AWS Solutions Architect Associate Certification
Designing for Security
AWS Shared Responsibility Model
Welcome back, future AWS architects. In this article, we revisit the AWS Shared Responsibility Model—a critical framework that outlines the security responsibilities shared between AWS and its customers. Understanding this model is essential as it forms the foundation of security, resiliency, and compliance best practices in the cloud.
The model clearly delineates roles. Responsibilities below the "hardware line" (e.g., compute, storage, databases, and networking components housed in AWS data centers) are managed entirely by AWS. In other words, if a component is part of the underlying infrastructure that you cannot access or configure, AWS is responsible for securing it.
On the other hand, anything above that line falls under customer control. For instance, if you have the ability to log into and configure a compute instance or storage service, you are accountable for patching, managing, and securing these elements. This division of responsibilities evolves depending on the type of service:
- Infrastructure as a Service (IaaS): Customers maintain significant control and responsibility.
- Platform as a Service (PaaS): AWS manages a larger portion of the security, reducing customer responsibility.
- Software as a Service (SaaS): AWS handles almost everything, leaving customers with minimal security responsibilities.
AWS recommends using managed services whenever possible to offload the operational burden, allowing your team to focus on higher-level tasks.
Below is a diagram that illustrates the division of responsibilities across various service types:
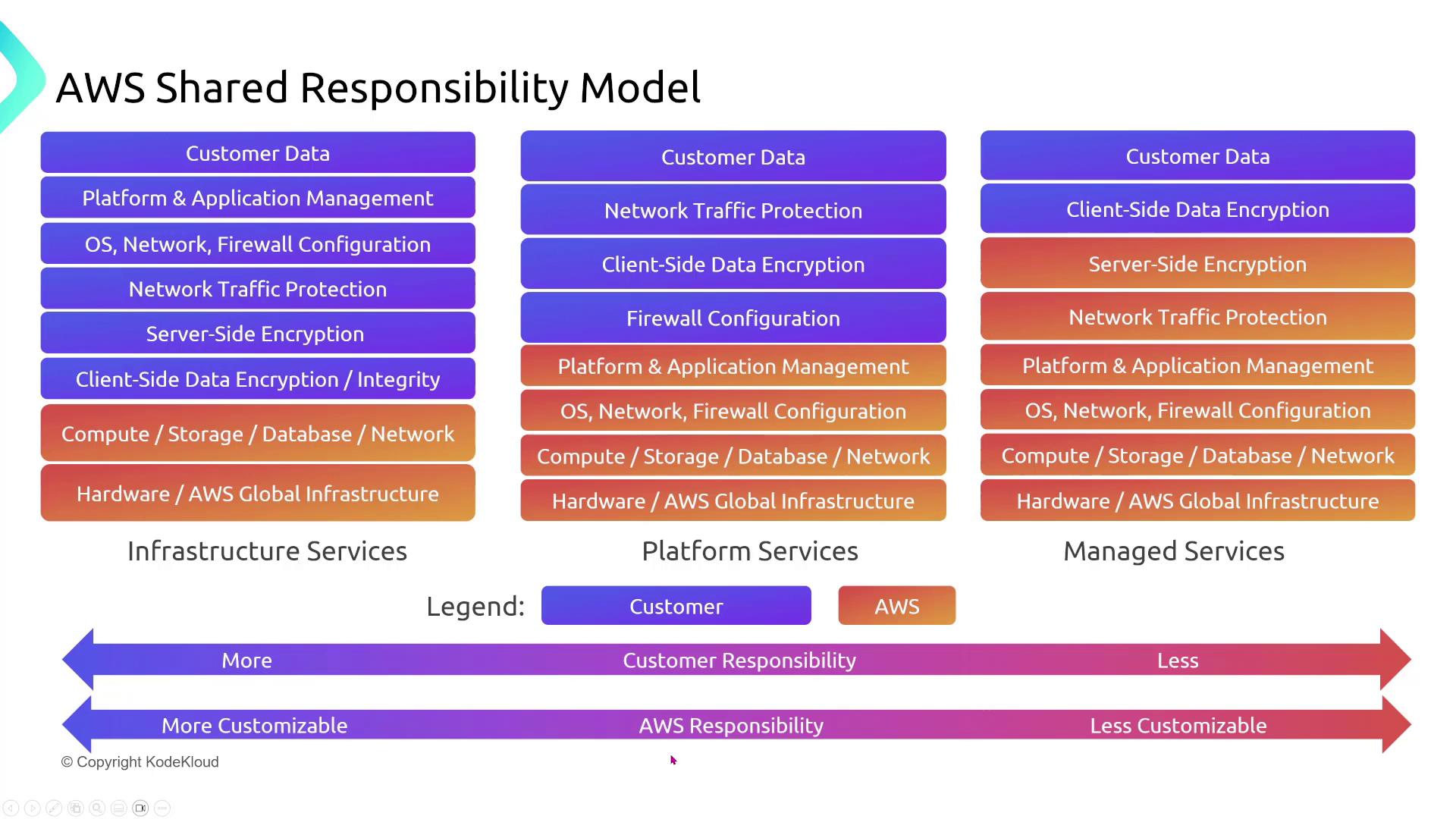
In this diagram, you can see that with infrastructure services such as Amazon Elastic Compute Cloud (EC2), you are responsible for managing compute, storage, databases, and networking. Imagine an additional block representing data centers—this block would give you more direct control over your network security. Conversely, services like serverless computing offer very little control over the underlying infrastructure since AWS fully manages those environments.
As you move from IaaS to Platform as a Service (PaaS) and finally to Software as a Service (SaaS), the customer's security responsibilities continue to diminish. For example:
- With AWS RDS (a PaaS offering), AWS handles most of the underlying management.
- With SaaS offerings like Amazon Simple Storage Service (Amazon S3), DynamoDB, SNS, and SQS, your interaction is largely limited to an API, and you have virtually no insight into the servers or infrastructure details.
Take a look at the following diagram for further clarity on how these responsibilities shift between AWS and the customer:
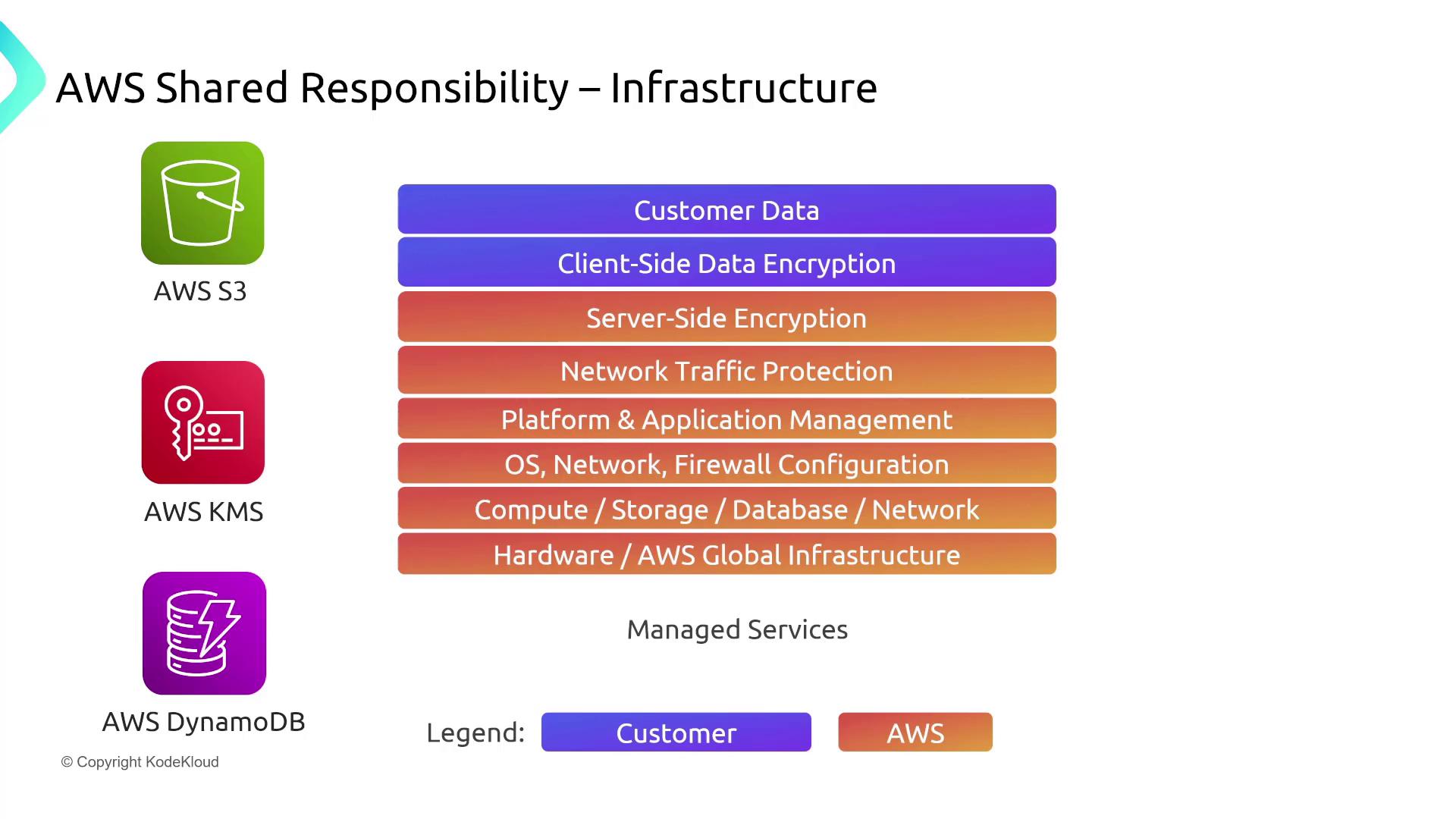
Key Takeaways
- If you can access, configure, or manage a component, you are responsible for its security.
- If you cannot access or configure a component, AWS assumes responsibility for its security.
- IaaS places the most responsibility on the customer, while PaaS and SaaS shift more responsibility to AWS.
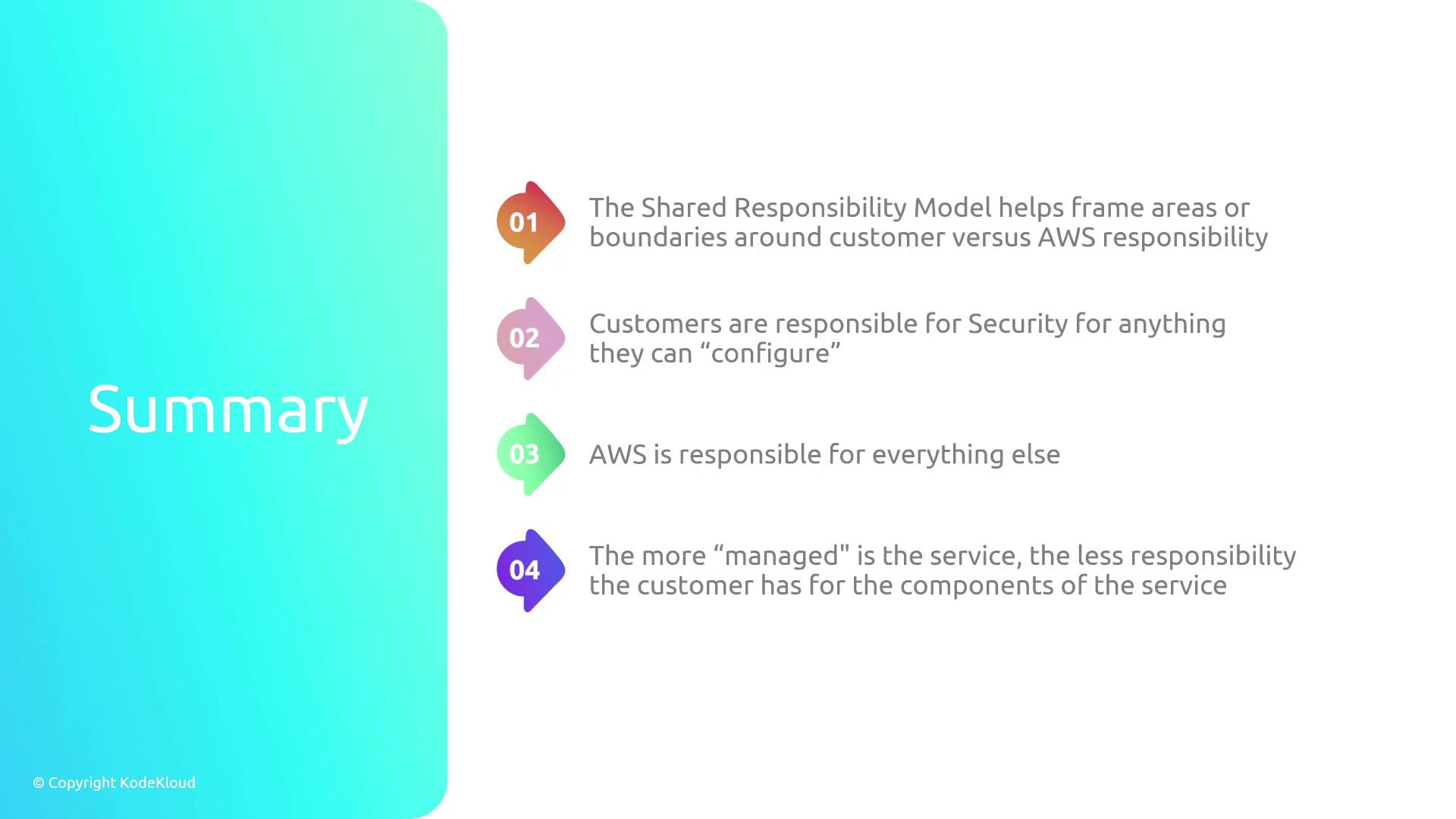
This model acts as a filtering mechanism to help you identify which aspects of security management require your attention and which can be entrusted to AWS. Customers agree to these defined responsibilities when setting up an AWS account, bearing the duty to secure what they control while relying on AWS to secure everything else. As services become more managed, your overall security responsibilities decrease correspondingly.
For additional documentation on AWS security, compliance details, or audit attestations, visit AWS Artifact. AWS Artifact provides a repository of certifications, attestations, and compliance documents that are especially useful during compliance audits.
If you have any questions or need further clarification, feel free to reach out via KodeKloud.com, join our Slack community, or participate in our forums.
Watch Video
Watch video content