- Authentication: Confirms the identity of the connected machine.
- Data Encryption: Secures data as it travels between your device and the server using HTTPS.
- Data Integrity: Assures that the transmitted data remains unaltered throughout transit.
What Is AWS Certificate Manager?
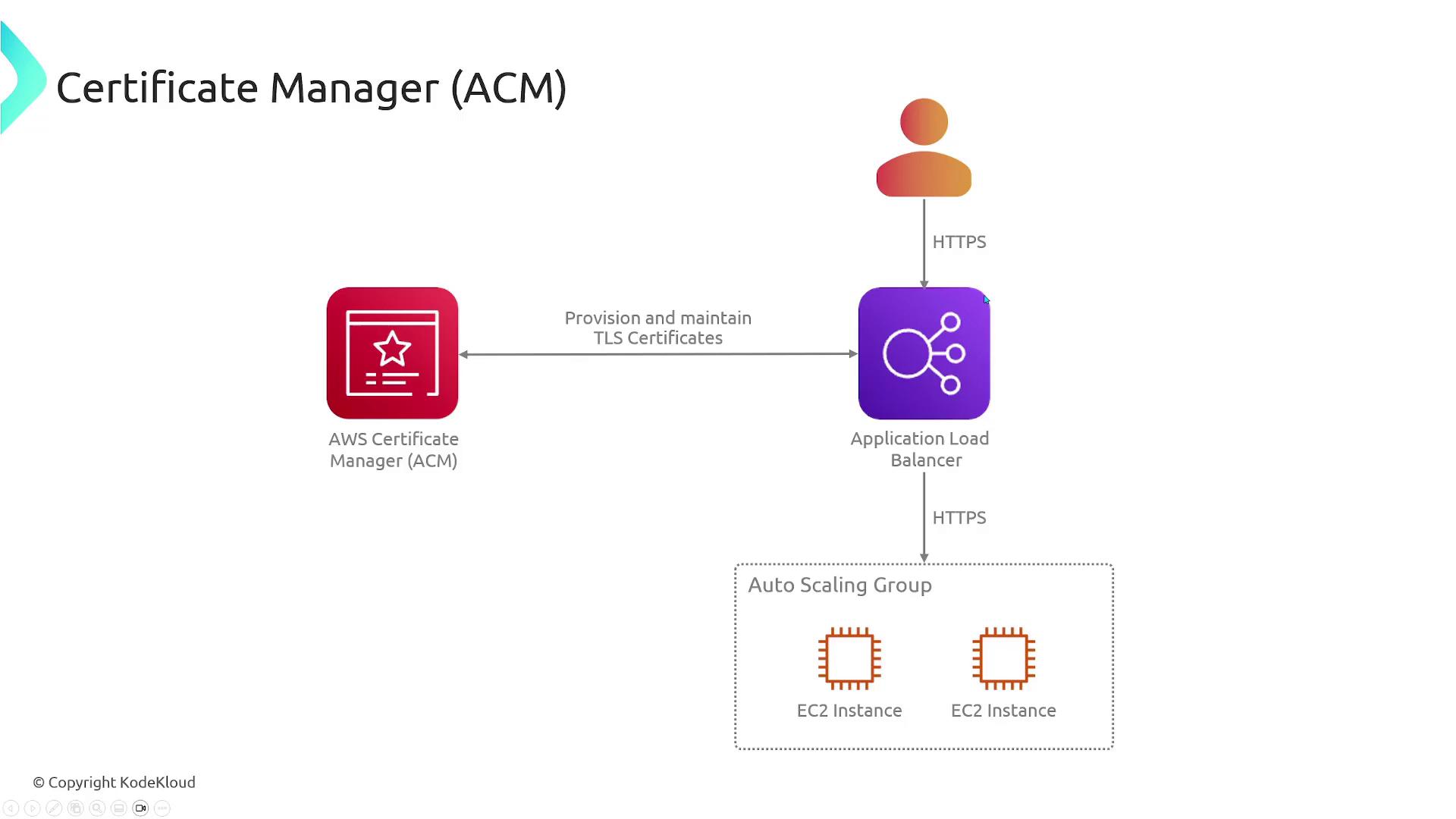
AWS Certificate Manager (ACM) is a managed service designed to simplify the generation and management of SSL/TLS certificates for secure web operations. Its key components include:- AWS Private Certificate Authority (CA): A trusted entity responsible for issuing certificates.
- ACM: Facilitates the entire process—from generating certificates to managing their deployment across multiple AWS services.
Requesting and Validating Certificates
ACM provides two main methods for certificate management:- Request a new SSL/TLS certificate.
- Import an existing certificate.
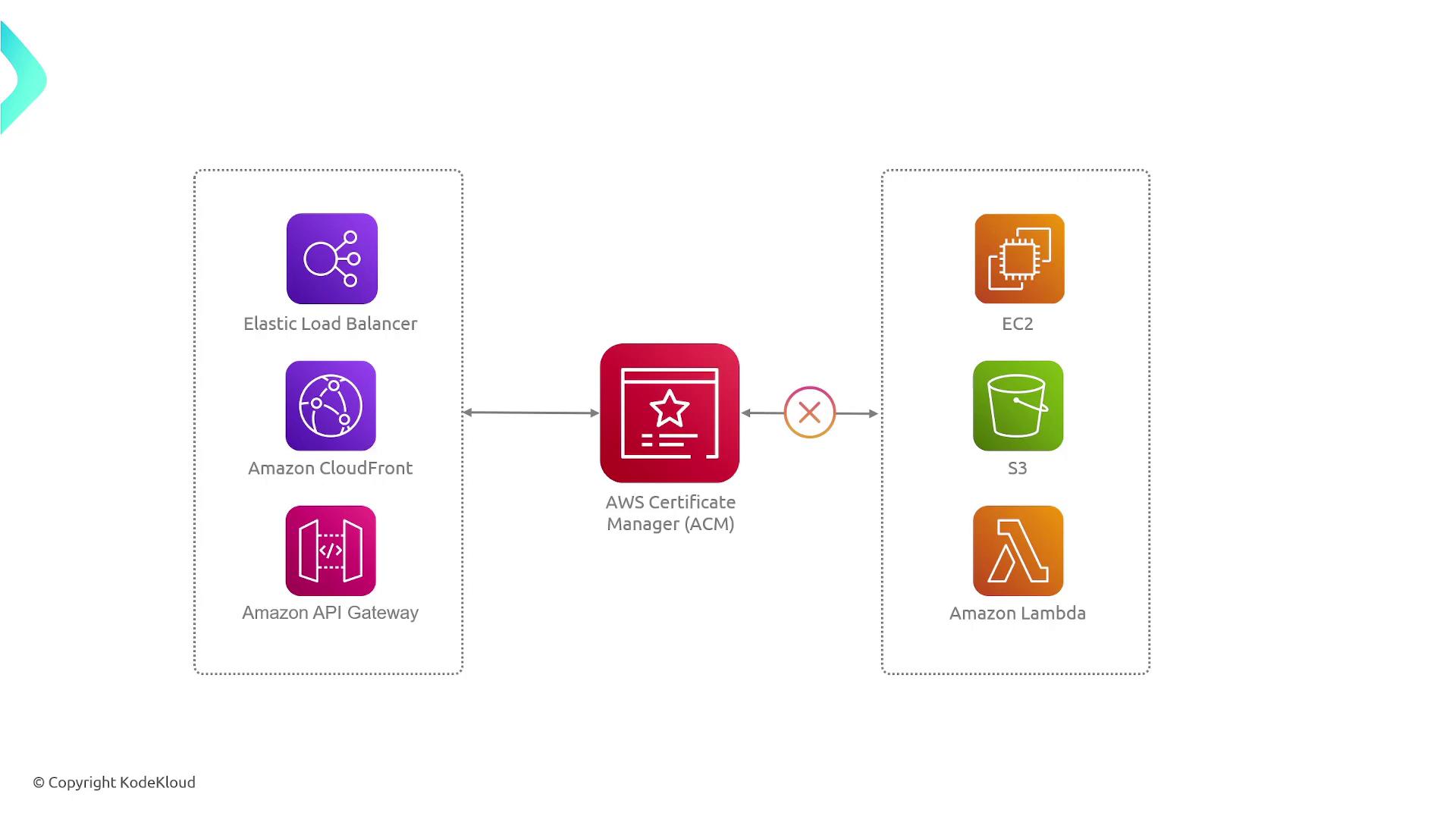
Service Integration and Limitations
ACM integrates with several key AWS services such as:- Elastic Load Balancer
- CloudFront
- API Gateway
ACM is designed to simplify secure communications across your AWS infrastructure by centralizing certificate management.
- EC2 Instances: ACM certificates cannot be directly installed on EC2 instances; they must be used with services like an ELB that manage external traffic.
- Amazon S3: To enable HTTPS for S3 static website hosting, route traffic through CloudFront using ACM.
- AWS Lambda: Direct support for ACM certificates is not available for Lambda functions.
How ACM Works
Using ACM involves several straightforward steps:- Request a Certificate: Start by submitting a request for the desired domain names.
- Domain Ownership Verification: Confirm that you own or control the specified domains.
- Certificate Issuance: Once the domains are verified, ACM issues the certificate.
- Automatic Renewal: ACM automatically renews certificates, eliminating the need for manual tracking.
- Integration: Finally, integrate the certificate with an AWS service, such as attaching it to an HTTPS listener on an Elastic Load Balancer.

Key Features of AWS Certificate Manager
ACM offers several features that streamline certificate management and enhance web security:- Automated Certificate Provisioning: Simplifies the process of acquiring certificates.
- Auto-Renewal: Automatically renews certificates to help avoid unexpected expirations.
- Seamless Deployment: Integrates natively with supported AWS services, reducing the risk of manual errors.
- Central Management: Provides a unified dashboard to manage all of your certificates efficiently.
- Deep AWS Integration: Works seamlessly with various AWS services for enhanced security.
