AZ-400: Designing and Implementing Microsoft DevOps Solutions
Implement Security and Validate Code Bases for Compliance
Integrating Mend and GitHub Dependabot
Automating dependency management and security scanning is essential for modern software delivery. Integrating Mend with Azure Pipelines and activating GitHub Dependabot enables you to enforce security, quality, and compliance across your DevOps workflow.
1. Incorporating Mend into Azure Pipelines
Mend (formerly WhiteSource) is a robust extension in the Azure DevOps Marketplace that automates open-source component analysis. By embedding Mend into your pipeline, you ensure continuous security checks and policy enforcement.
1.1 Prerequisites & Installation
Note
You need Project Administrator permissions in Azure DevOps to install and configure extensions.
- Open the Azure DevOps Marketplace.
- Search for Mend and select the extension.
- Click Install and choose your Azure DevOps organization.
- Under Project settings ▶ Extensions, configure your Mend API token.
1.2 Key Features of Mend
| Feature | Description | Benefit |
|---|---|---|
| Continuous Detection | Scans all repositories for open-source components | Complete visibility of dependencies |
| Security Notifications | Sends alerts for new vulnerabilities in real time | Rapid triage and remediation |
| Automated Enforcement | Applies organizational policies and compliance rules automatically | Enforces standards without manual reviews |
By integrating Mend, your pipelines will block builds that violate security or license policies, ensuring that only compliant artifacts are deployed.
2. Activating GitHub Dependabot for Enhanced Security
GitHub Dependabot automates dependency version updates and vulnerability remediation in your repositories. It works seamlessly with GitHub Actions and supports multiple ecosystems (npm, Maven, Python, Docker, and more).
2.1 Enabling Dependabot
Create a
dependabot.ymlin the root of your repository (e.g.,.github/dependabot.yml).Define update intervals, package ecosystems, and target directories:
version: 2 updates: - package-ecosystem: "npm" directory: "/" schedule: interval: "daily"Commit and push the configuration. Dependabot will start scanning and raising pull requests.
Warning
Ensure you have branch protection rules enabled; Dependabot PRs must comply with your CI checks.
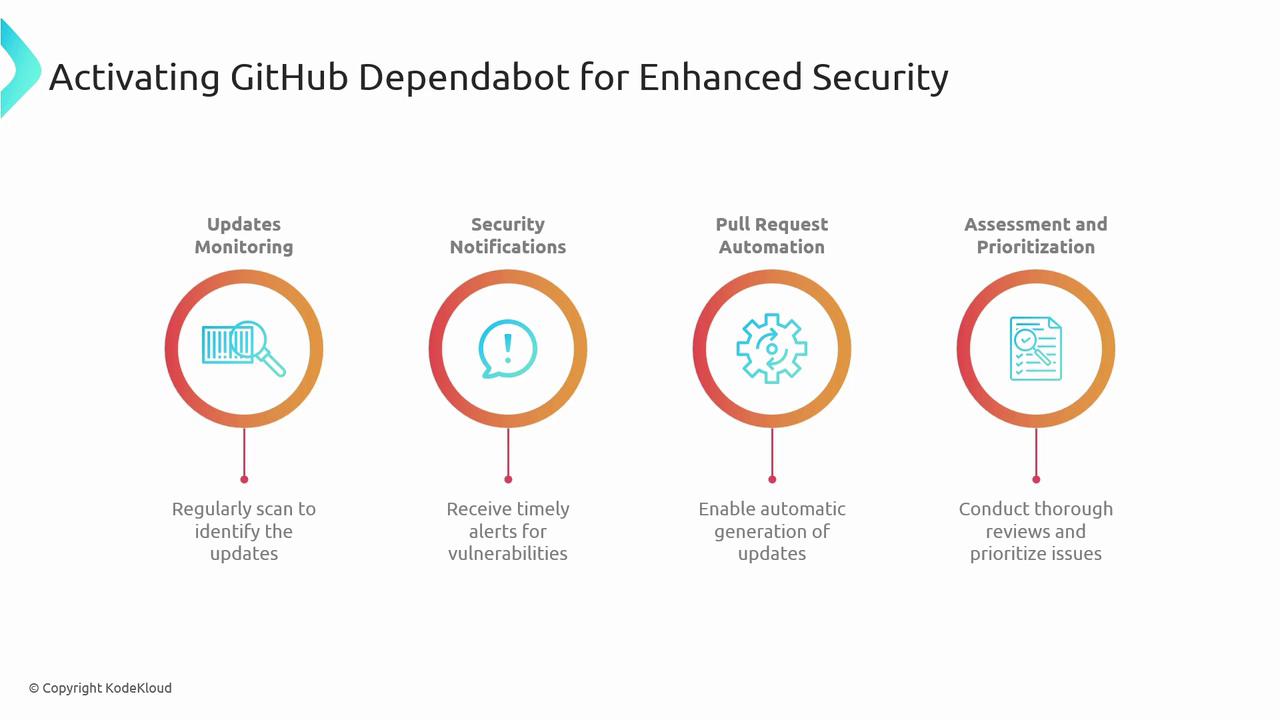
2.2 Core Benefits of Dependabot
| Feature | Description | Benefit |
|---|---|---|
| Updates Monitoring | Detects outdated dependencies and available security patches | Keeps libraries up to date |
| Security Notifications | Alerts when a vulnerability is found in your dependency graph | Immediate awareness of security risks |
| Pull Request Automation | Automatically generates PRs to update dependencies | Reduces manual maintenance overhead |
| Assessment & Prioritization | Reviews and ranks updates by severity and impact | Focuses efforts on high-risk upgrades first |
Conclusion
By combining Mend’s open-source security enforcement with GitHub Dependabot’s automated updates, you’ll achieve a fully automated DevSecOps pipeline. This proactive strategy helps you:
- Detect and remediate vulnerabilities early
- Enforce organizational policies without slowing development
- Maintain up-to-date dependencies with minimal manual effort
Links and References
- Azure DevOps Marketplace – Mend Extension
- Mend Documentation
- GitHub Dependabot
- DevSecOps Best Practices
Watch Video
Watch video content