AZ-400: Designing and Implementing Microsoft DevOps Solutions
Implement Security and Validate Code Bases for Compliance
Delving into Software Composition Analysis SCA
Software Composition Analysis (SCA) is a cornerstone of DevSecOps, enabling teams to inventory, track, and secure the open source and third-party libraries in your applications. Not only is SCA a critical domain for the AZ-400 exam, but it also helps you build resilient, compliant, and high-quality software that meets modern security standards.
Note
Incorporating SCA early in your workflow reduces risk by catching vulnerabilities before they reach production. Automate scans as part of your CI/CD pipelines for continuous protection.
Package Management Strategies
Maintaining control over the components in your software supply chain starts with a solid package management approach:
Single Source of Truth
Host all approved binaries in a central repository to ensure consistency across teams.Local Approval Repository
Curate an internal feed containing only vetted packages, giving you complete governance over dependencies.Azure Artifacts for Distribution
Use Azure Artifacts to store, share, and manage NuGet, npm, Maven, Gradle, Universal, and Python packages.
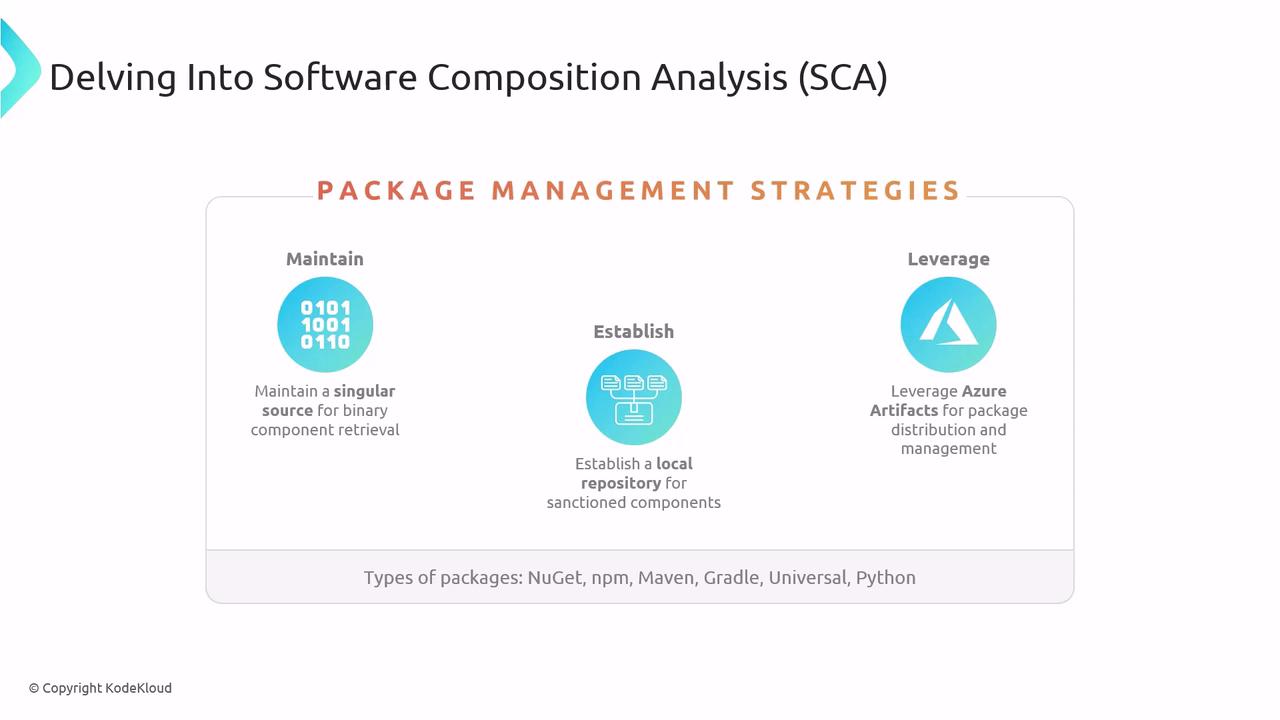
By combining a central repository with a curated internal feed and the flexible distribution model of Azure Artifacts, you can improve traceability, enforce policy, and speed up your release cycle.
Supported Package Types
| Package Type | Use Case |
|---|---|
| NuGet | .NET libraries and frameworks |
| npm | JavaScript modules for web and Node.js |
| Maven | Java and JVM-based artifacts |
| Gradle | Build automation for multi-language apps |
| Universal | Generic binaries and scripts |
| Python | Python packages and wheels |
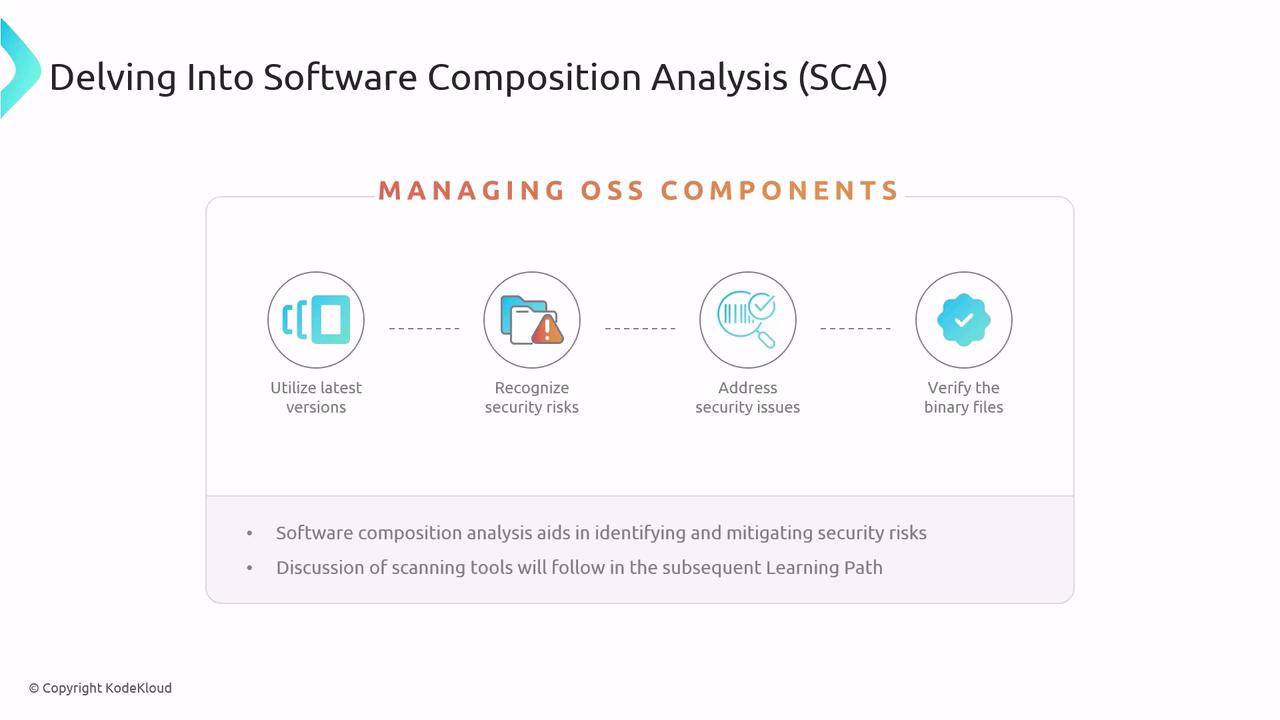
Managing Open-Source Software Components
Open-source libraries drive innovation but can introduce vulnerabilities if not managed properly. Adopt these best practices:
Keep Dependencies Updated
Upgrade to the latest stable releases to incorporate security patches and improvements.Map Transitive Dependencies
Analyze indirect dependencies to reveal hidden vulnerabilities.Verify Package Integrity
Use signatures or checksums to confirm that binaries have not been tampered with.
Warning
Delaying remediation of known vulnerabilities can expose your organization to breaches. Set up automated alerts and prioritize fixes based on risk severity.
SCA tools simplify this process by scanning your codebase, reporting issues, and offering actionable remediation steps. Integrate these scanners into your build and release pipelines to ensure continuous monitoring and protection.
Next Steps
To dive deeper into SCA implementation:
- Explore popular SCA tools like OWASP Dependency-Check and Snyk.
- Integrate SCA scans into Azure DevOps pipelines: Configuring SCA extensions.
- Review compliance frameworks: NIST SBOM guidelines.
Links and References
- Software Composition Analysis - Wikipedia
- AZ-400 Exam: Designing and Implementing Microsoft DevOps Solutions
- Azure Artifacts Documentation
Watch Video
Watch video content