IAM vs. Kubernetes RBAC
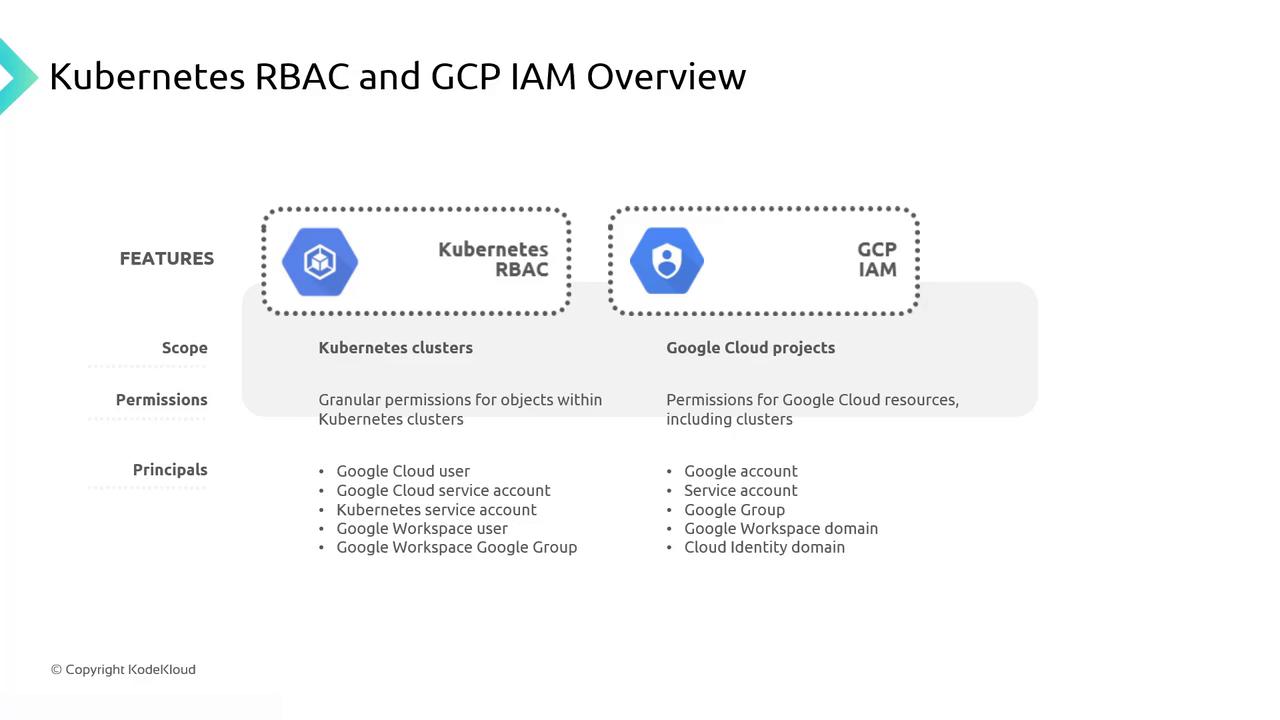
Choosing between GCP IAM and Kubernetes RBAC depends on your security requirements:| Feature | GCP IAM | Kubernetes RBAC |
|---|---|---|
| Scope | Project-level (all GKE clusters in a project) | Namespace or cluster-level |
| Permission Granularity | Broad, across multiple Google Cloud services | Fine-grained, Kubernetes API objects & verbs |
| Principal Types | Users, groups, service accounts | Kubernetes users, groups, service accounts |
| Best Use Case | Cross-service roles (e.g., billing, logging) | Cluster-specific permissions |
Use GCP IAM for overarching control across Google Cloud, and Kubernetes RBAC when you need detailed, in-cluster permissions.
Google Cloud IAM
Google Cloud’s Identity and Access Management (IAM) lets you assign roles to users, groups, or service accounts at the project level. Each role is a collection of permissions that define what actions can be taken on GKE clusters and other GCP resources.- Scope: Project-wide (all clusters in a project)
- Example Role:
roles/container.developer(Kubernetes Engine Developer) - gcloud example:
- Best for: Broad, cross-service management without per-object granularity
Kubernetes RBAC
Kubernetes Role-Based Access Control (RBAC) is native to the Kubernetes API. It grants permissions on specific Kubernetes resources (pods, deployments, secrets, etc.) at the namespace or cluster level.- ClusterRole: Permissions across the entire cluster
- Role: Permissions within a single namespace
- RoleBinding / ClusterRoleBinding: Attach Roles or ClusterRoles to subjects (users, groups, service accounts)
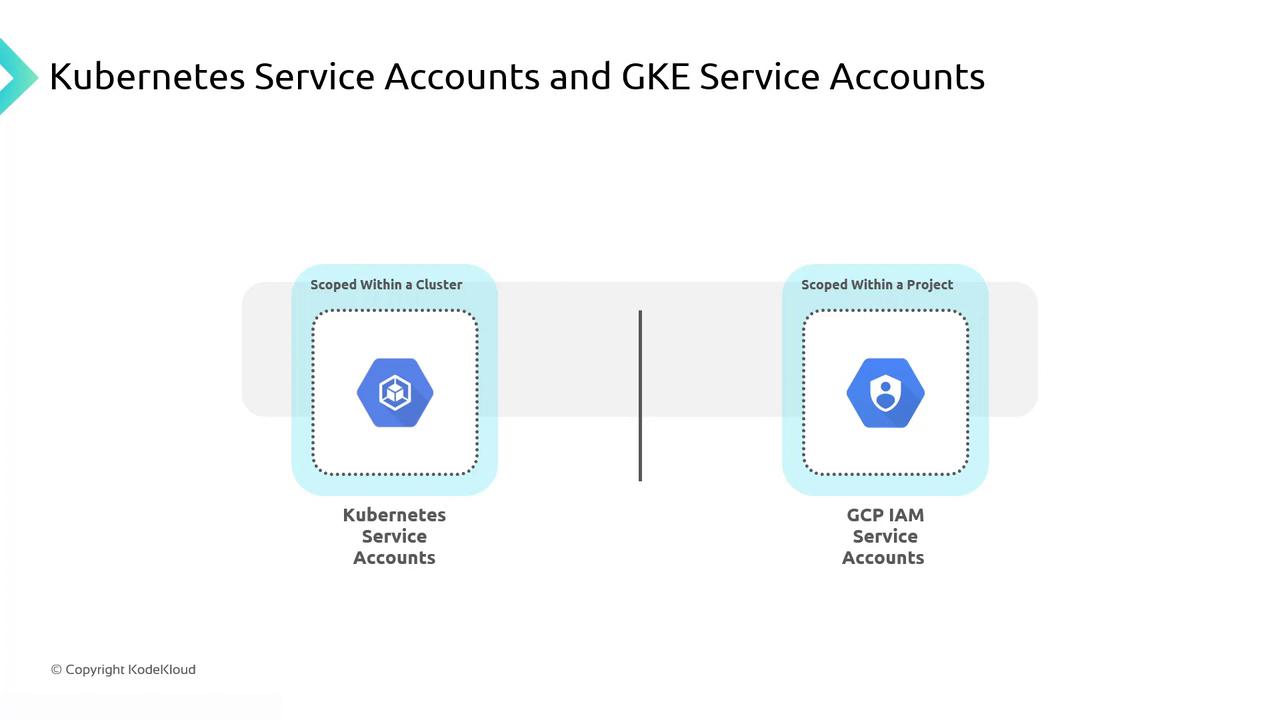
Service Accounts in GKE
GKE supports three types of service accounts for workload authentication:- Kubernetes Service Accounts
- GCP IAM Service Accounts
- GKE Service Agents
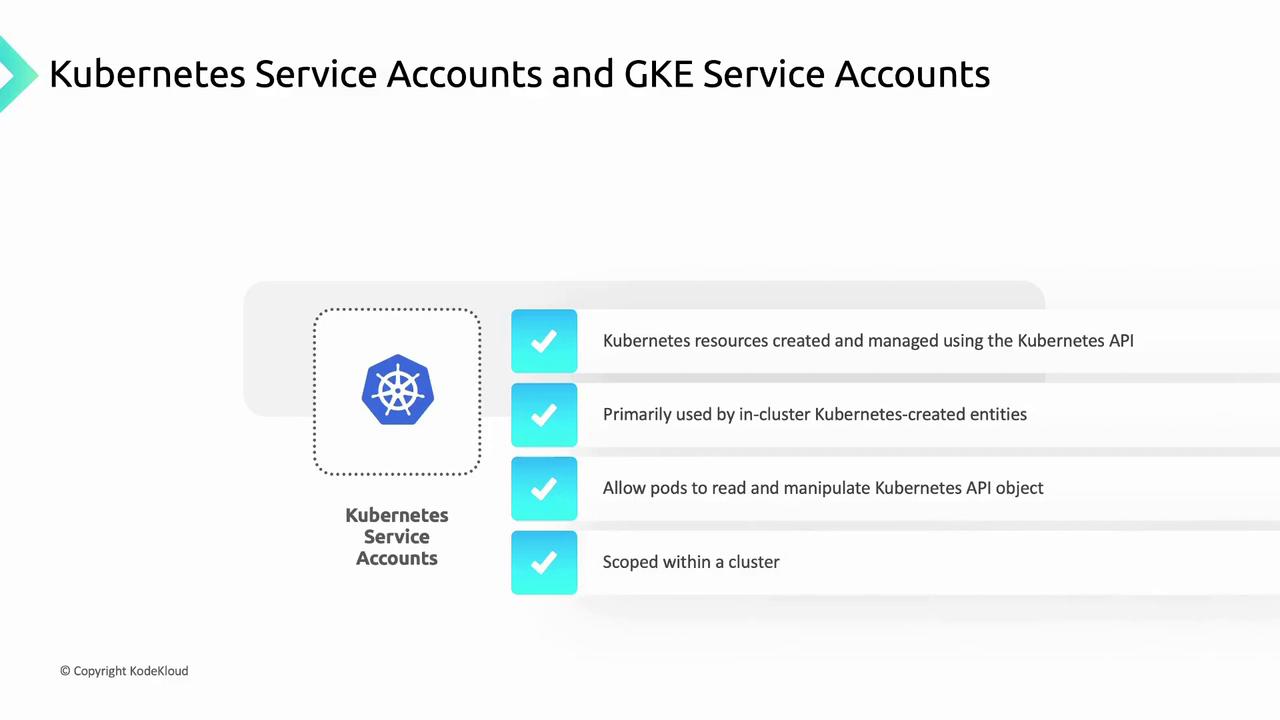
1. Kubernetes Service Accounts
Kubernetes Service Accounts are native to Kubernetes. They authenticate Pods to the Kubernetes API server or external services, enabling in-cluster workloads to manage Kubernetes objects.- Scope: Single cluster
- Use case: Pod to API-server communication
- Create example:
Always assign the minimal set of permissions to a ServiceAccount via Role or ClusterRole.
2. GCP IAM Service Accounts
GCP IAM Service Accounts are global to a GCP project. They represent non-human identities for applications to call Google APIs and interact with Google Cloud services.- Scope: Project-level
- Use case: Granting workloads access to GCP services (e.g., Cloud Storage, Pub/Sub)
- Create example:
Bind minimal roles (e.g.,
roles/storage.objectViewer) to limit service-account permissions.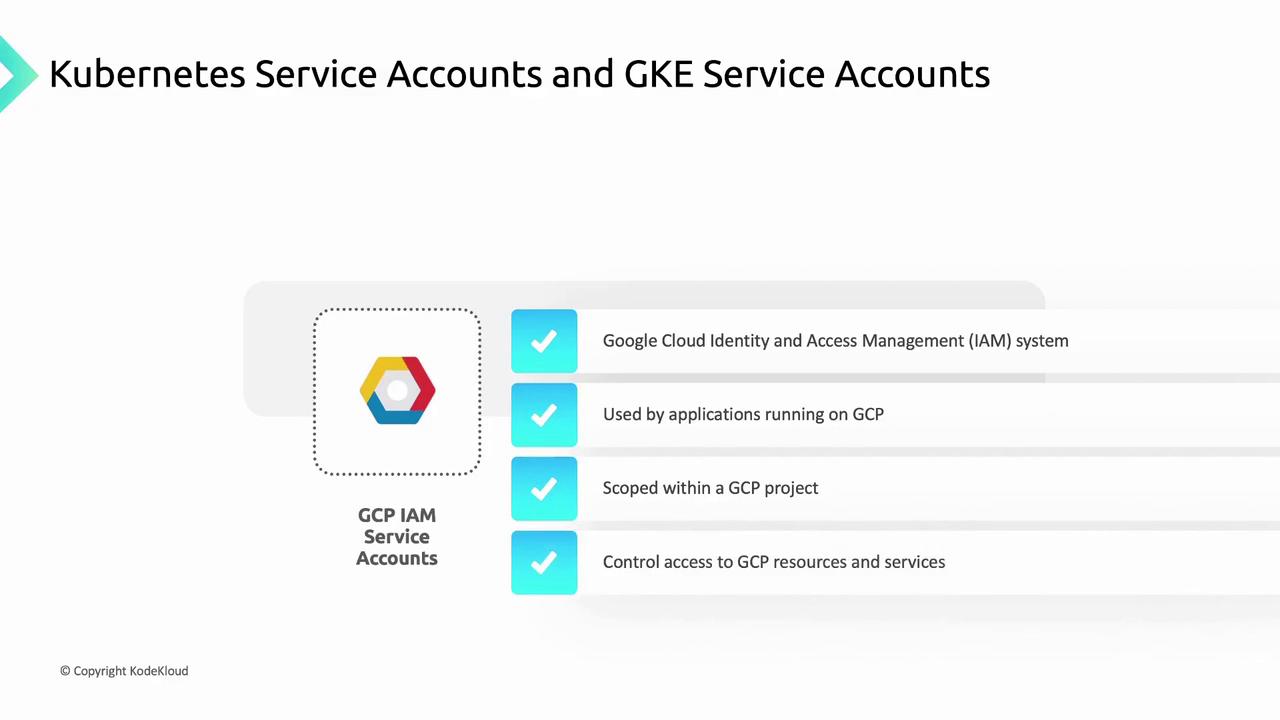
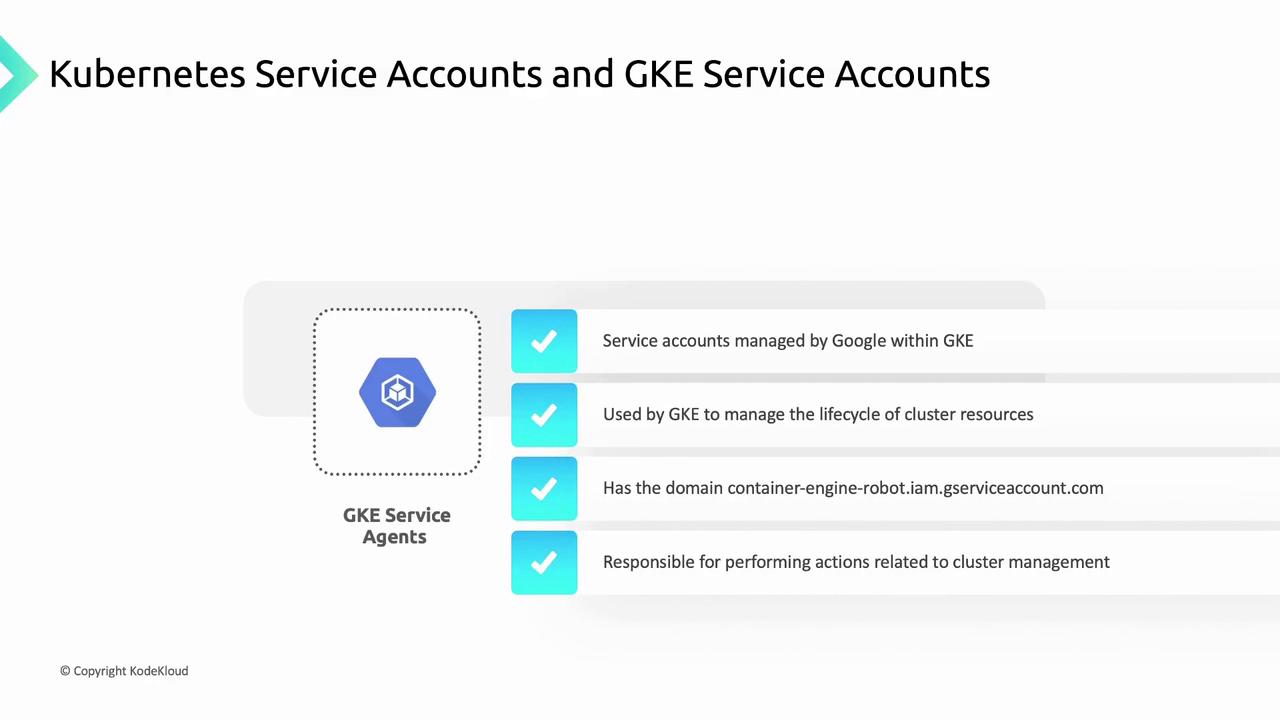
3. GKE Service Agents
GKE Service Agents are managed by Google to perform cluster lifecycle operations—such as provisioning nodes, disks, and load balancers—on your behalf. When you enable the GKE API, Google automatically creates a service agent with theroles/container.serviceAgent role.
- Managed by: Google
- Role:
roles/container.serviceAgent - Use case: Cluster provisioning and infrastructure management
Do not delete the GKE Service Agent, as it’s required for cluster operations.
Service Account Scope Comparison
| Service Account Type | Scope | Primary Use |
|---|---|---|
| Kubernetes Service Account | Cluster | In-cluster workloads calling API server |
| GCP IAM Service Account | Project | Workloads using GCP APIs |
| GKE Service Agent | Managed by GKE | Cluster lifecycle management |