DevSecOps - Kubernetes DevOps & Security
Kubernetes Operations and Security
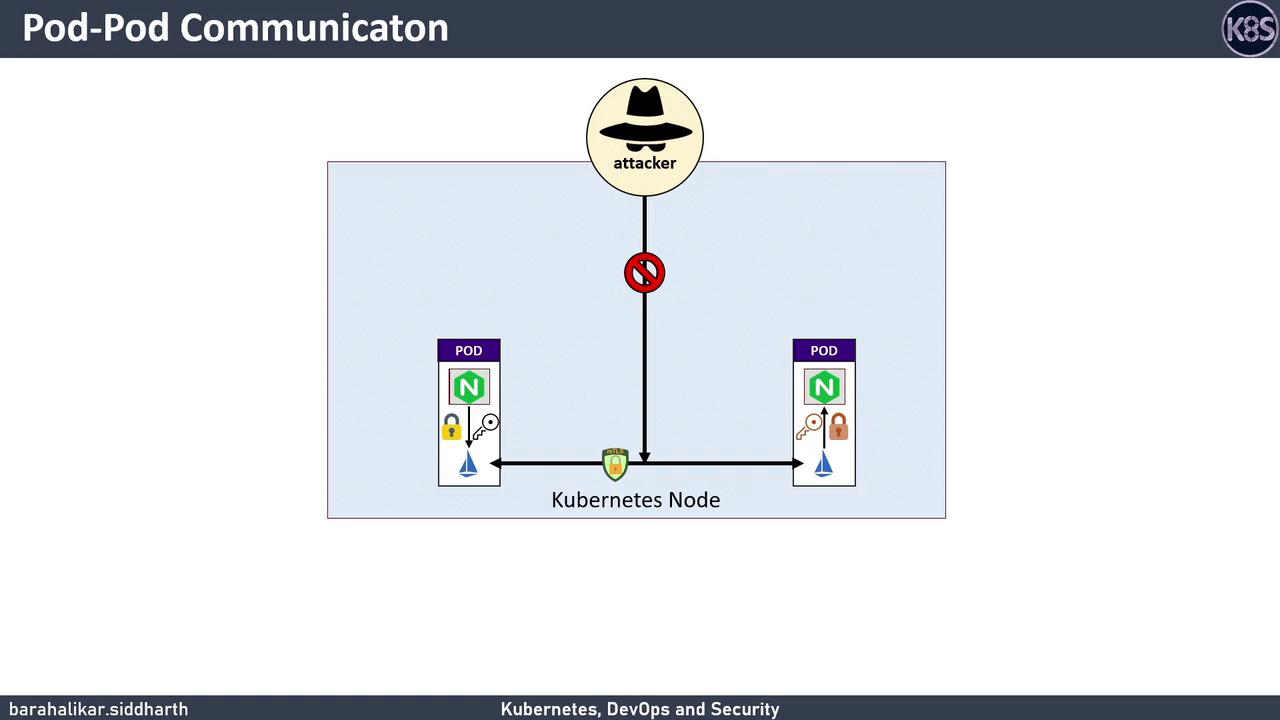
Pod Pod Communication Need for mTLS
Securing communication between pods is critical in a microservices architecture. By default, Kubernetes routes traffic in plaintext, exposing sensitive data to network eavesdroppers. This guide explains the risks of unencrypted pod-to-pod traffic and shows how a service mesh—specifically Istio—simplifies end-to-end encryption using mutual TLS (mTLS).
Table of Contents
- 1. The Risk of Plaintext Pod-to-Pod Traffic
- 2. Challenges of Embedding TLS in Applications
- 3. Service Mesh Solution: Istio and mTLS
- 4. Comparing Approaches
- 5. Next Steps and References
1. The Risk of Plaintext Pod-to-Pod Traffic
By default, Pod A sends HTTP requests directly to Pod B over the cluster network. An attacker on the same node—or any compromised network segment—can intercept and read this traffic.
Pod A (HTTP) ───► Pod B (HTTP)
Warning
Plaintext HTTP between pods exposes API keys, tokens, and PII to packet sniffers. Always encrypt inter-service traffic in production.
2. Challenges of Embedding TLS in Applications
To secure traffic with TLS (HTTPS), every microservice must handle:
- Generating and rotating key pairs
- Securely storing private keys
- Performing TLS handshakes
- Updating certificates upon expiry
This creates significant operational complexity and duplicates effort across teams.
3. Service Mesh Solution: Istio and mTLS
A service mesh like Istio offloads TLS responsibilities to sidecar proxies, automating certificate issuance and mTLS handshakes.
Prerequisites
Note
Ensure you have:
- A running Kubernetes cluster (v1.20+)
kubectlconfigured for your cluster- Helm (optional) or
istioctlCLI installed
Step-by-Step Guide
Install Istio
istioctl install --set profile=demo -yEnable Automatic Sidecar Injection
kubectl label namespace default istio-injection=enabledDeploy Your Applications
Any pod in thedefaultnamespace now includes an Istio sidecar.Verify mTLS is Enforced
istioctl authn tls-check
When Pod A calls Pod B:
- Pod A’s app → plaintext to Envoy sidecar
- Envoy (Pod A) → performs mTLS handshake → Envoy (Pod B)
- Envoy (Pod B) → decrypts → plaintext to Pod B’s app
4. Comparing Approaches
| Approach | TLS Management | Complexity | Encryption Type |
|---|---|---|---|
| Manual TLS in Service | Developer | High | HTTPS |
| Istio Service Mesh | Sidecar Proxies (Envoy) | Low | mTLS |
5. Next Steps and References
We’ll dive deeper into advanced Istio features—custom mTLS policies, certificate rotation, and traffic observability.
Links and References
Watch Video
Watch video content