- NPM Audit (critical-level checks)
- OWASP Dependency-Check (via Jenkins plugin)
Table of Contents
- 1. NPM Dependency Audit
- 2. OWASP Dependency-Check Plugin
- 3. Running the Pipeline
- 4. Enforcing Quality Gates
- Conclusion
1. NPM Dependency Audit
Add an NPM audit stage to yourJenkinsfile:
npm install --no-auditinstalls dependencies without auditing.npm audit --audit-level=criticalchecks for critical vulnerabilities and exits1if found.
Sample package.json
CLI Output Example
NPM Audit supports four severity levels:
Adjust
low, moderate, high, and critical.Adjust
--audit-level based on your policy.2. OWASP Dependency-Check Plugin
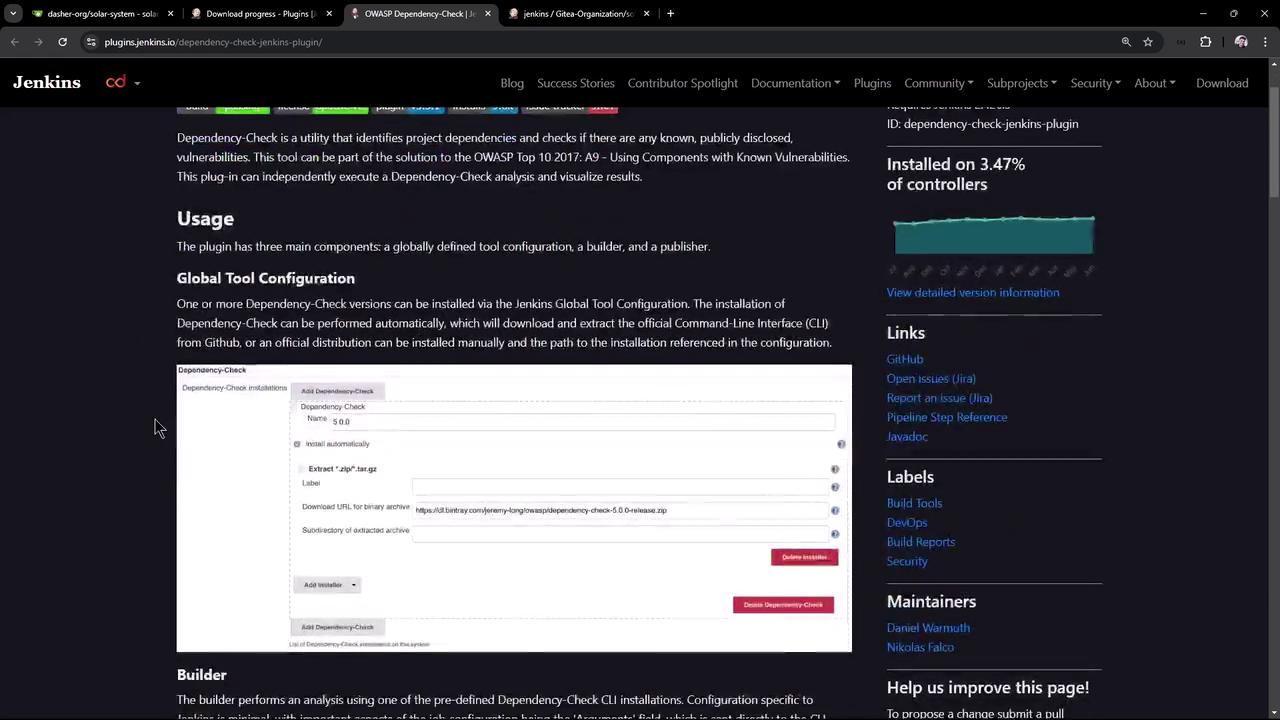
The OWASP Dependency-Check plugin scans multiple formats (HTML, XML, JSON, CSV) and supports quality gates.2.1 Install the Plugin
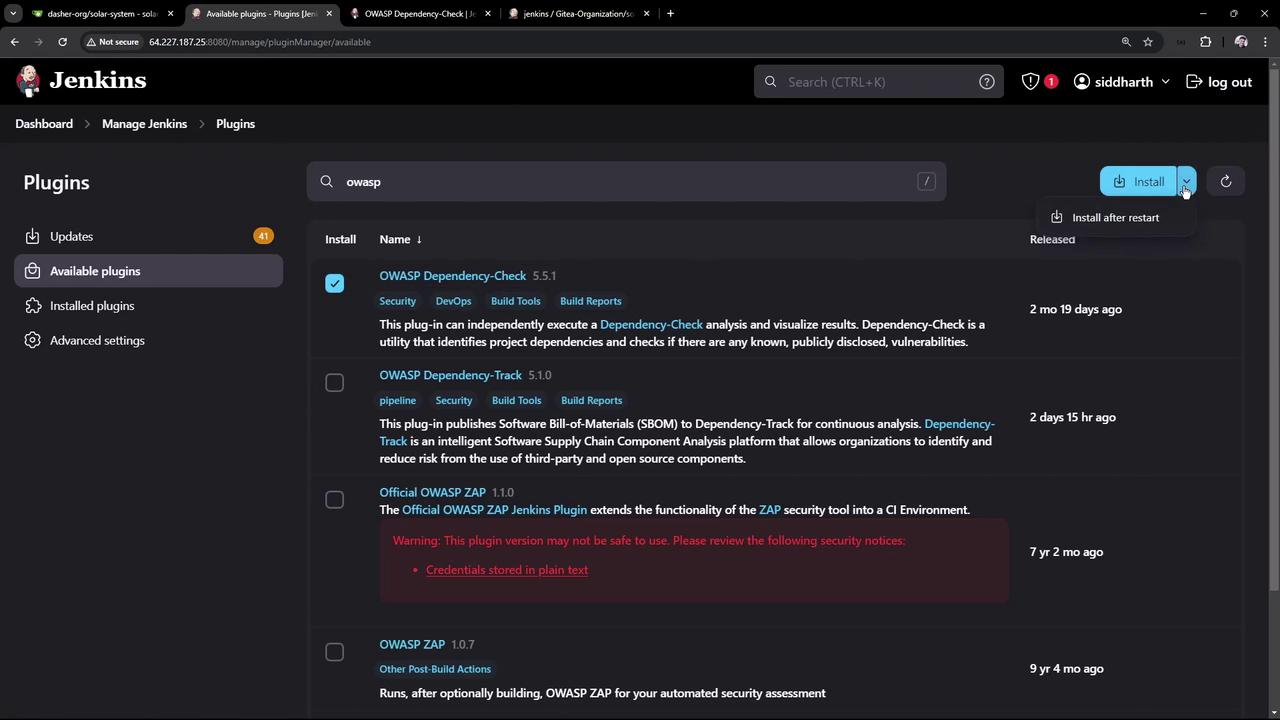
- Manage Jenkins > Manage Plugins > Available
- Search OWASP Dependency-Check, install, and restart.
2.2 Global Tool Configuration
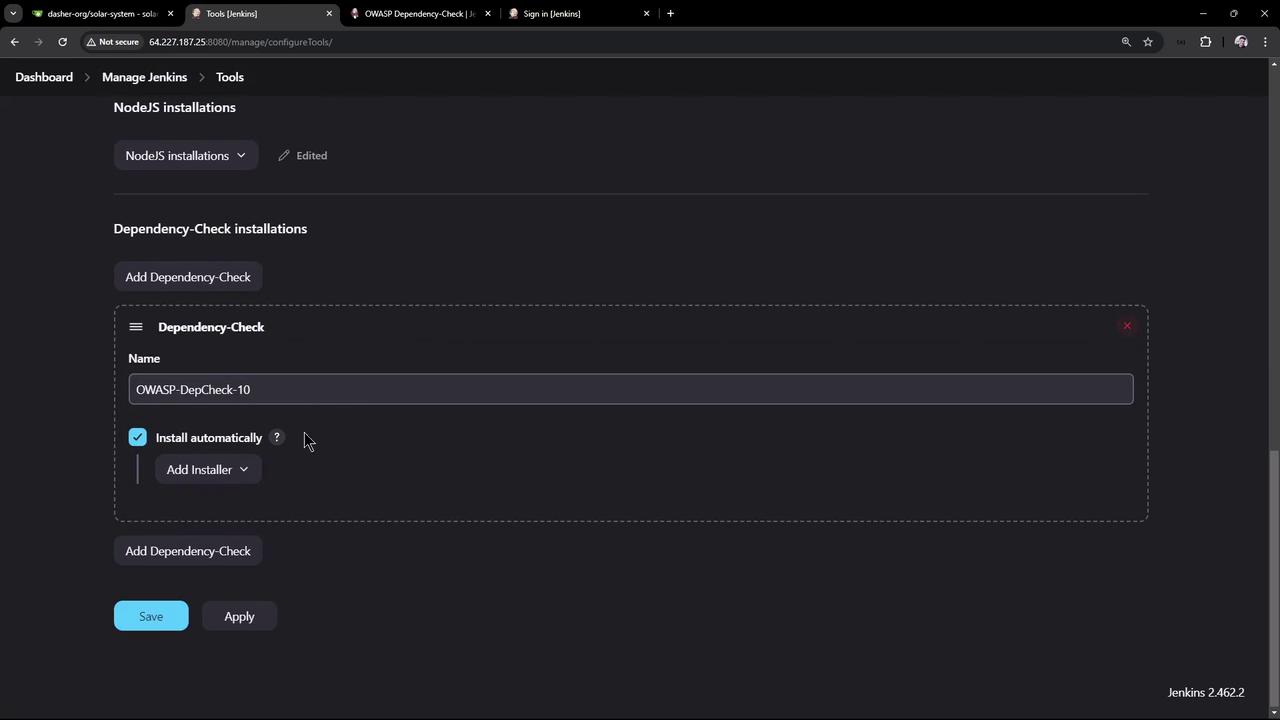
After restarting, go to Manage Jenkins > Global Tool Configuration.Add a Dependency-Check installation (e.g., version 10.0.3) and enable auto-install from GitHub.
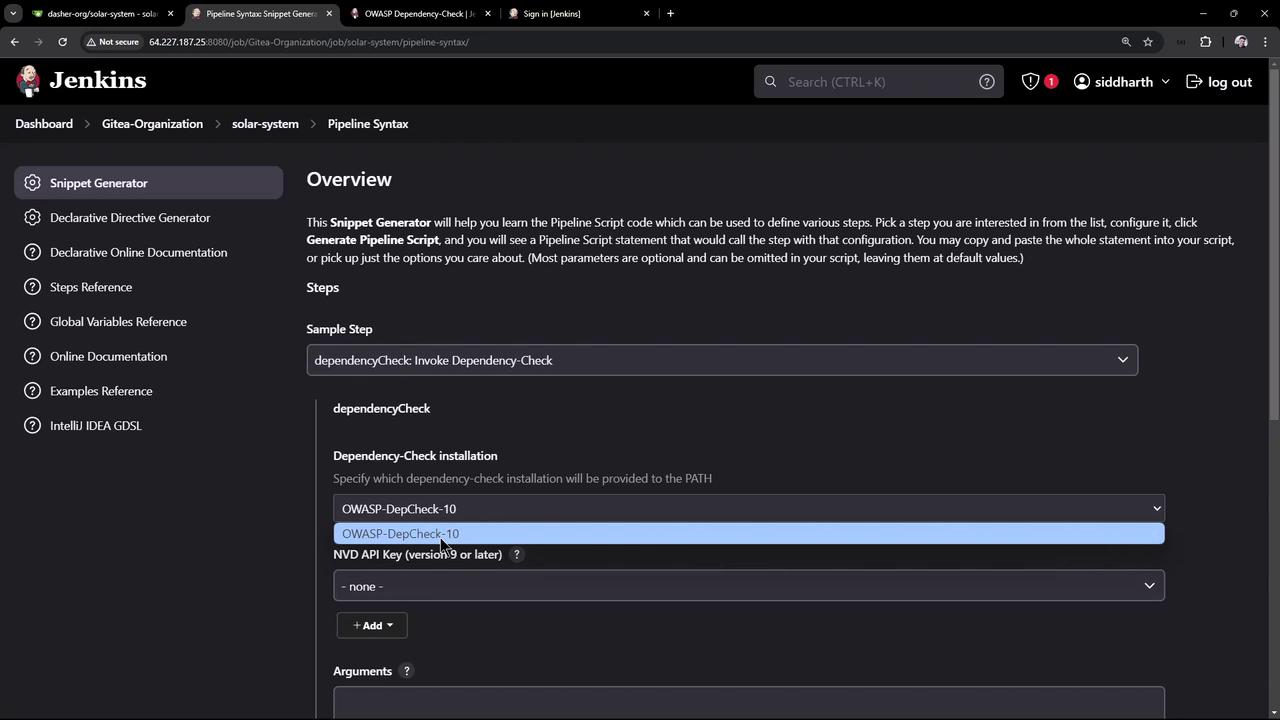
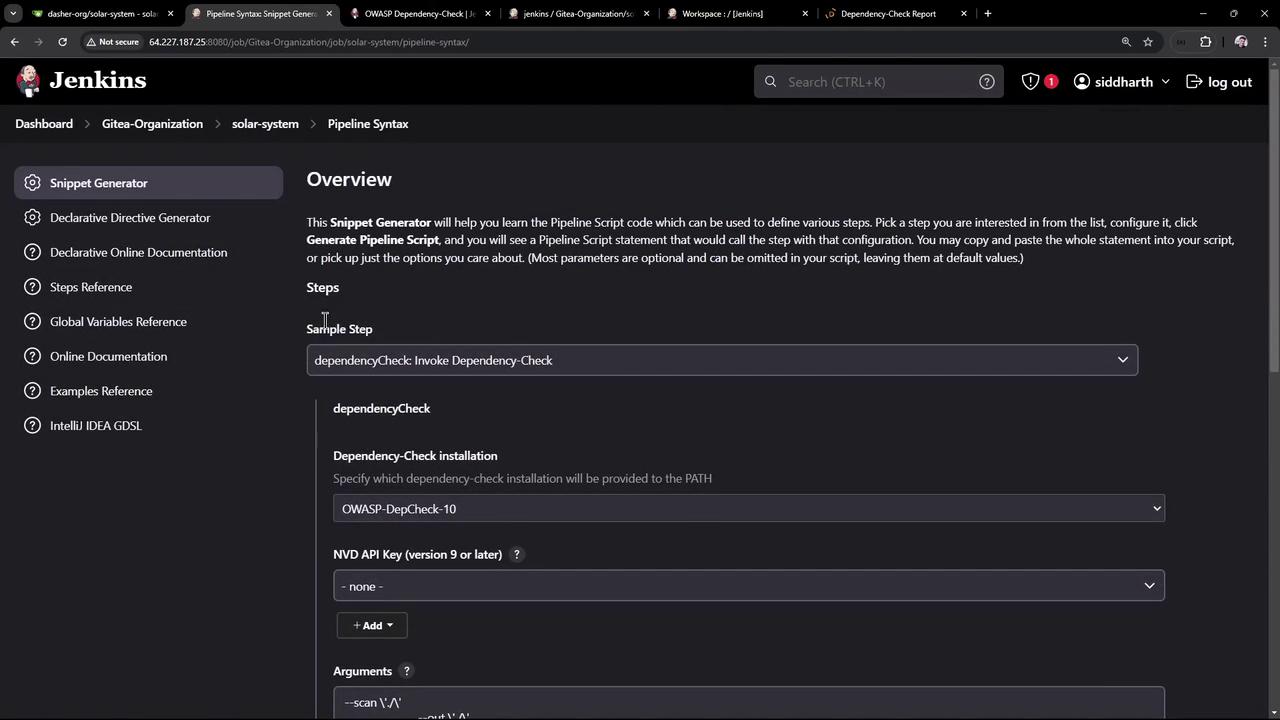
2.3 Generate Pipeline Snippet
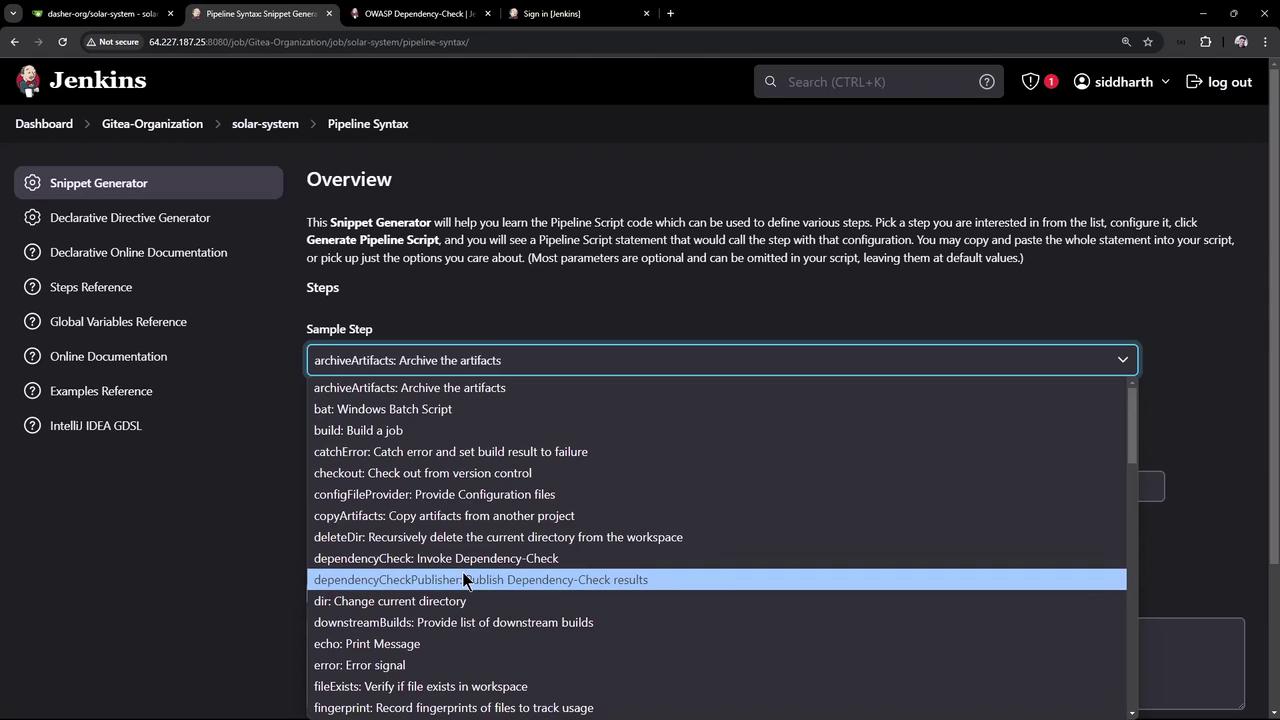
In Pipeline Syntax > Snippet Generator:- Step: Invoke Dependency-Check
- Installation:
OWASP-DepCheck-10 - Arguments:
Jenkinsfile:
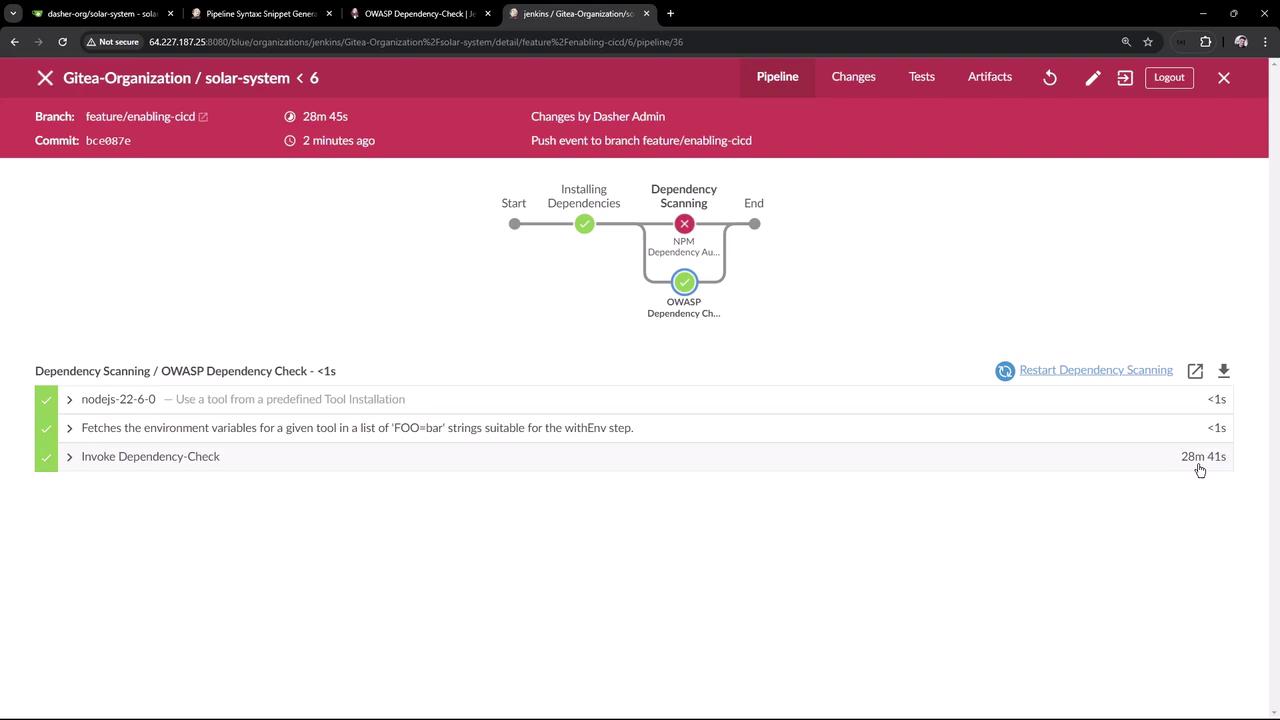
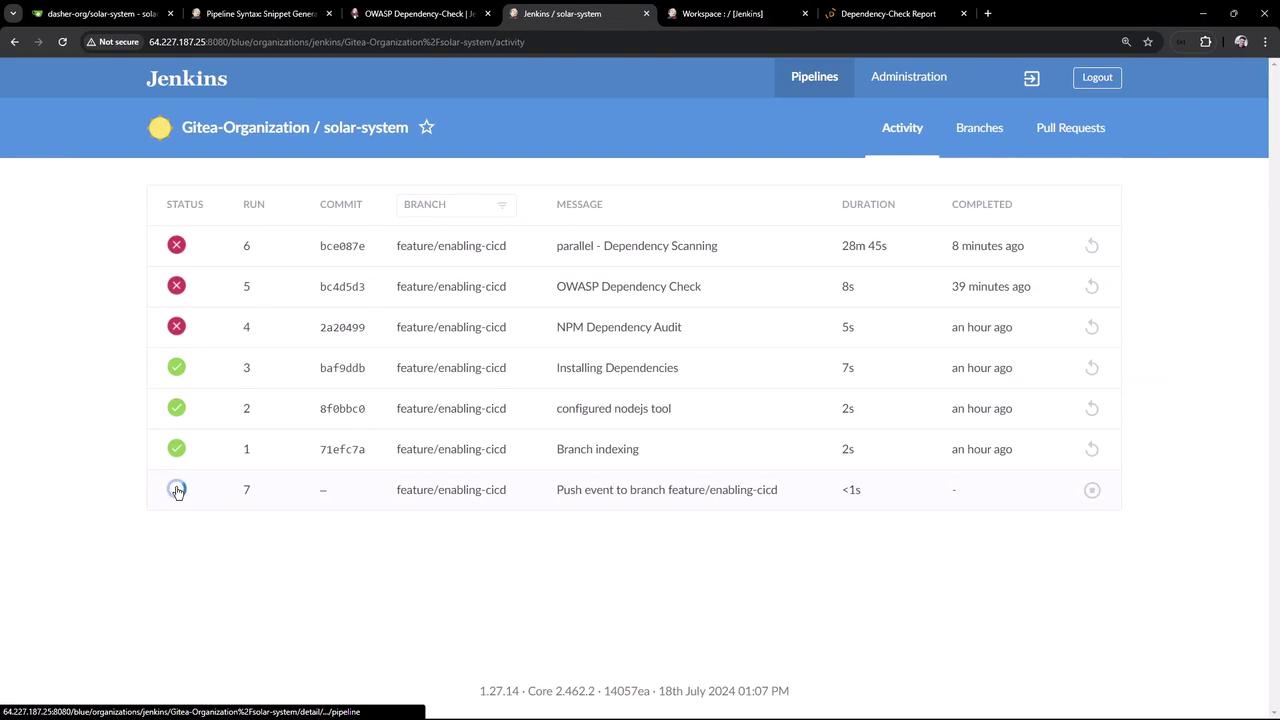
3. Running the Pipeline
Commit and push yourJenkinsfile. The first run downloads the NVD database (~263 000 records), taking about 20–30 minutes. Look for logs like:
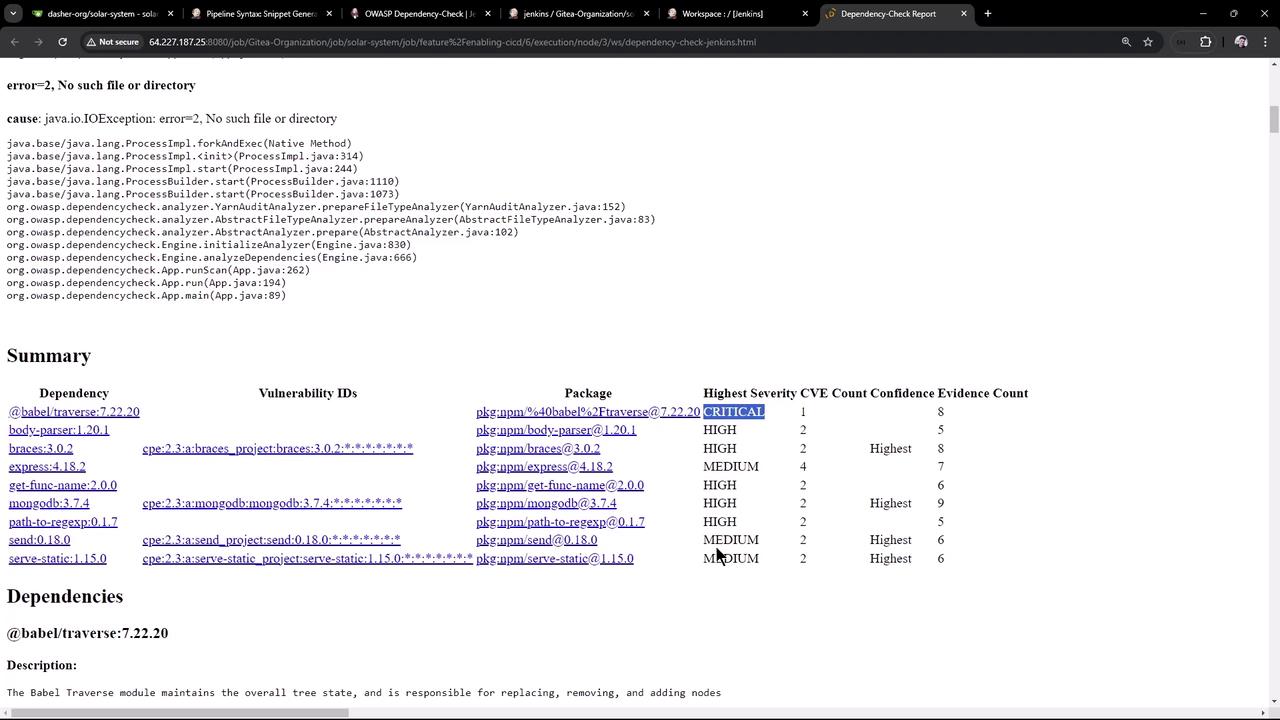
| Format | File Name |
|---|---|
| HTML | dependency-check-report.html |
| XML | dependency-check-report.xml |
| JSON | dependency-check-report.json |
| CSV | dependency-check-report.csv |
4. Enforcing Quality Gates
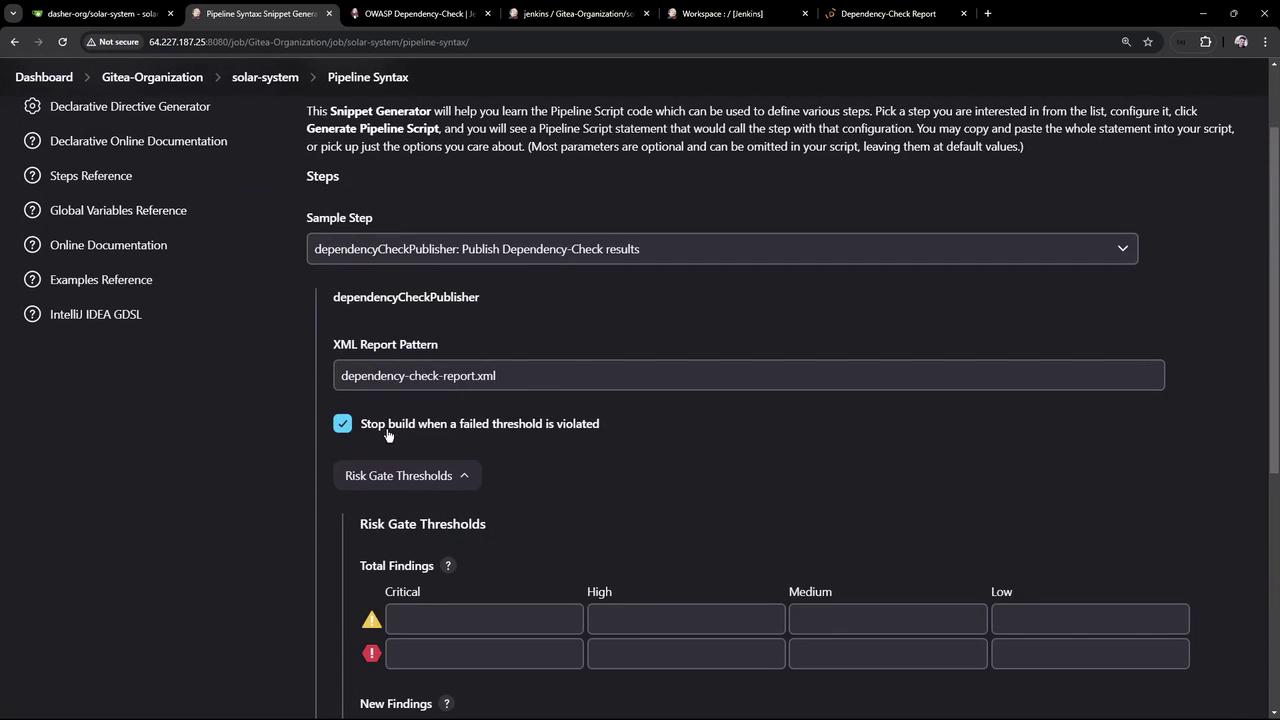
Fail builds if thresholds are exceeded:- In Snippet Generator, select Publish Dependency-Check results
- Configure:
- XML report pattern:
dependency-check-report.xml - Stop build on threshold violation
- Failed total critical:
1
- XML report pattern:
Builds will now fail if
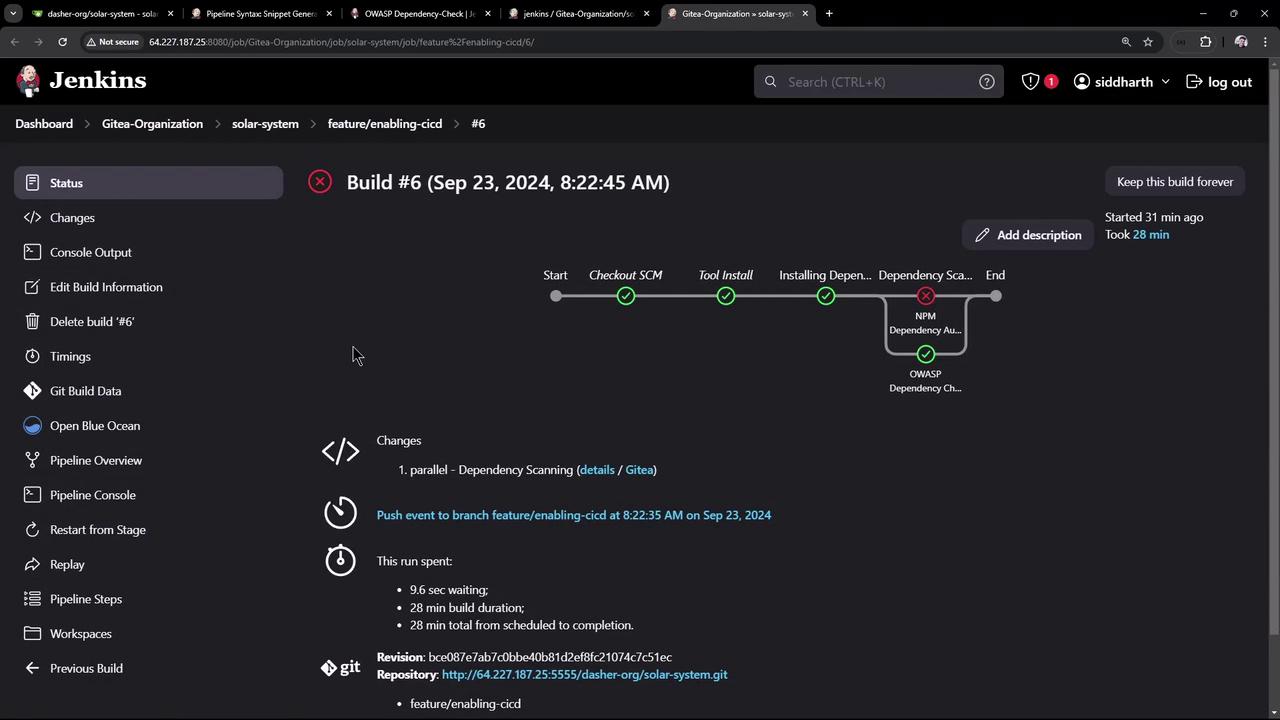
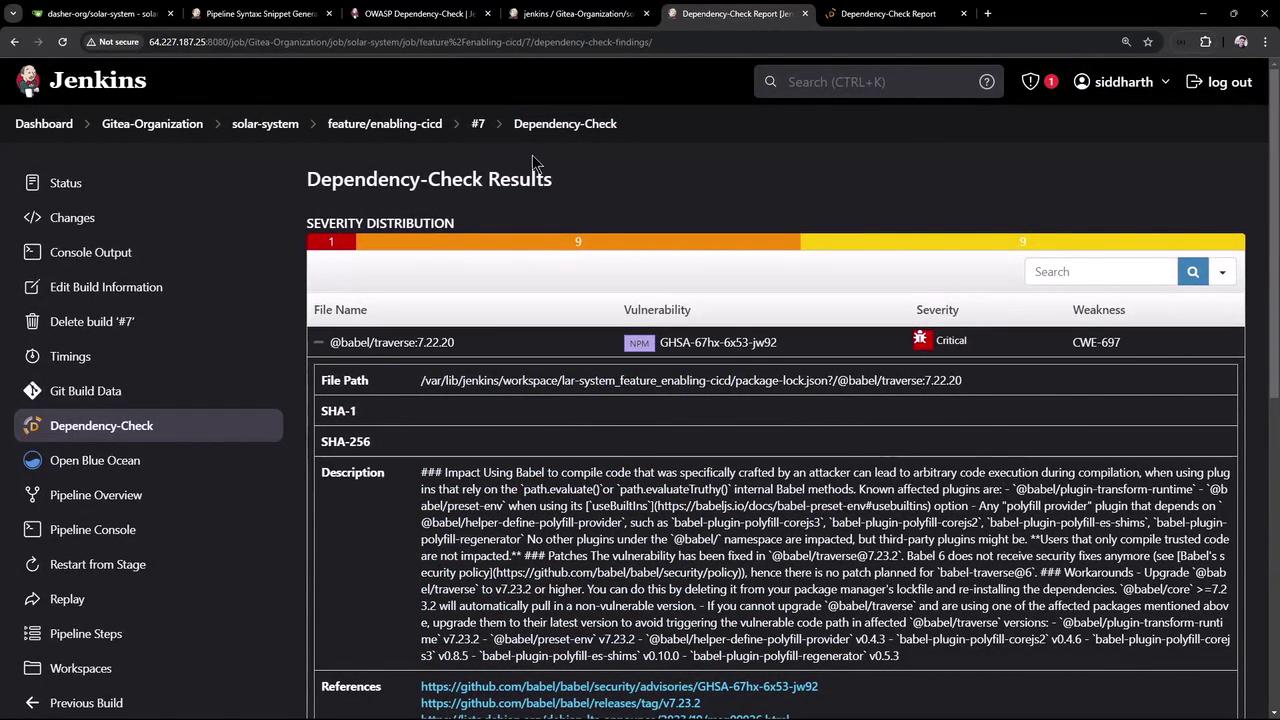
Review detailed results in the Jenkins UI to remediate issues.
critical vulnerabilities exceed your defined threshold.Review detailed results in the Jenkins UI to remediate issues.
Conclusion
In this guide, we have:- Integrated NPM Audit to catch critical Node.js vulnerabilities.
- Configured OWASP Dependency-Check for comprehensive scanning.
- Parallelized both stages to reduce build time.
- Enforced quality gates to automatically fail on critical findings.