ubuntu-docker-jdk17-node20) and connect it as a Jenkins agent using JNLP.
Prerequisites
- A running Jenkins controller (installation guide)
- A VM with a matching JDK installed
- Network connectivity between controller and agent
1. Add a New Node in Jenkins
- On the Jenkins controller, go to Manage Jenkins → Manage Nodes and Clouds.
- Click New Node, enter a name (e.g.,
Ubuntu-Agent), select Permanent Agent, and OK.
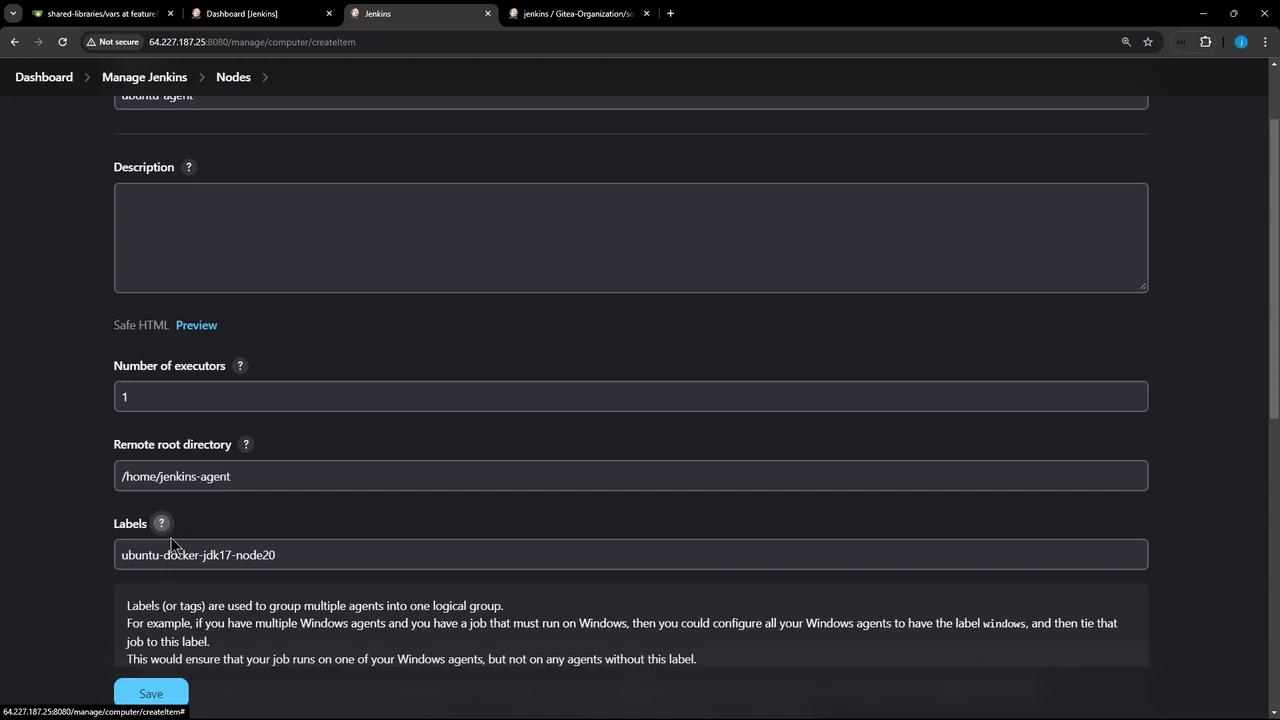
- Fill in the node configuration:
| Field | Purpose | Example |
|---|---|---|
| Description | Brief summary of this agent’s role | Ubuntu build executor |
| # of Executors | Max concurrent builds this agent can run | 2 |
| Remote Root Directory | Directory on the agent for workspaces, logs, and artifacts | /home/jenkins-agent |
| Labels | Tags for targeting in jobs or pipelines | docker jdk17 ubuntu |
| Usage | Restrict builds to labels matching this node | Only build jobs with label expressions matching this node |
| Launch method | How the agent connects (e.g., JNLP) | Launch agent by connecting from the controller |
| Availability | Agent online policy | Keep this agent online as much as possible |
Under Node Properties, you can add environment variables or enable disk space monitoring to maintain agent health.
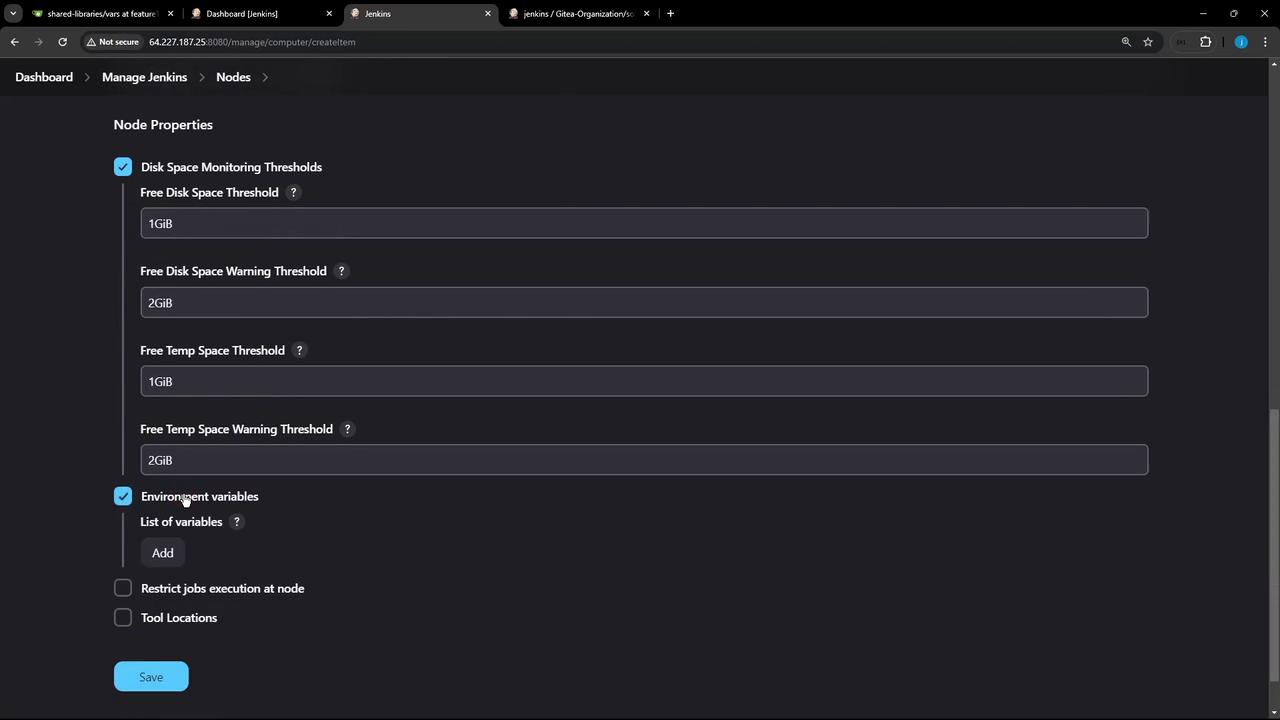
- Click Save. The agent remains offline until it connects to the controller.
2. Enable TCP Inbound Agent Port
- Navigate to Manage Jenkins → Configure Global Security.
- Under Agents → TCP port for inbound agents, select Fixed or Random.
- Click Save.
3. Connect the Agent from the Command Line
On the agent VM (ubuntu-docker-jdk17-node20):
Keep the
secret-file secure. Exposing the JNLP secret allows unauthorized agents to connect.4. Verify the Agent in Jenkins
Return to Manage Nodes and Clouds and confirmUbuntu-Agent is online:
5. Inspect the Agent Workspace
On the agent VM:workspaces, logs, and artifacts directories under /home/jenkins-agent.
Next, we’ll run a sample job on this agent to demonstrate distributed execution.