Key Benefits
- Open-Source & Community-Driven: Backed by OWASP with regular updates.
- Extensible Add-Ons: Customize scans with community scripts and extensions.
- CI/CD Ready: Automate security checks in your pipeline for continuous feedback.
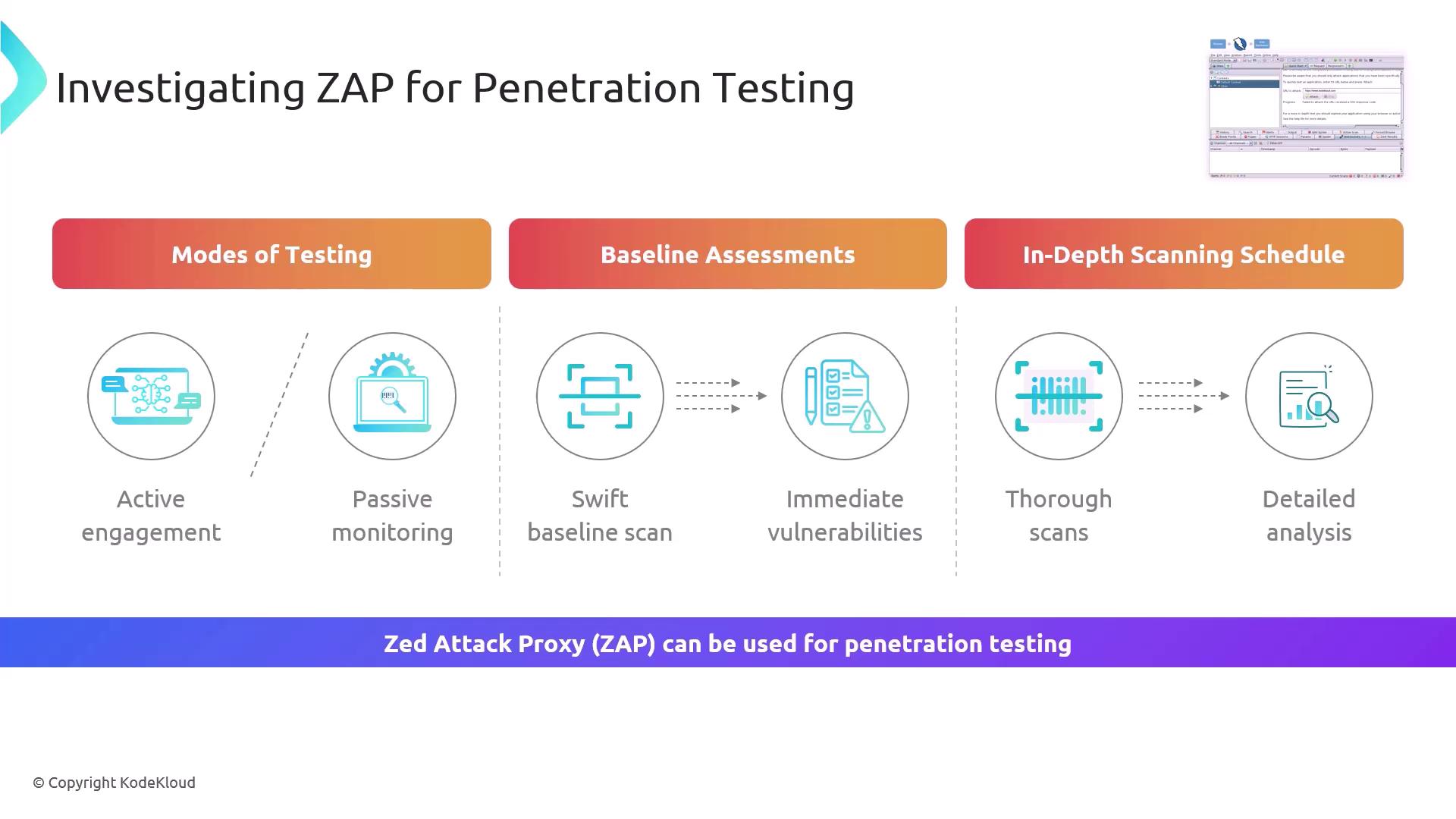
Testing Modes
| Scan Mode | Description | Ideal Use Case |
|---|---|---|
| Passive Scanning | Observes traffic without alteration, flags missing headers or insecure cookies | Ongoing development |
| Active Scanning | Injects payloads and probes responses to detect vulnerabilities automatically | Pre-release security testing |
Baseline vs. In-Depth Scans
| Scan Type | Scope | Duration | Use Case |
|---|---|---|---|
| Baseline Assessment | Quick, non-intrusive checks | Minutes | CI/CD pre-merge checks |
| In-Depth Analysis | Comprehensive, rule-based testing | Hours | Nightly or weekly audits |
Only perform active scans on applications you own or have explicit permission to test. Unauthorized scanning may violate legal or organizational policies.
By default, ZAP listens as a proxy on
http://127.0.0.1:8080. Configure your browser or API client to route traffic through ZAP for accurate results.Getting Started with ZAP CLI
Scan from the command line to integrate seamlessly with scripts and pipelines:Integrating ZAP into Your Workflow
- Automate baseline assessments on every build for immediate vulnerability feedback.
- Enable passive scanning during feature development to catch missing headers early.
- Schedule full active scans overnight for exhaustive coverage and historic tracking.