- A manual approval checkpoint after deploying the app via GitOps (Argo CD sync).
- A Dynamic Application Security Testing (DAST) step using OWASP ZAP.
What Is DAST?
Dynamic Application Security Testing (DAST) probes a live application for vulnerabilities like SQL injection and XSS. Instead of scanning source code (SAST), DAST injects malicious payloads at runtime to uncover weaknesses in a running service.
OWASP Zed Attack Proxy (ZAP)
OWASP ZAP is an open-source, community-driven web application scanner. It supports passive, active, and API scans.
ZAP Scan Modes
| Mode | Description |
|---|---|
| Baseline | Time-boxed passive scan |
| Full | AJAX Spider + active + passive scans |
| API | Scans OpenAPI/GraphQL/SOAP endpoints (our choice) |
zap-api-scan.py Usage
Install or use the Docker imageghcr.io/zaproxy/zaproxy to invoke zap-api-scan.py:
Integrating with Jenkins
Add the following stages to yourJenkinsfile:
| Stage | Purpose | Trigger |
|---|---|---|
| App Deployed? | Manual approval after Argo CD sync | PR branch |
| DAST – OWASP ZAP | Run ZAP API scan on deployed service | After approval |
1. App Deployed? (Manual Approval)
This stage pauses the pipeline until an operator merges your PR and syncs Argo CD.
The
input step blocks the pipeline until a user clicks Proceed or the timeout expires.2. DAST – OWASP ZAP
Once approved, execute ZAP against your live API:Sample OpenAPI Definition
Our service exposes/api/docs/ with this minimal spec:
Running the Pipeline
- Commit your
Jenkinsfilechanges and open a PR. - Jenkins triggers a new build:
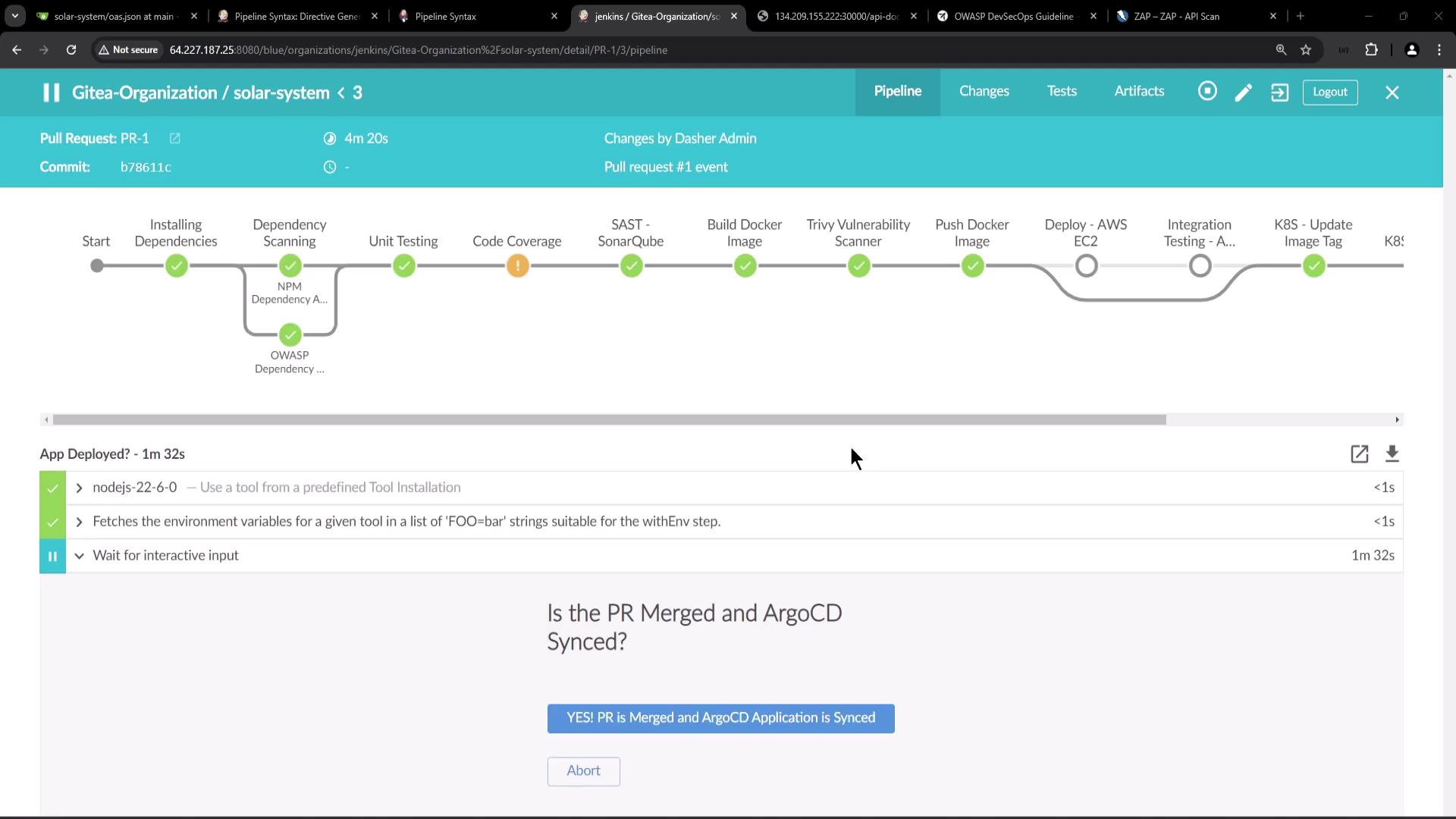
- App Deployed? waits for merge and Argo CD sync.
- Merge the PR:
- Sync your app in Argo CD:
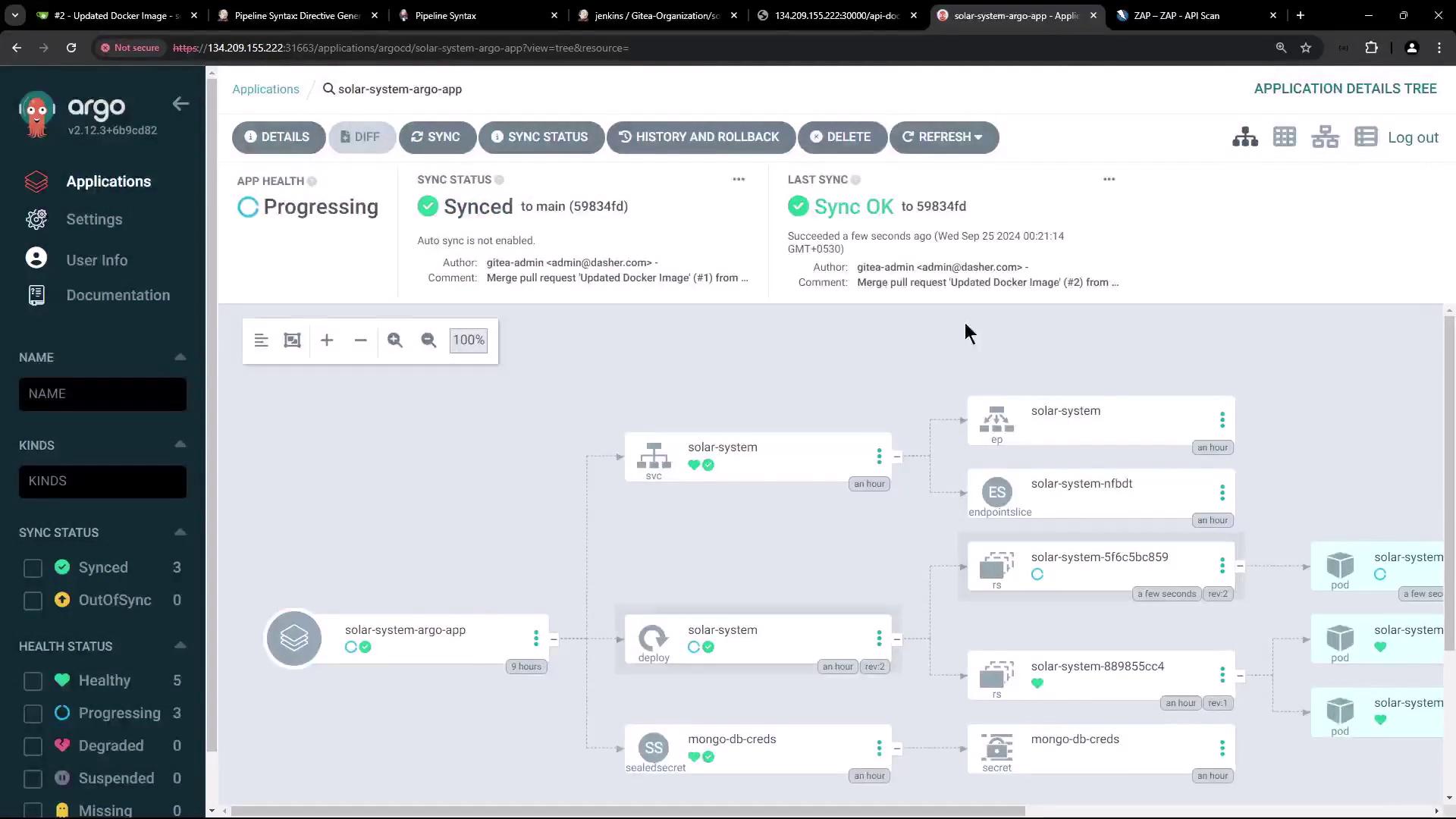
- Approve and let the pipeline proceed to the DAST stage. ZAP will scan and generate reports.
If ZAP detects critical issues or unexpected content types, it exits with a non-zero code, causing the stage (and pipeline) to fail. Adjust your
-c config or handle alerts as needed.