Persistence in Kubernetes refers to an attacker’s ability to survive pod restarts, node reboots, or configuration changes by planting backdoors or manipulating resources.

Example Scenario
Consider a multi-tier web application running NGINX for the front end, Node.js for business logic, and MySQL as the data store. An initial breach may occur when a container vulnerability is exploited. Once inside, the attacker focuses on persistence to survive your cleanup efforts.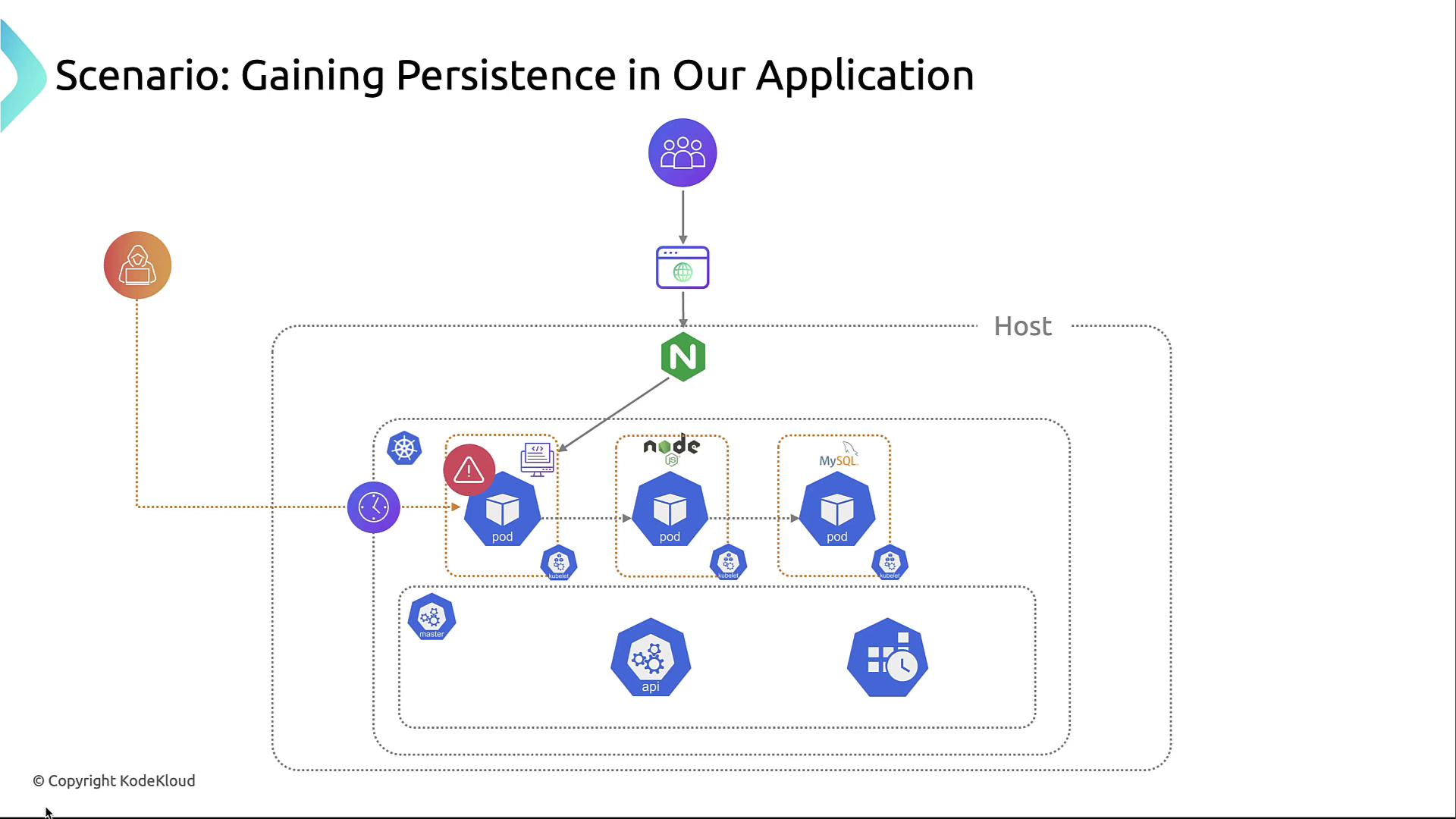
Attack Vectors for Persistence
The CNCF Financial Users Group defines the following key persistence vectors: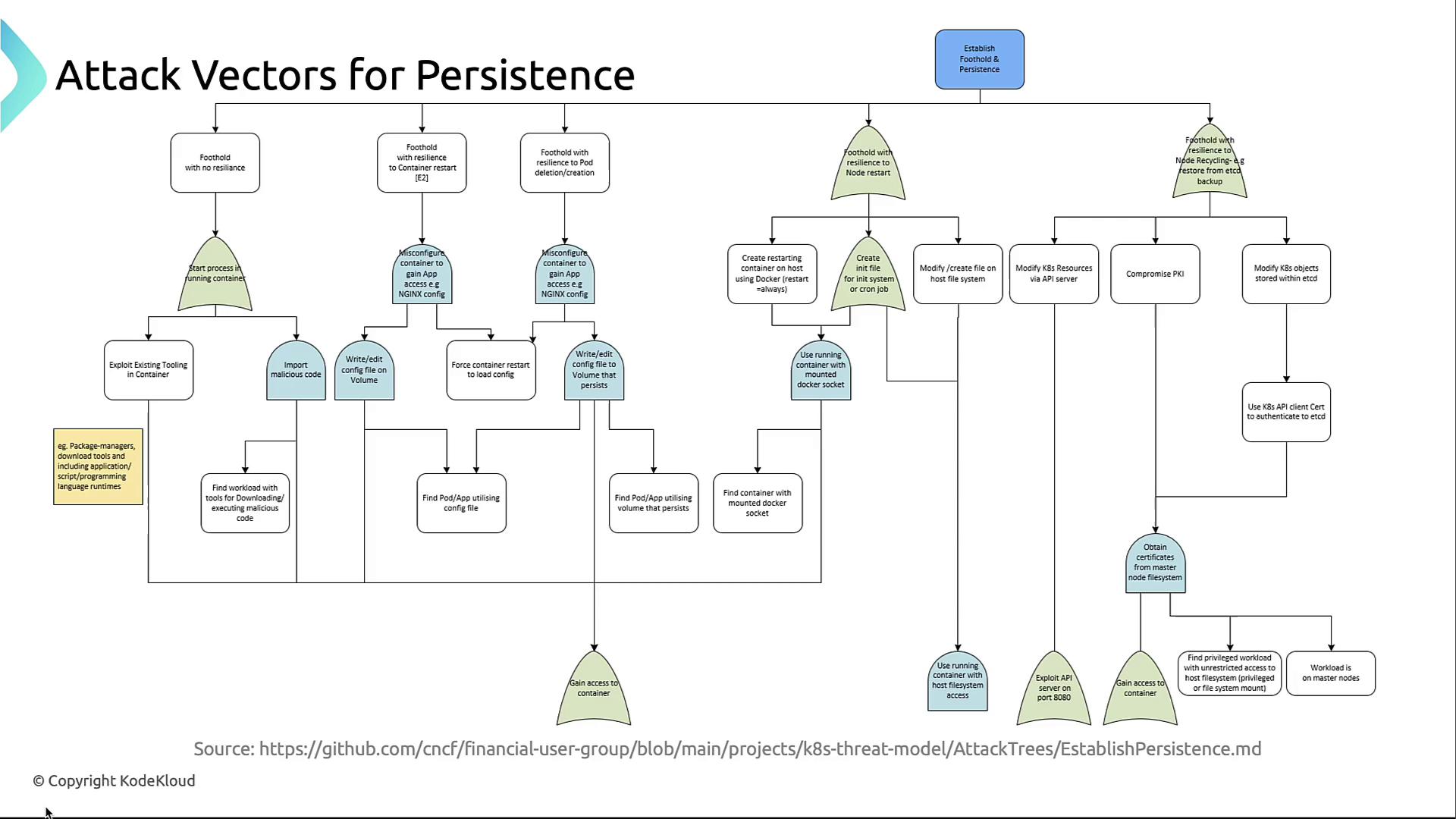
| Vector ID | Name | Description |
|---|---|---|
| 1 | Foothold with No Resilience | Transient access inside a container; lost on pod restart or delete. |
| 2 | Foothold with Resilience to Container Restart | Changes on mounted volumes or configs survive container restarts. |
| 3 | Foothold with Resilience to Node Restart | Host-level scripts or always-restart containers survive node reboots. |
| 4 | Foothold via Kubernetes API & PKI | Compromise service account tokens or certificates to control the API. |
| 5 | Leveraging Privileged Workloads | Abuse privileged pods or hostPath mounts to access the node. |
1. Foothold with No Resilience
This initial compromise lives only as long as the container does.- Running a Malicious Process: Execute a backdoor binary inside the pod.
- Using Native Tools: Leverage
apt,yum,pip, or scripting runtimes (python,node) to fetch and run code. - Container Hopping: Identify other pods with matching runtimes and pivot laterally.
2. Foothold with Resilience to Container Restart
Persistence here relies on writable volumes or config files:- Volume-Backed Config Tweaks: Edit configs (e.g., NGINX settings) stored on a
PersistentVolumeClaim. - Forcing a Restart: Trigger a pod restart (
kubectl rollout restart deployment/nginx) to pick up malicious changes.
3. Foothold with Resilience to Node Restart
Attackers move outside the pod sandbox:- Always-Restart Containers: Launch a Docker container on the host with
--restart=always. - Init Scripts & Cron Jobs: Append malicious commands to
/etc/rc.localor create entries in/etc/cron.d/. - Host File System Implants: Drop binaries or scripts directly onto the host for execution.
Host-level persistence bypasses Kubernetes controls. Monitor for unexpected containers on nodes and unauthorized changes to init files or cron entries.
4. Foothold via Kubernetes API & PKI
Compromising API credentials grants cluster-wide power:- Service Account Token Theft: Steal or mount tokens from
/var/run/secrets/kubernetes.io/serviceaccount. - Certificate Forgery: Extract or fabricate client certificates to impersonate admins.
5. Leveraging Privileged Workloads
Privileged pods break out of the container isolation:- Privileged Mode: Pods with
securityContext.privileged: truecan manipulate the host. - HostPath Mounts: Access and modify host directories like
/etcor/var/lib/kubelet.
Mitigations for Persistent Threats
Defending against persistence requires a layered approach:1. Role-Based Access Control (RBAC)
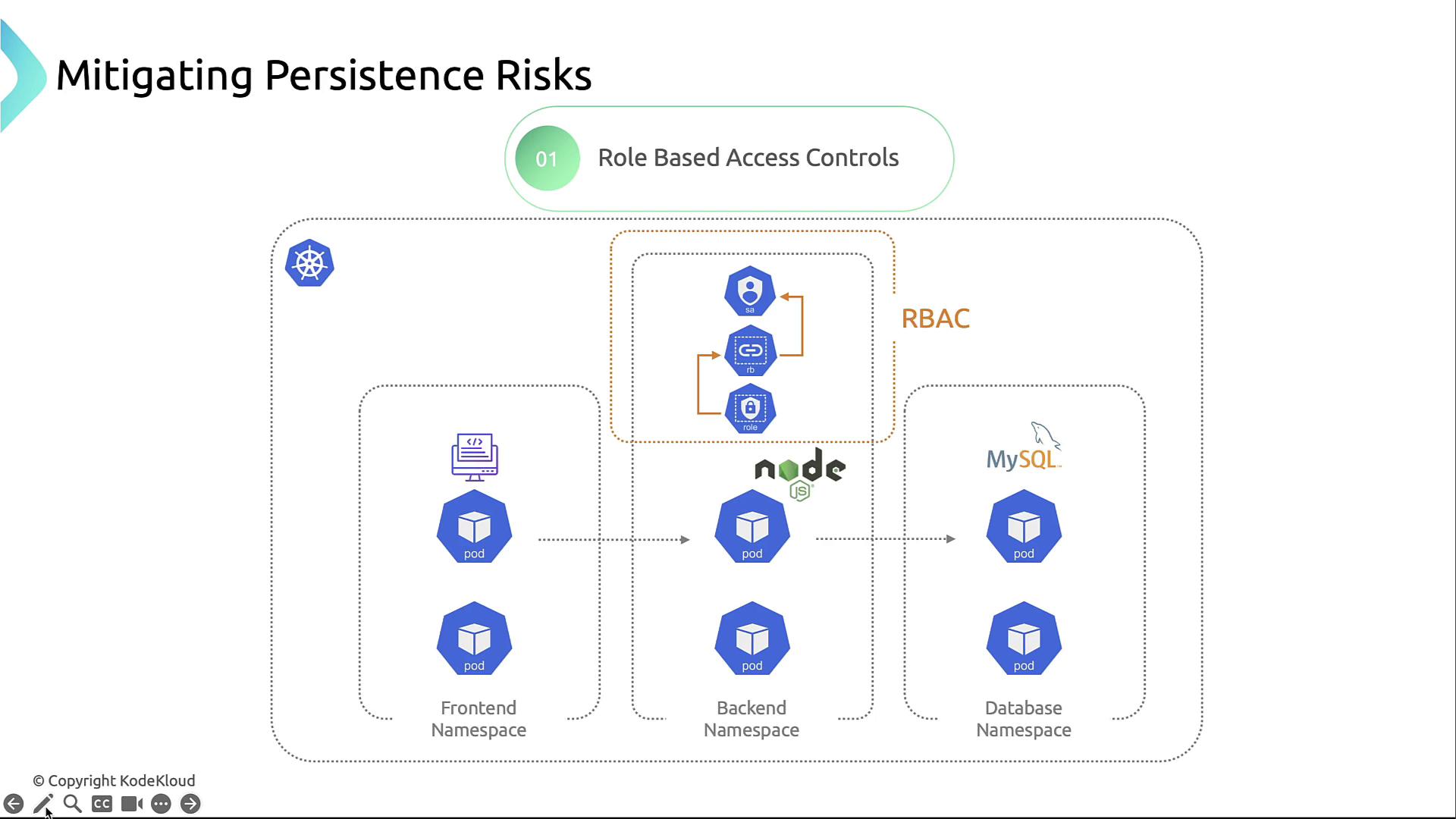
- Grant the least privilege to service accounts.
- Regularly audit
ClusterRoleandRolebindings.
2. Secrets Management
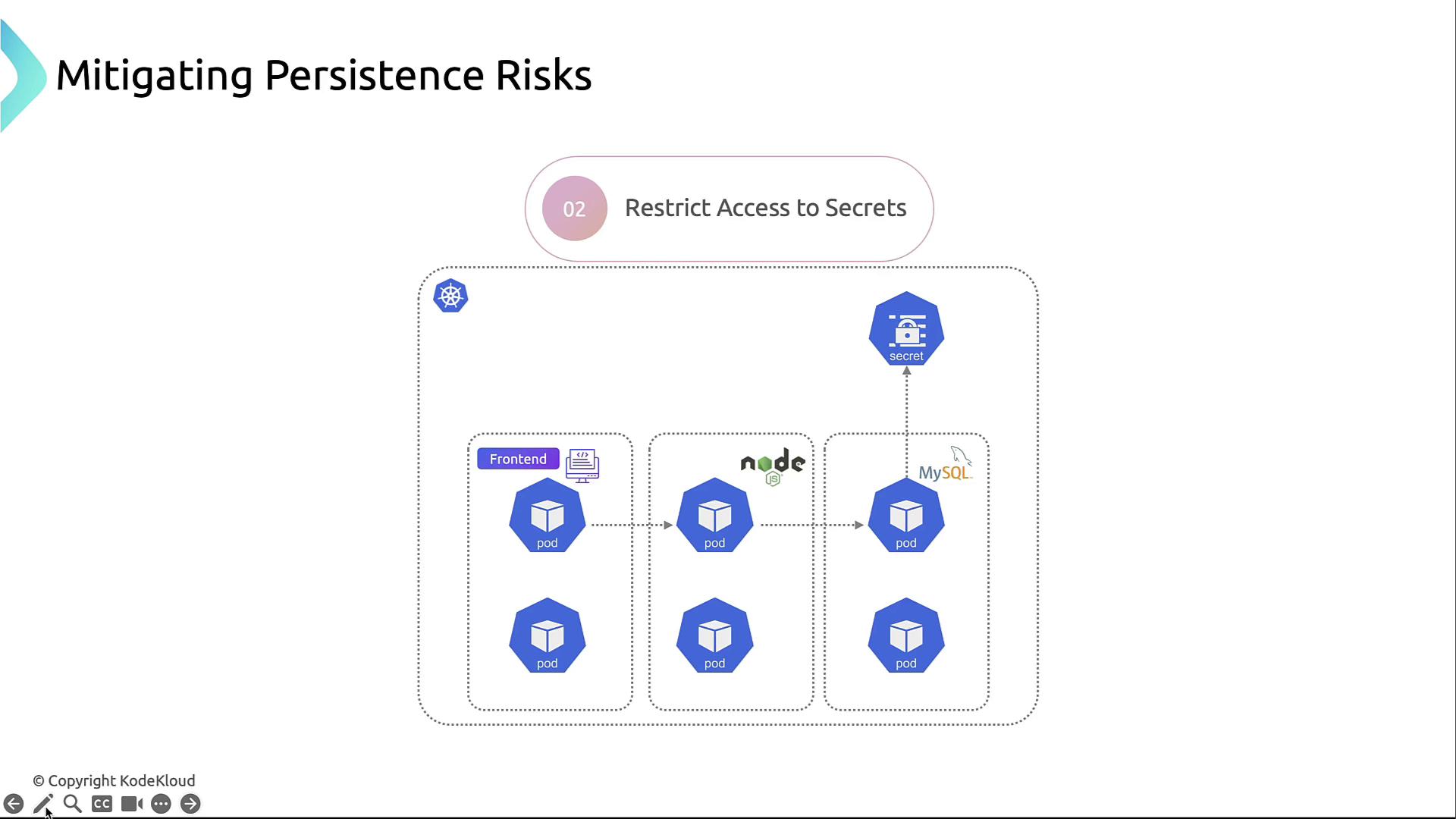
- Store credentials in Kubernetes Secrets.
- Restrict secrets to only the pods that require them.
3. Pod Security Standards
- Enforce Pod Security Admission (PSA) or Pod Security Policies (PSP).
- Disallow
privilegedcontainers andhostPathmounts. - Set
readOnlyRootFilesystem: truewhere possible.
4. Regular Updates & Patching
- Use image scanning tools to detect vulnerabilities.
- Automate rolling updates for base images:
5. Monitoring & Auditing

- Centralize logs (e.g., using Elasticsearch, Fluentd, Kibana).
- Alert on unexpected pod restarts, new privileged pods, or RBAC changes.
- Periodically review the audit log via
kubectl logs -n kube-system.
Persistent threats allow attackers to survive cleanup, exfiltrate data, and hijack resources. Key defenses include:
- Enforce strict RBAC and Pod Security Standards
- Secure and rotate Secrets regularly
- Keep images and nodes up to date
- Monitor, audit, and alert on suspicious actions