DevSecOps - Kubernetes DevOps & Security
Kubernetes Operations and Security
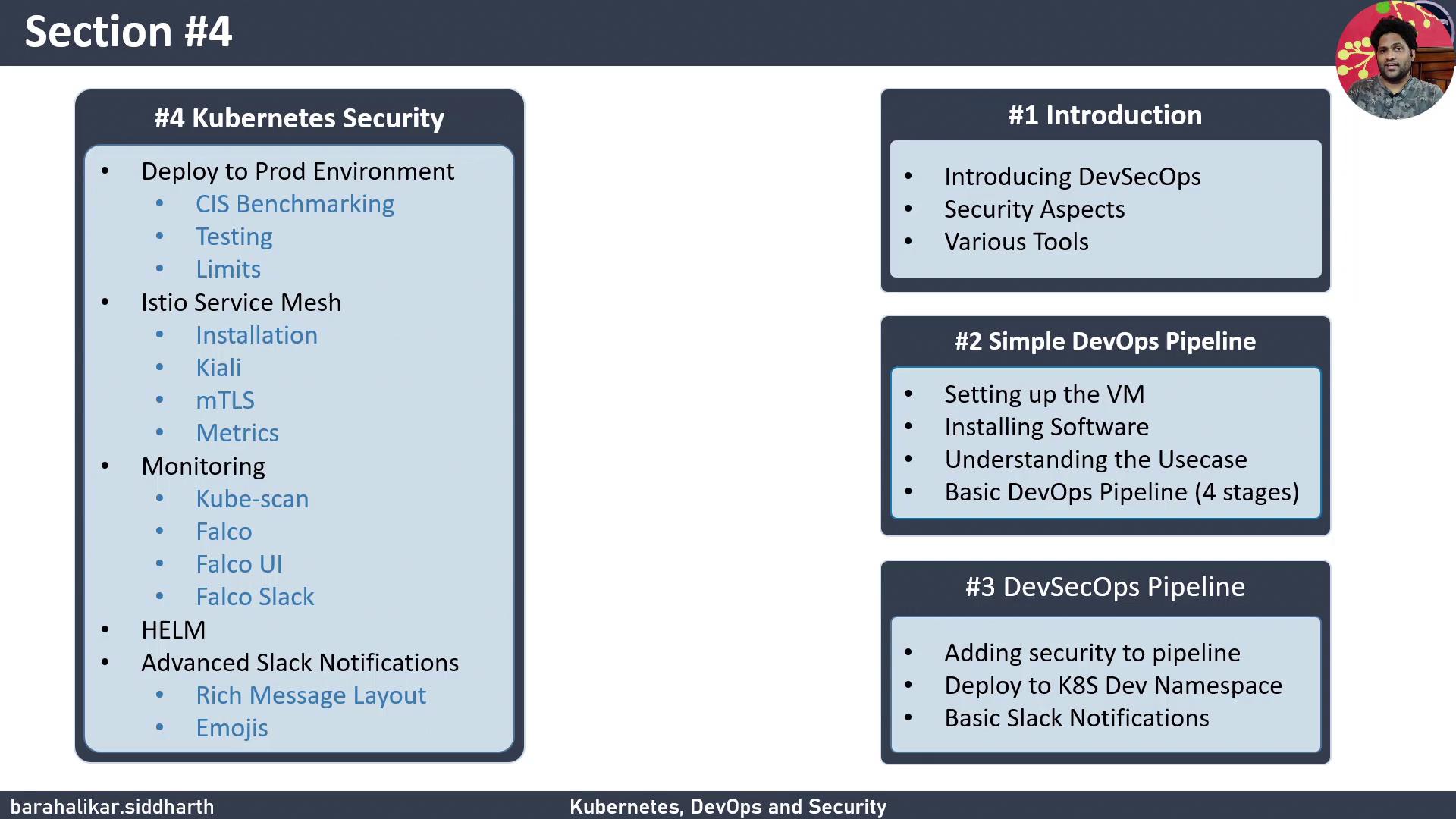
Section 4 Topics
In this section, we’ll build on our existing CI/CD workflow by integrating security, observability, and notification features. You will learn how to:
- Integrate a CIS benchmark scan into your Jenkins pipeline
- Deploy the application into a dedicated Kubernetes production namespace
- Enforce mutual TLS and policy-driven traffic using Istio
- Monitor runtime security and compliance with Falco and KubeScan
- Publish detailed, content-rich notifications to Slack
Prerequisites
Ensure you have the following already set up before proceeding:
- A Jenkins server with pipeline-as-code enabled
- Access to a Kubernetes cluster (production namespace created)
kubectl,helm, and Istio CLI (istioctl) installed and configured- Slack App credentials with incoming-webhook permissions
| Step | Tool(s) | Purpose |
|---|---|---|
| 1. CIS Benchmarking | cis-scanner | Validate cluster configuration against CIS guidelines |
| 2. Kubernetes Deployment | kubectl, Helm | Deploy your app to the production namespace |
| 3. Istio Traffic Security | Istio | Enable mTLS and policy enforcement |
| 4. Cluster Monitoring | Falco, KubeScan | Real-time security alerts and compliance checks |
| 5. Slack Notifications | Slack API | Send structured pipeline updates and alerts |
That's it for this overview. Let’s dive into Task 1: adding a CIS benchmarking stage to our Jenkins pipeline.
Links and References
Watch Video
Watch video content