Introduction to Encryption
Encryption plays a pivotal role in protecting sensitive data. When data is stored without encryption, it is in plain text and vulnerable to unauthorized access. For instance, if your confidential health records, social security numbers, or credit card details are stored in plain text, any unauthorized user or hacker who gains access to the server could easily read this data. Encryption transforms data into a form that appears as gibberish without the proper cryptographic key. These keys are essential; without the correct key, decryption is impossible, ensuring both confidentiality and data integrity. Additionally, encryption guards against data tampering and secures data during network transmission.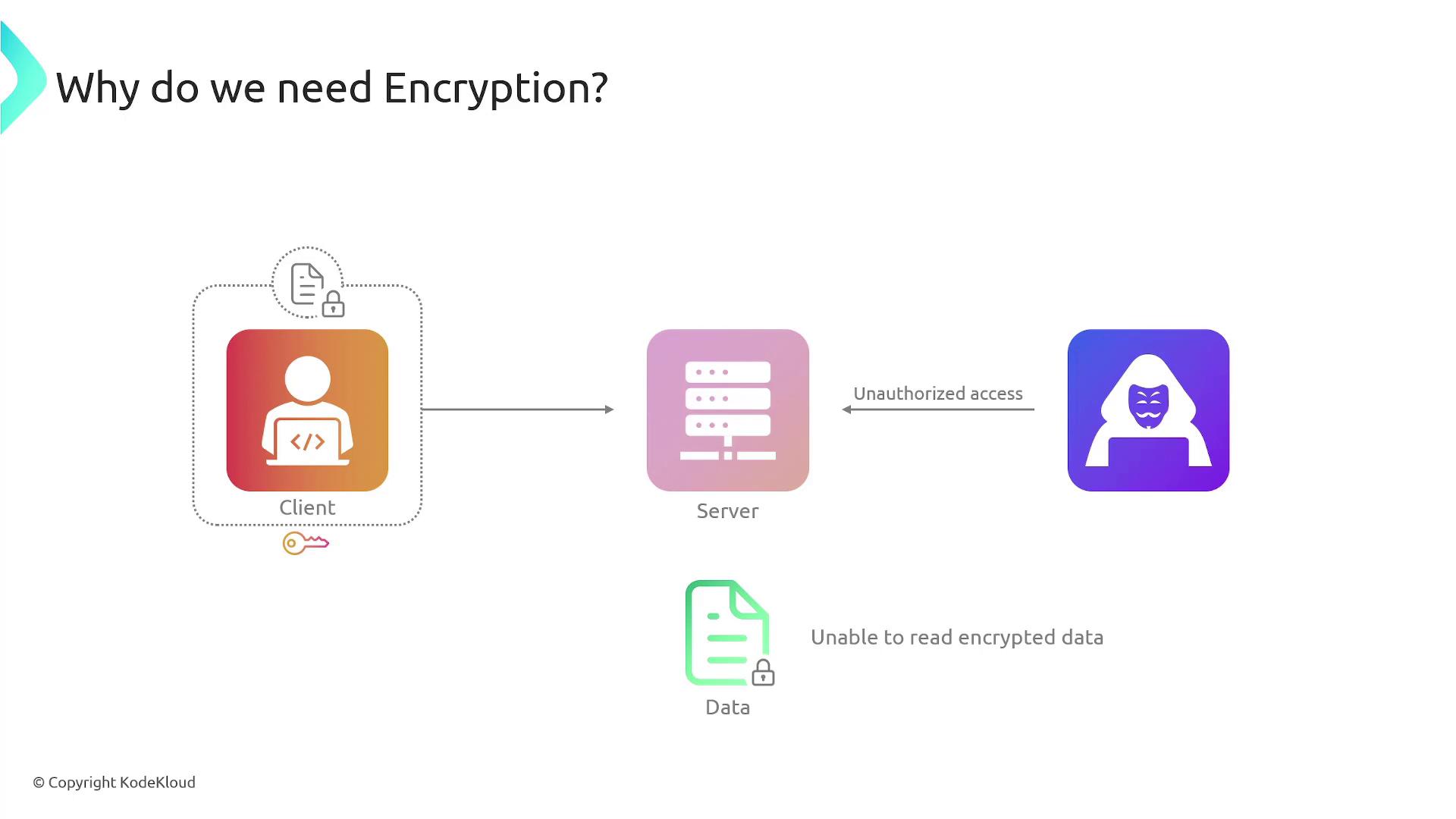
What is AWS KMS?
AWS KMS is a managed service designed to simplify the creation and control of cryptographic keys used for AWS services and applications. With AWS KMS, you no longer have to manage the entire key lifecycle—AWS KMS handles key generation, rotation, deletion, and policy enforcement. It supports cryptographic operations such as encryption, decryption, digital signing, and verification.
Key Attributes and Policies
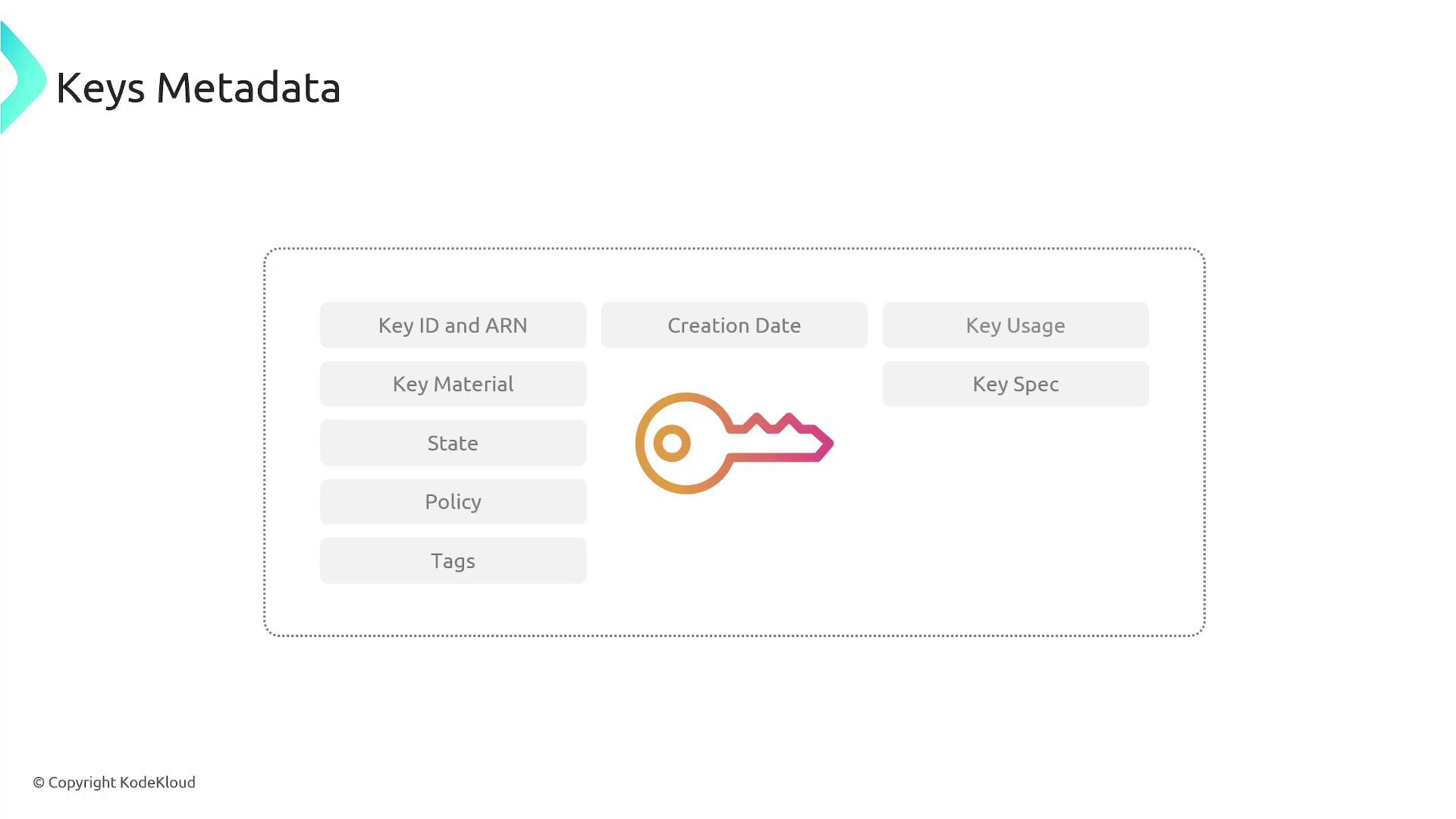
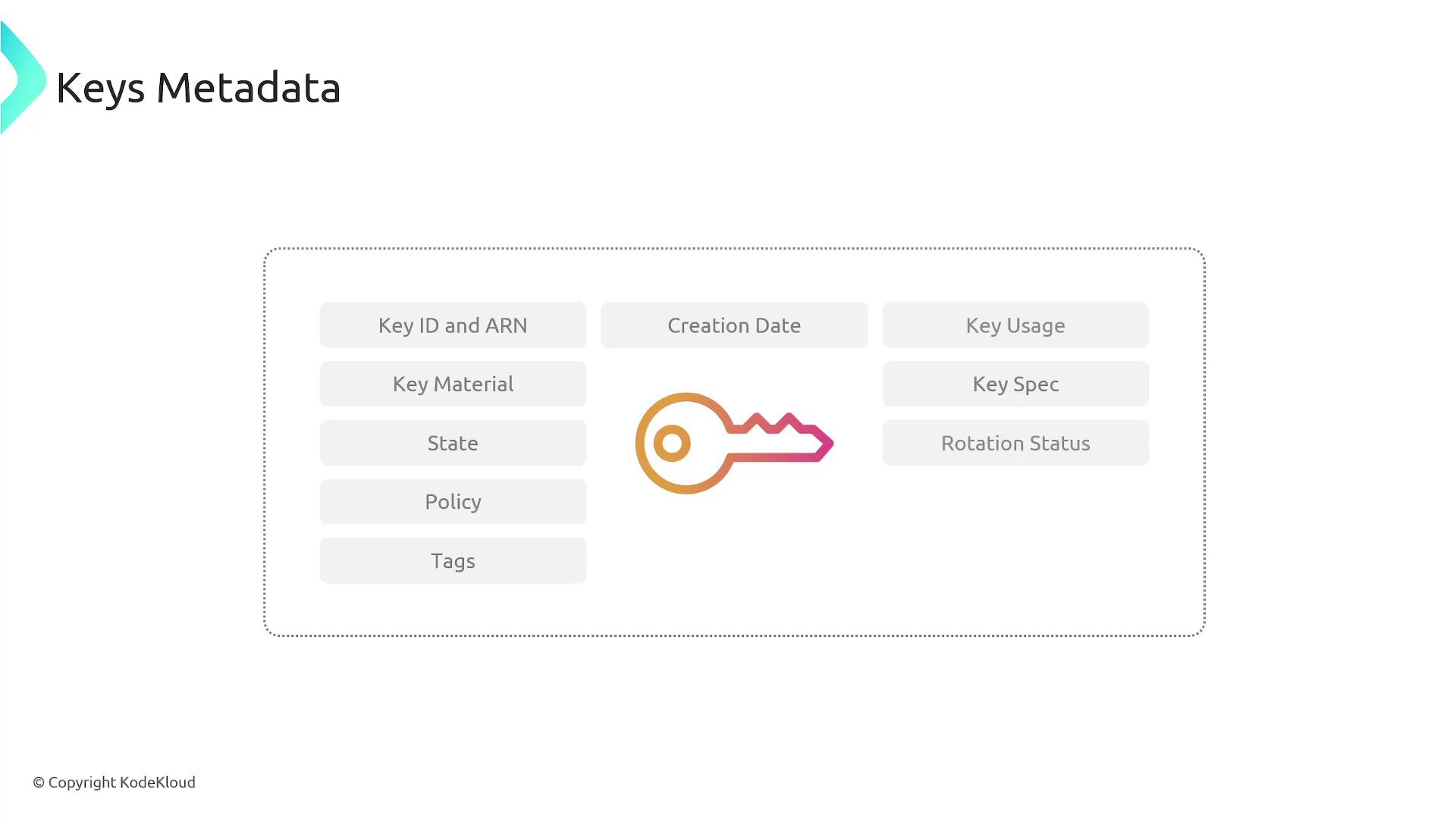
Each KMS key is characterized by multiple attributes:- Key ID and Key Material: This comprises the cryptographic material used for encryption and decryption. In AWS KMS, the key material is either generated internally or imported.
- States: Keys may be enabled, disabled, pending deletion, or pending import.
- Policy: Allows you to control which users have access to the keys and the specific operations they can perform.
- Tags, Creation Date, Key Usage, and Key Specs: These metadata elements track configurations such as permitted operations (encrypt/decrypt for symmetric keys or sign/verify for asymmetric keys) and rotation settings.
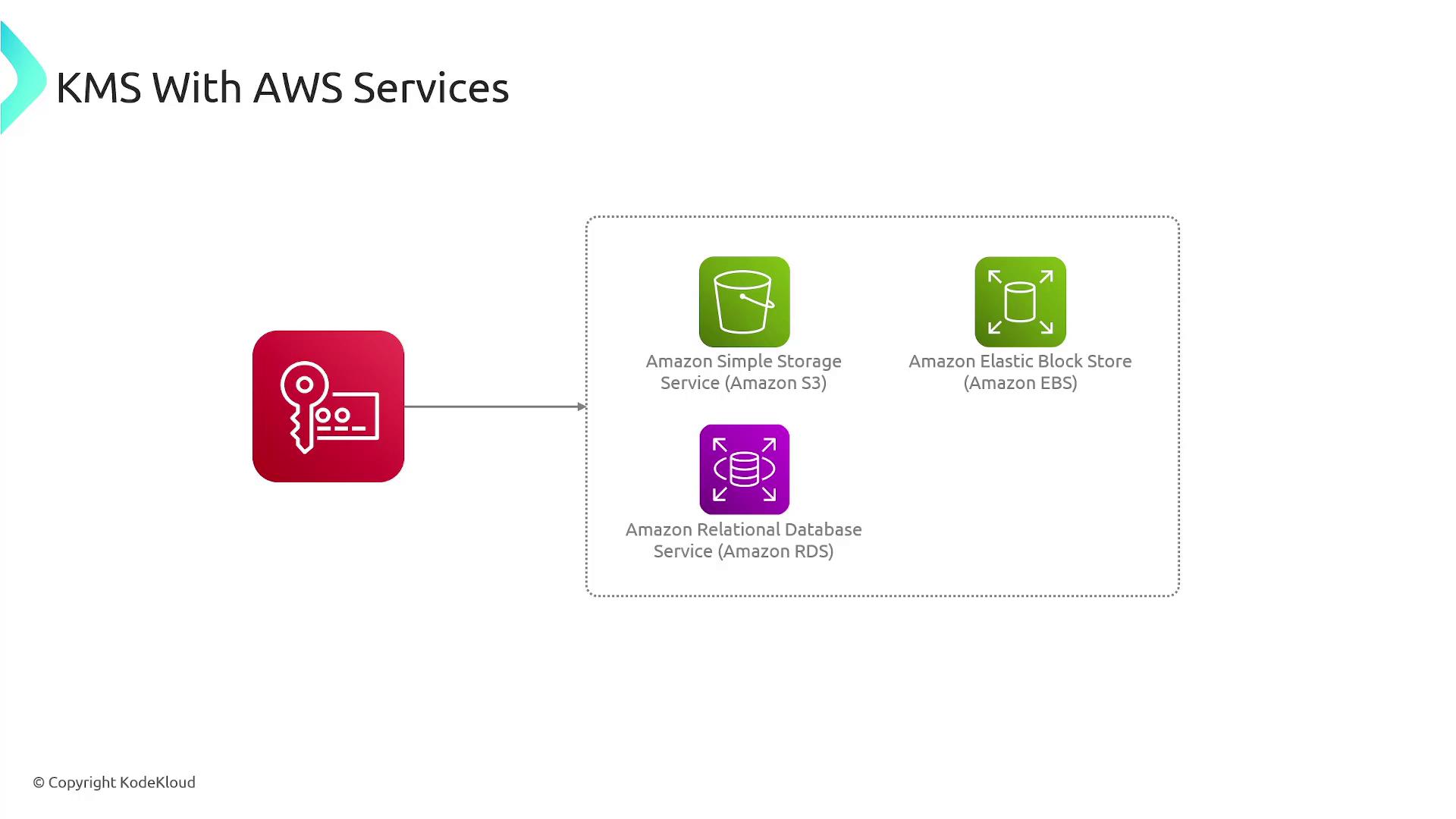
Integration with AWS Services
AWS KMS is designed to integrate seamlessly with various AWS services, ensuring a secure environment:- Amazon S3: Objects stored in S3 can be encrypted automatically using a KMS key.
- Amazon Elastic Block Store (EBS): Encrypted volumes leverage KMS for their encryption.
- Amazon RDS: Underlying data for RDS instances can be encrypted with KMS.
Types of Keys in KMS
AWS KMS supports several key types to meet diverse security and operational requirements:-
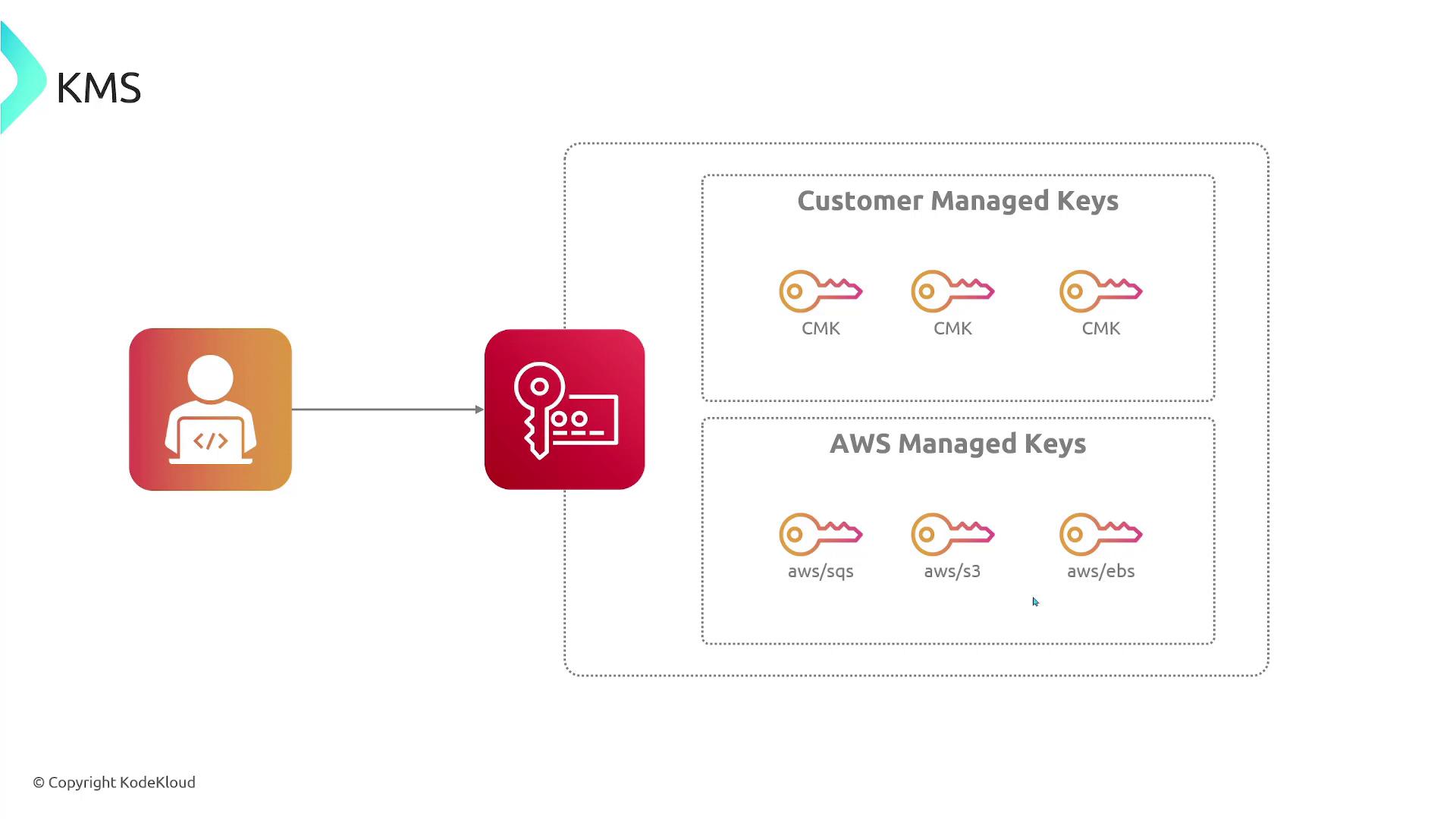
Customer Master Keys (CMKs) / KMS Keys:
The primary resource used to encrypt, decrypt, and re-encrypt data. With customer managed keys, you have full control over creation, deletion, and policy management; note that these keys incur a cost. -
Data Keys:
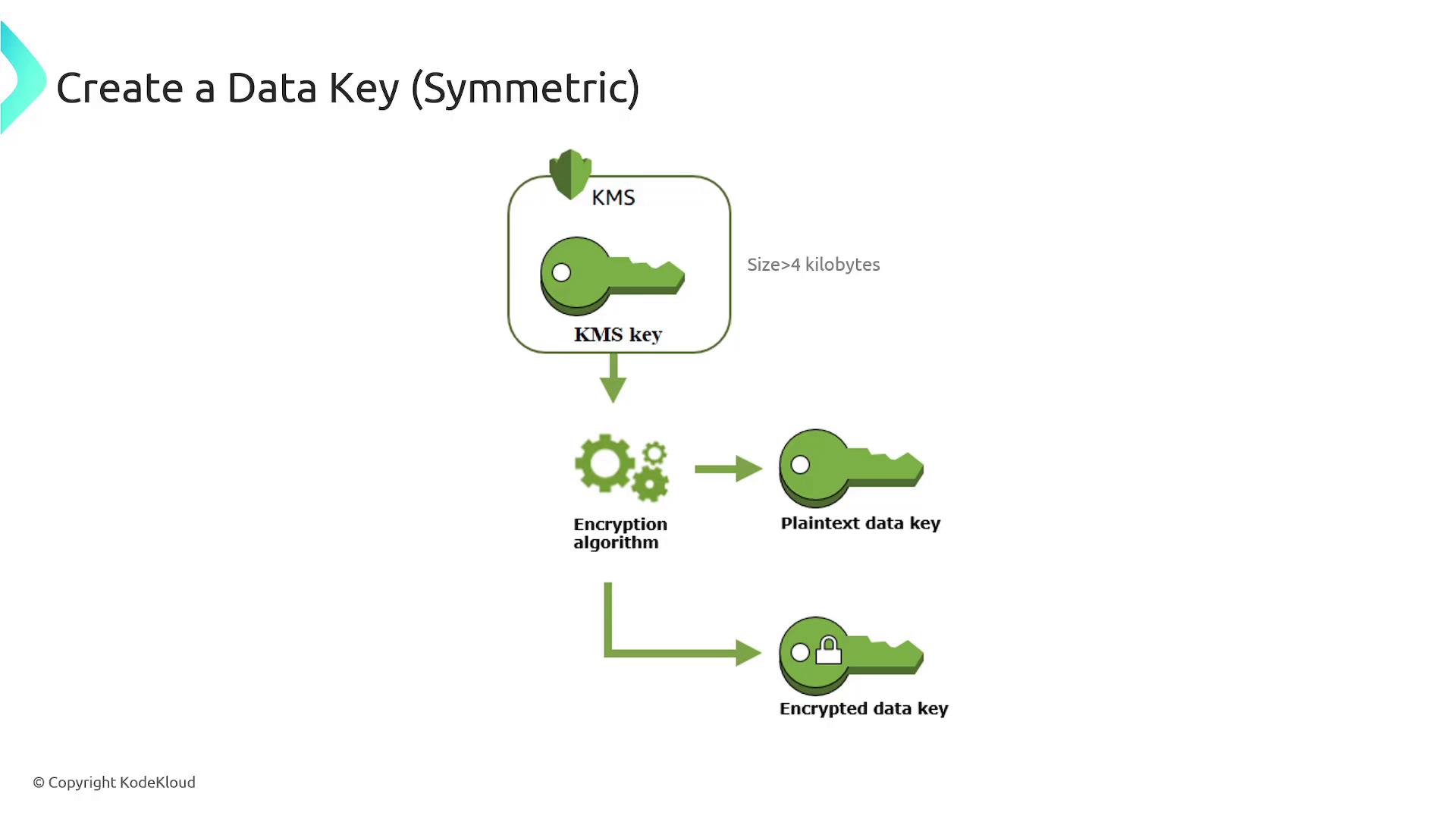
These are used for encrypting large volumes of data. Because CMKs have a size limitation (around 4 kilobytes), AWS KMS generates data keys in two versions—plaintext and encrypted. The plaintext version is used to encrypt your data, while the encrypted version is stored with the data to allow later decryption. -
Imported Key Material:
This option lets you import your own key material, providing additional control over key lifecycle management. -
AWS Managed Keys:
These keys are automatically created, managed, and rotated by AWS for services like S3, EBS, and Redshift. Unlike customer managed keys, AWS managed keys cannot be modified and do not incur additional costs. -
AWS Owned Keys:
Fully managed by AWS, these keys are used across various AWS accounts to protect metadata and operational elements and are not visible to individual accounts.
Symmetric vs. Asymmetric Encryption
In AWS KMS, encryption methods are categorized into two primary types:Symmetric Encryption
Symmetric encryption uses a single key for both encryption and decryption. This is the most common method within KMS, where the same key handles the complete encryption-decryption cycle.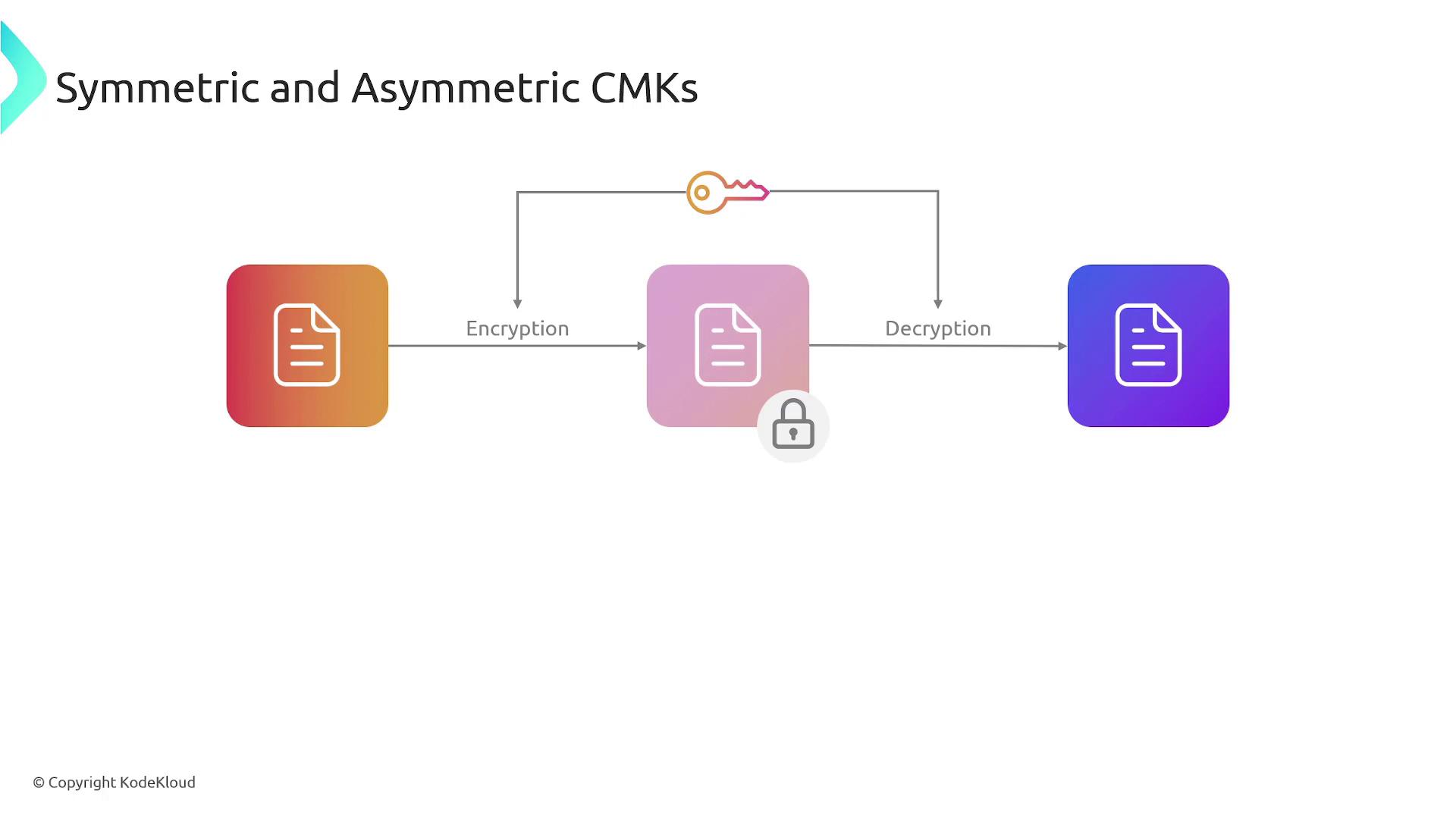
Asymmetric Encryption
Asymmetric encryption involves a key pair—a public key and a private key. The public key is used to encrypt data or verify a signature, while the private key is used to decrypt data or to create a digital signature. This method allows the public key to be shared openly without exposing the private key.Using Data Keys for Encrypting Large Payloads
Since CMKs are limited to encrypting data up to approximately 4 kilobytes, AWS KMS employs data keys to handle larger payloads. The process of using data keys typically follows these steps:- AWS KMS generates a data key and returns both its plaintext and encrypted versions.
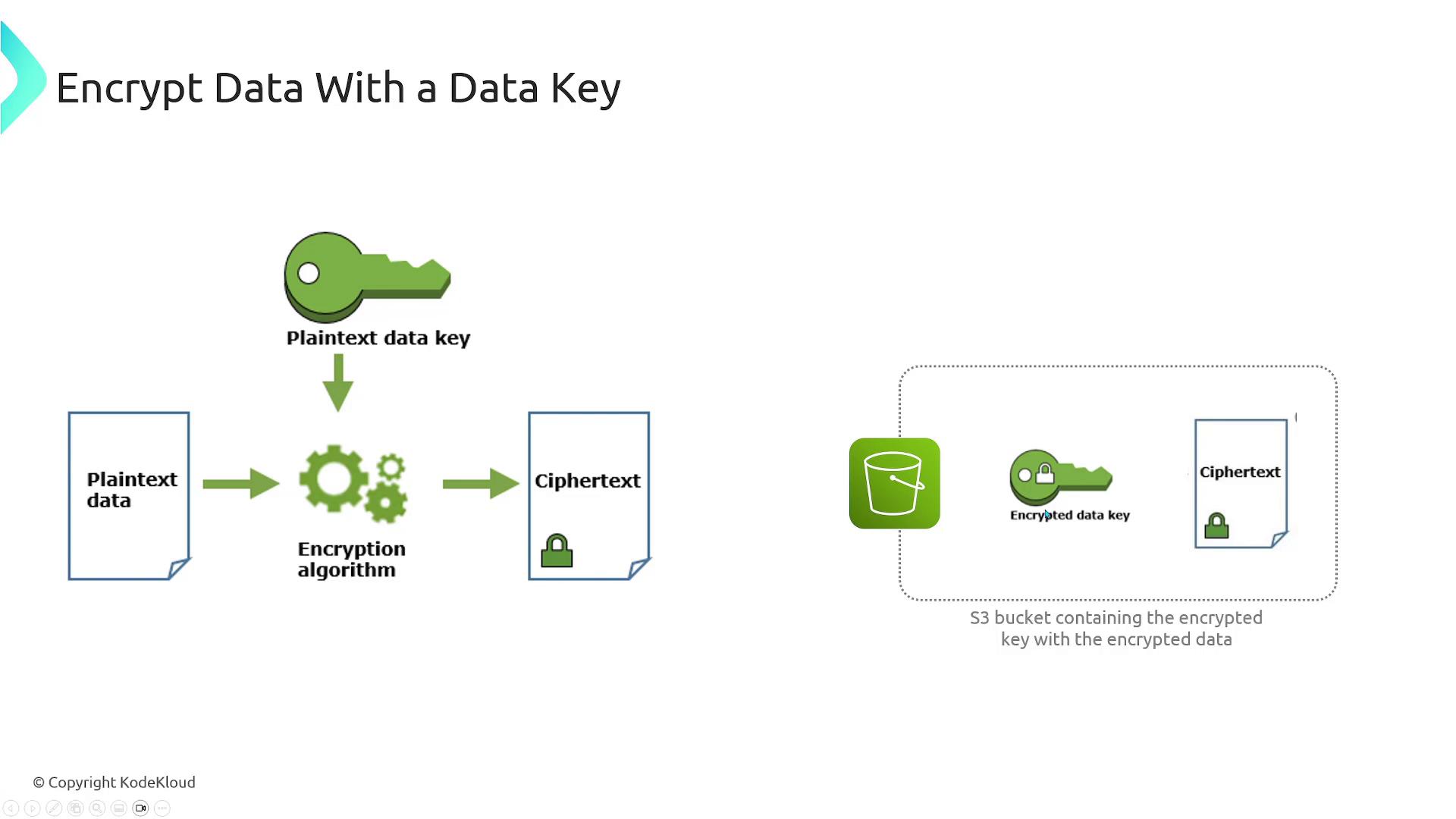
- The plaintext version of the data key is used to encrypt your larger dataset.
- The encrypted data key is then stored alongside the encrypted data (for example, in an S3 bucket) so it can be retrieved and used later for decryption.
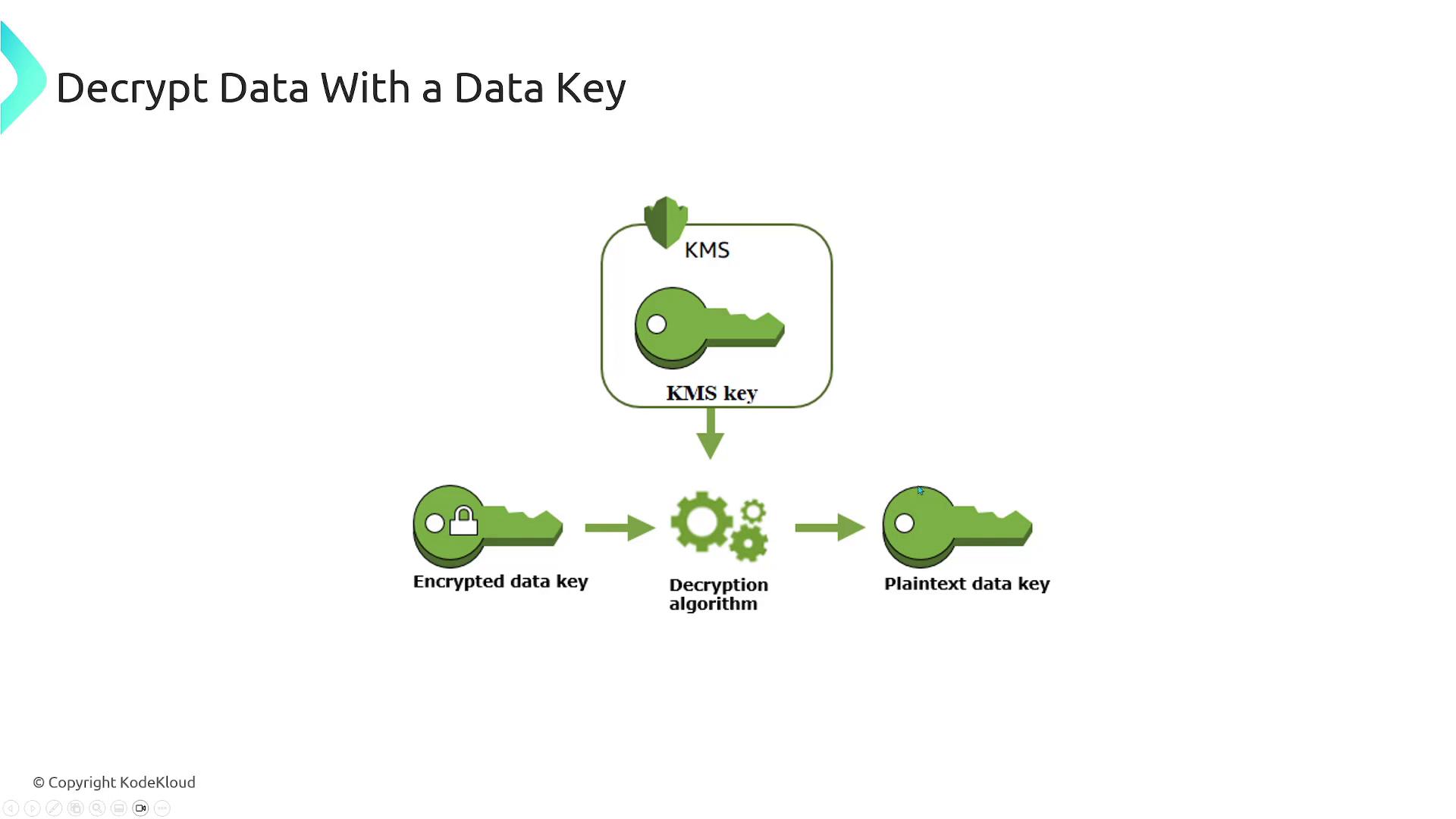
- When data decryption is required, AWS KMS first decrypts the stored encrypted data key, which is then used to decrypt the actual data.
Summary
AWS KMS offers centralized key management with seamless integration across AWS services. By utilizing AWS KMS, you can:- Create, manage, and enforce access policies for encryption keys.
- Automatically rotate keys and manage various key types to meet your needs.
- Securely encrypt both small payloads (using CMKs) and large amounts of data (using data keys).
- Leverage AWS CloudTrail and CloudWatch for comprehensive auditing and monitoring of cryptographic operations.
AWS KMS is essential for safeguarding your data by ensuring confidentiality, integrity, and compliance throughout your AWS environment.