AWS Solutions Architect Associate Certification
Designing for Security
Turning up Security on Network Services Part 2
In this article, we explore advanced AWS networking design strategies that enhance security while ensuring optimal performance. We cover global architectures, multi-VPC deployments, secure subnet design, and specialized networking features—all aimed at keeping customer data compliant with regional regulations and streamlining internal communications.
Designing for Global Architecture and VPC Deployment
Imagine a global e-commerce company that must serve customers in North America, Europe, and Asia with low-latency access while ensuring local storage of customer data. To achieve this, it deploys applications in multiple VPCs—one per region (e.g., Virginia, Frankfurt, and Tokyo). A single VPC approach would risk cross-region data flow, even with replication in place.
Using Route 53, requests are directed to the nearest region to comply with data regulations like GDPR and minimize latency:
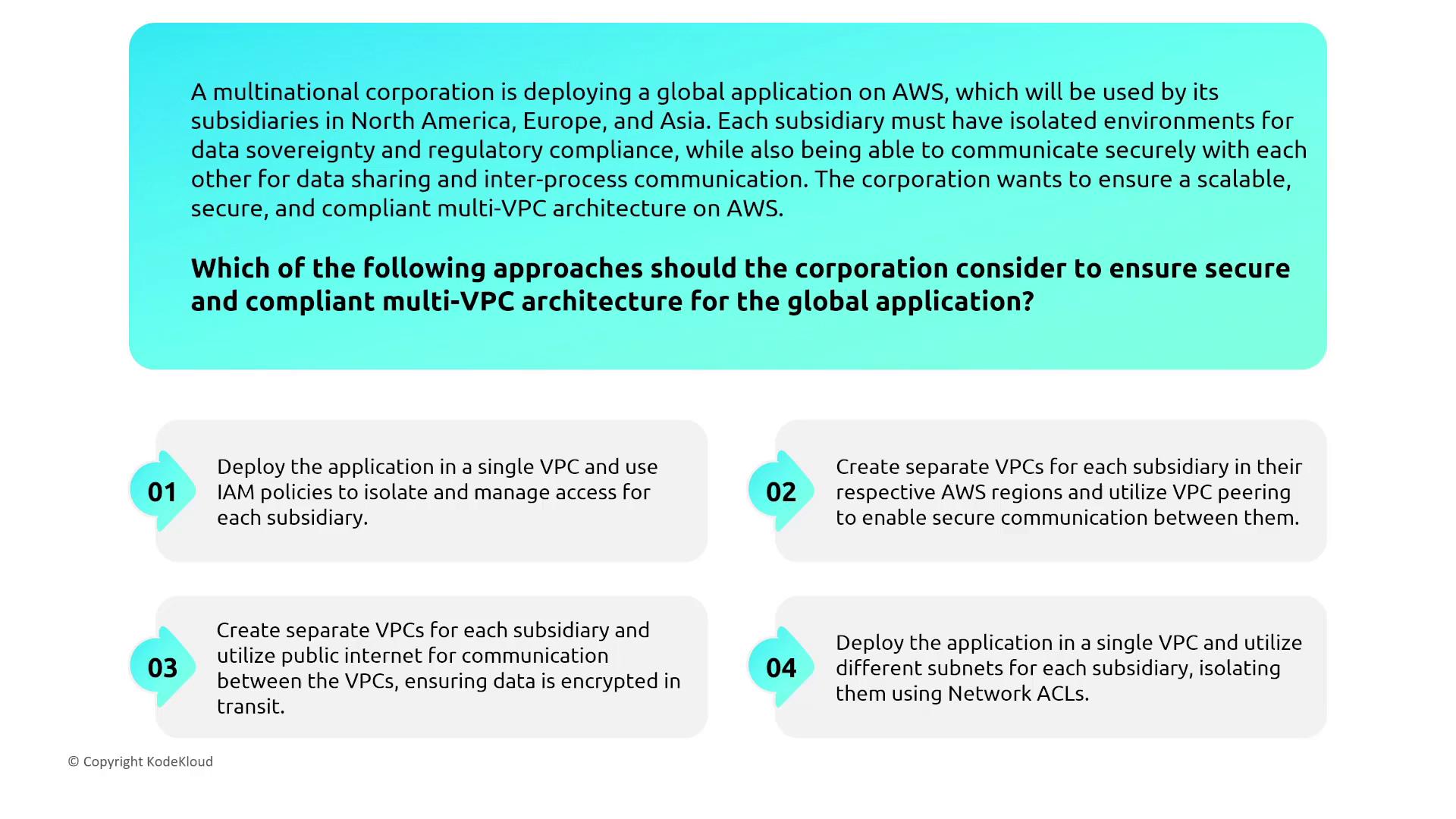
Isolated Multi-VPC Architecture for Multinational Corporations
Multinational corporations often require isolated VPC environments for each subsidiary to meet data sovereignty and regulatory standards. Although deploying separate VPCs with encrypted internet communication is an option, AWS VPC Peering provides a more secure alternative by leveraging AWS’s private backbone.
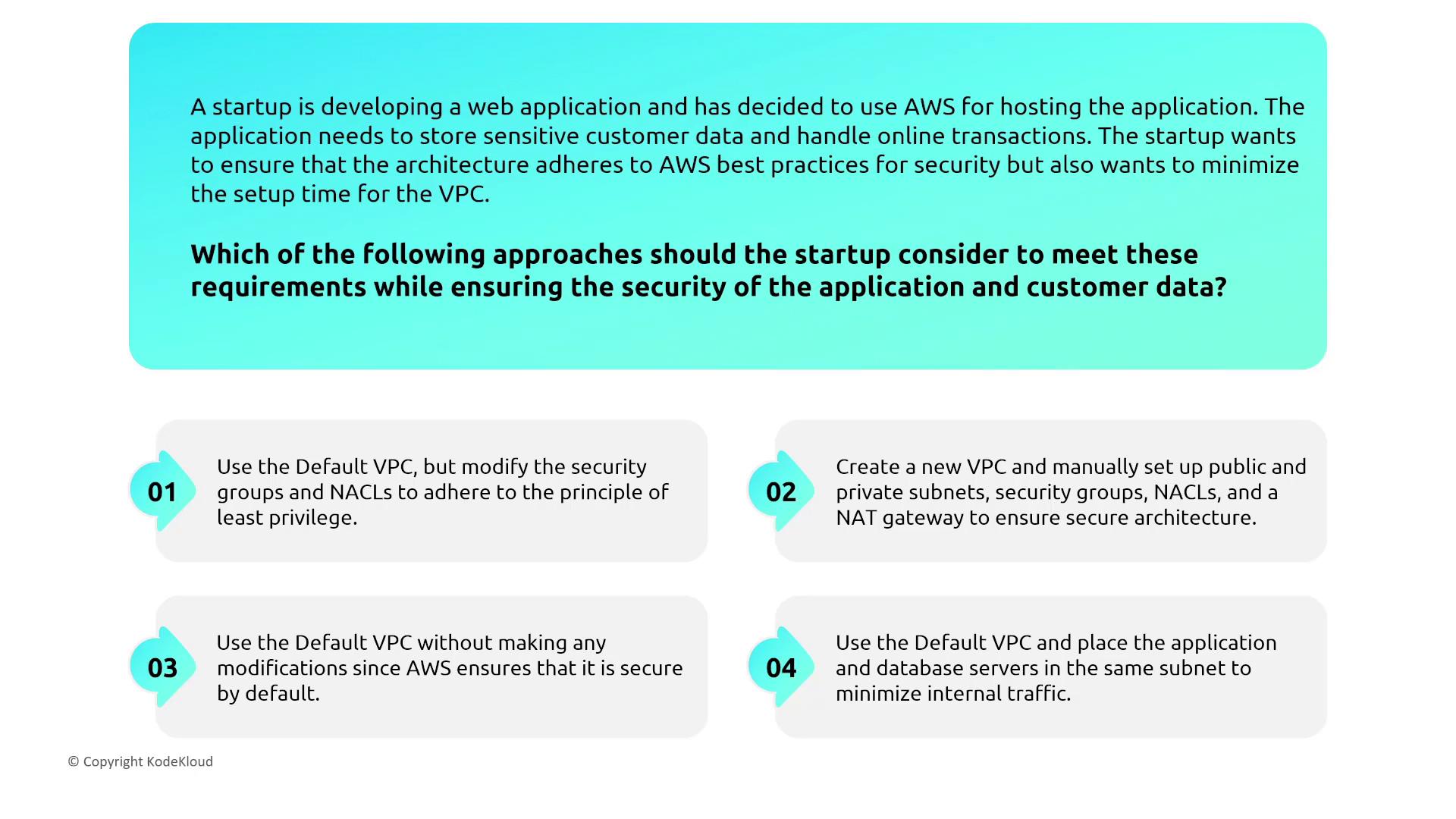
Default VPC vs. Custom VPCs for Startups
For startups launching web applications on AWS, time is of the essence. Using the default VPC can speed up deployment, provided that the security groups and network ACLs are modified to enforce the principle of least privilege. Keep in mind that the default VPC comes preconfigured with broad access, so manual adjustments are necessary for enhanced security.
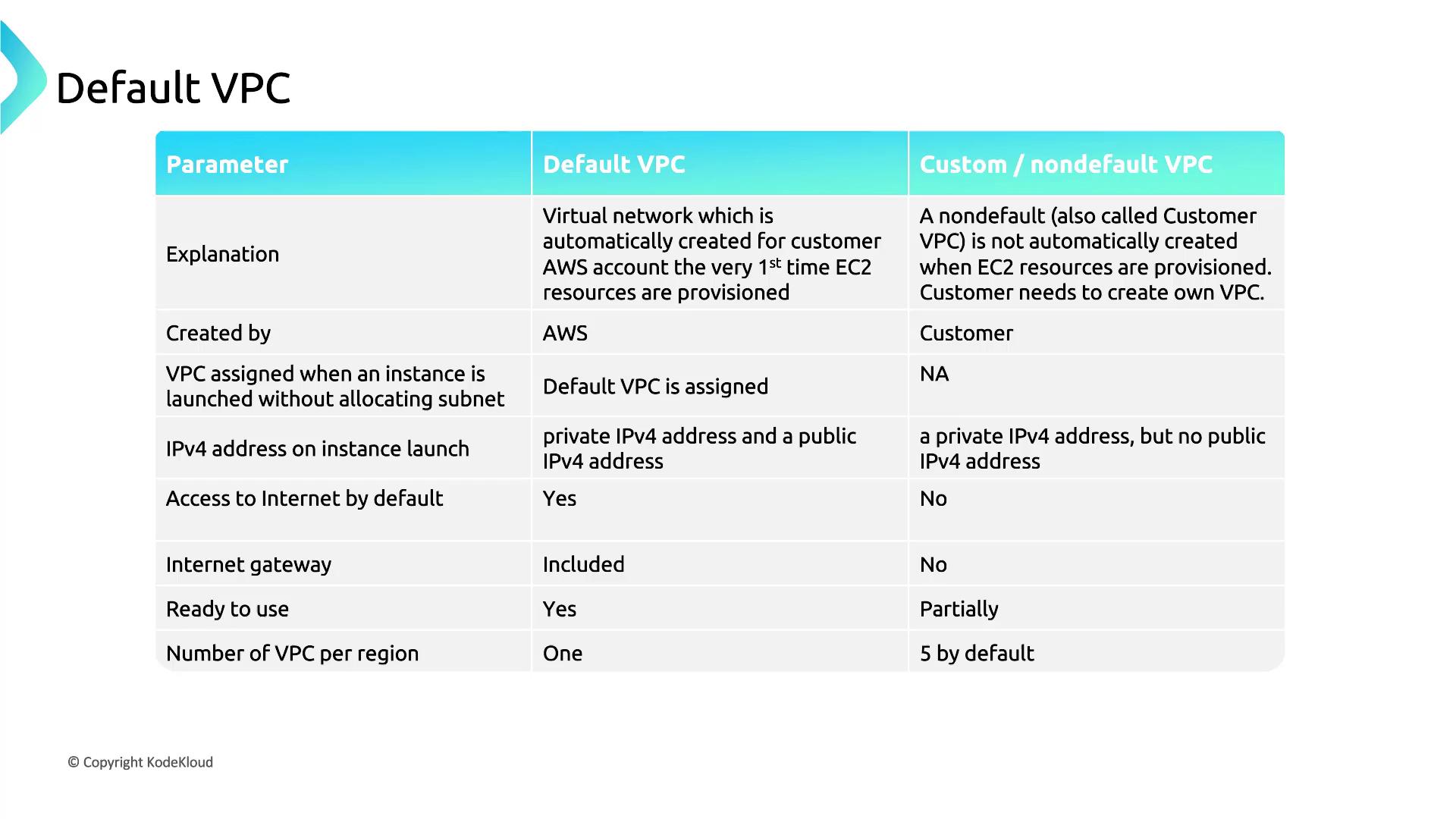
By default, AWS provides each region with one default VPC and five additional customer VPCs, with more available upon request:
Subnet Design for Layer Segregation
For a retail company deploying an e-commerce application, separating the application and database layers reduces the risk of unauthorized access. Instead of isolating these layers across different VPCs, the best practice is to use multiple subnets within a single VPC. One subnet handles the application layer while another, secured by distinct firewall rules, serves the database layer.

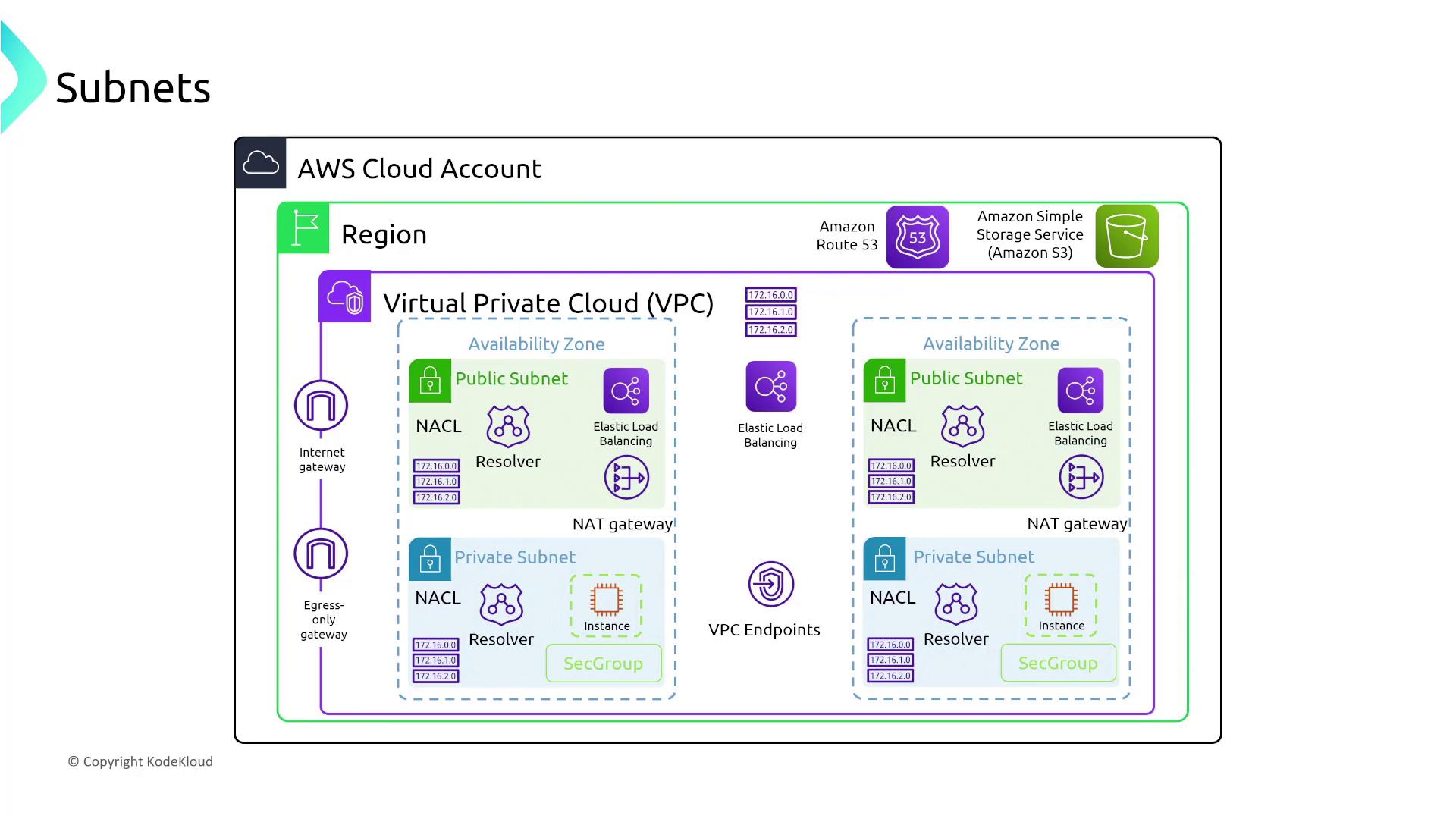
For more complex setups like three-tier architectures, the web tier resides in a public subnet while the application and database tiers are isolated in private subnets with carefully configured routing and access control.
A foundational diagram illustrating public and private subnets within a VPC is shown below:
Routing Between Tiers
For multinational corporations running multi-tier web applications, configuring routing tables is crucial. Typically, only the web tier has a route to an Internet Gateway, while the application and database tiers remain isolated from direct internet exposure. Even if the primary focus is on protecting the database, restricting the application tier from direct internet access is a good security practice.
Internet Gateways and Controlled Access
A software development company might deploy an application on AWS for testing that must be accessible through an Internet Gateway—exclusively to developers. While attaching an Internet Gateway is simple, security groups need to restrict inbound access to specific IP addresses. In many cases, companies enhance this configuration with remote hybrid connectivity.
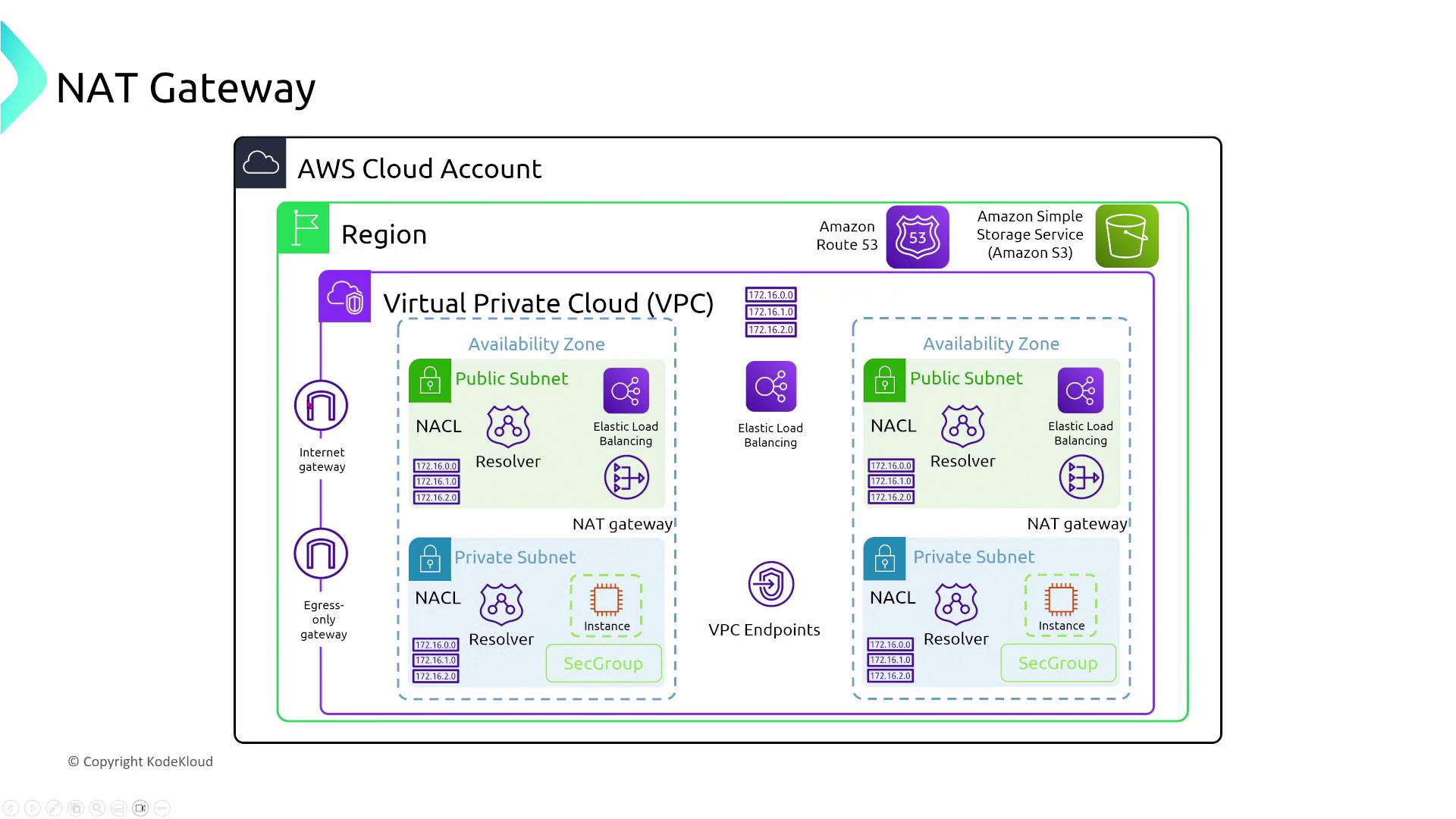
NAT Gateways for Outbound Traffic
For FinTech and financial analytics companies, applications in private subnets may need secure access to public APIs. Deploy a NAT Gateway in a public subnet and update the private subnet’s routing to direct outbound traffic through it. This configuration allows secure data retrieval from the internet without exposing the internal instances.
Egress-Only Gateways for IPv6 Traffic
In situations where an IPv6 application must download external datasets without accepting incoming IPv6 traffic, deploying an egress-only Internet Gateway is the ideal solution. Direct all IPv6 outbound traffic from private subnets to the gateway, ensuring that the application remains shielded from unsolicited inbound requests.

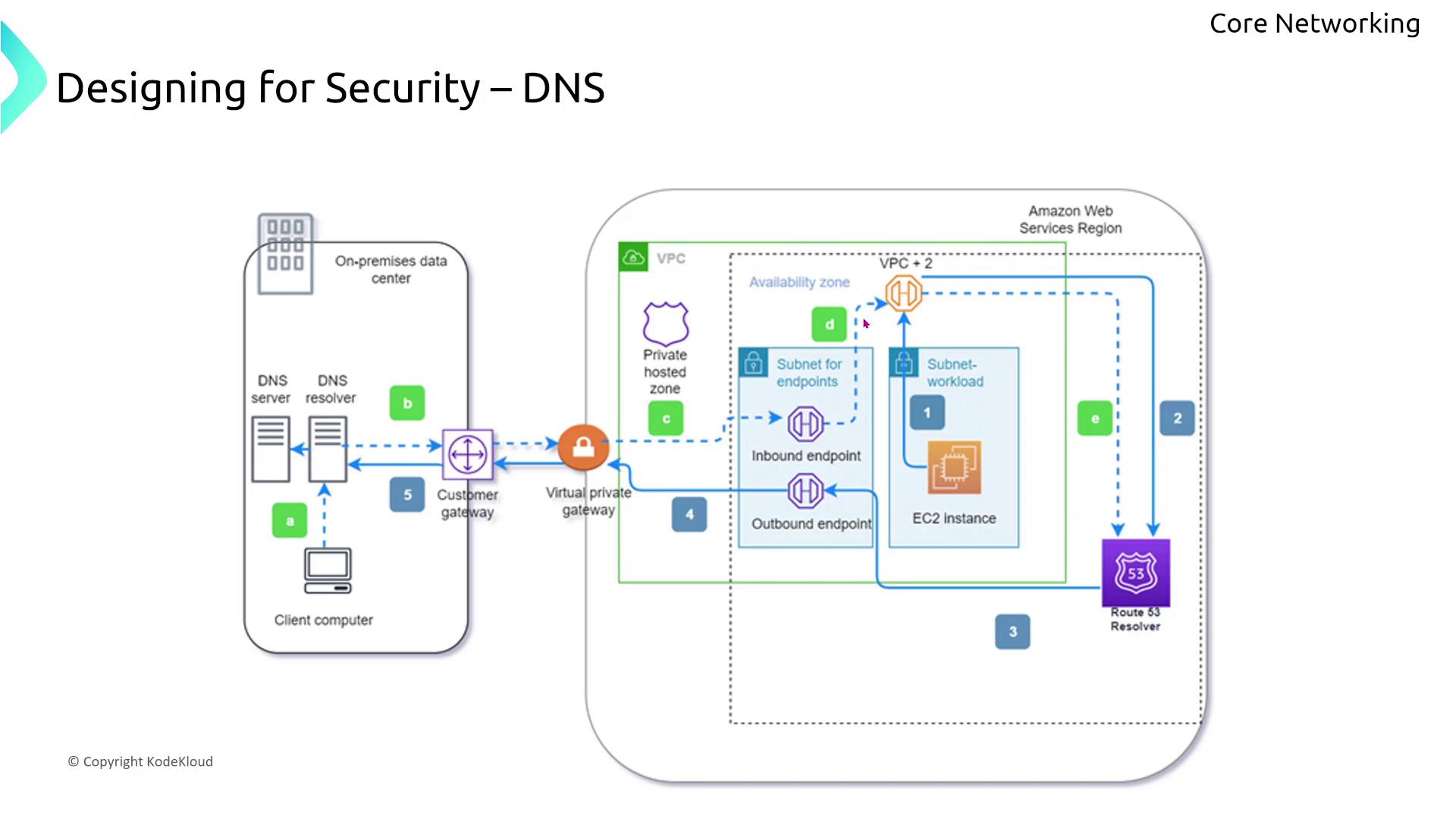
Secure DNS Resolution within a VPC
For multi-tier applications, ensuring that EC2 instances communicate using private DNS names is fundamental to security. Enable DNS resolution and hostname settings within your VPC so that internal DNS queries do not traverse the public internet. One effective approach uses the Route 53 Resolver to connect an on-premises data center with AWS, allowing granular control over DNS query rules.
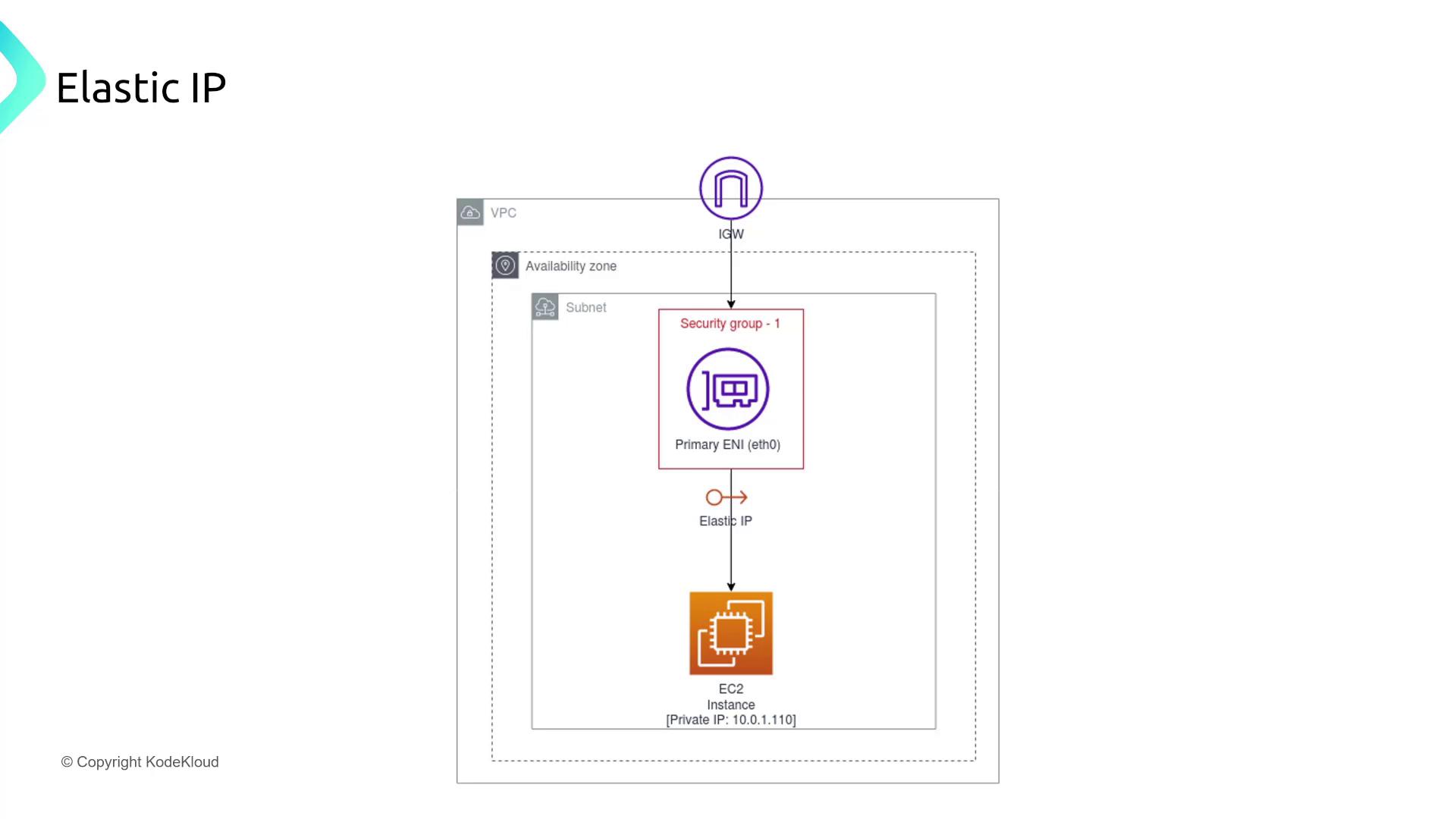
Elastic IP Addresses for Persistent Connectivity
For web applications hosted on EC2 instances, maintaining a consistent public IP address is critical, even after instance restarts. Assigning an Elastic IP (EIP) guarantees persistent public connectivity, unlike dynamically assigned public IPs that can change upon reboot.
An additional diagram illustrates an EC2 instance with a dedicated Elastic IP, ensuring continuous connectivity:
Enhancing Network Performance with Specialized Adapters
High-performance applications, such as multiplayer game backends or financial analytics platforms, demand low latency and high throughput. AWS offers two specialized networking options:
- Elastic Network Adapter (ENA): Provides consistent throughput and low latency for demanding applications. Ensure security groups and NACLs are tuned to optimize traffic flow.
- Elastic Fabric Adapter (EFA): Ideal for high-performance computing (HPC) environments, offering isolated, low-latency communication perfect for HPC workloads.
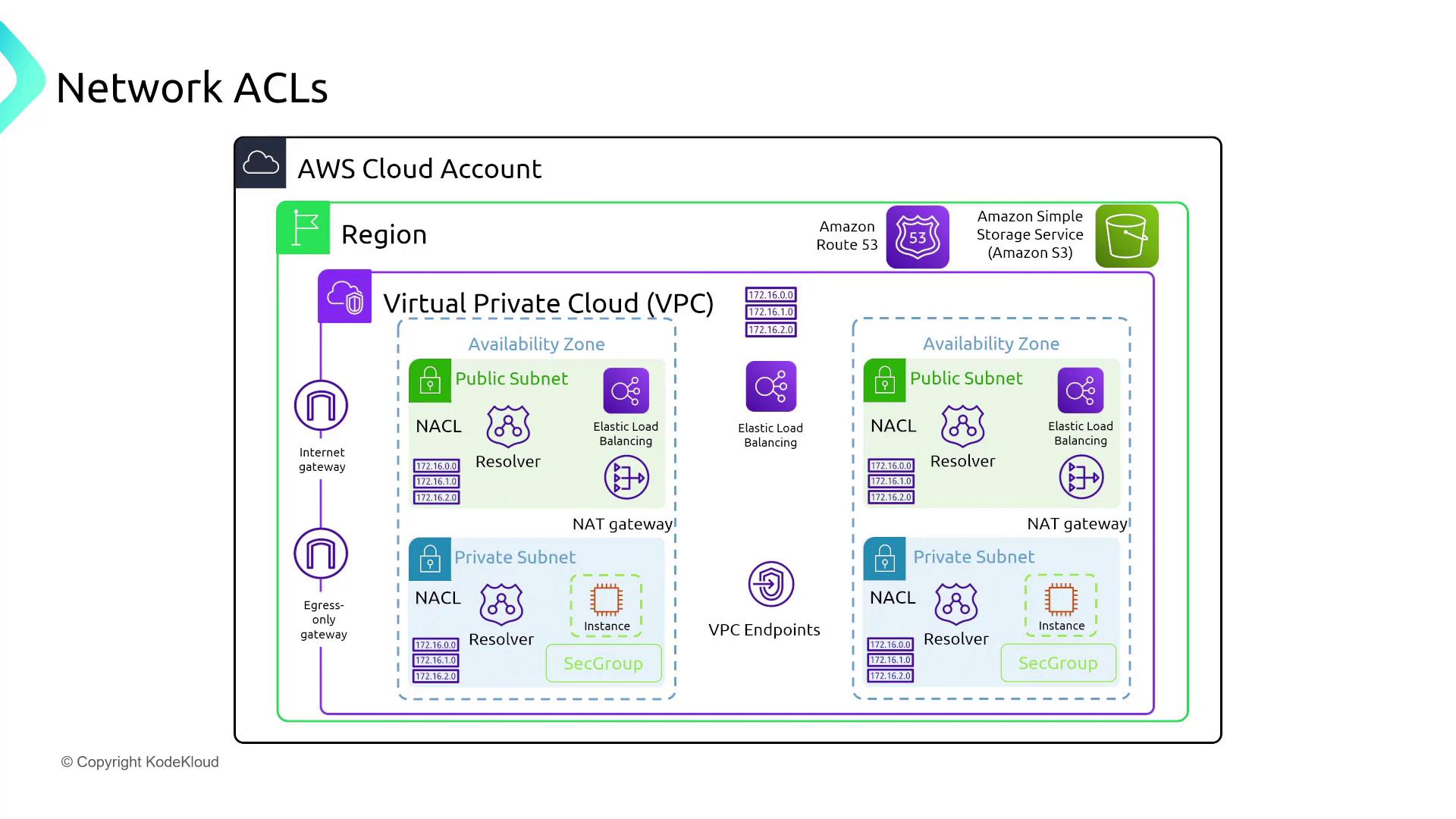
Network Access Control Lists (NACLs)
NACLs provide stateless filtering at the subnet level. Consider the following use cases:
Securing Database Servers: In a multi-tier application, configure NACLs on private subnets so that only traffic from web servers (within a specified IP range) is allowed, with outbound rules permitting necessary responses. (Remember that NACLs evaluate rules in order; deny rules should precede allow rules to be effective.)
Note
Ensure your NACL rules are strictly ordered, as misconfiguration may inadvertently allow unauthorized access.
Blocking Unauthorized Access: For FinTech companies facing repeated attacks, implement top-priority deny rules in your NACL configurations to block known malicious IP ranges.
Allowing Outbound Connections: For gaming companies, configure NACLs to allow all outbound traffic while restricting inbound traffic to ephemeral ports, ensuring only response traffic is accepted.
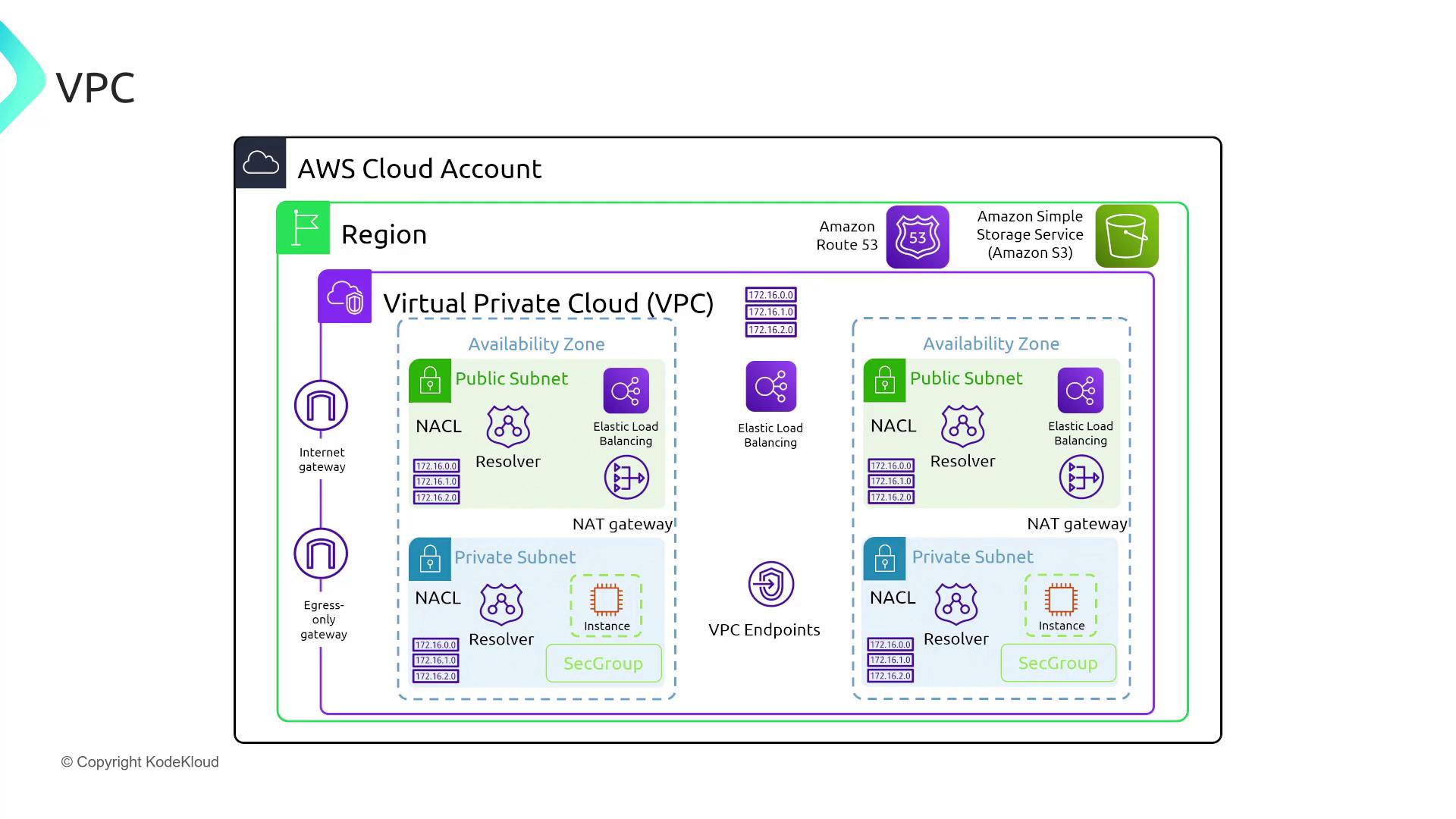
Additional diagrams illustrate broader VPC architectures featuring public/private subnets, NAT gateways, and load balancers:
Security Groups for Stateful Firewall Protection
Security Groups act as stateful firewalls and are essential for controlling traffic between instances within a VPC. Consider these scenarios:
Inter-Instance Communication: For backend applications that need to communicate with database and cache layers, assign all related instances to a single security group. This allows free intra-group communication while blocking external access by default.
Layered Security Model: For applications with multiple tiers (e.g., healthcare applications), create separate security groups for the web, application, and database layers. Limit communication between layers to only essential interactions to reduce cross-tier vulnerabilities.
Application Load Balancers (ALBs) and SSL/TLS Termination
Applications that process sensitive data, such as FinTech payment gateways, benefit from offloading SSL/TLS termination to an Application Load Balancer (ALB). By terminating the SSL/TLS connection at the ALB, the backend servers receive decrypted traffic, thereby reducing their computational load. AWS Certificate Manager simplifies public certificate management, ensuring smooth certificate rotation.
A diagram below illustrates an architecture with ALBs in public subnets and internal load balancers or application servers within private subnets:
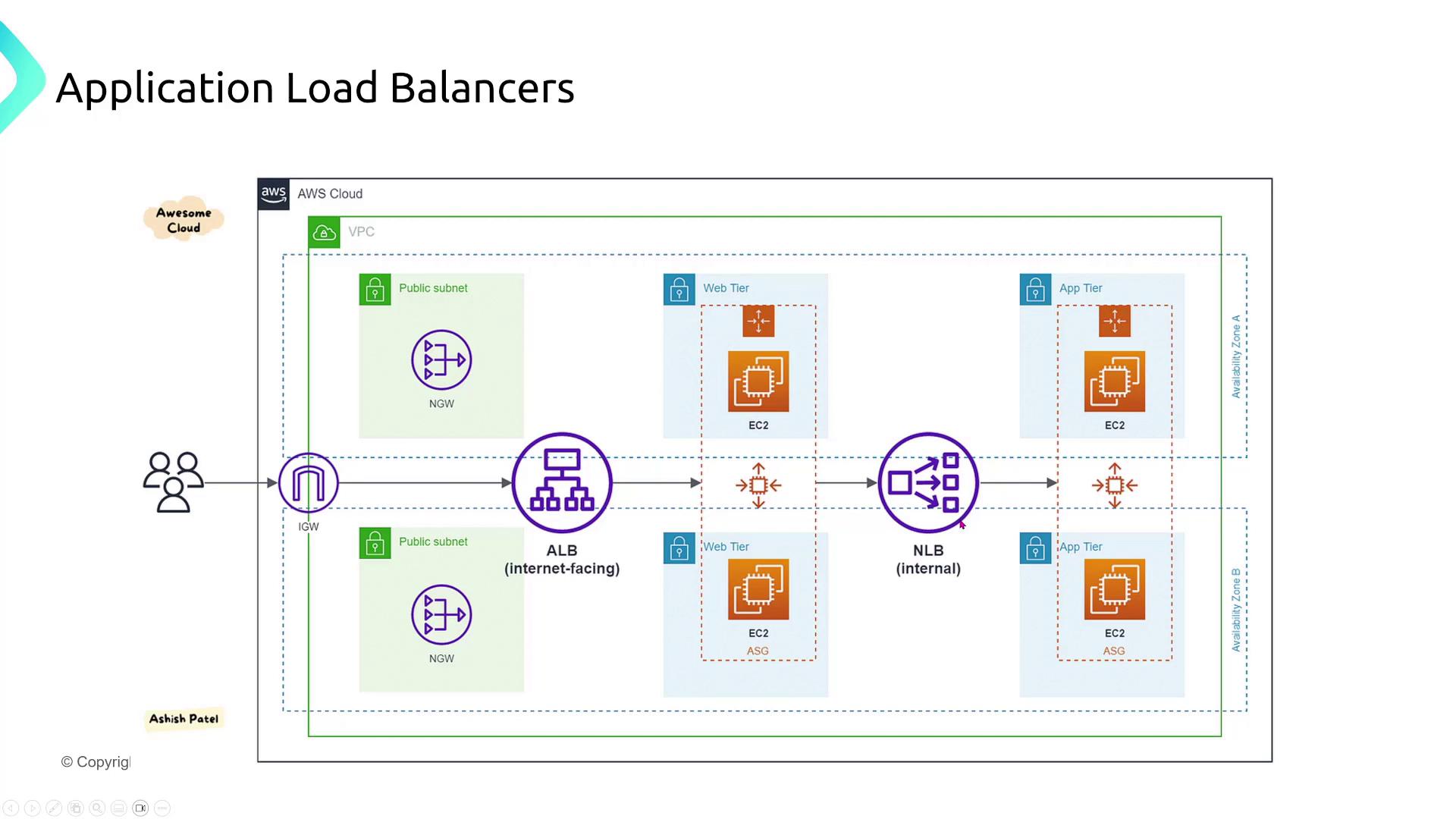
This deployment demonstrates how VPCs, subnets, and load balancers work together to provide secure and efficient communications.
This article has provided a comprehensive overview of AWS networking security strategies—from multi-VPC and subnet designs to specialized adapters, NACLs, and security groups. By configuring these components effectively, organizations can build architectures that are secure, scalable, and compliant with regional data regulations.
For more details on AWS security best practices and network design, explore the following resources:
Happy architecting!
Watch Video
Watch video content