1. Enterprise-Level Policies
At the enterprise scope, you can enforce Actions policies for all organizations or only selected ones.- Navigate to Policies → Actions in your enterprise account.
- Review the available settings for enabling or disabling GitHub Actions.
- Optionally allow organizations to manage self-hosted runners at the repository level.
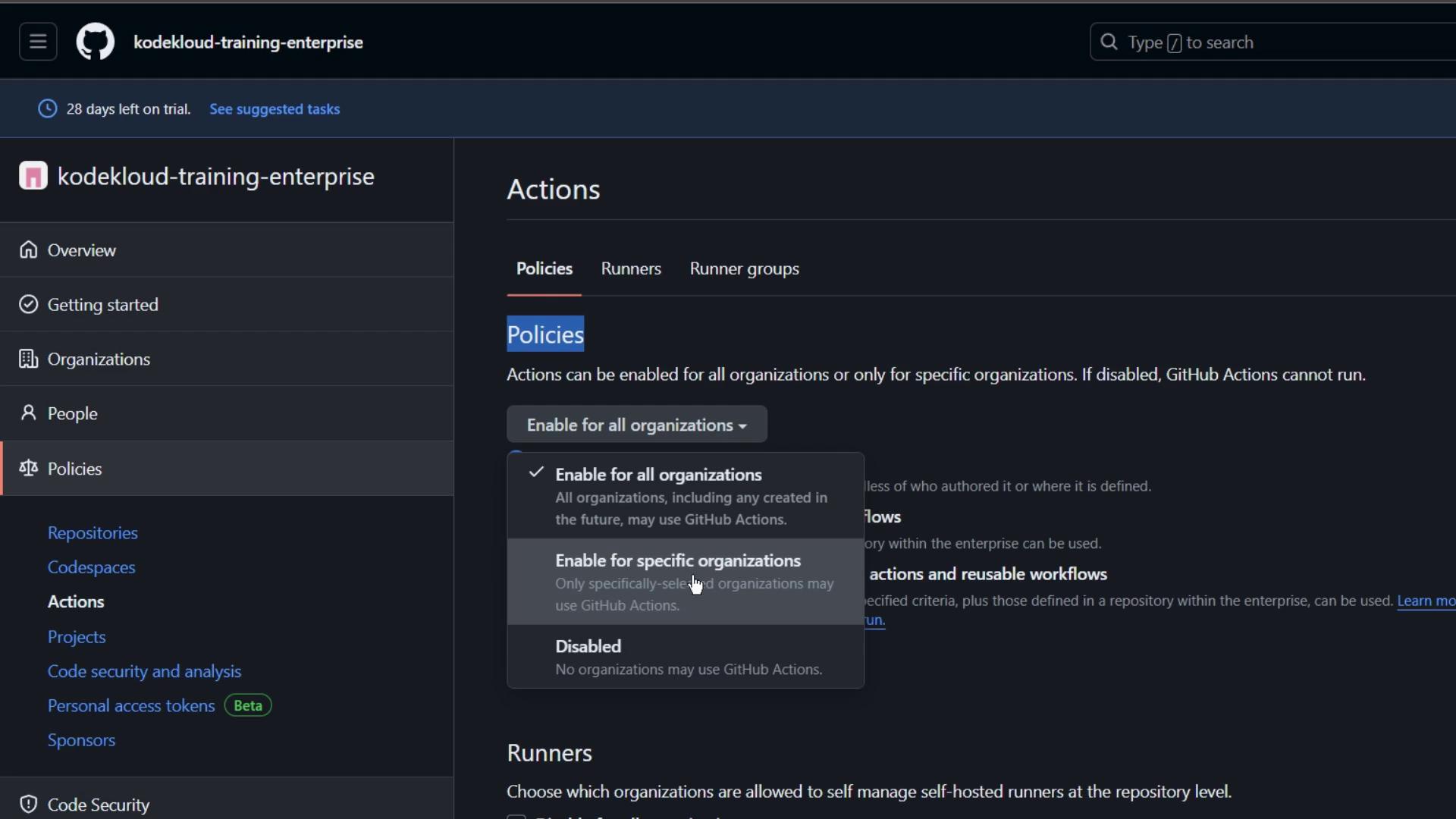
- Enable or disable Actions for every organization.
- Grant or revoke permission to self-manage self-hosted runners.
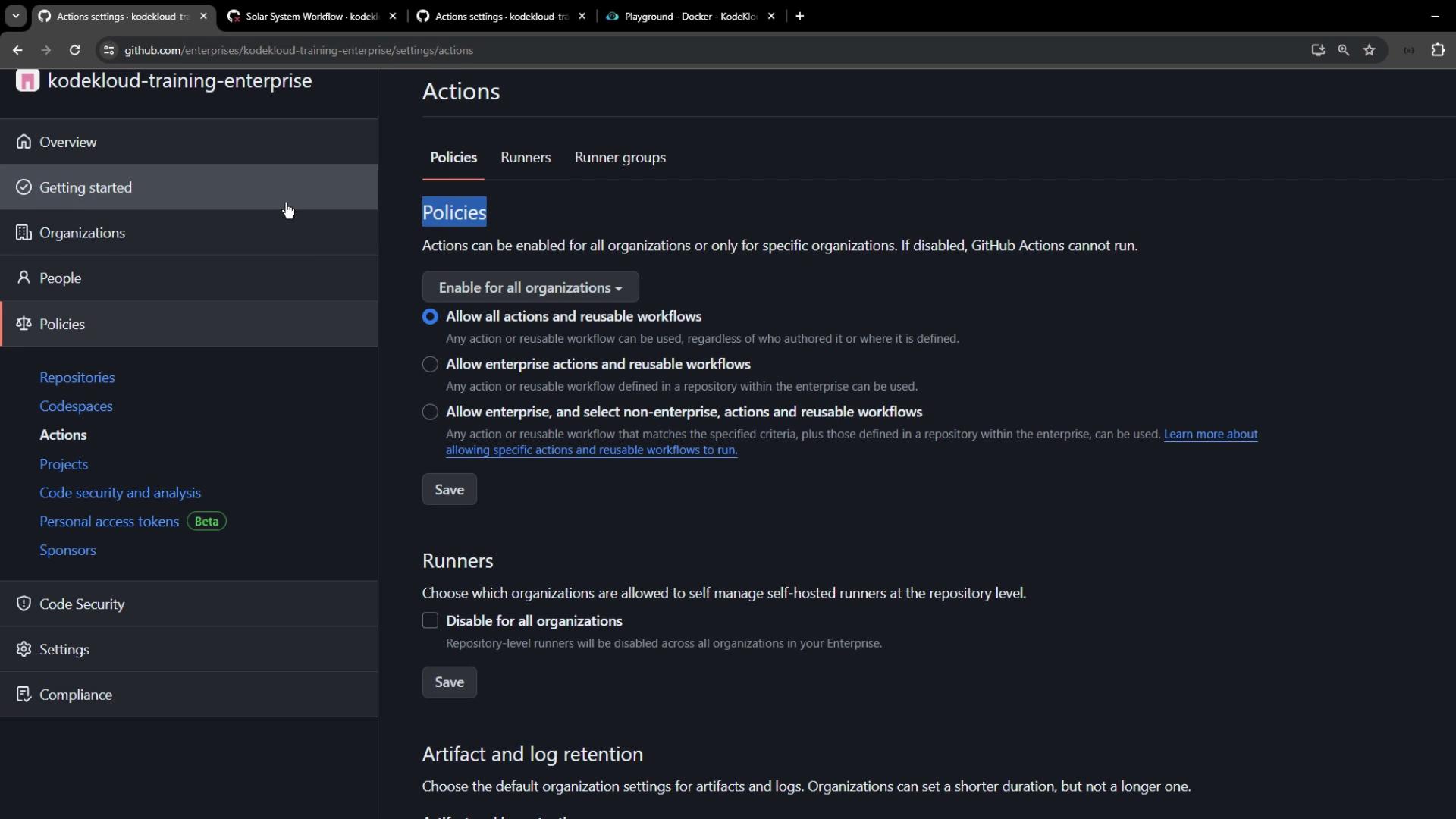
Enterprise-level policies take precedence over organization and repository settings. Once set, lower levels become read-only and inherit these policies.
1.1 Allowing a Specific Action Across Your Enterprise
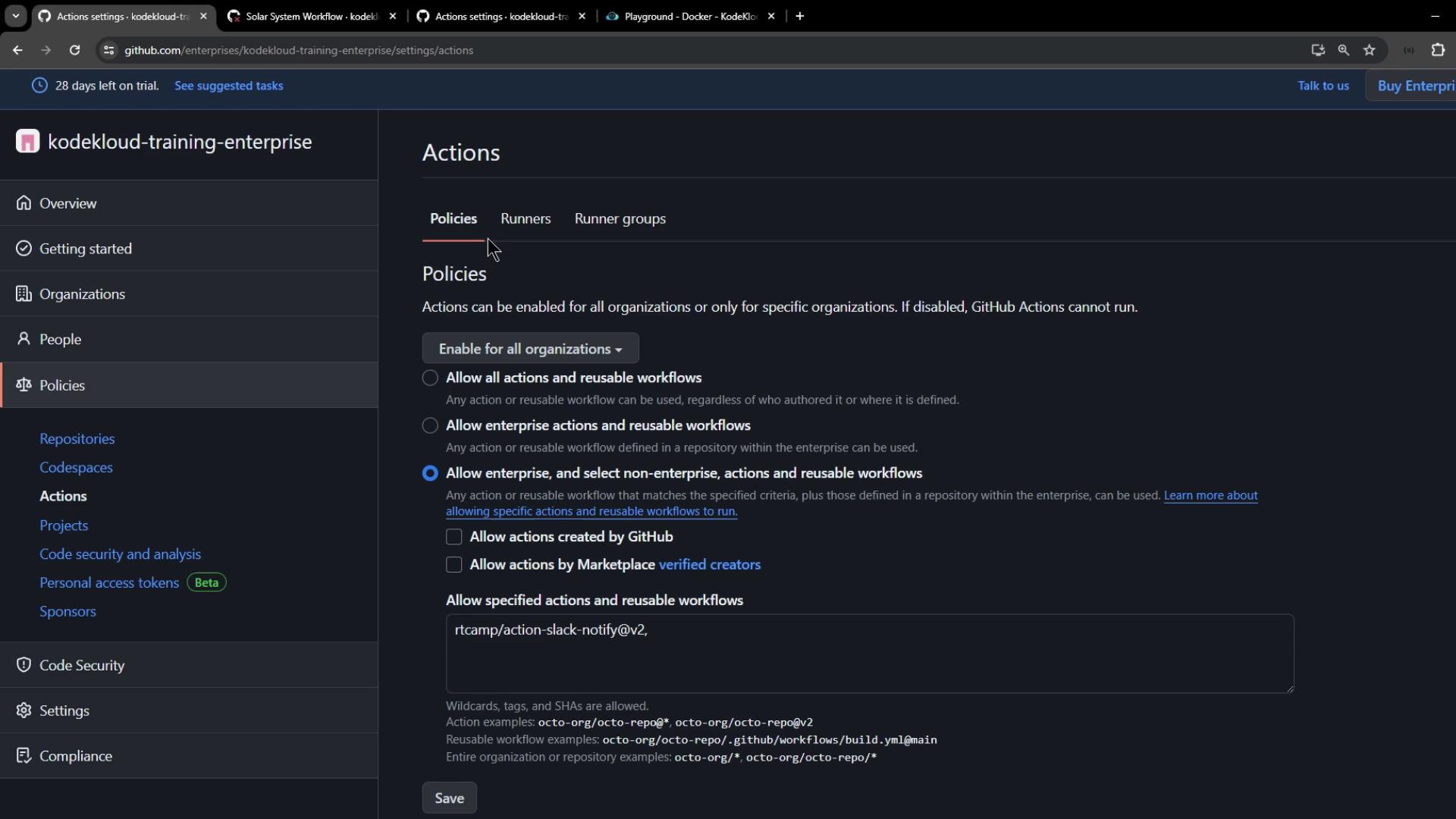
To whitelist a single action:- Under Policies → Actions, choose Allow specific actions.
- Enter the action reference, for example:
- Click Save to enforce this setting for all organizations.
- Go to any organization in your enterprise.
- Select Settings → Actions → General.
- Observe that organization-level controls are disabled and display your enterprise policy.
2. Repository-Level Policies
If you need more granular control, define Actions permissions per repository—whether under an organization or a personal account.2.1 Viewing and Selecting Repositories
Start by listing repositories in your organization: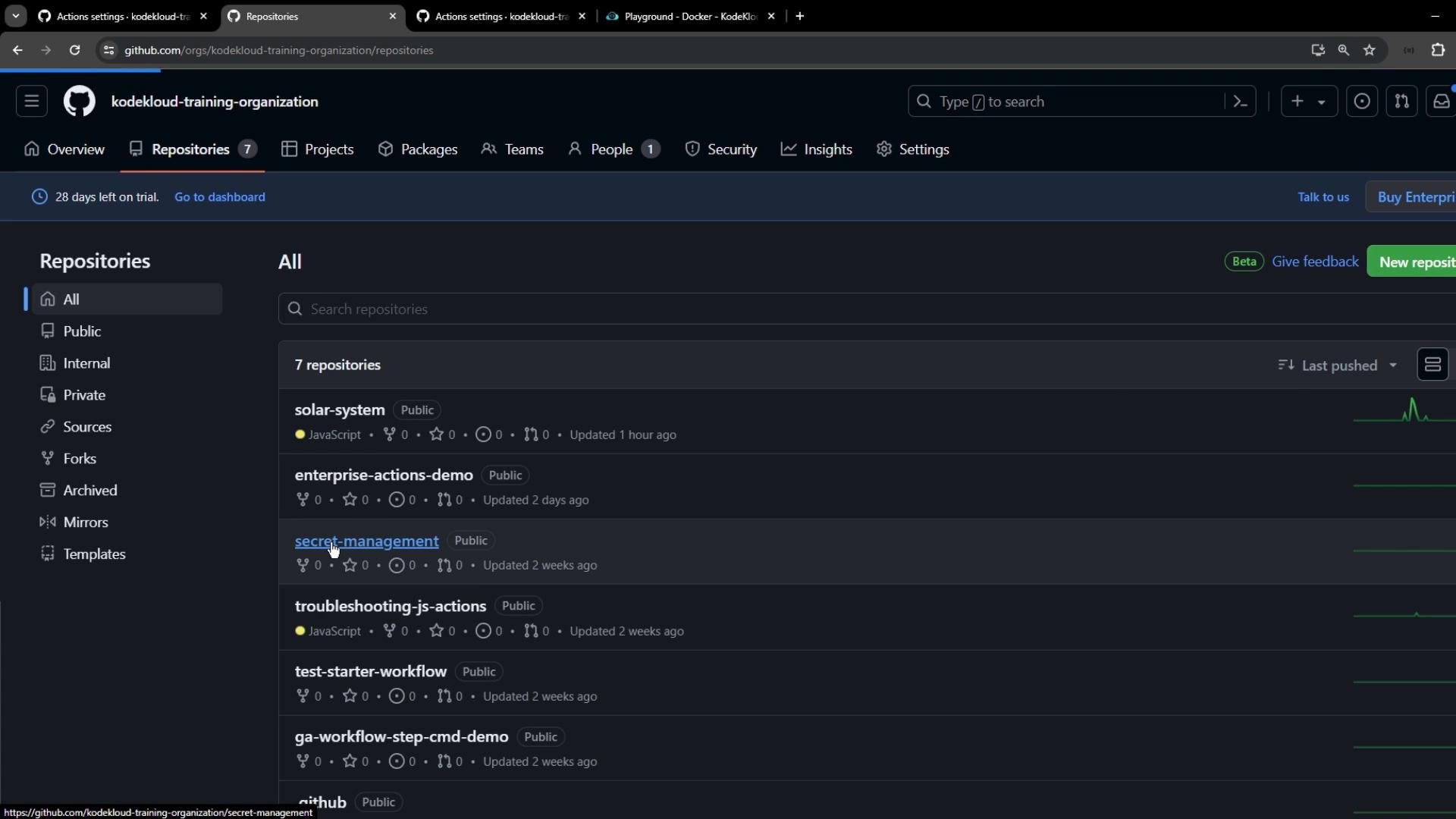
2.2 Configuring Actions Permissions
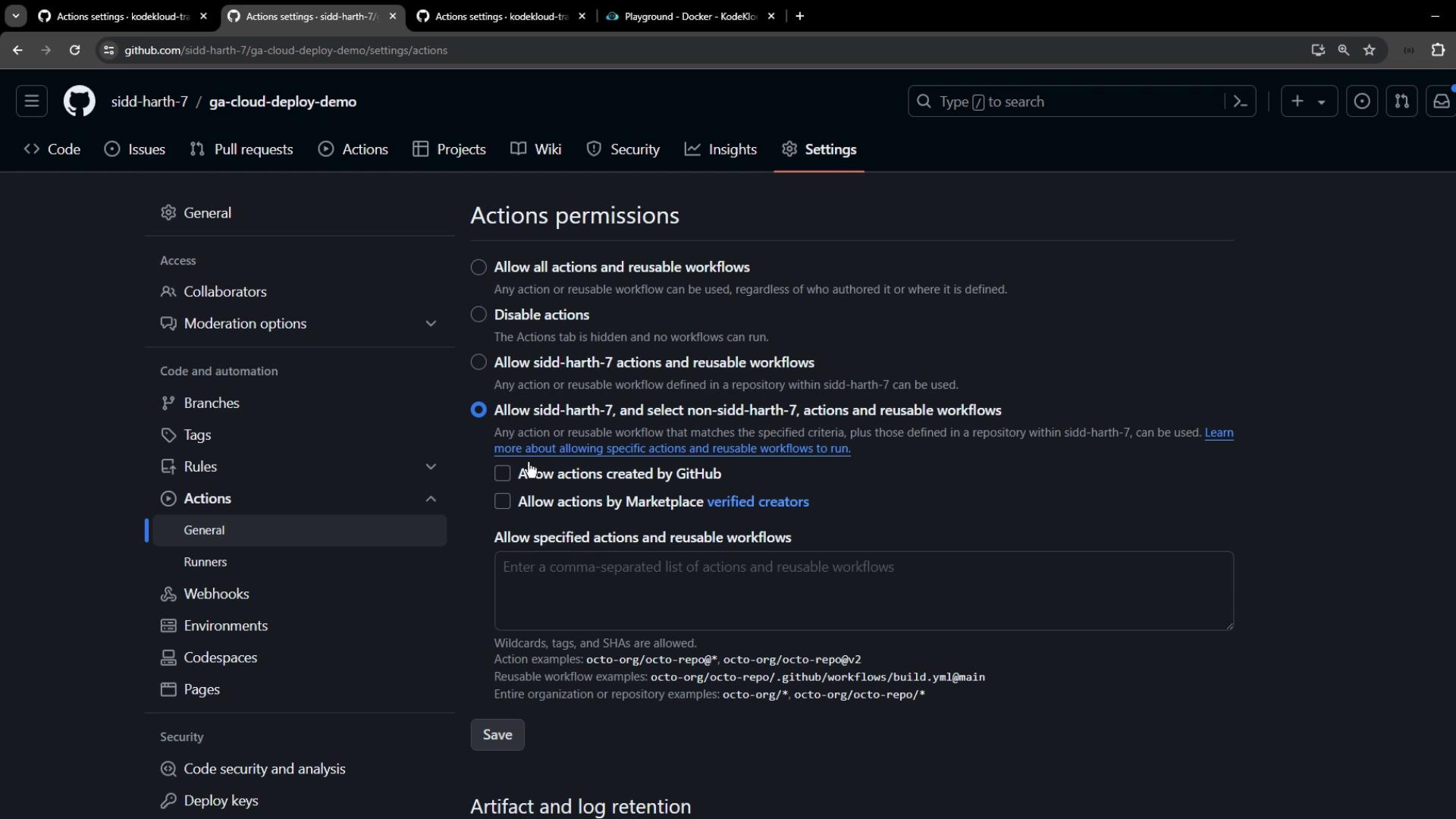
Open the target repository’s Settings → Actions → General to choose:- Disable Actions
- Allow all Actions
- Allow local Actions only
- Allow specific Actions and reusable workflows
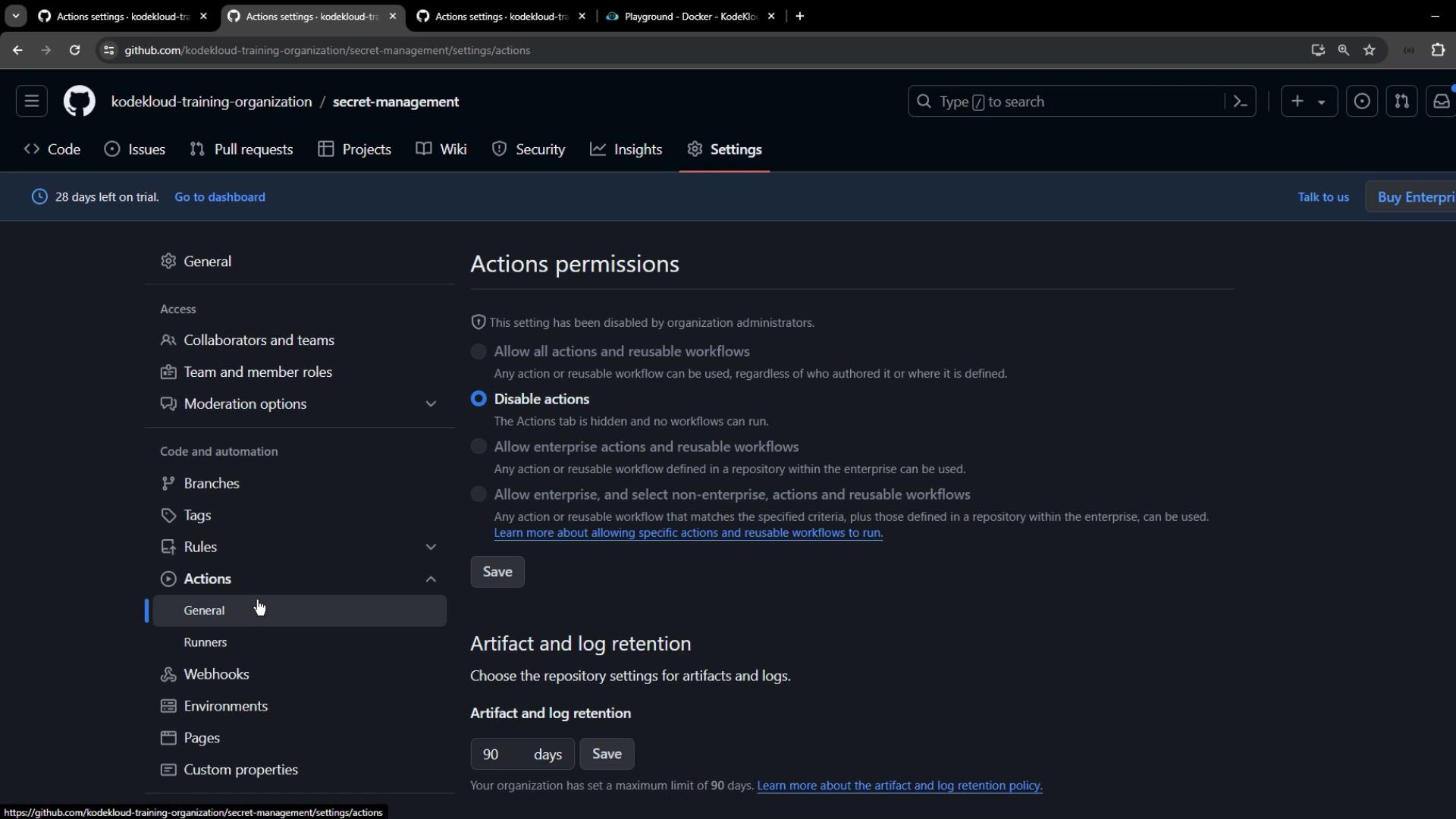
Disabling Actions at the repository level will prevent any workflows from running, including those critical for CI/CD.
Personal Repository Example
For personal repositories like ga-cloud-deploy-demo, the steps are identical:- Navigate to the repository.
- Click Settings → Actions → General.
- Set your desired permission level.
3. Summary of Policy Levels
| Scope | Applies To | Typical Use Case |
|---|---|---|
| Repository level | Individual repos | Custom workflows, personal projects |
| Organization level* | Multiple repos in one organization | Team-wide policy enforcement |
| Enterprise level | All or selected organizations | Global compliance, centralized CI/CD governance |