AWS Solutions Architect Associate Certification
Services Storage
S3 Pres Signed URLs Demo
In this lesson, we demonstrate how pre-signed URLs work with Amazon S3. Pre-signed URLs allow you to grant temporary access to private S3 objects without making them public, ensuring controlled and secure sharing.
Creating the Bucket
Begin by navigating to the S3 console and selecting "Create bucket." Configure the bucket with default settings and ensure that public access is blocked. This setup guarantees that only you (as the root user) or users with explicit permissions can access your bucket.
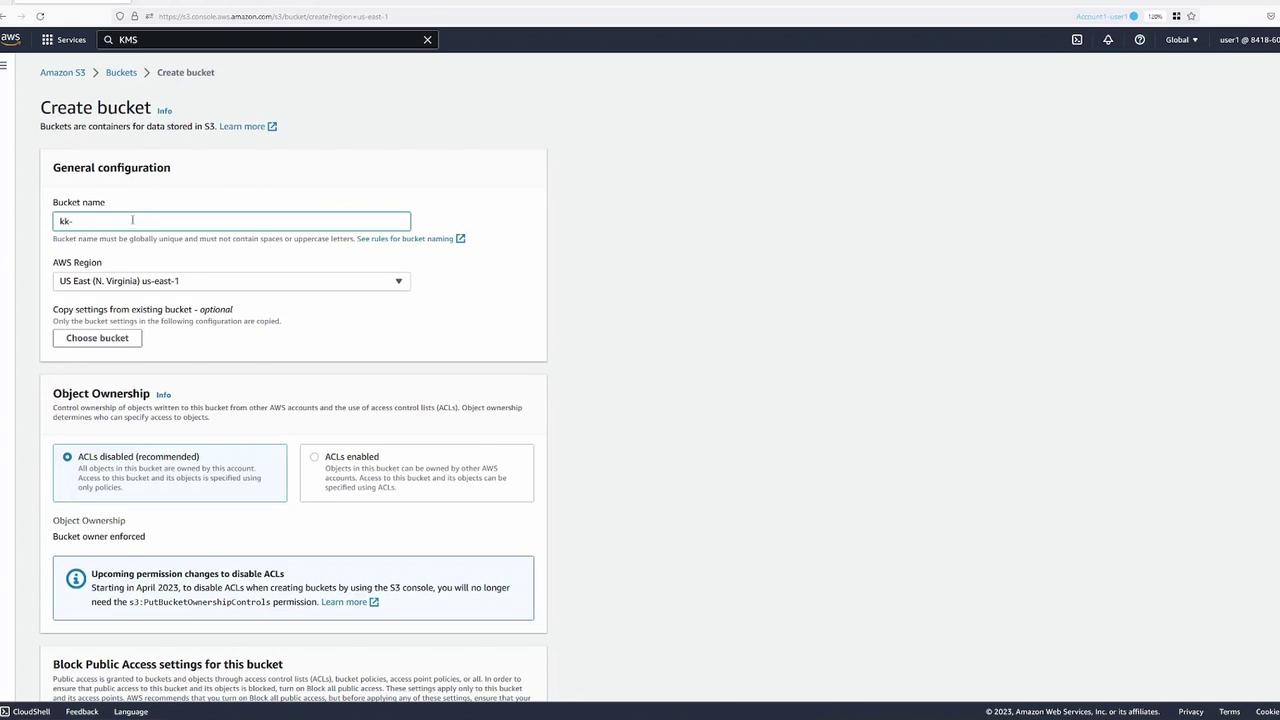
After the bucket is created, you will see a bucket similar to the one displayed below. Notice that both the bucket and its objects remain private.
Uploading an Object
Next, open your pre-signed demo bucket and upload an object. Authenticated users can view the object normally, but unauthenticated users will encounter an "Access Denied" error when trying to access it.
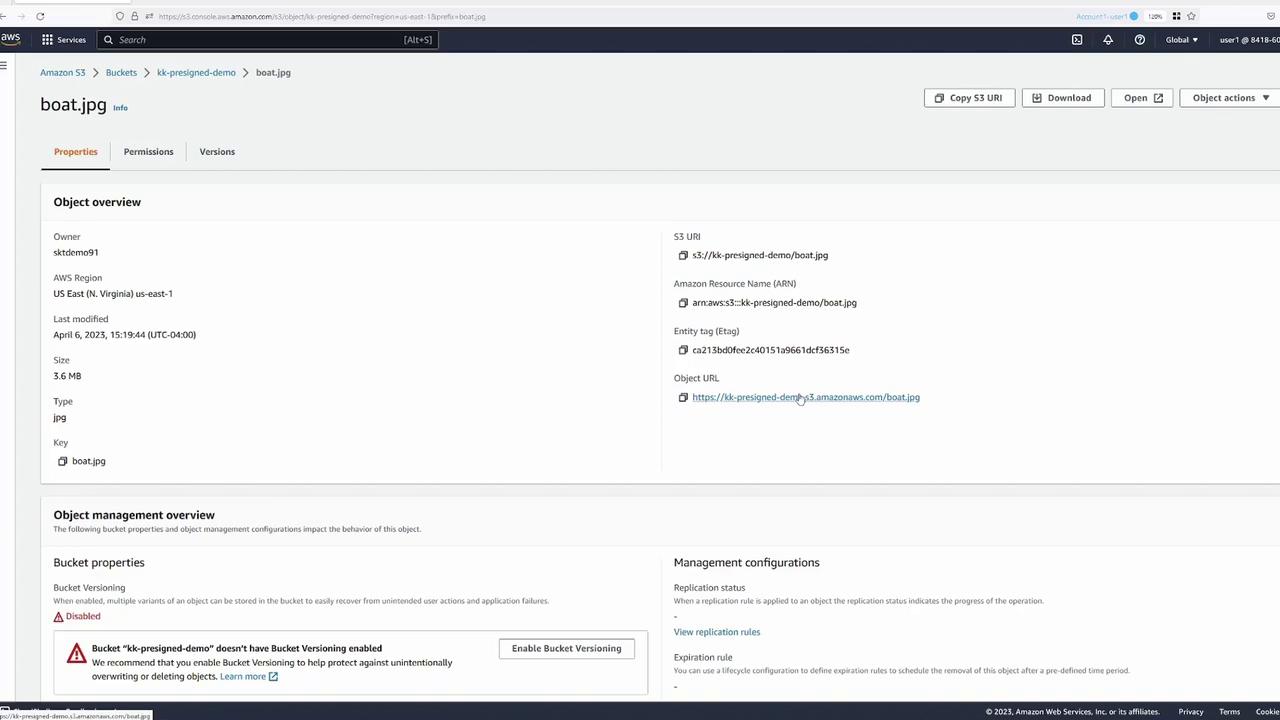
A quick review of the bucket permissions confirms that public access is blocked and no policies allow anonymous access.
Generating a Pre-Signed URL
Imagine you want to share this image with a friend who does not have an AWS account—without making the image publicly available. Pre-signed URLs serve this purpose perfectly. To generate one, follow these steps:
- Navigate to the object's details page and click "Share with a pre-signed URL."
- Specify the duration for which the URL will remain active (for example, 30 minutes).
- Generate the pre-signed URL, which will be copied to your clipboard. If it isn’t automatically copied, click the URL to copy it manually.
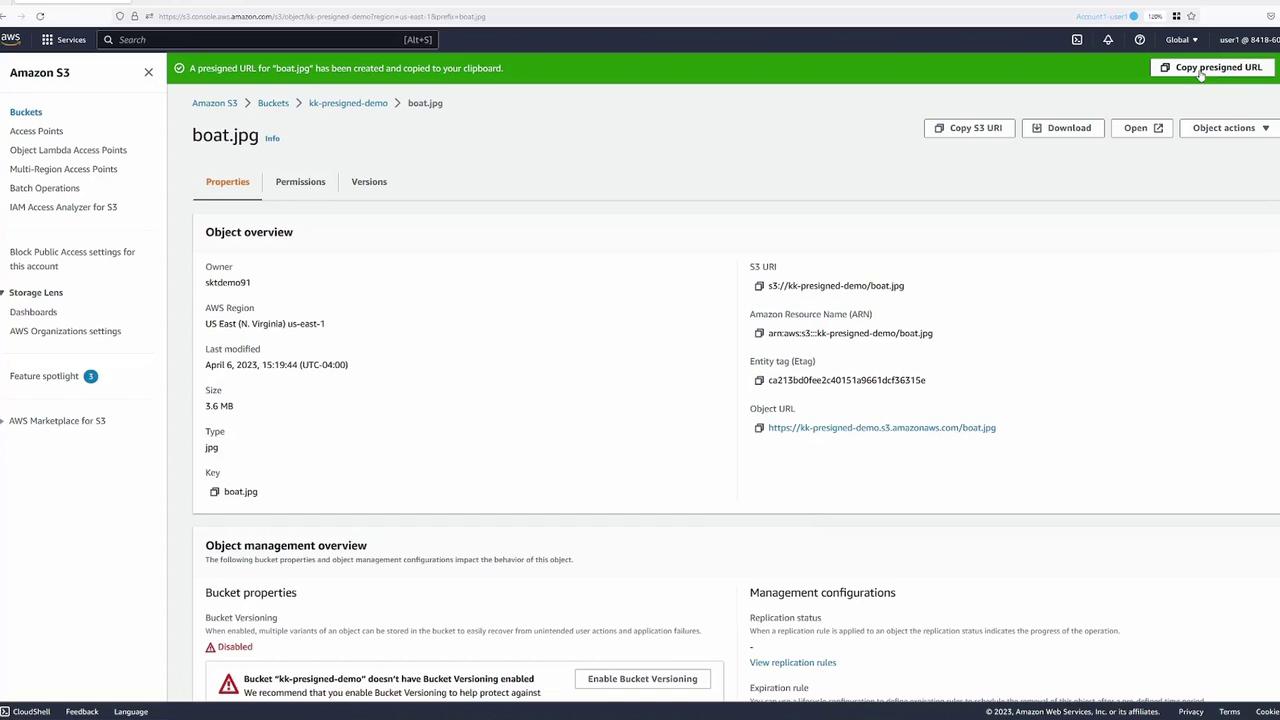
When accessed in your browser, the URL includes all necessary authentication data, allowing temporary access to the object for the specified period (30 minutes, in this case). Even though the URL can be used by anyone with the link during this timeframe, the object remains private for any access attempts outside the allowed window.
Programmatic URL Generation
While the AWS Console offers a simple method for generating pre-signed URLs, production environments typically generate them programmatically using the AWS SDK or AWS CLI.
Demonstrating User Permissions and URL Behavior
Next, let's explore the behavior of pre-signed URLs when generated by a user with limited permissions. Return to your original account and open the IAM console. Here, you will see another account named user2.
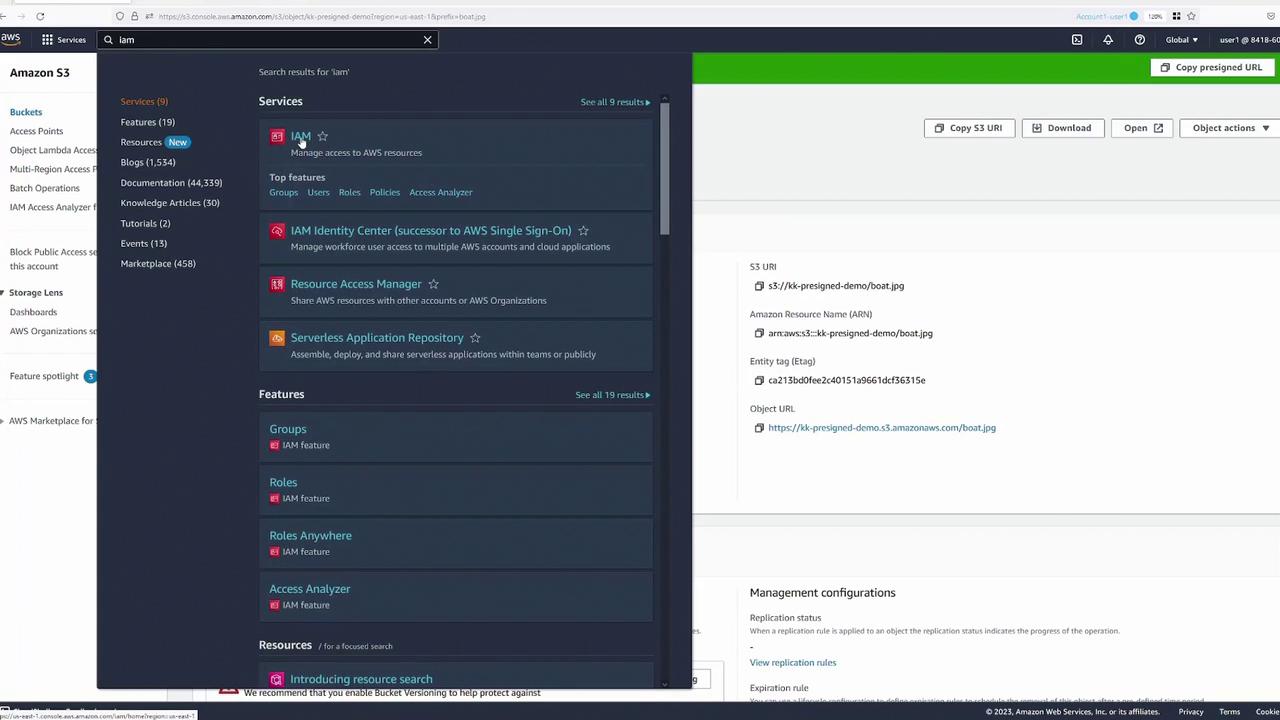
User2 has been granted a policy that allows bucket listing but restricts object retrieval and deletion. Below is the policy applied to user2:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:ListAllMyBuckets",
"s3:ListBucket"
],
"Resource": "*"
}
]
}
This policy permits user2 to list all buckets and enumerate the contents of the pre-signed demo bucket.
However, when user2 attempts to open an object, access is denied because the policy does not include the "s3:GetObject" permission.
Even with limited permissions, user2 can still generate a pre-signed URL for the object. If they share this URL, any public attempt to access the object will also result in an "Access Denied" error. This is because the pre-signed URL only operates under the permissions of the user who generated it. Since user2 lacks sufficient permission to retrieve the object, the URL cannot override this restriction.
Below is an example error response when attempting to access the object via a pre-signed URL generated by a user without the proper permissions:
<Error>
<Code>AccessDenied</Code>
<Message>Access Denied</Message>
<RequestId>348F7B3F19D916A7V</RequestId>
<HostId>AHmIbdweQpZyPcoVo2t5fMcp4jSywbWtlAkYdLXoADepHMfM1v1Zk9aCKBW0=</HostId>
</Error>
Important Security Note
Remember: A pre-signed URL does not grant additional privileges beyond those allowed by the generating user's IAM permissions.
Conclusion
Pre-signed URLs offer a secure and temporary method for granting access to private objects stored in Amazon S3. The essential point to remember is that the URL inherits the permissions of the user who created it. Even if the URL is shared publicly, it cannot bypass the underlying IAM permissions.
That’s all for this lesson on pre-signed URLs. For further details on AWS best practices and permissions, consider exploring additional Amazon S3 documentation.
Watch Video
Watch video content