Docker Certified Associate Exam Course
Docker Engine Enterprise
RBAC in Docker Enterprise
Role-Based Access Control (RBAC) is a security mechanism that defines which subjects can perform specific operations on resources. In Docker Enterprise, RBAC is configured through the Universal Control Plane (UCP) console, enabling fine-grained access control across both Docker Swarm and Kubernetes environments.
Subjects
A subject is the actor requesting access. Docker Enterprise supports these subject types:
- User: An individual account with credentials and profile information.
- Team: A logical grouping of users for shared permissions.
- Organization: A higher-level grouping of teams.
- Service Account: A Kubernetes object enabling workloads to authenticate to the cluster.
Note
Service Accounts are Kubernetes-native identities used by pods and controllers. They allow automation to interact with the API without human credentials.
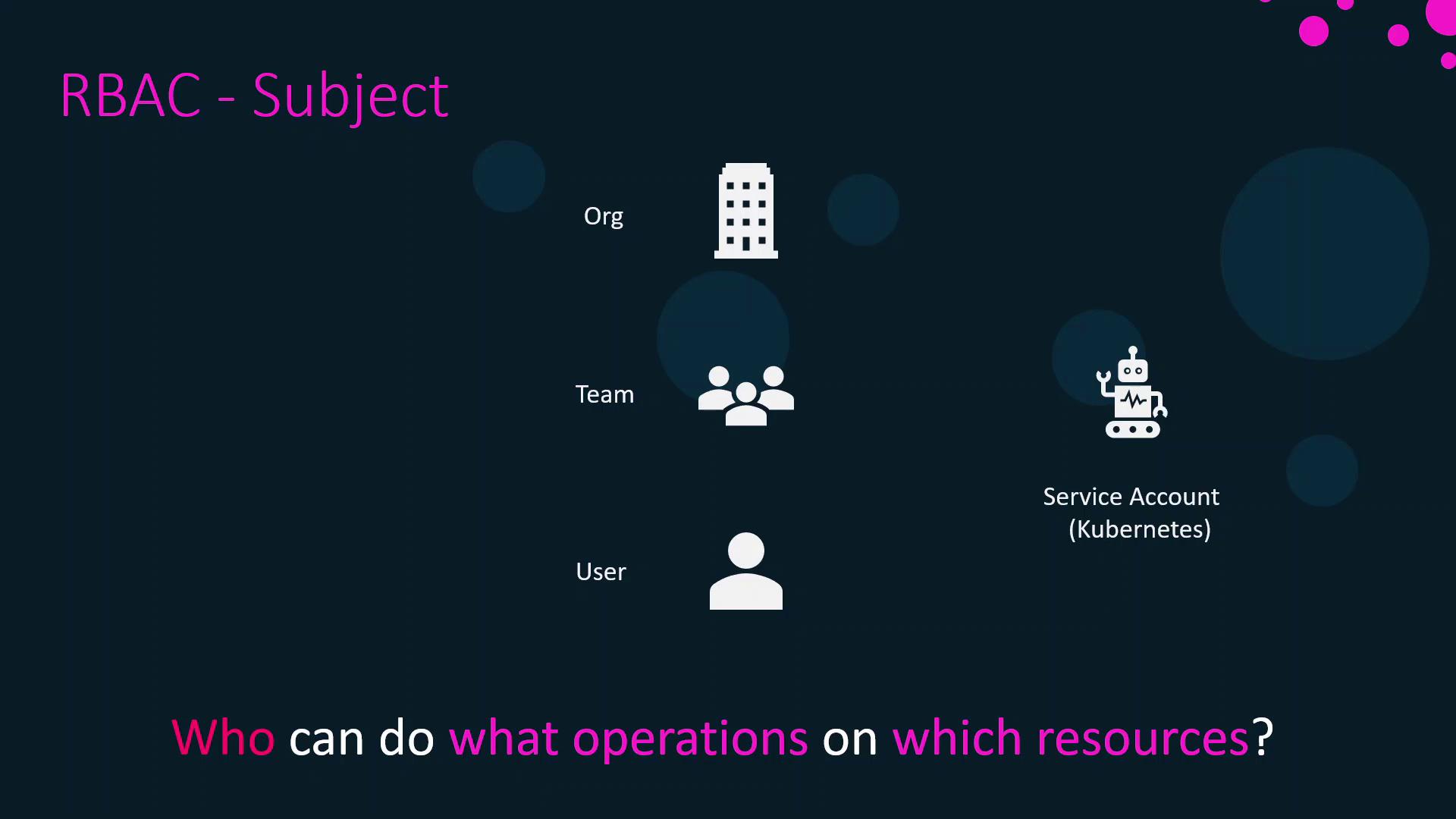
You can manage subjects in the UCP console under Account Management by creating users, teams, organizations, or service accounts.
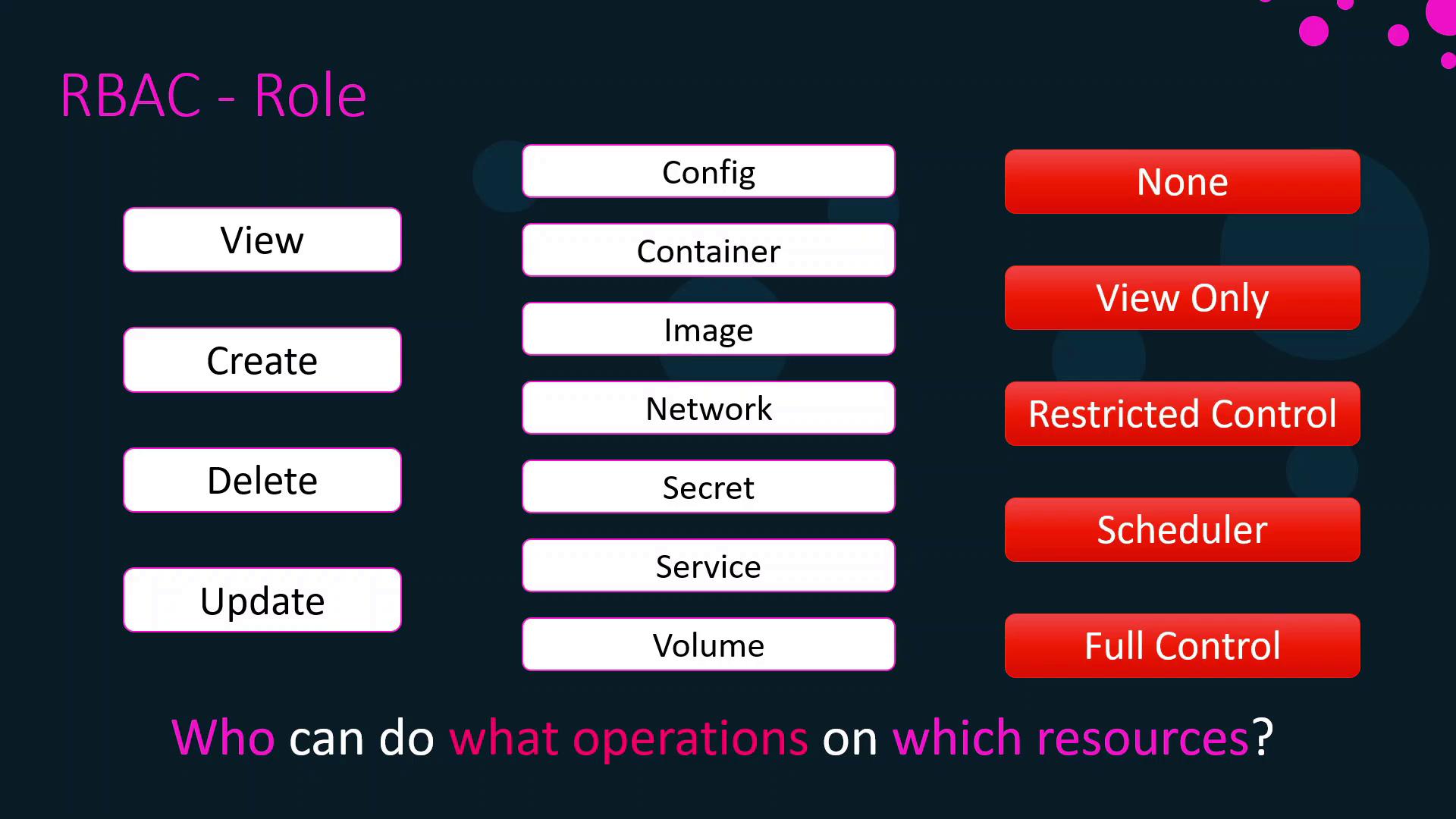
Roles
A role specifies which operations a subject can execute on particular resource types. Common operations include:
- View (read-only)
- Create
- Update
- Delete
Resources span Docker and Kubernetes objects—such as configs, containers, images, networks, secrets, services, and volumes. You can group multiple resource-operation pairs into custom roles.
Built-in roles in Docker Enterprise:
| Role Name | Description |
|---|---|
| None | No access to Swarm or Kubernetes resources. |
| View Only | Read-only access across all resources. |
| Restricted Control | Can view and edit resources but cannot run services or mount host volumes. |
| Scheduler | Can view nodes and schedule workloads (default for Swarm collections). |
| Full Control | Unrestricted access to manage every resource. |
Warning
Grant Full Control sparingly. Excessive privileges can lead to unintended changes or security risks.
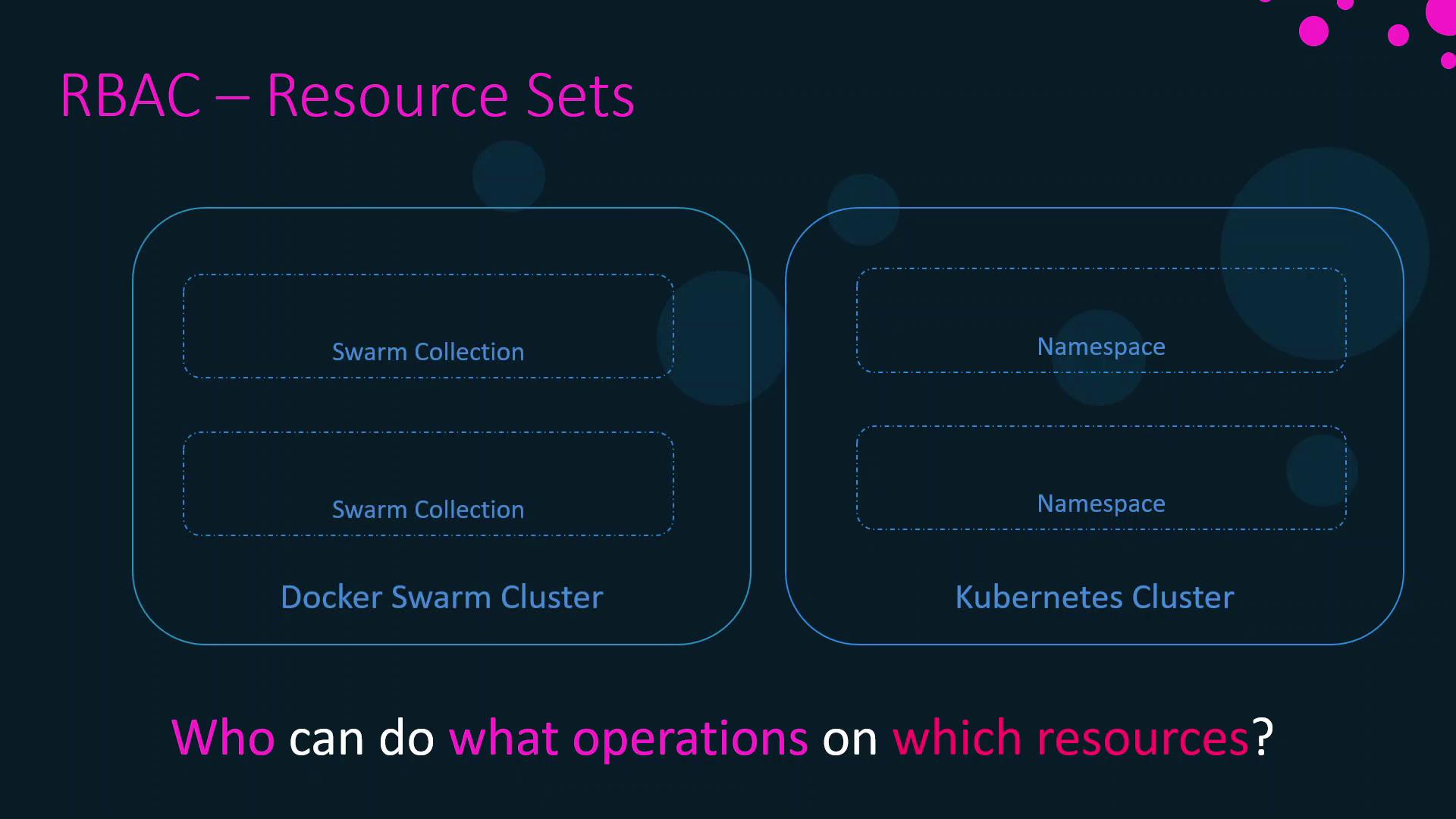
Resource Sets
A resource set defines the scope where a role applies:
- Kubernetes Namespaces: Logical partitions within a cluster.
- Swarm Collections: Groups of nodes, services, volumes, and networks in UCP.
Collections are created and maintained via the UCP console under Swarm Collections. Namespaces can be managed using standard Kubernetes tooling or via the UCP Kubernetes dashboard.
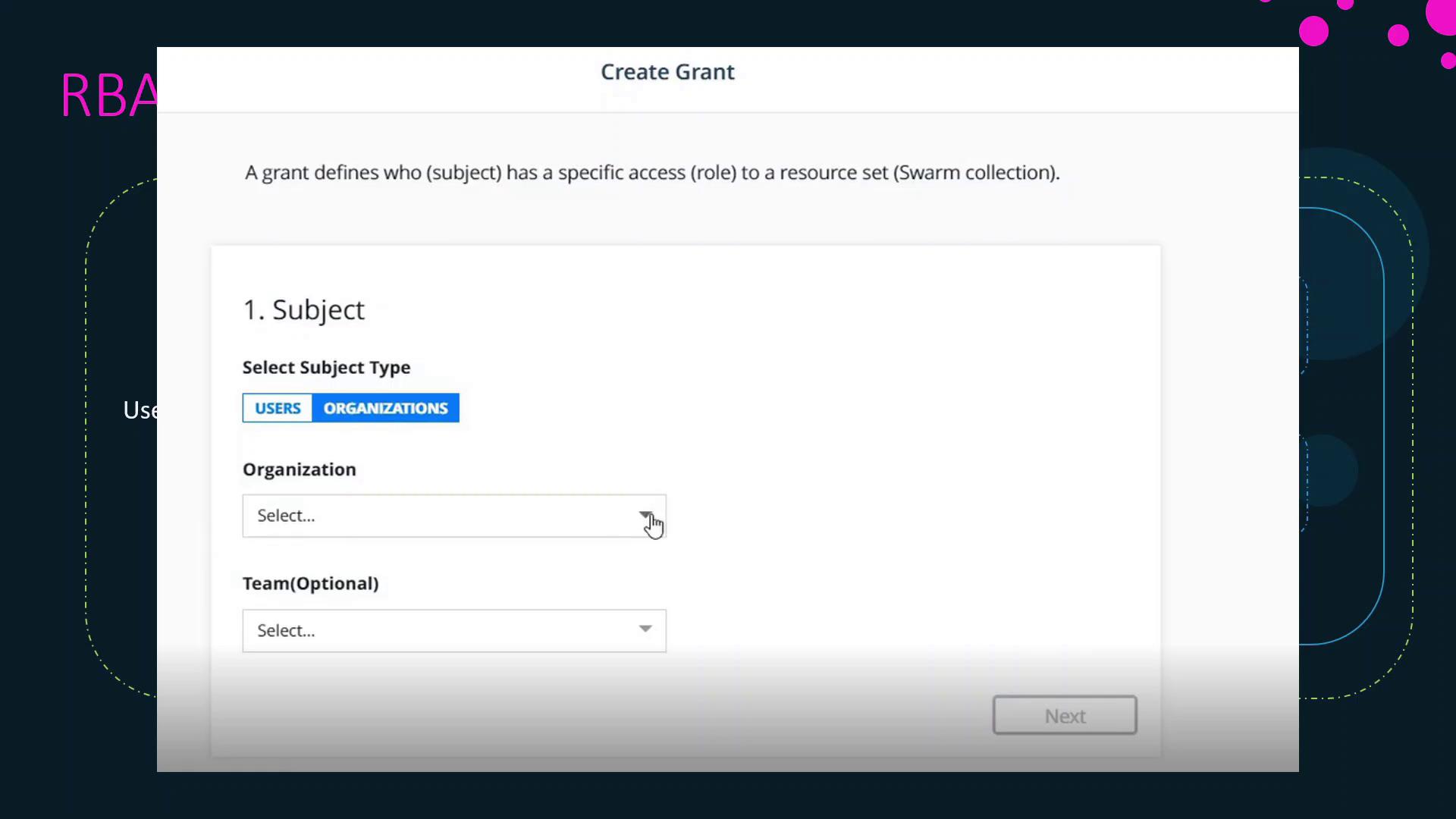
Grants
A grant binds together a subject, a role, and a resource set to enforce permissions. To create a grant in UCP:
- Navigate to Access Control > Grants.
- Select the Subject (user, team, organization, or service account).
- Choose the Role (built-in or custom).
- Pick the Resource Set (Swarm collection or Kubernetes namespace).
- Save the grant to apply the permissions.
Summary & Best Practices
- Configure Subjects
- Define users, teams, organizations, or service accounts in UCP.
- Define Roles
- Use built-in roles or create custom roles tailored to your security requirements.
- Create Resource Sets
- Organize workloads into Swarm collections or Kubernetes namespaces.
- Grant Access
- Combine subject + role + resource set to enforce least privilege.
Best Practices:
- Segment large teams into multiple groups with narrow privileges.
- Manage team membership rather than assigning permissions per user.
- Integrate UCP with LDAP or Active Directory for centralized identity management.
- Regularly review and audit grants to maintain a secure environment.

In the next section, we will demonstrate creating users, custom roles, Swarm collections, and grants in action.
Watch Video
Watch video content