AWS Solutions Architect Associate Certification
Designing for Security
Agenda and Introduction for Designing for Security
Welcome back, Future Solutions Architects. I’m Michael Forrester, and in this lesson we dive deep into designing for security—also known as the "Citadel of Security." In this session, we will cover AWS-recommended design principles, explore the four foundations of cybersecurity, and review the AWS Shared Responsibility Model. This practical guide is aligned with the AWS Solutions Architect Associate Certification.
After the cost optimization module, your first design challenge will focus on security. The course format includes diagrams, analytical questions, and in-depth answers, so be sure to take thorough notes to reinforce your learning.
Below is the agenda diagram for the security design section:
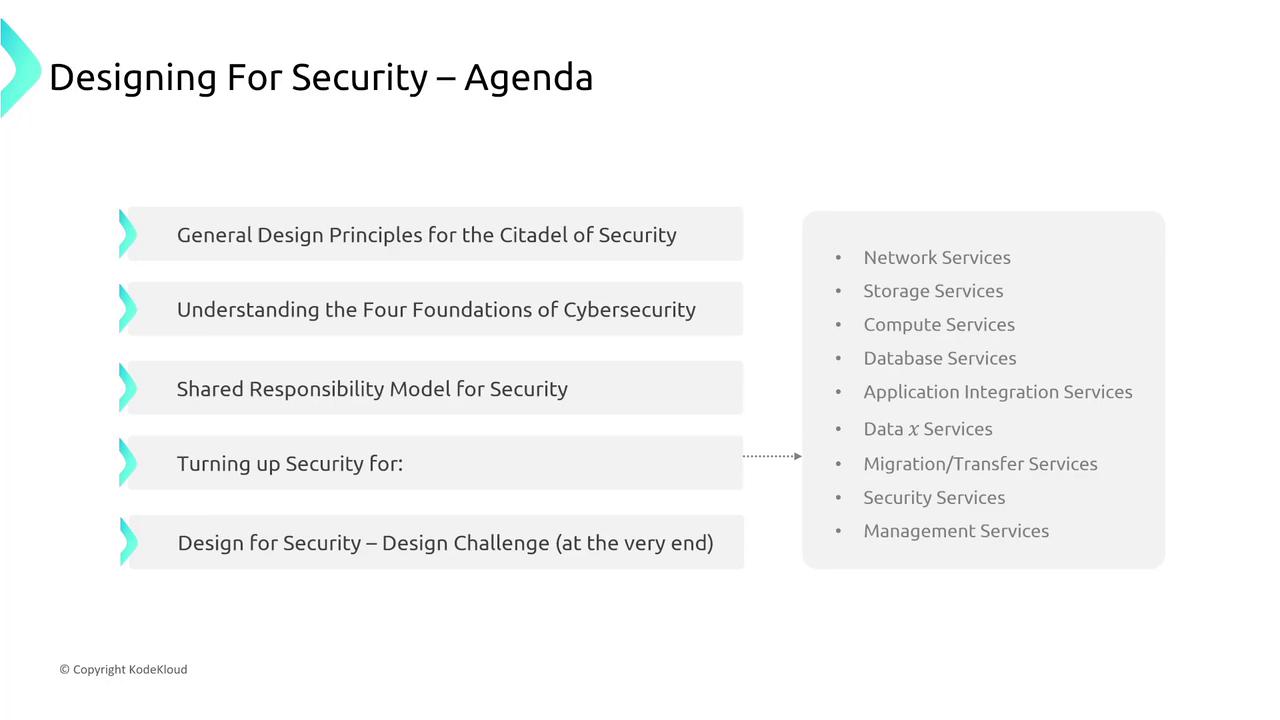
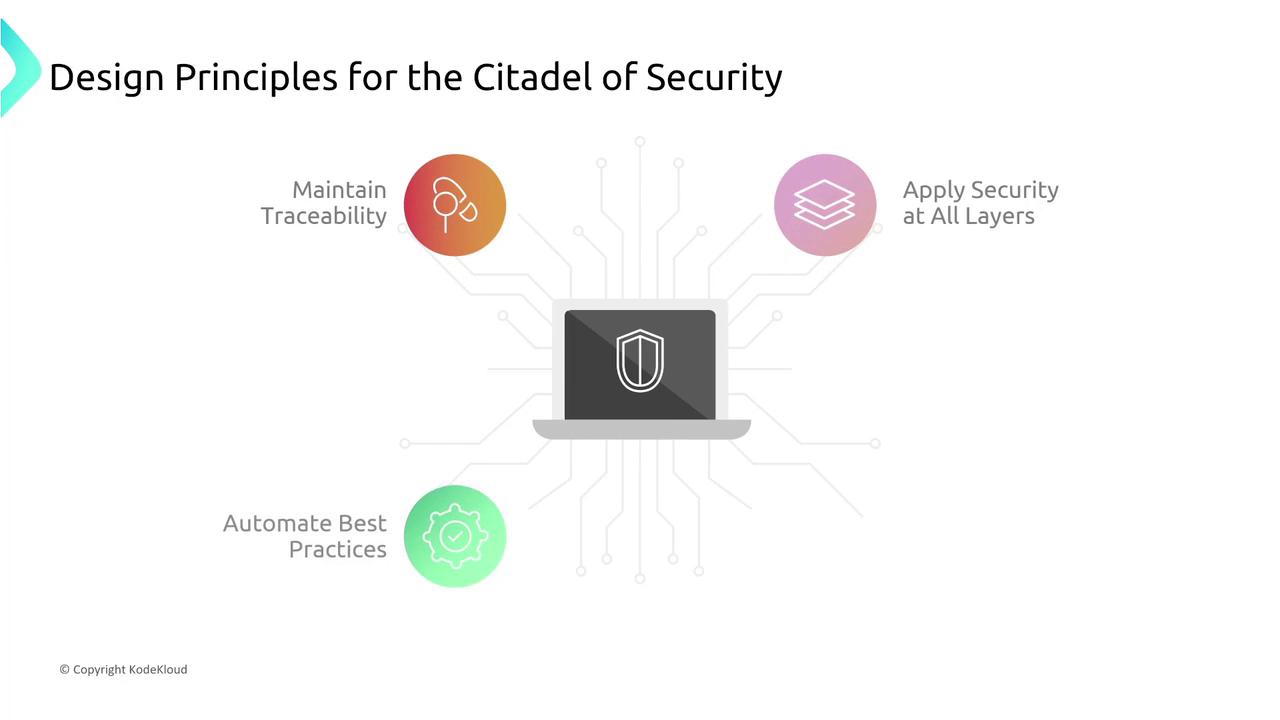
Section 1: Design Principles
In this section, we introduce the key design principles that form the backbone of the Citadel of Security. The topics include:
- Maintaining Traceability
- Applying Security at All Layers
- Automating Best Practices
These foundational concepts set the stage for the more detailed discussions that follow.
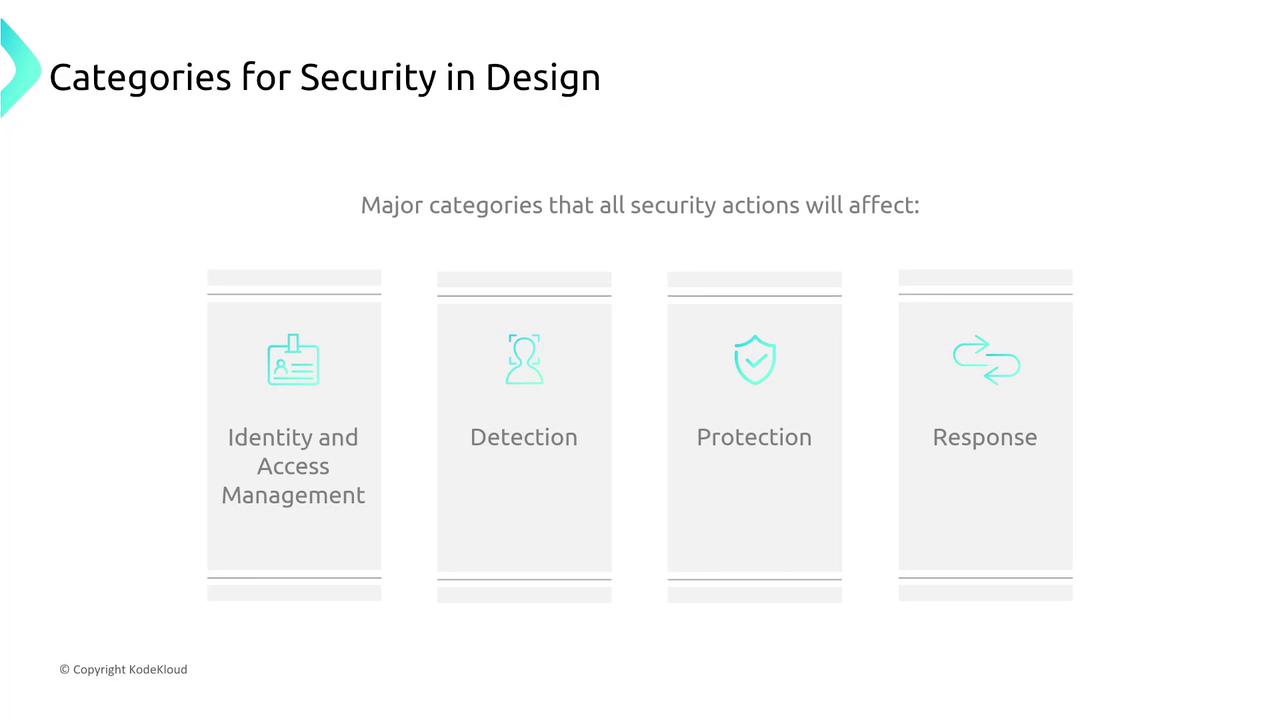
Section 2: Categories for Security in Design
This section defines the four fundamental categories that govern all security actions in AWS:
- Identity and Access Management (IAM): Controlling and managing access.
- Detection: Identifying issues as soon as they occur.
- Protection: Defending against potential threats.
- Response: Taking corrective action to resolve issues.
Understanding these categories helps pinpoint the focus areas for enhancing security within AWS.
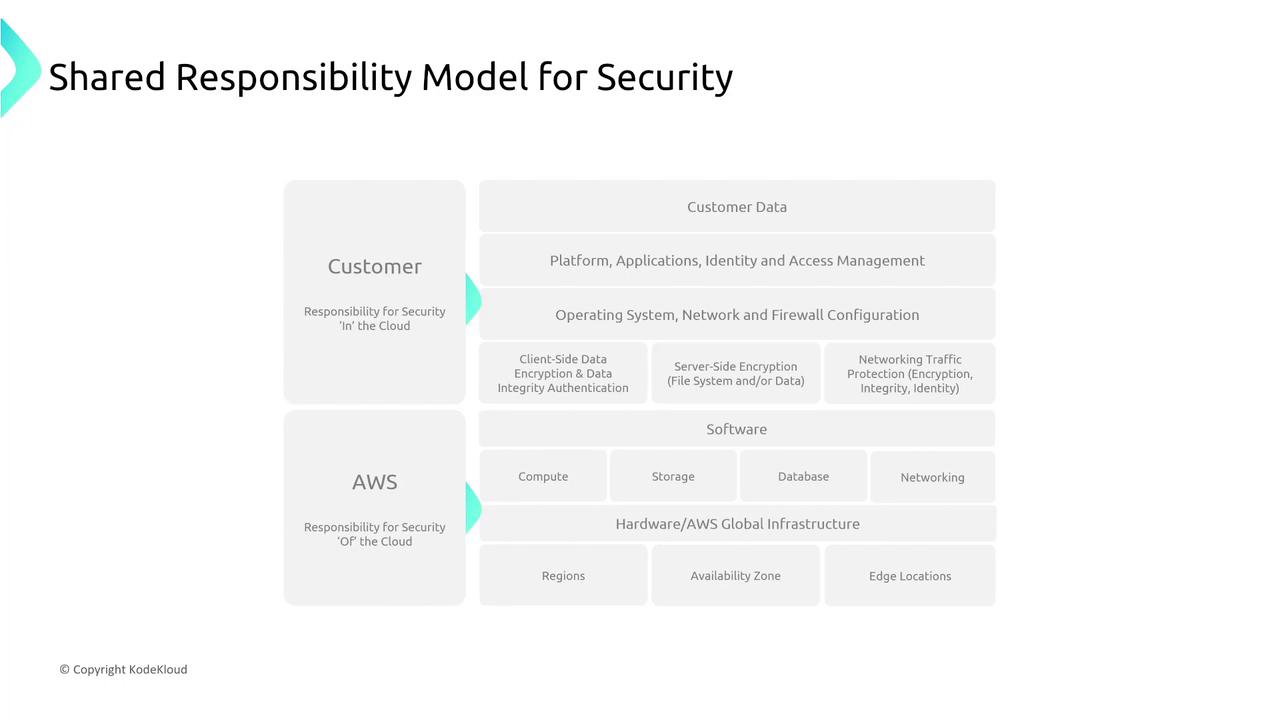
Section 3: The Shared Responsibility Model
Next, we explore the AWS Shared Responsibility Model, which clearly delineates security responsibilities between the customer and AWS. Key points include:
- Customer Responsibilities (Security “in” the Cloud): Tasks that customers must handle, such as data protection and access management.
- AWS Responsibilities (Security “of” the Cloud): AWS covers the security of the underlying infrastructure.
We will also review new services and their specific responsibilities within this model.
Sections 4 to 12: Enhancing Security Across Services
In these sections, we delve into security specifics for various AWS service categories including network, compute, storage, management, data, and machine learning. Topics include:
- Adjusting security on management and compute services.
- Enhancing network and storage security.
- Exploring available configuration options ("knobs") for each AWS service.
A detailed diagram below illustrates these layers and highlights opportunities for fine-tuning security settings.
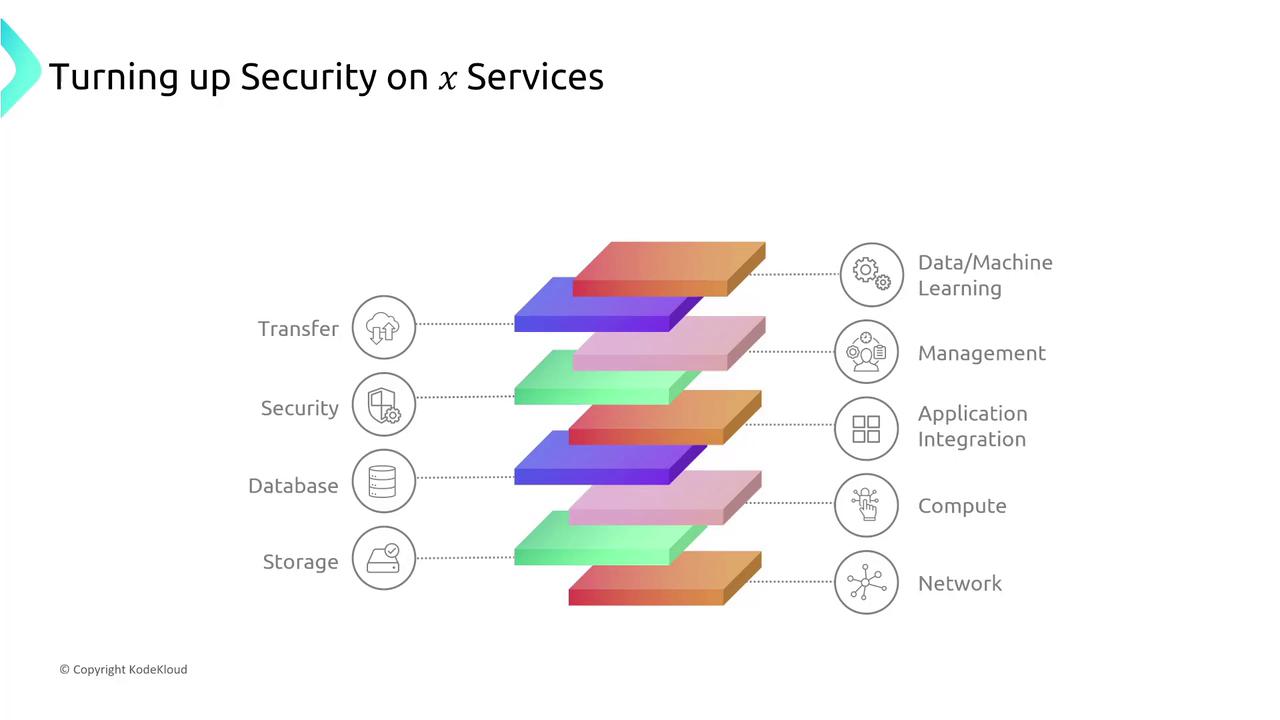
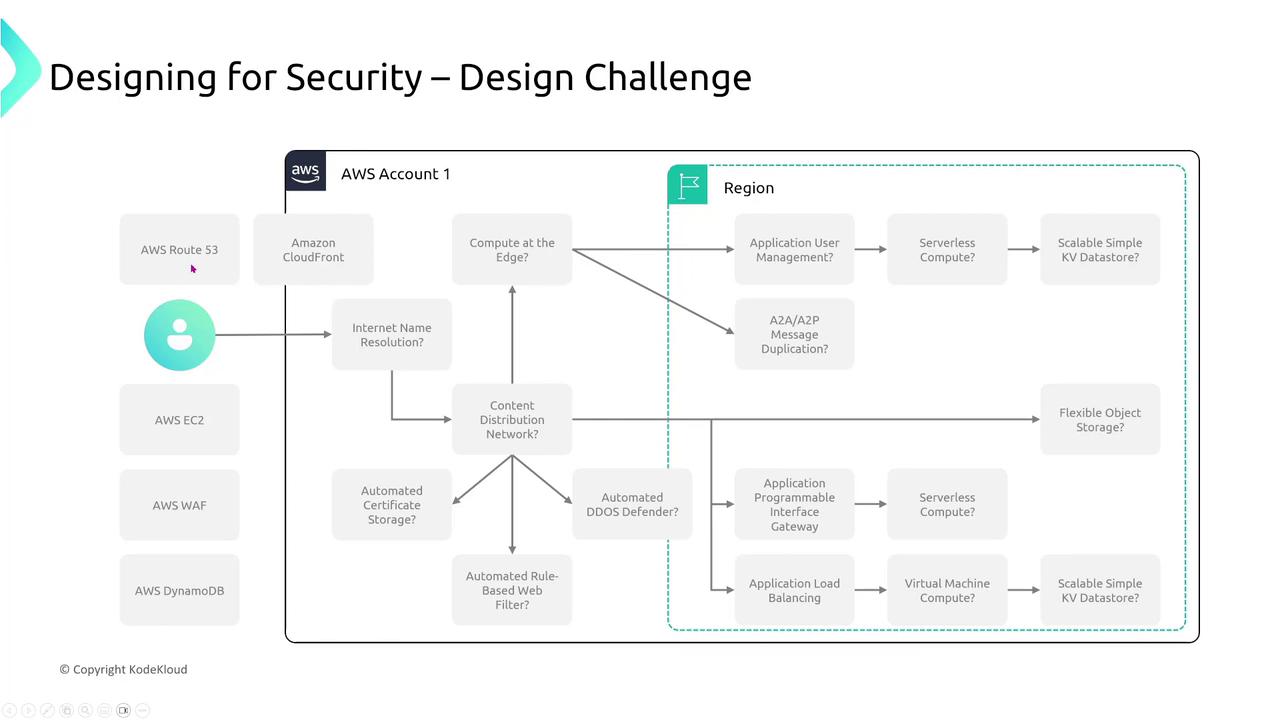
Section 13: Designing for Security Challenge
The final section features an interactive design challenge. You will be presented with a diagram similar to the one below, where one or more elements are intentionally missing. Your task is to select the correct AWS services and features (such as Route 53, WAF, DynamoDB, Amazon EC2, or Lambda) and drag them to their appropriate positions in the diagram.
Lesson Summary
To recap, this lesson on designing for security includes:
- A refresher on AWS Security Fundamentals based on the Well-Architected Framework.
- An introduction to key security design principles and the four essential security categories.
- A detailed examination of the AWS Shared Responsibility Model.
- Insights into security configurations across various AWS service categories.
- An engaging design challenge that reinforces the concepts discussed.

Note
This comprehensive approach is tailored to strengthen your architectural analysis skills and prepare you for the AWS Solutions Architect Associate Certification while honing practical security design abilities.
Thank you for joining this session. Be sure to take detailed notes as you progress through the lesson. I’m Michael Forrester, and I look forward to seeing you in the next lesson.
Watch Video
Watch video content