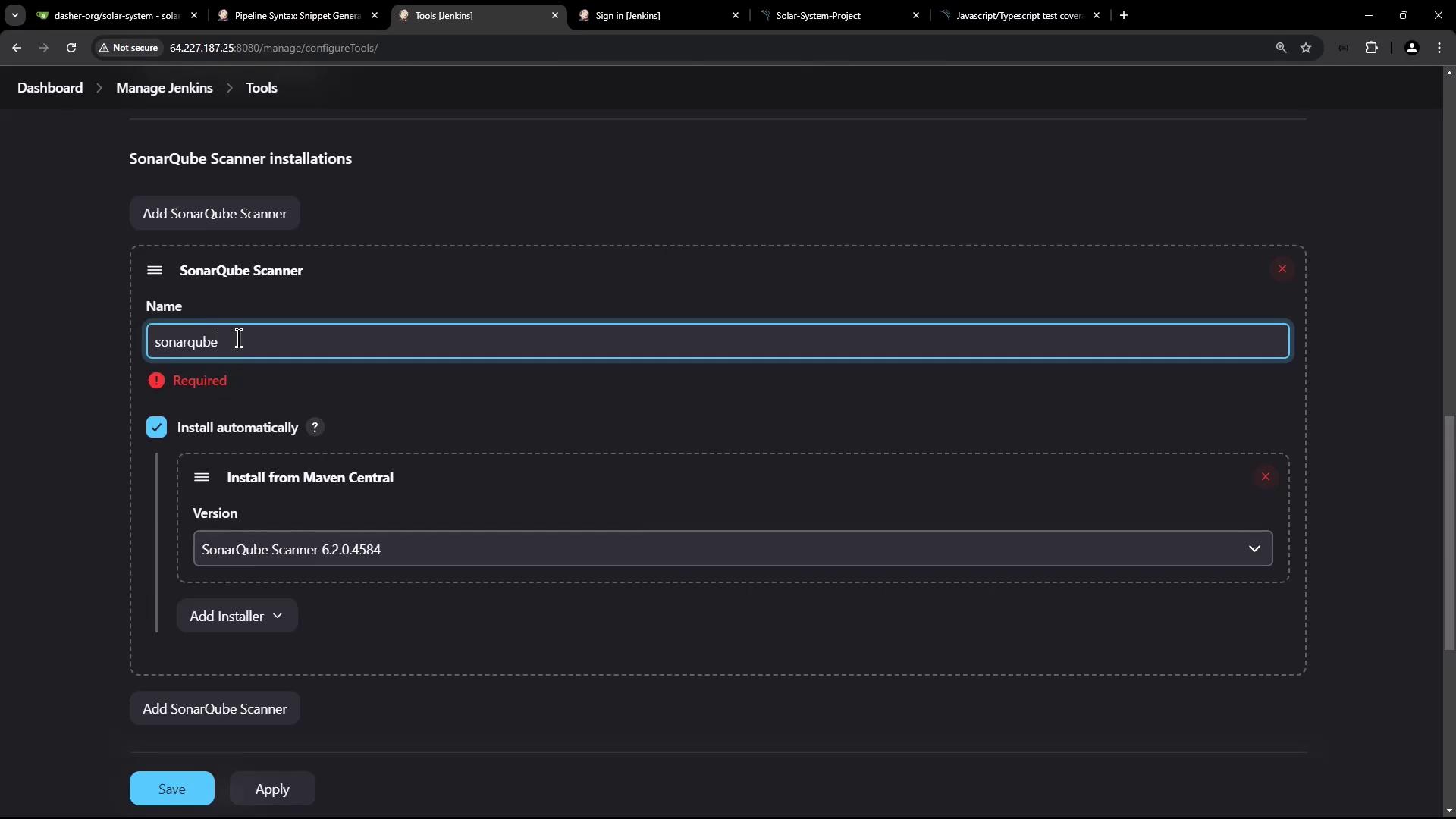
- After restart, navigate to Manage Jenkins → Global Tool Configuration → SonarQube Scanner.
- Name:
sonarqube-scanner-6.1.0 - Select Install automatically from Maven Central
- Name:
6. First SonarQube Analysis Result
Run your Jenkins pipeline. After it completes, refresh SonarQube:
ANALYSIS SUCCESSFUL, you can find the results at: http://<host>:9000/dashboard?id=Solar-System-Project
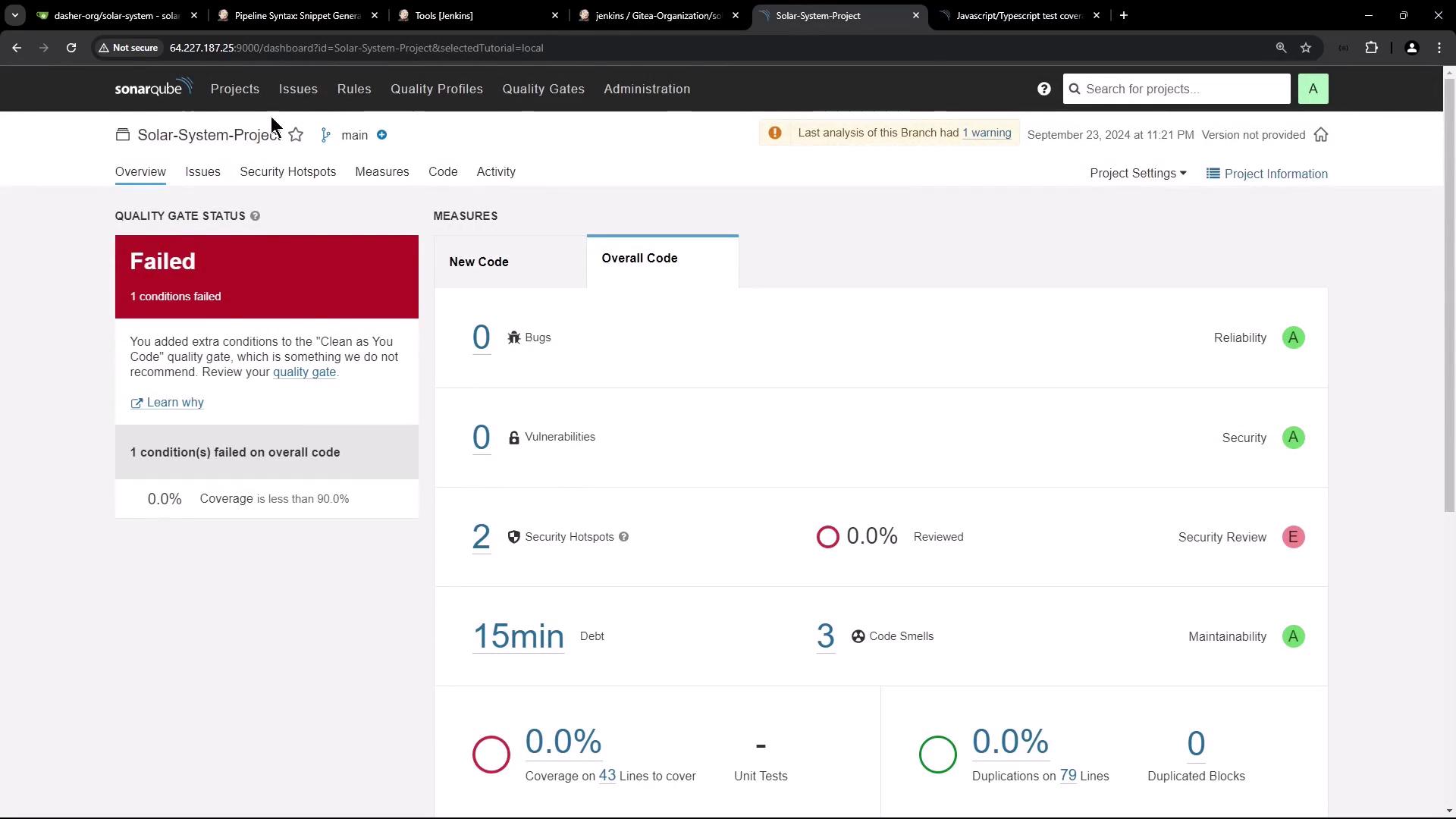
Coverage is reported as 0%, so the Quality Gate fails (coverage < 90%).
7. Adding Code Coverage Reports
Generate coverage before the SonarQube stage:
npm run coverageThis creates
./coverage/lcov.info.Import the report by updating the scanner command:
stage('SAST - SonarQube') { steps { sh 'echo $SONAR_SCANNER_HOME' sh """ $SONAR_SCANNER_HOME/bin/sonar-scanner \ -Dsonar.projectKey=Solar-System-Project \ -Dsonar.sources=app.js \ -Dsonar.host.url=http://<host>:9000 \ -Dsonar.javascript.lcov.reportPaths=./coverage/lcov.info \ -Dsonar.login=<YOUR_TOKEN> """ } }
After rerunning the pipeline, your coverage will appear (e.g., 73%) but still below 90%.
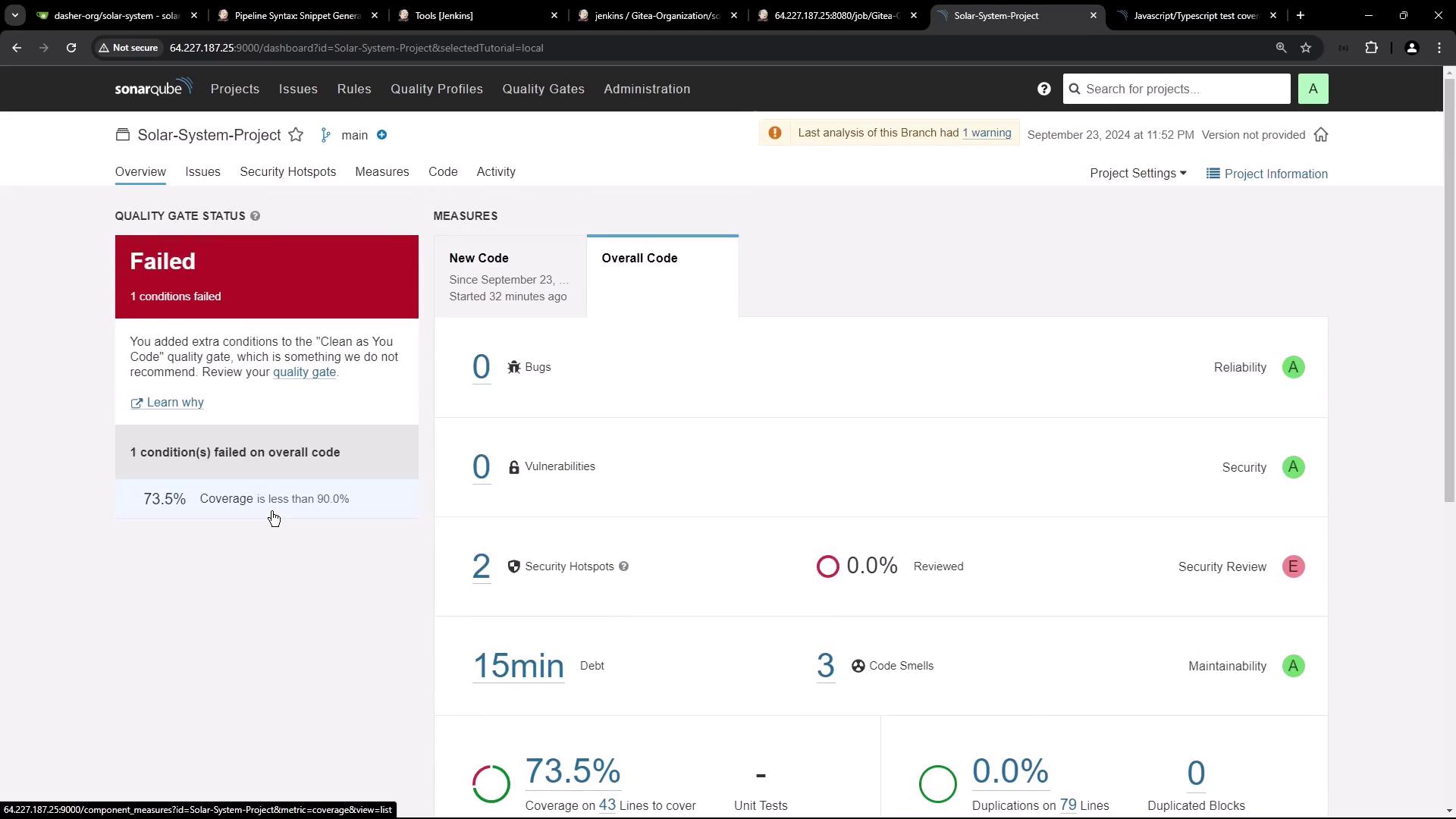
Note
Since SonarQube doesn’t return the Quality Gate status to Jenkins by default, your pipeline may remain green. In the next tutorial, we’ll configure the SonarQube Quality Gate plugin to fail builds when the gate fails.
Links and References
Watch Video
Watch video content