- Enforces coding standards automatically
- Fails builds on critical issues
- Provides real-time feedback on code smells, bugs, and vulnerabilities
Prerequisites
| Requirement | Details |
|---|---|
| SonarQube Scanner for Jenkins (v2.13.1+) | Installed via Manage Plugins |
| SonarQube instance | Accessible URL (Community, Developer, or Enterprise edition) |
| Jenkins webhook | Configured in SonarQube Administration → Webhooks |
| Jenkins credentials | SonarQube auth token added as a Secret Text credential |
Ensure you have administrative access in both Jenkins and SonarQube to configure plugins, credentials, and webhooks.
1. Verify SonarQube Scanner Plugin
In Jenkins, navigate to Manage Jenkins → Manage Plugins, then open the Installed tab to confirm: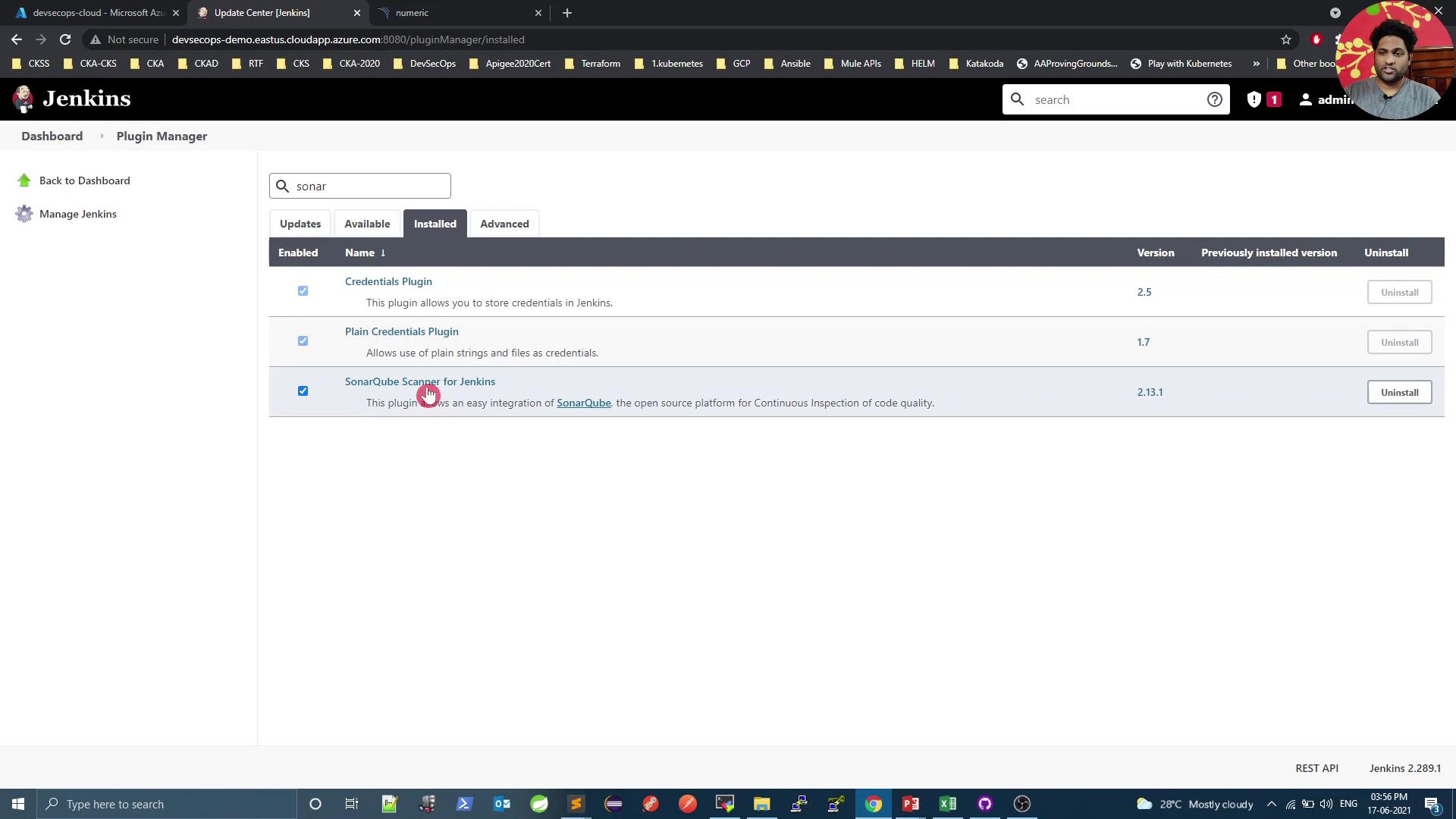
2. Configure SonarQube Server in Jenkins
- In your SonarQube user profile, generate an authentication token.
- In Jenkins, go to Credentials → System → Global credentials and add a new Secret Text credential with your token:
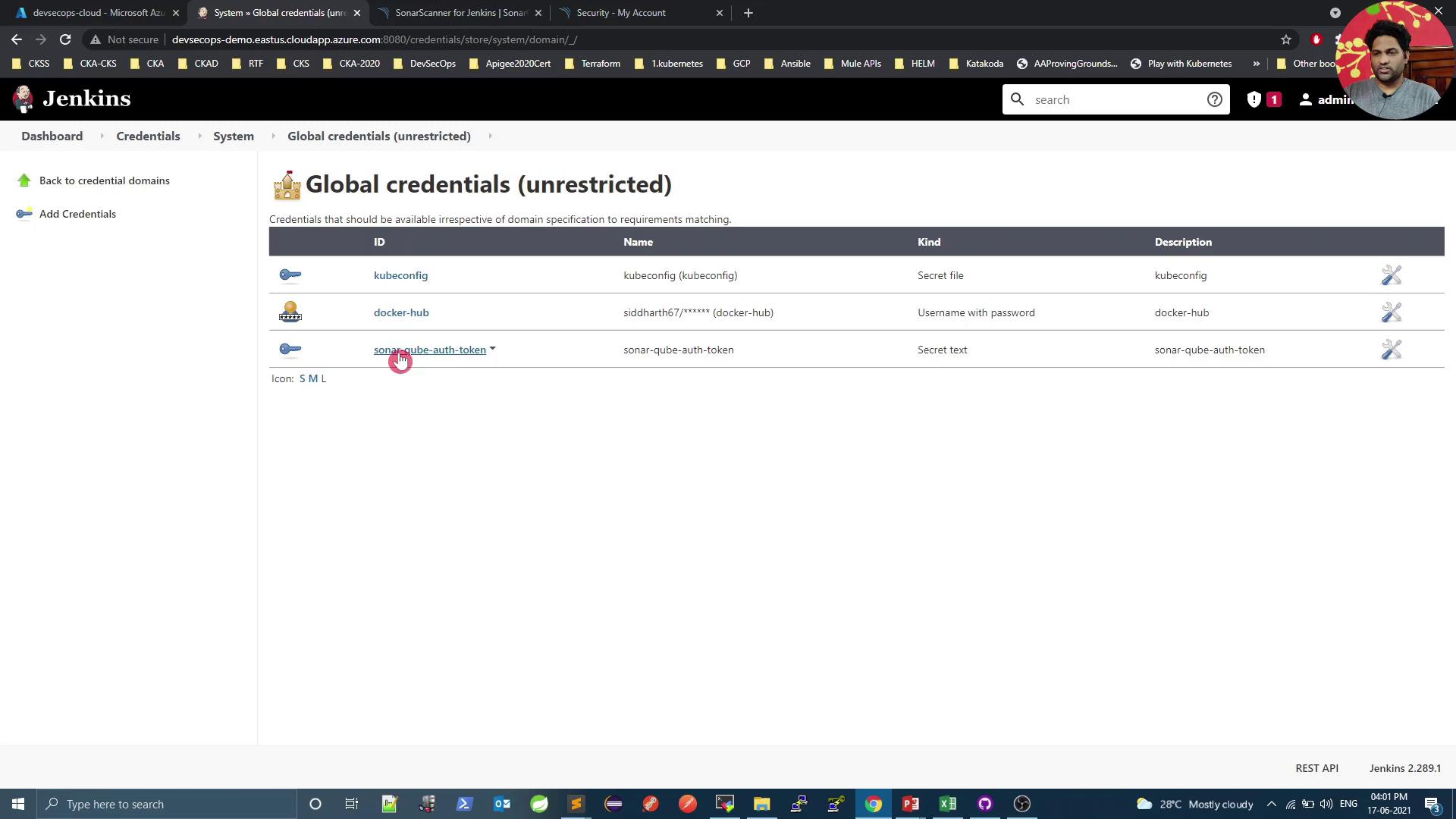
-
Still under Manage Jenkins → Configure System, scroll to SonarQube servers and add:
- Name: SonarQube
- Server URL:
https://<your-sonarqube-host> - Server authentication token: Select your Secret Text credential
3. Add SonarQube Webhook
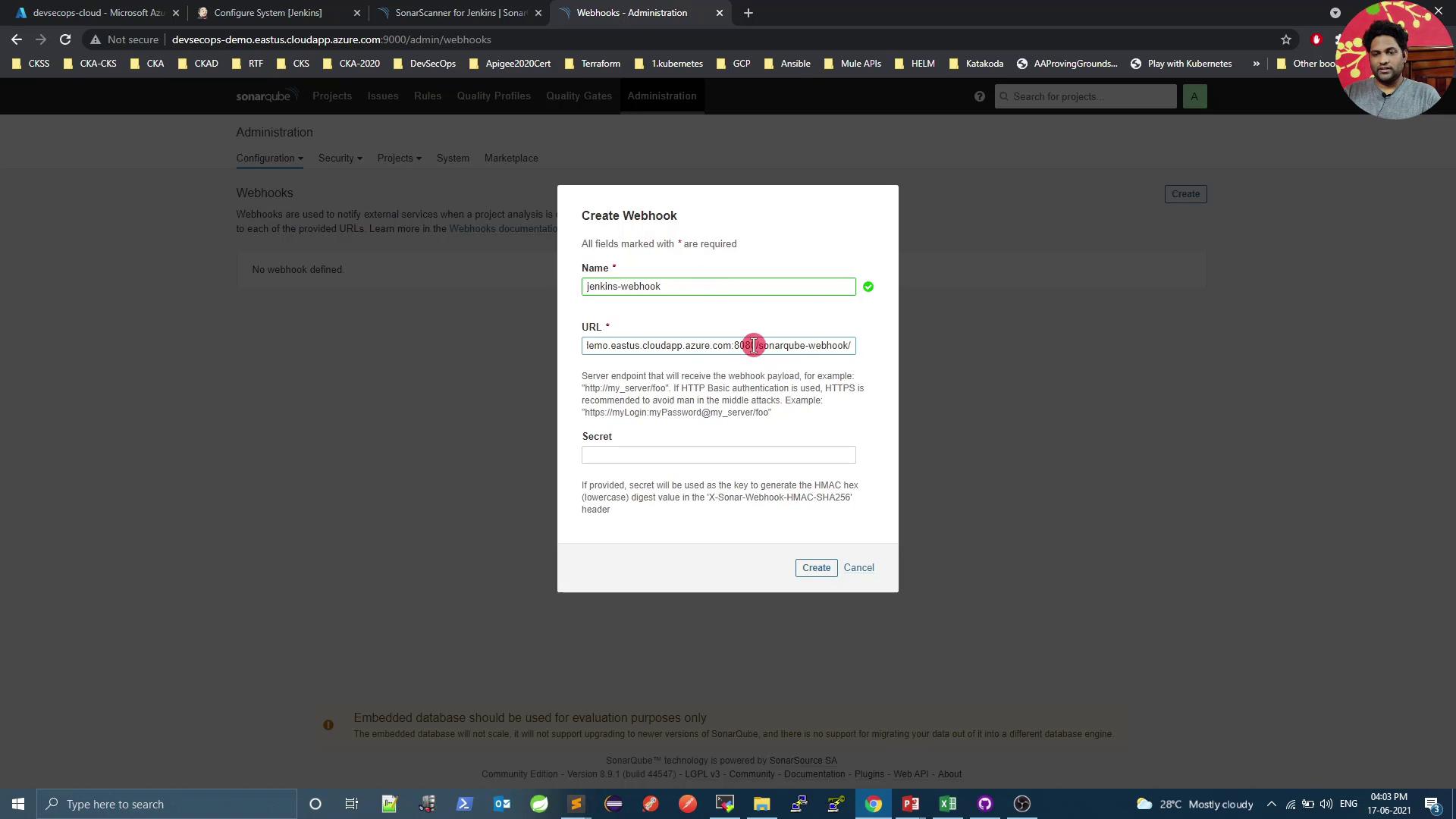
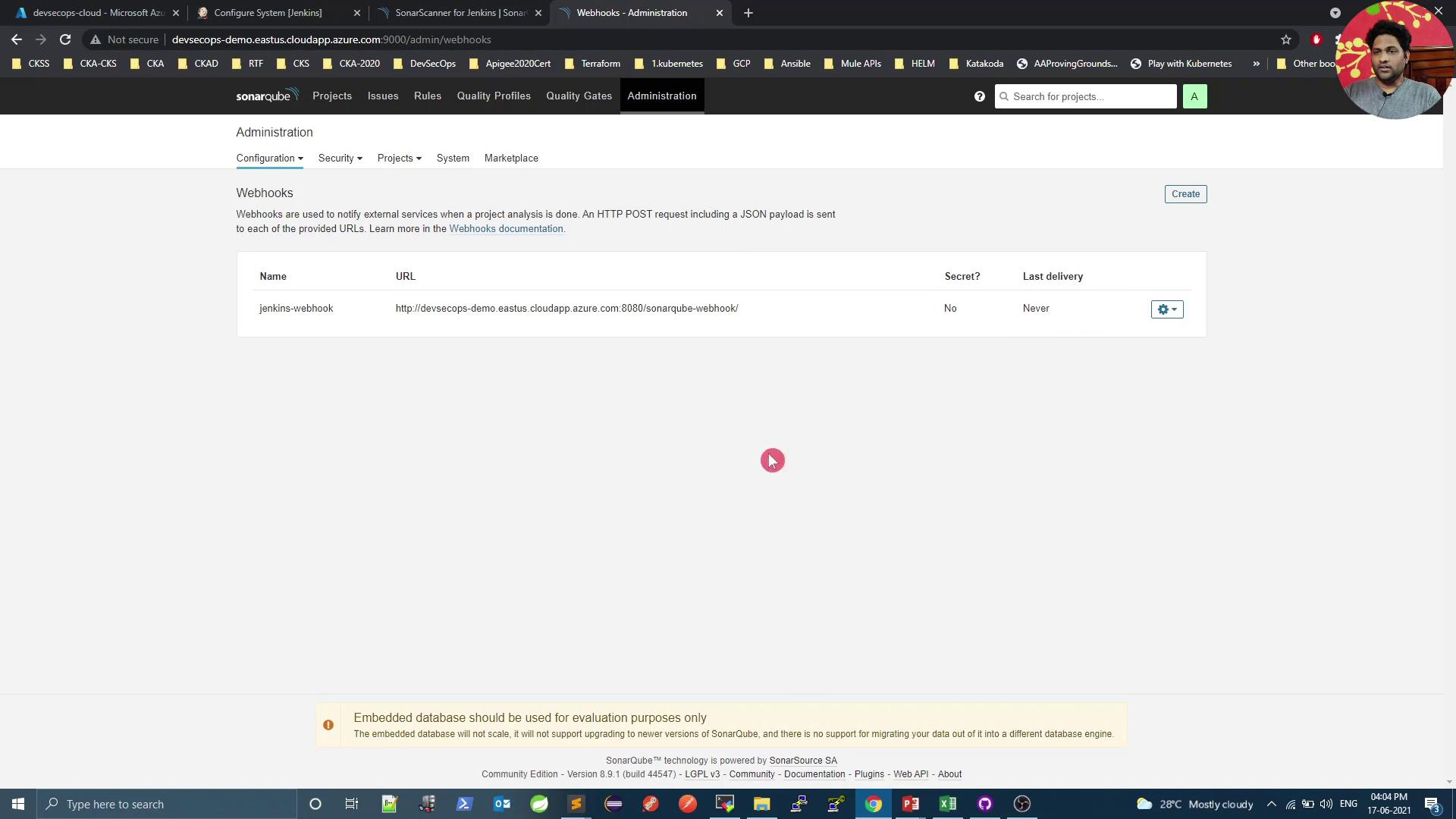
In SonarQube, go to Administration → Configuration → Webhooks:- Name: Jenkins webhook
- URL:
https://<your-jenkins-host>/sonarqube-webhook/ - (Optional) Secret if you want to secure payloads
4. Create Declarative Jenkins Pipeline
Place the following Jenkinsfile at the root of your repository. It:- Checks out source code
- Runs Maven build & SonarQube analysis
- Waits for the quality gate result (
abortPipeline: truestops the build on failure) - Builds and pushes a Docker image
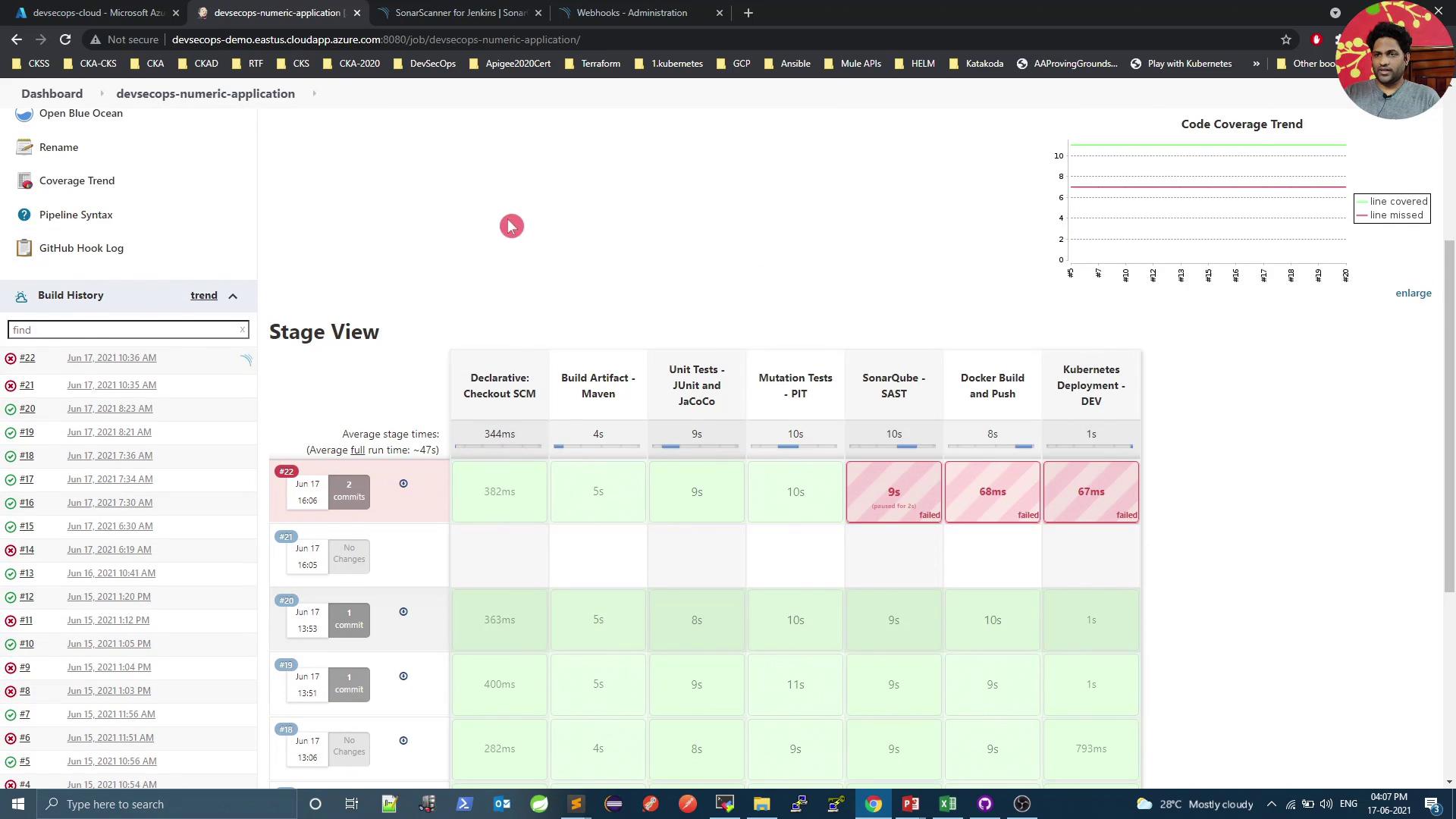
If the quality gate fails, the pipeline will abort at the Quality Gate stage. Inspect and resolve all reported issues before retrying.
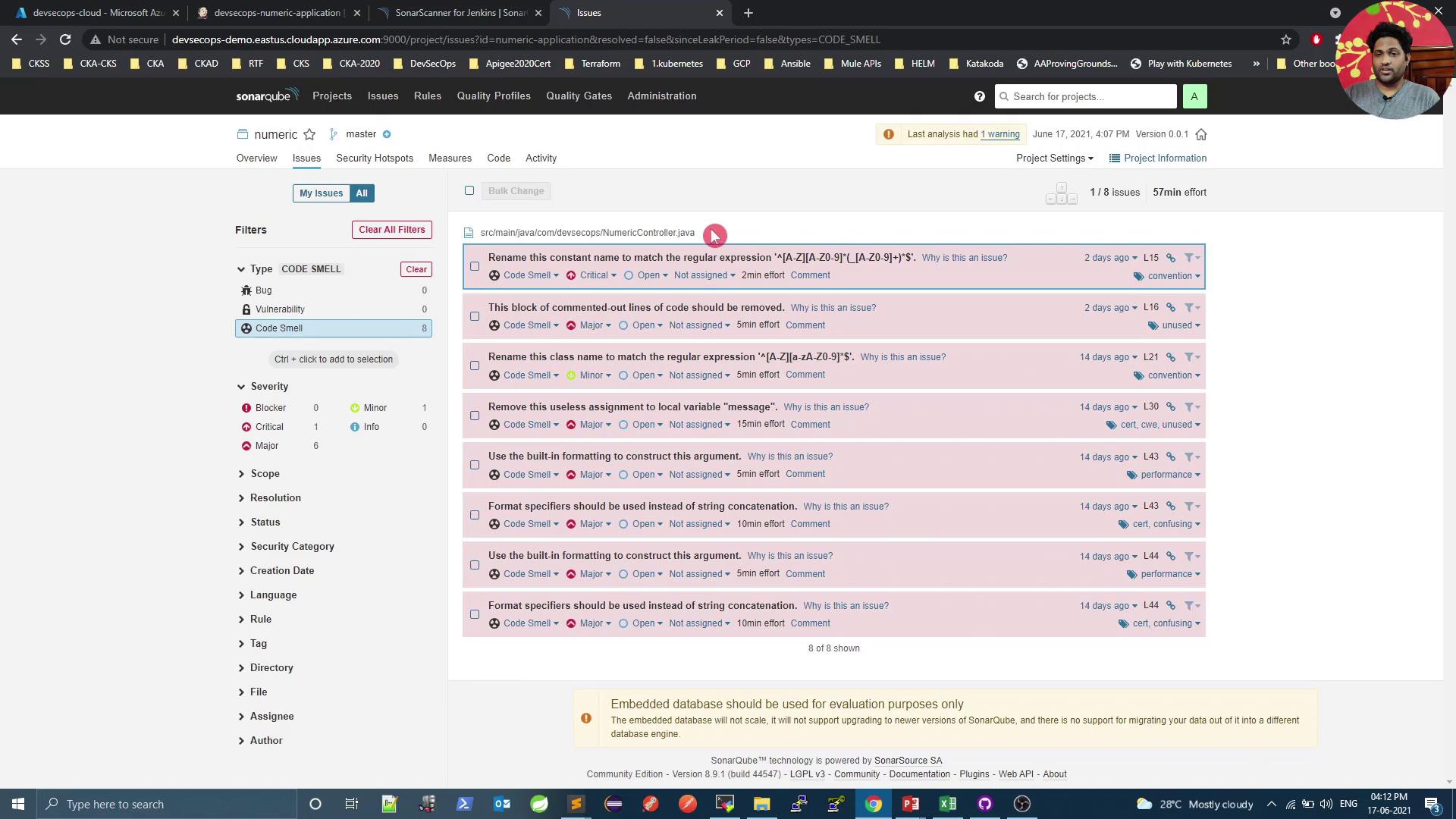
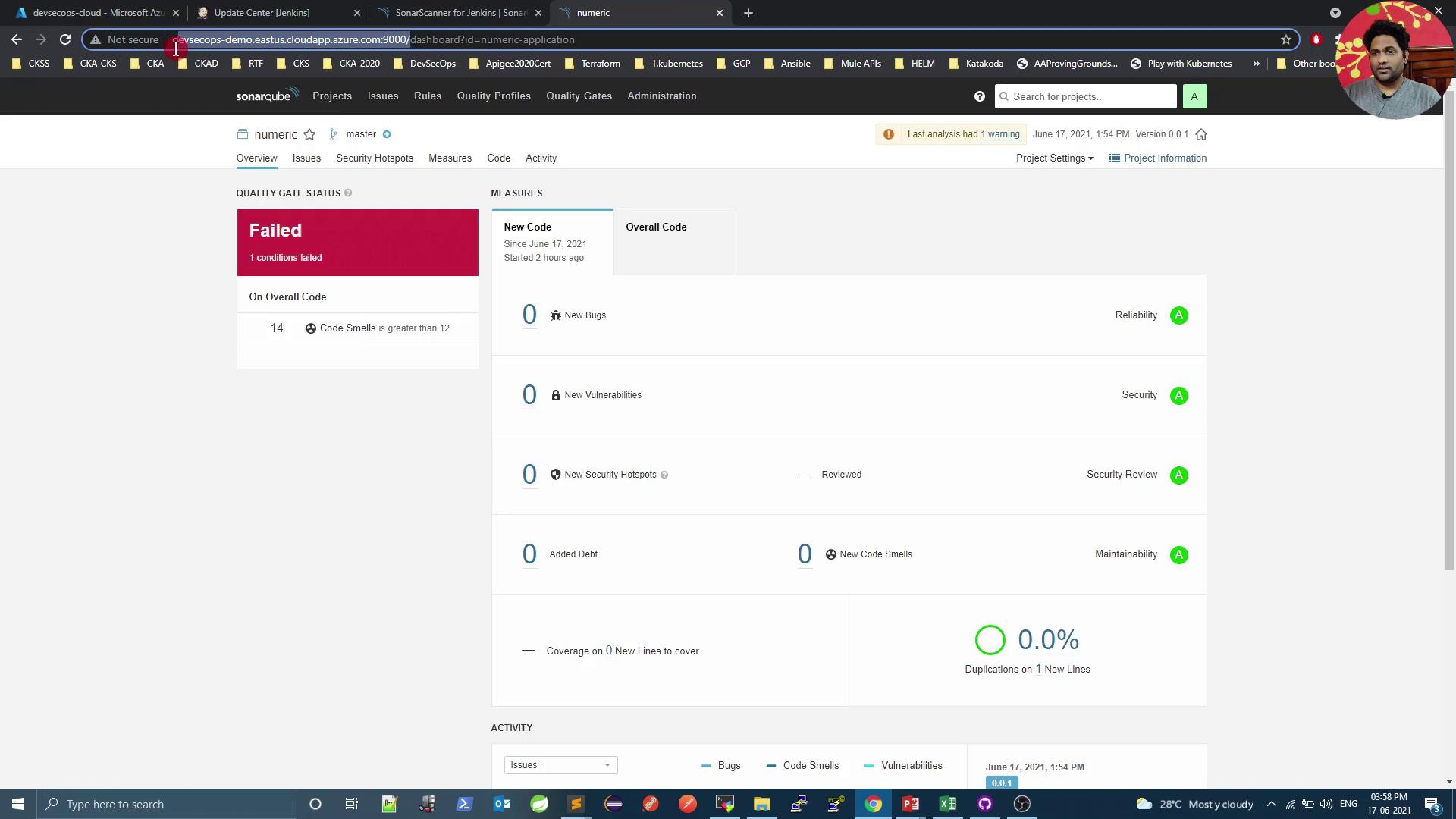
5. Diagnose Quality Gate Failures
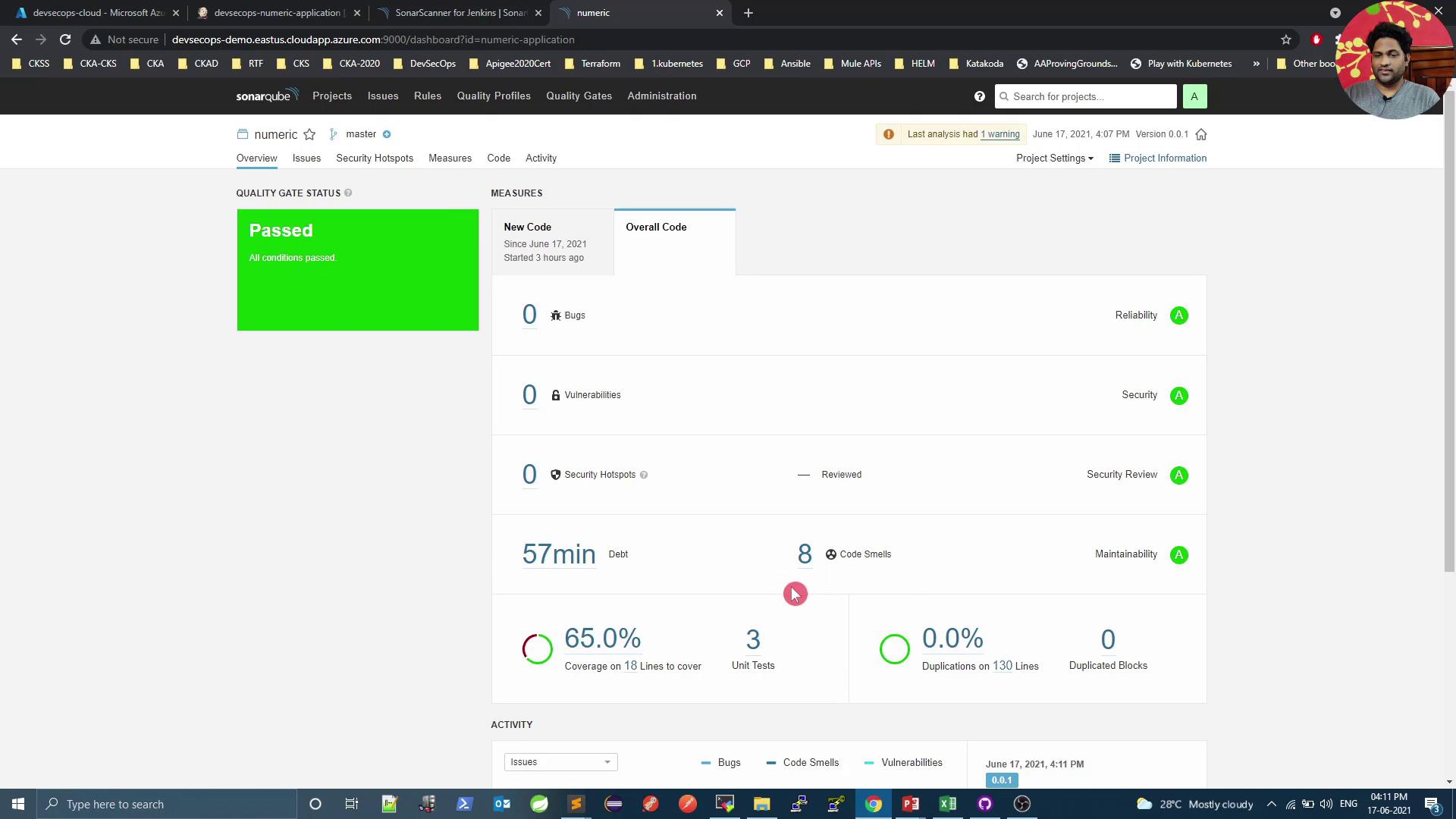
When the pipeline fails at the gate, open SonarQube to see detailed issues:
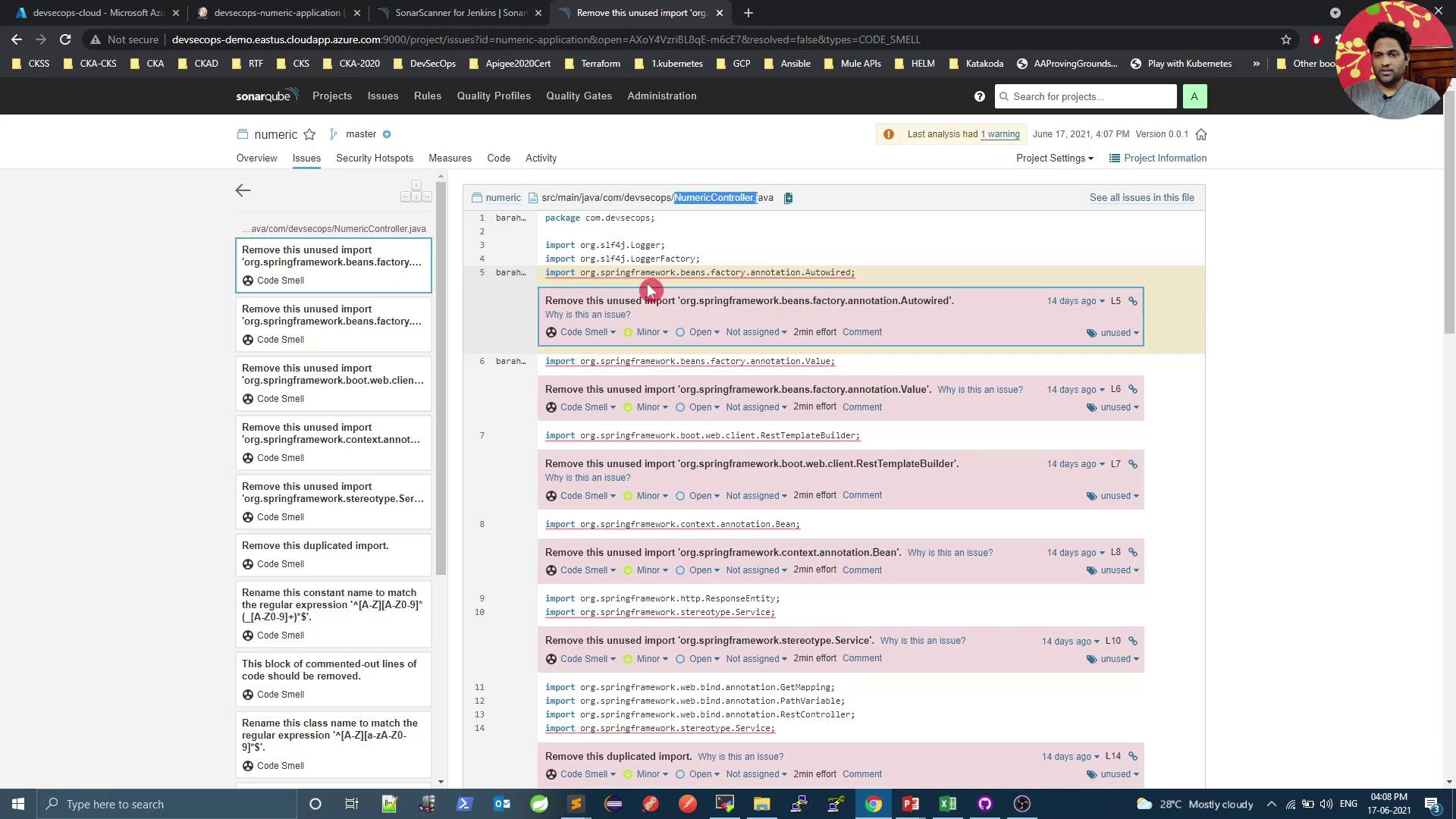
6. Confirm Quality Gate Pass
After addressing issues, trigger a new build. A successful SonarQube analysis will pass the gate: