When deploying AWS Network Firewall, always configure dedicated Firewall Endpoints within exclusive subnets. Avoid sharing these subnets with other resources to ensure comprehensive protection.
Firewall Endpoints and Subnet Configuration
To safeguard your VPC and its subnets, it is crucial to create dedicated Firewall Endpoints. These endpoints act as the primary points for traffic inspection. You must allocate a specific subnet for your firewall deployment because placing a Firewall Endpoint in a subnet with other resources could compromise their protection.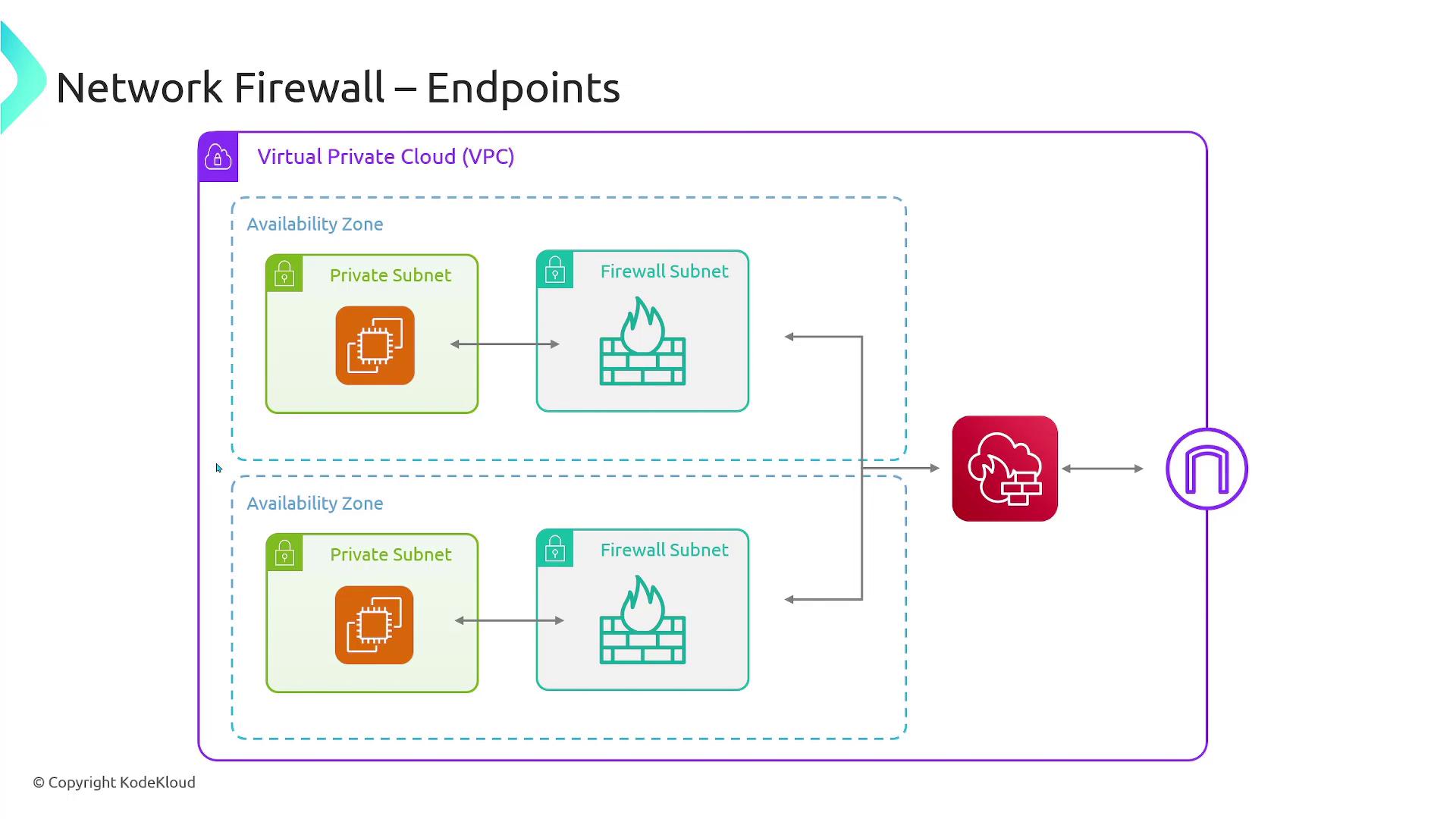
Key Features of AWS Network Firewall
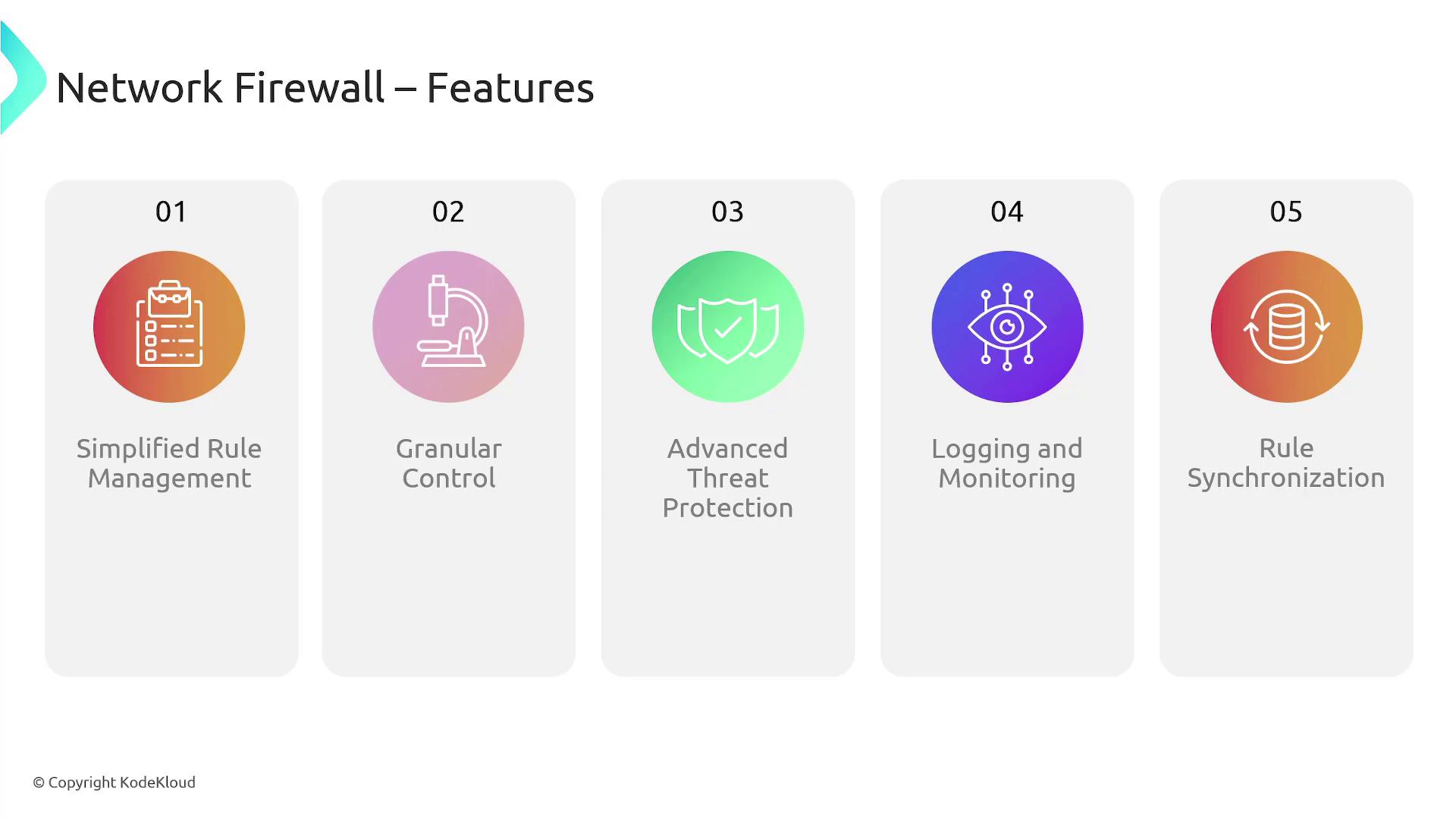
AWS Network Firewall offers a range of robust features designed to enhance your network security:- Centralized Rule Management: Simplify administration with rule groups that ensure consistent policies across multiple VPCs.
- Granular Traffic Control: Define detailed rules based on IP addresses, ports, protocols, and other traffic attributes.
- Deep Packet Inspection & Intrusion Detection: Identify and block advanced threats at both network and application layers.
- Comprehensive Logging: Maintain detailed logs of network and firewall activity for security analysis, compliance, and troubleshooting.
- Rule Synchronization: Seamlessly synchronize rules across multiple firewall instances, ideal for complex network architectures and multi-VPC environments.
Traffic Flow Process
When AWS Network Firewall is enabled, traffic within your VPC is directed through a carefully managed inspection process:- Inbound Traffic: Traffic from the Internet Gateway is first routed to the dedicated Firewall Endpoint in the firewall subnet. After being inspected and validated against the firewall rules, it is forwarded to the subnet hosting your resources.
- Outbound Traffic: Similarly, outbound traffic from your resources is sent to the Firewall Endpoint for inspection before exiting the VPC.
Improper routing configuration can lead to traffic bypassing the firewall inspection, potentially exposing your network to security risks.
Deployment Models
AWS Network Firewall supports two primary deployment models to suit different network architectures:- VPC Deployment: Protects resources within a single VPC by directing traffic from the Internet Gateway to the Firewall Endpoint and then to the target subnet.
- Transit Gateway Deployment: Provides centralized protection across multiple VPCs or on-premises networks by connecting them through an AWS Transit Gateway, eliminating the need for deploying individual firewalls for each VPC.
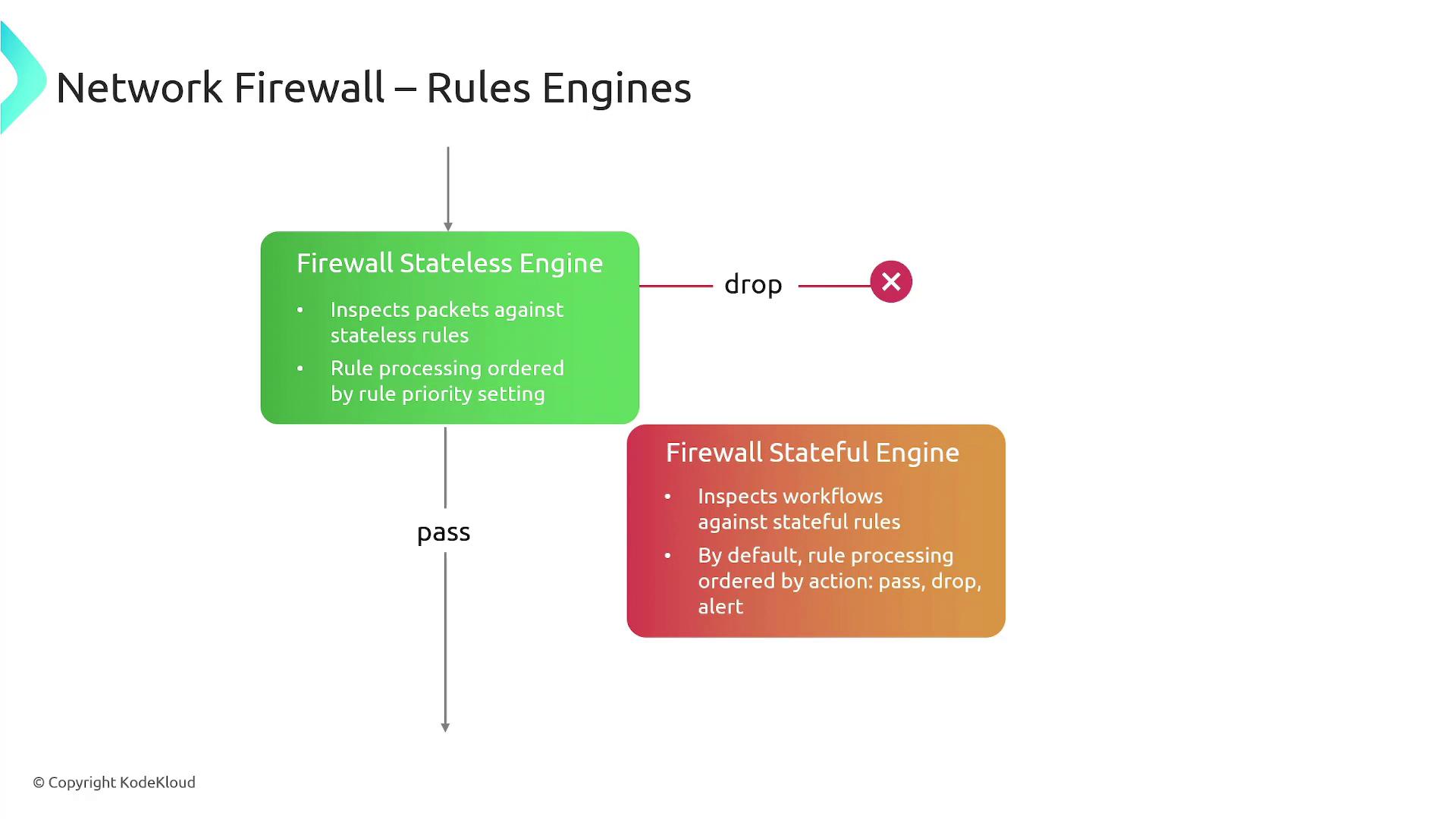
Rules Engines: Stateless vs. Stateful
AWS Network Firewall employs two distinct rules engines that allow you to tailor traffic inspection based on your security needs:- Stateless Rules Engine: Analyzes each packet independently without considering the traffic context. This engine processes rules in a user-defined order—similar to network ACLs—to determine if packets should be allowed or dropped.
- Stateful Rules Engine: Inspects packets within the context of their ongoing traffic flow. It recognizes the request-response pattern, supports complex rules, and logs traffic details. The engine processes pass rules first, followed by drop rules, and finally alert rules. It functions similarly to VPC security groups and is compatible with Suricata IPS.