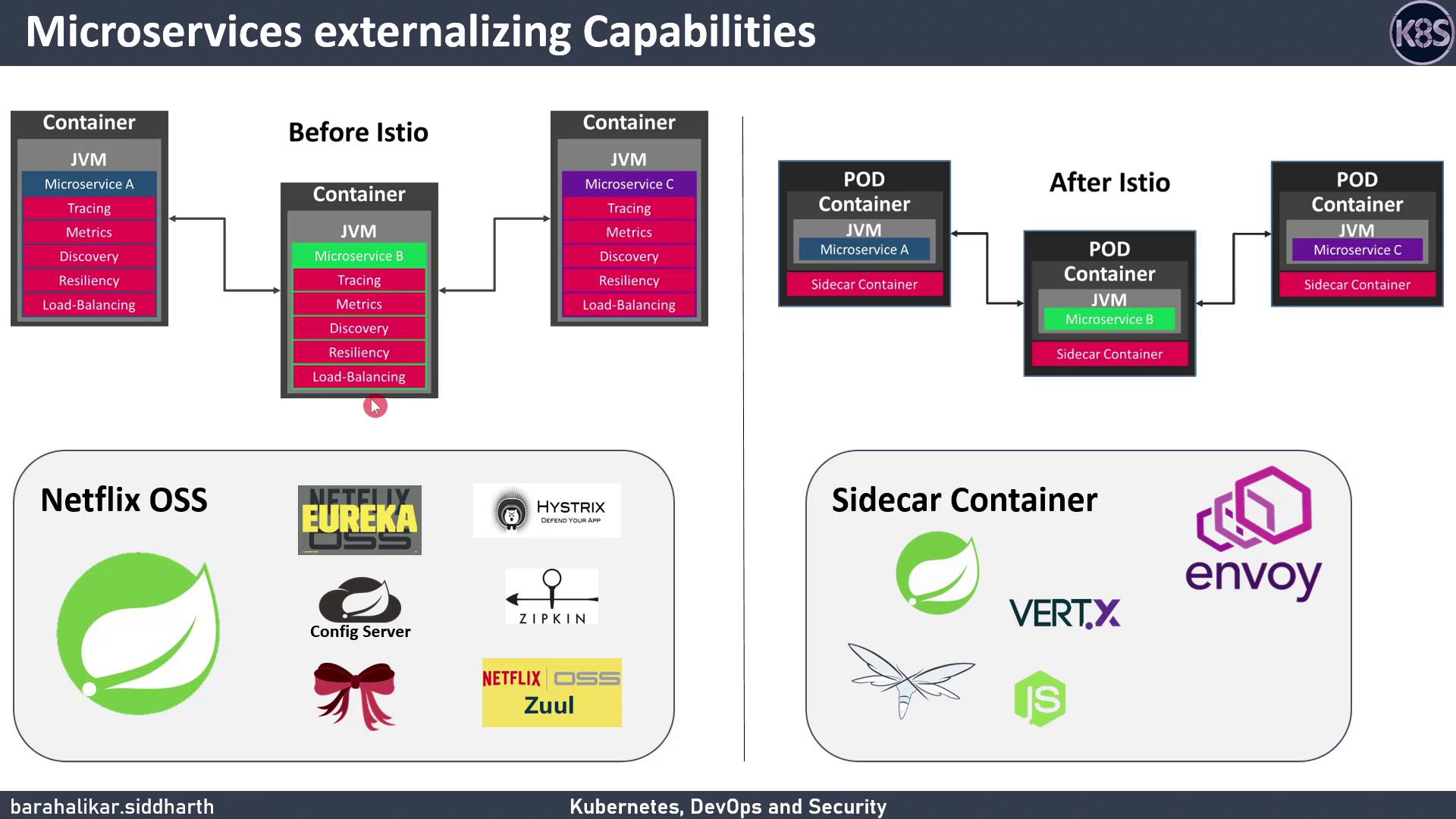
- Automated service discovery, load balancing, and failure recovery
- Fine-grained traffic control for A/B testing, canary releases, and rate limiting
- End-to-end security with mutual TLS, policy enforcement, and telemetry
- Zero or minimal changes to application code
Istio works transparently alongside any application stack (Spring Boot, Node.js, Vert.x, etc.) by injecting an Envoy sidecar proxy into each pod.

Architecture Overview
Istio’s design is split into two planes:- Data Plane
Consists of Envoy sidecar proxies that run next to application containers. They intercept all inbound/outbound traffic, enabling metrics collection, policy enforcement, and traffic routing. - Control Plane
Configures and manages the proxies, distributing routing rules, certificates, and configuration to ensure consistent behavior across the mesh.
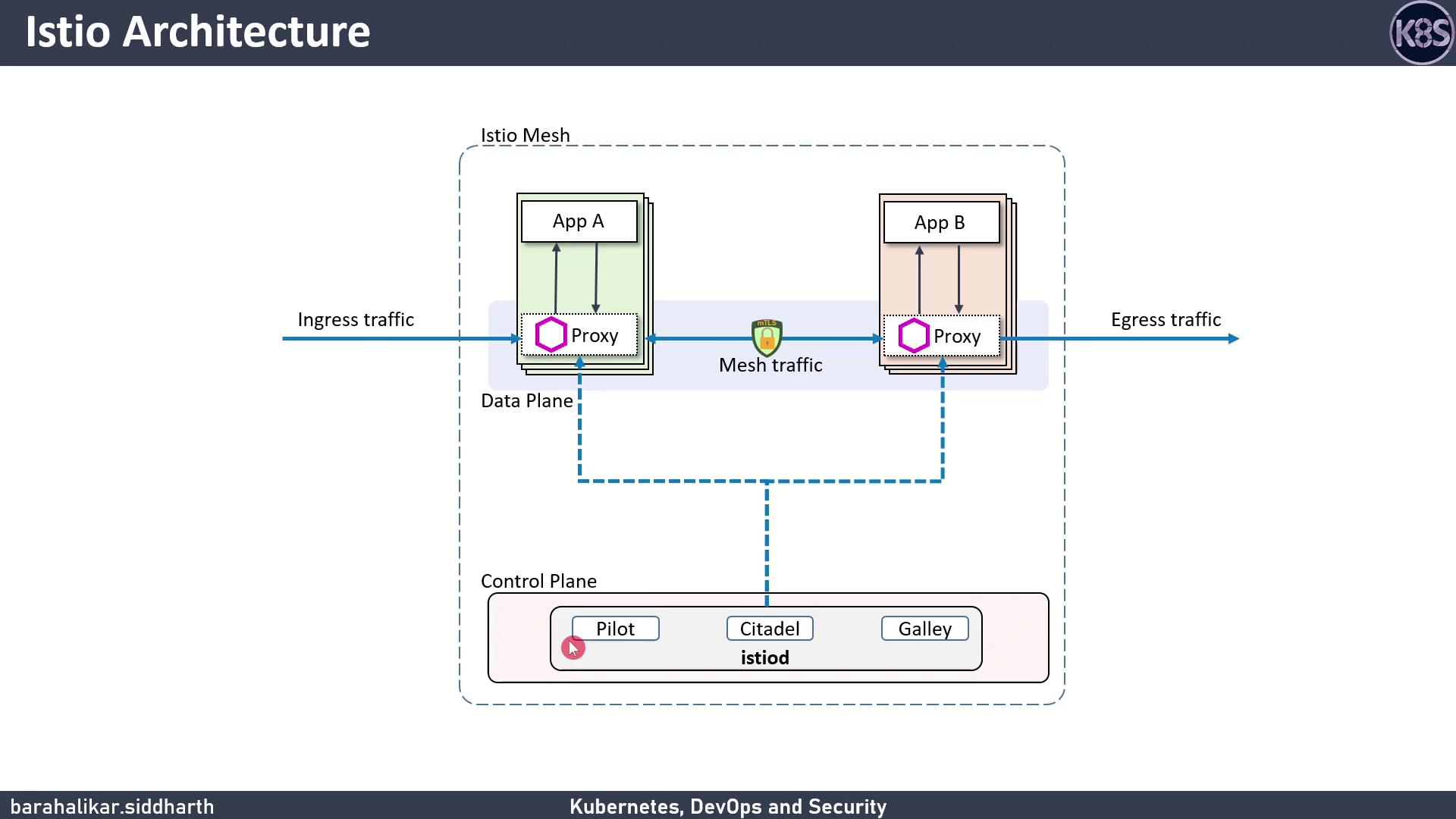
Control Plane Components
| Component | Responsibility | Reference |
|---|---|---|
| Pilot | Service discovery, traffic management & routing | Pilot Docs |
| Citadel | mTLS-based authentication & certificate issuance | Citadel Docs |
| Galley | Configuration ingestion, validation & distribution | Galley Docs |
In Istio 1.5+, Galley and Pilot components were merged into
istiod. Be sure to check your Istio version and configuration model.Sidecar Proxy Pattern
When you deploy Istio, each application pod includes an Envoy sidecar. The sidecar:- Intercepts all network traffic to/from the application
- Forwards requests to the application container and relays responses
- Encrypts traffic between pods using mutual TLS
From Netflix OSS to Istio
Before Istio, Spring Boot microservices often required embedding multiple Netflix OSS libraries:| Netflix OSS Component | Use Case | Istio Equivalent |
|---|---|---|
| Eureka | Service discovery | Envoy + Pilot |
| Spring Cloud Config Server | Centralized configuration | Galley / Config APIs |
| Ribbon | Client-side load balancing | Envoy load-balancer |
| Hystrix | Circuit breaking & resilience | Envoy retry & circuit-breakers |
| Zipkin | Distributed tracing | Envoy + Zipkin/Jaeger plugin |
| Zuul | API gateway | IngressGateway |