AZ-400: Designing and Implementing Microsoft DevOps Solutions
Configuring and Managing Repositories
Recovering Data From Source Control Using Azure Repos
When working with Azure Repos, you can leverage the full power of Git along with a rich web interface to recover lost or deleted data. Whether you prefer command-line operations or a GUI, Azure DevOps provides the tools you need.
Prerequisites
Ensure you have a local clone of your Azure Repos repository and the latest Git version installed. You will also need sufficient permissions to push changes back to the remote.
1. Recovering with Git commands
All standard Git recovery commands work seamlessly with Azure Repos. Here are common scenarios:
| Recovery Task | Git Command | Description |
|---|---|---|
| Undo a specific commit | git revert <commit> | Creates a new commit that reverses the changes in <commit>. |
| Reset working directory | git reset --hard HEAD | Discards all uncommitted changes in your working tree. |
| Recover a deleted branch | git reflog → git branch <branch> <commit> | Locate the commit in reflog and recreate the branch. |
Example: Recover a deleted branch named feature-x
# Step 1: Identify the lost branch reference
git reflog
# Step 2: Recreate the branch at the desired commit (e.g., abc1234)
git branch feature-x abc1234
# Step 3: Push the restored branch to Azure Repos
git push origin feature-x
Force Push Risks
Avoid using git push --force on shared branches—it can overwrite history and disrupt other collaborators. Use --force-with-lease when you need safer history rewrites.
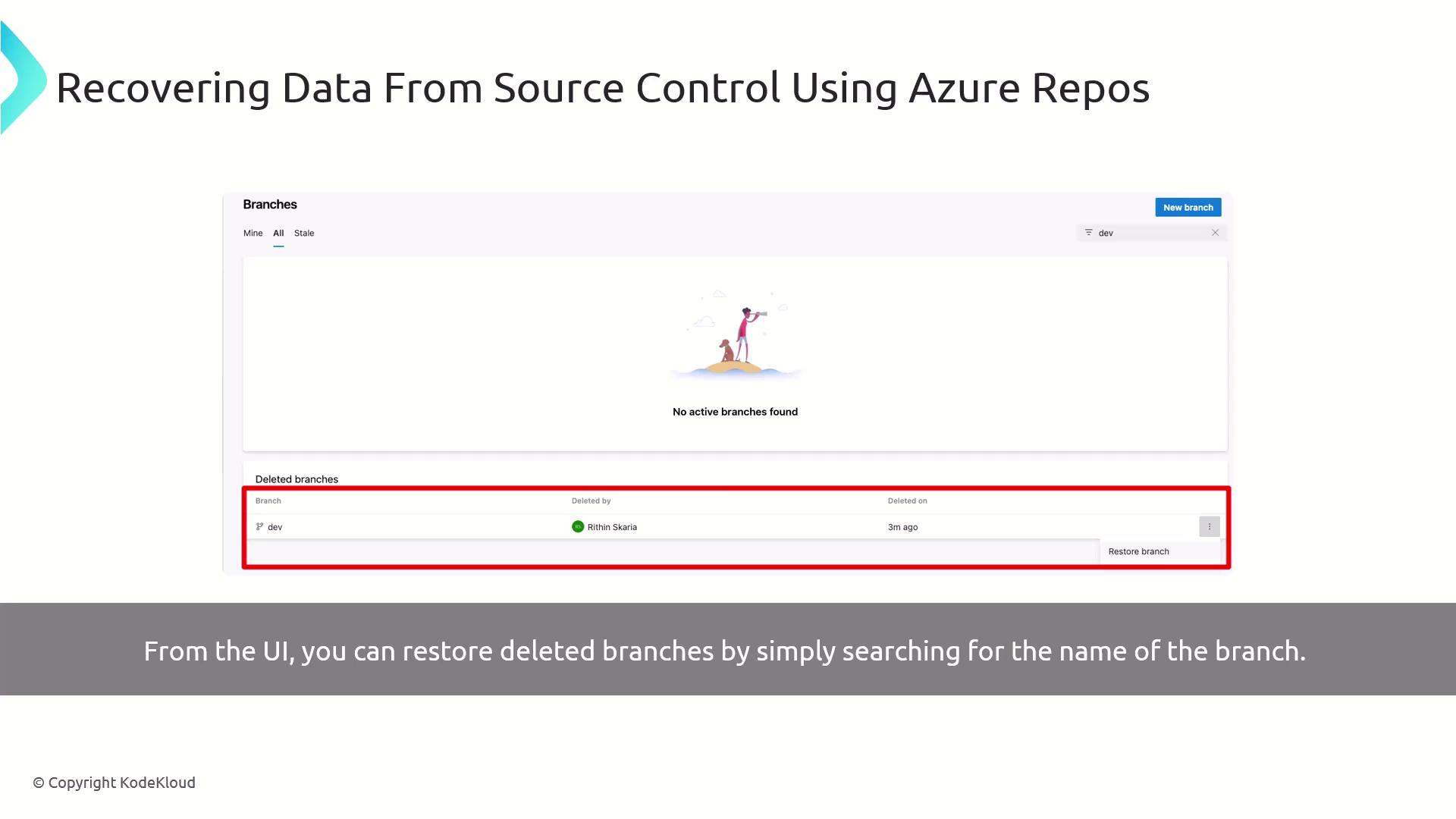
2. Restoring deleted branches in the Azure Repos UI
If you prefer a visual approach, Azure Repos provides a point-and-click interface to restore branches:
- In Azure DevOps, navigate to Repos > Branches.
- Toggle Show deleted branches in the filter bar.
- Search for the branch name (e.g.,
dev). - Click Restore next to the deleted branch.
No matter which method you choose—Git CLI or Azure Repos UI—you can quickly recover commits, branches, and deleted data with confidence.
Next, we’ll explore how to purge sensitive or unwanted data from your source control to meet security and compliance requirements.
References
Watch Video
Watch video content