
Setting Up AWS Inspector
Before initiating assessments, you need to define the AWS resources to be scanned by setting up an assessment target—a specific resource group. This allows you to target only production environments, for instance, while excluding development resources.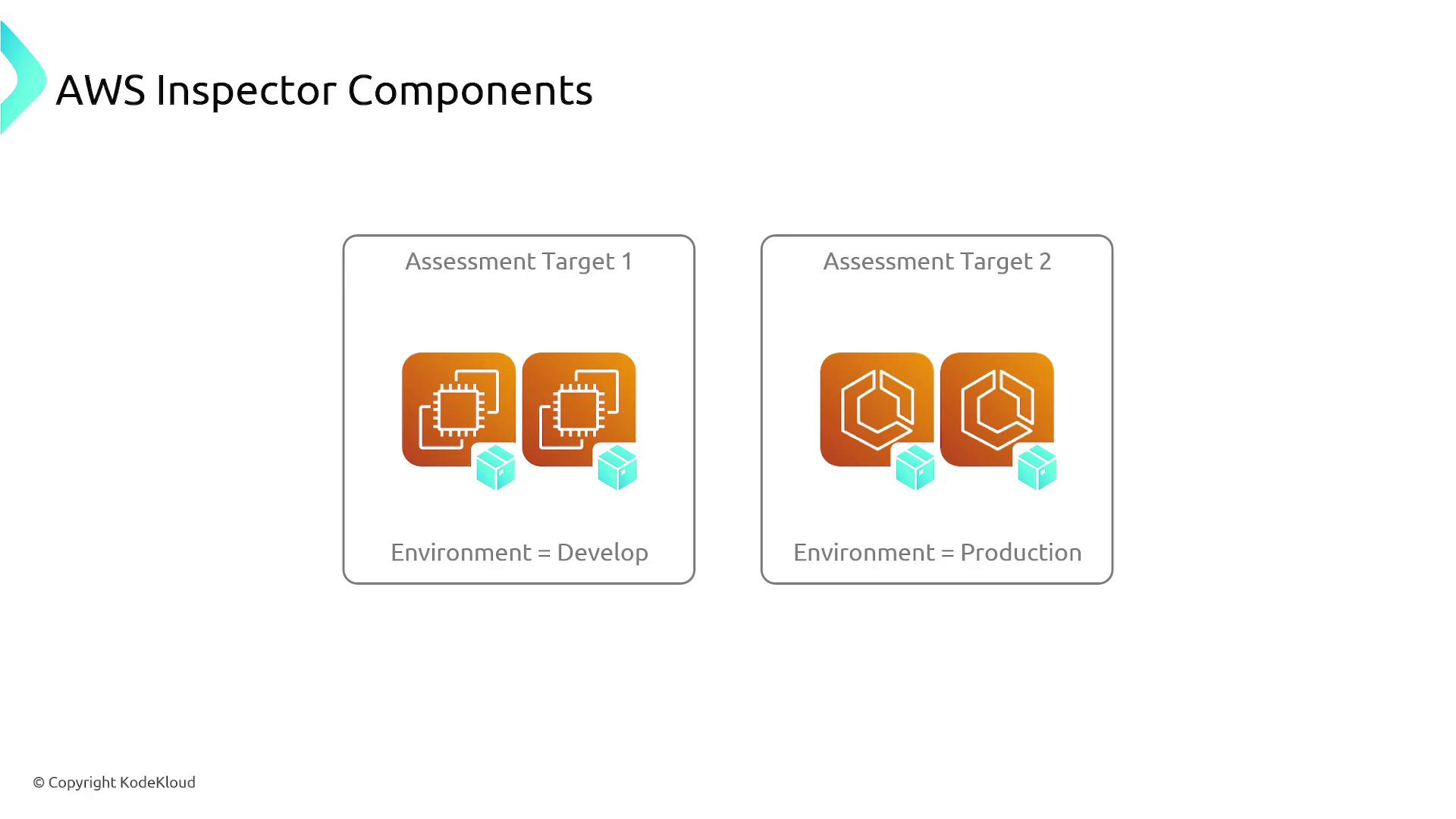
- Create an assessment target by grouping resources based on appropriate tags.
- Select the rules packages that align with your security requirements.
- Initiate the assessment to start scanning the defined resources.
For detailed guidance on tagging resources for assessment targets, refer to the AWS Inspector documentation.
Key Features of AWS Inspector
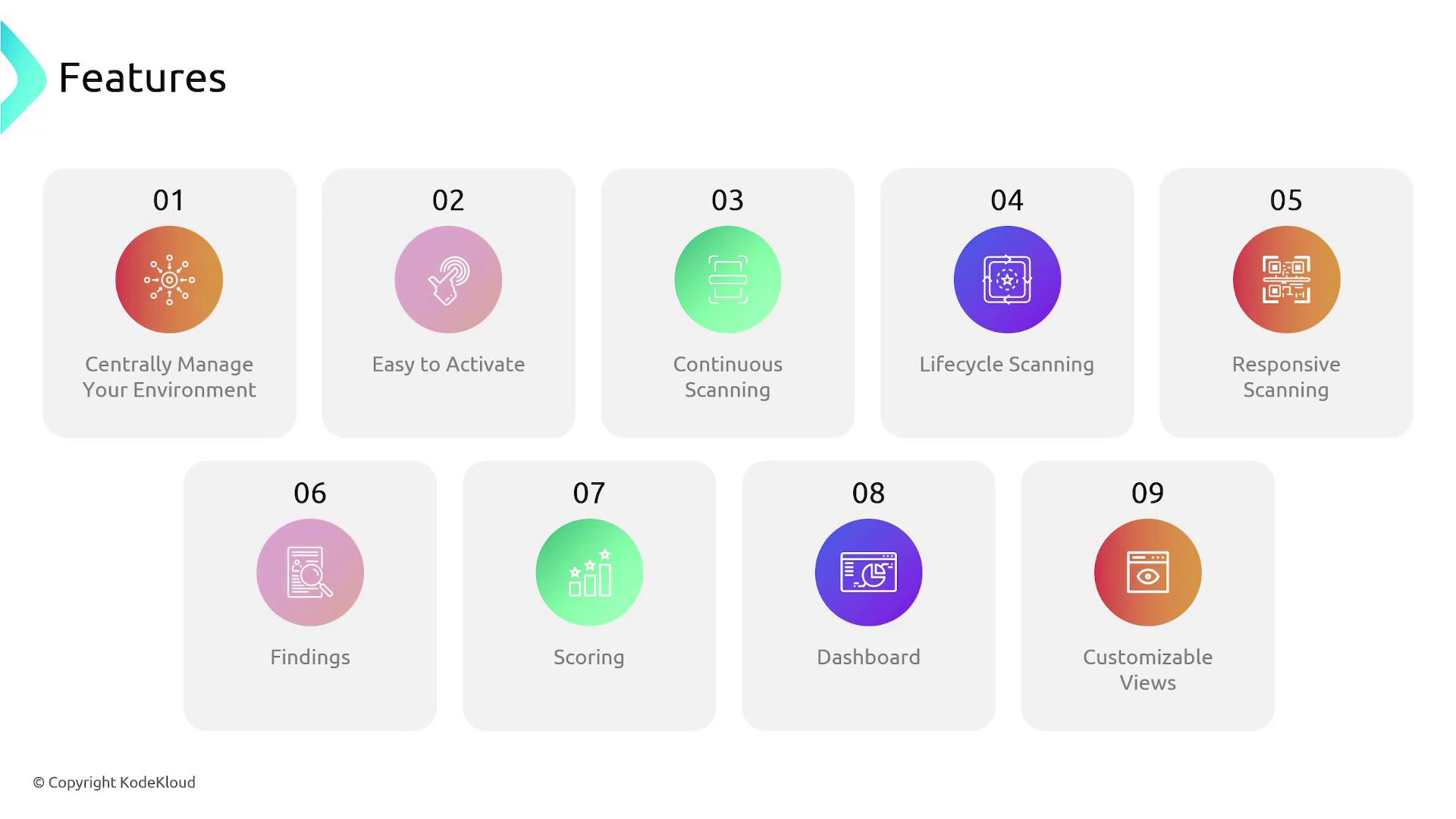
AWS Inspector offers a centralized management approach through integration with AWS Organizations, which allows you to oversee vulnerability assessments across multiple AWS accounts. Its one-click activation and continuous monitoring provide a user-friendly yet powerful security solution. Key features include:- Continuous and Responsive Scanning: AWS Inspector monitors for vulnerabilities in real time and triggers re-scans automatically after any significant system modifications.
- Detailed Findings and Severity Scoring: The service generates in-depth findings with severity scores, enabling you to prioritize remediation efforts based on risk.
- Customizable Centralized Dashboard: A user-friendly dashboard displays all findings, helping you to focus on resolving critical security issues.
Types of Findings
AWS Inspector classifies its findings into three primary categories:-
Package Vulnerability:
These findings highlight vulnerabilities in software packages that could be exploited to compromise the confidentiality, integrity, or availability of your systems, potentially leading to unauthorized access. -
Code Vulnerability:
These alerts identify exploitable segments in your code, which might result in injection flaws, data exposure, weak cryptographic practices, or insufficient encryption. AWS Inspector leverages automated reasoning and Amazon CodeGuru to assess the security compliance of your Lambda function code. -
Network Reachability:
These findings point out open network paths to Amazon EC2 instances or overly permissive network configurations, including misconfigured security groups, access control lists, or Internet Gateways.
AWS Inspector Workflow
The AWS Inspector workflow is straightforward and can be summarized with the following steps:- Define assessment targets by specifying the resources to be scanned.
- Select the relevant rules packages to identify vulnerabilities and ensure compliance.
- Launch the assessment to scan your configured environment.
- Review the findings generated by AWS Inspector.
- Investigate and remediate any issues detected.

This continuous, responsive, and centralized scanning process makes AWS Inspector an essential security tool in dynamic AWS environments.