AWS Organizations
AWS Organizations allows you to group multiple AWS accounts into organizational units, simplifying policy management and security control enforcement across an enterprise. A crucial feature is Service Control Policies (SCPs). SCPs serve as an account-level permission guard: when an SCP denies access to a service, no account-level configuration can override that decision. This approach enforces consistent IAM policies and logging practices.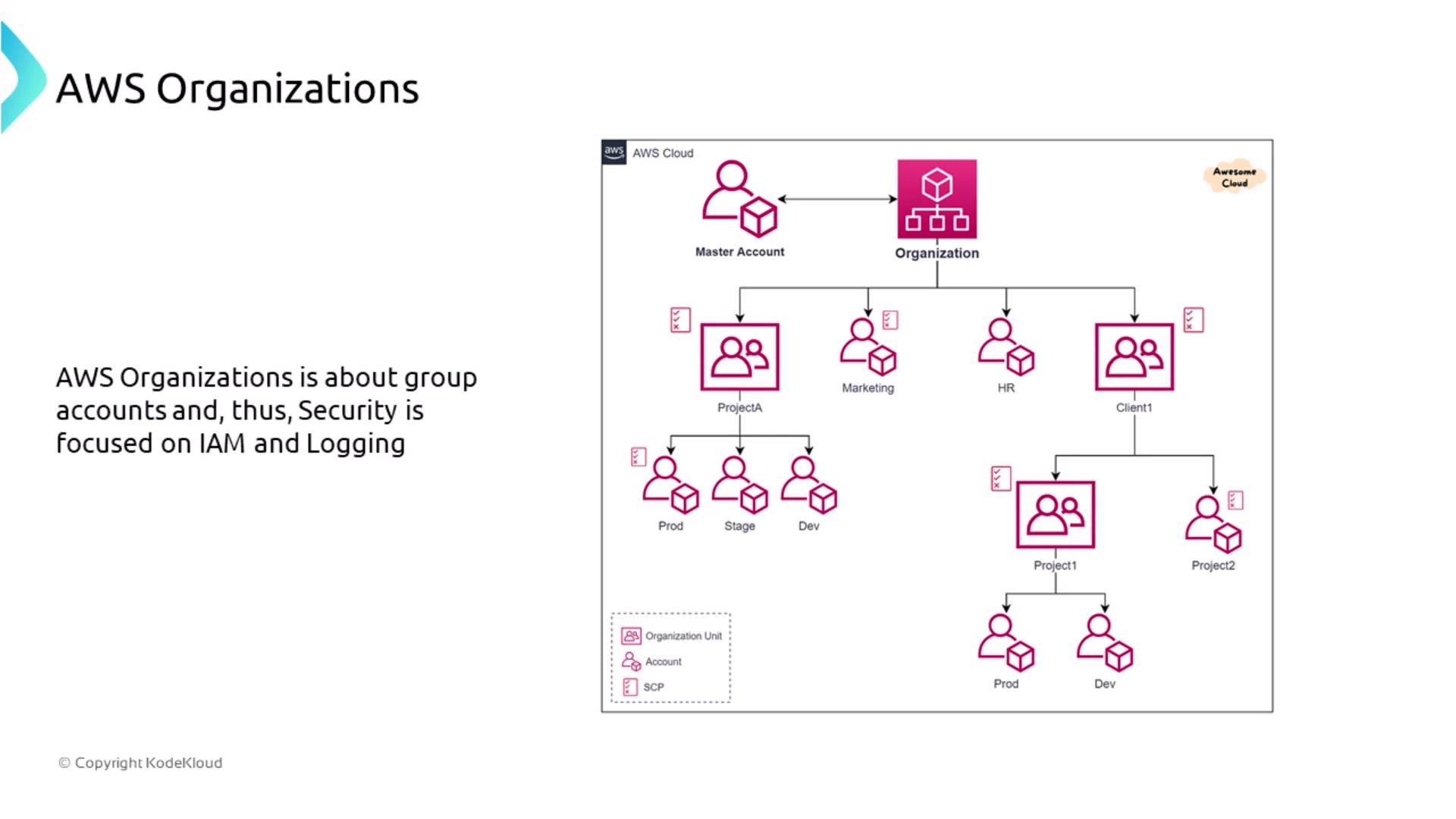

CloudTrail and Centralized Logging
Centralizing CloudTrail logging across AWS Organizations simplifies the management of global events. With a single trail capturing events from all accounts, compliance and auditing are streamlined, and uniform security monitoring is maintained. Integration with AWS Control Tower further improves the automated enforcement of security standards.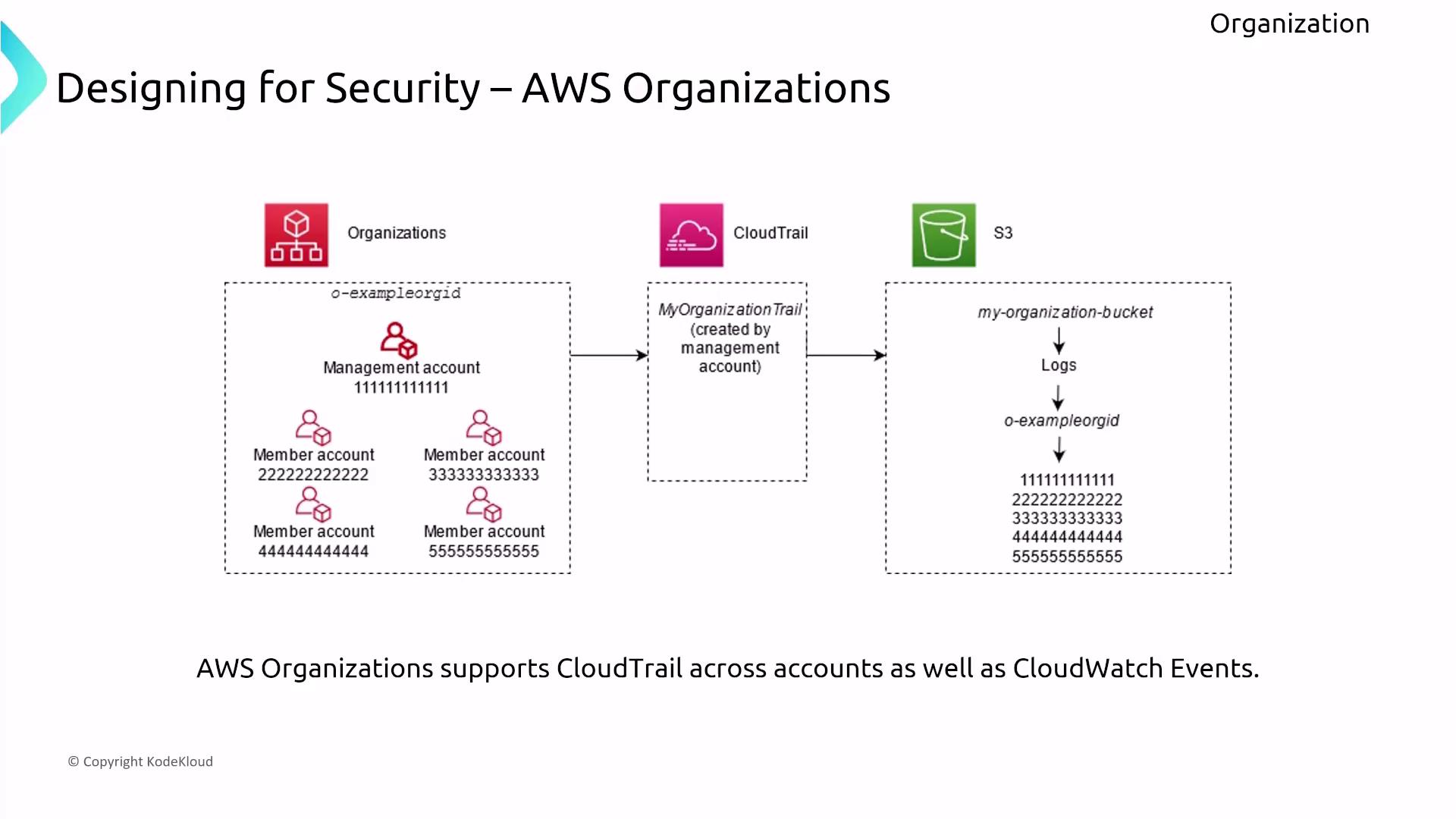
AWS Control Tower and IAM Identity Center
AWS Control Tower simplifies the setup and governance of multi-account environments by integrating AWS Organizations with AWS Identity Center (formerly SSO). Control Tower automatically configures IAM Identity Center to enable centralized user management, automated account provisioning, and governance. This setup not only activates CloudTrail but also enforces both proactive prevention and detection controls via AWS Config.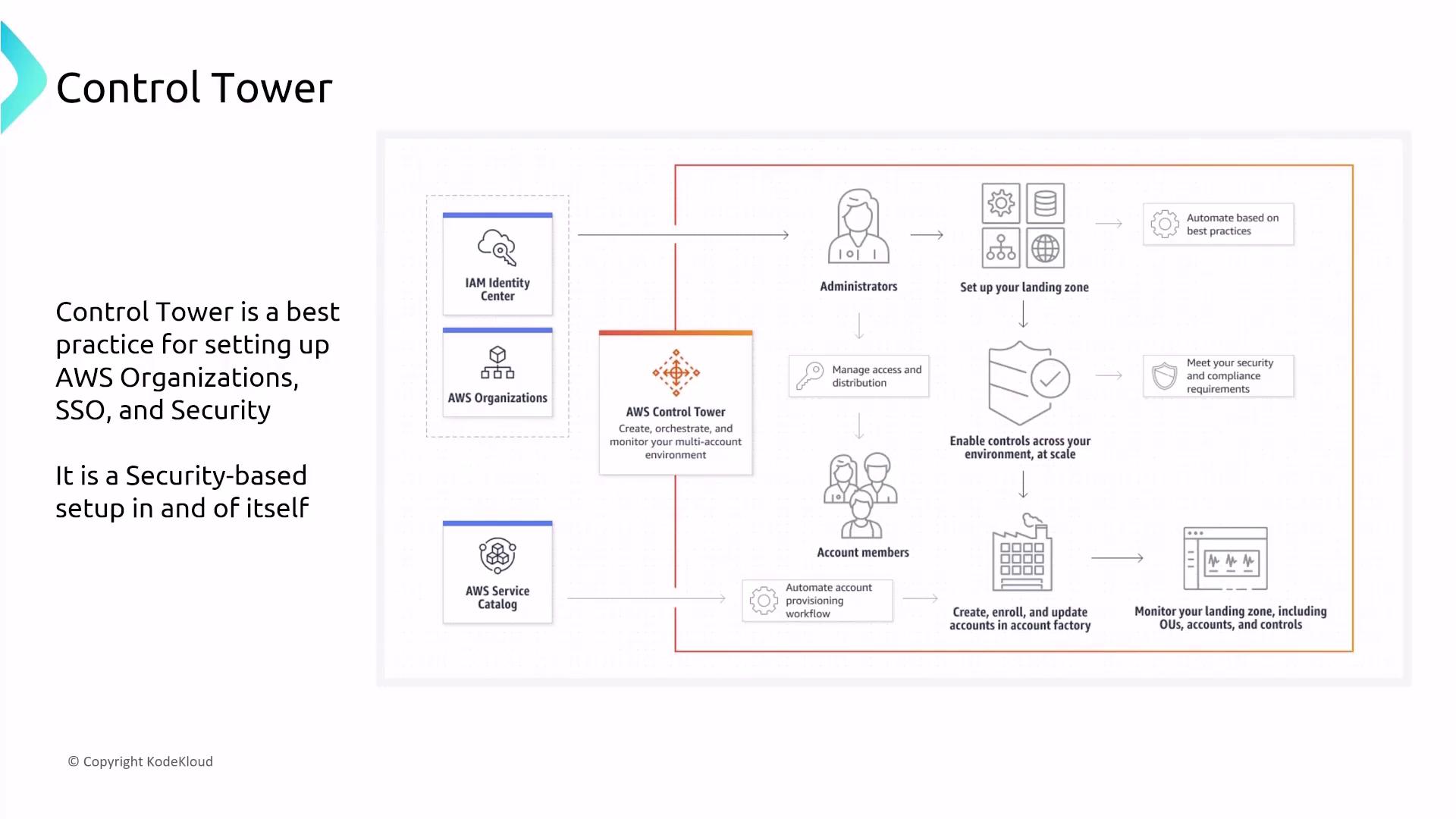
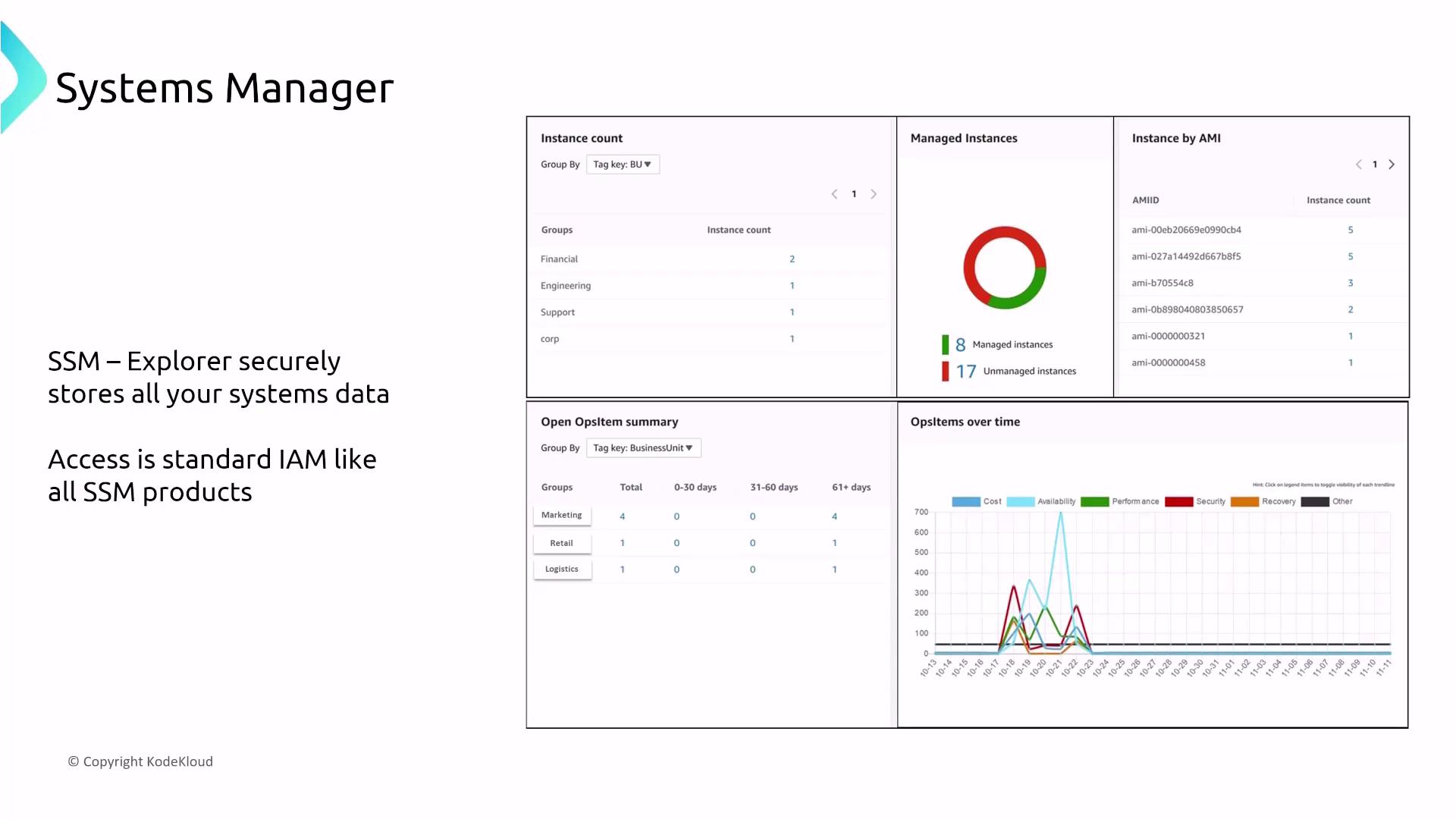
AWS Systems Manager
AWS Systems Manager is a comprehensive management suite designed for routine operational tasks such as patching, inventory management, session management, and compliance reporting for both EC2 and on-premises servers. By installing the Systems Manager (SSM) agent, you can perform secure operations at scale.Key Components of Systems Manager
- Systems Manager Explorer and OpsCenter
Use Explorer for gaining operational insights, while OpsCenter facilitates incident management. Together with CloudTrail, CloudWatch, and IAM, these components secure and log operational actions.
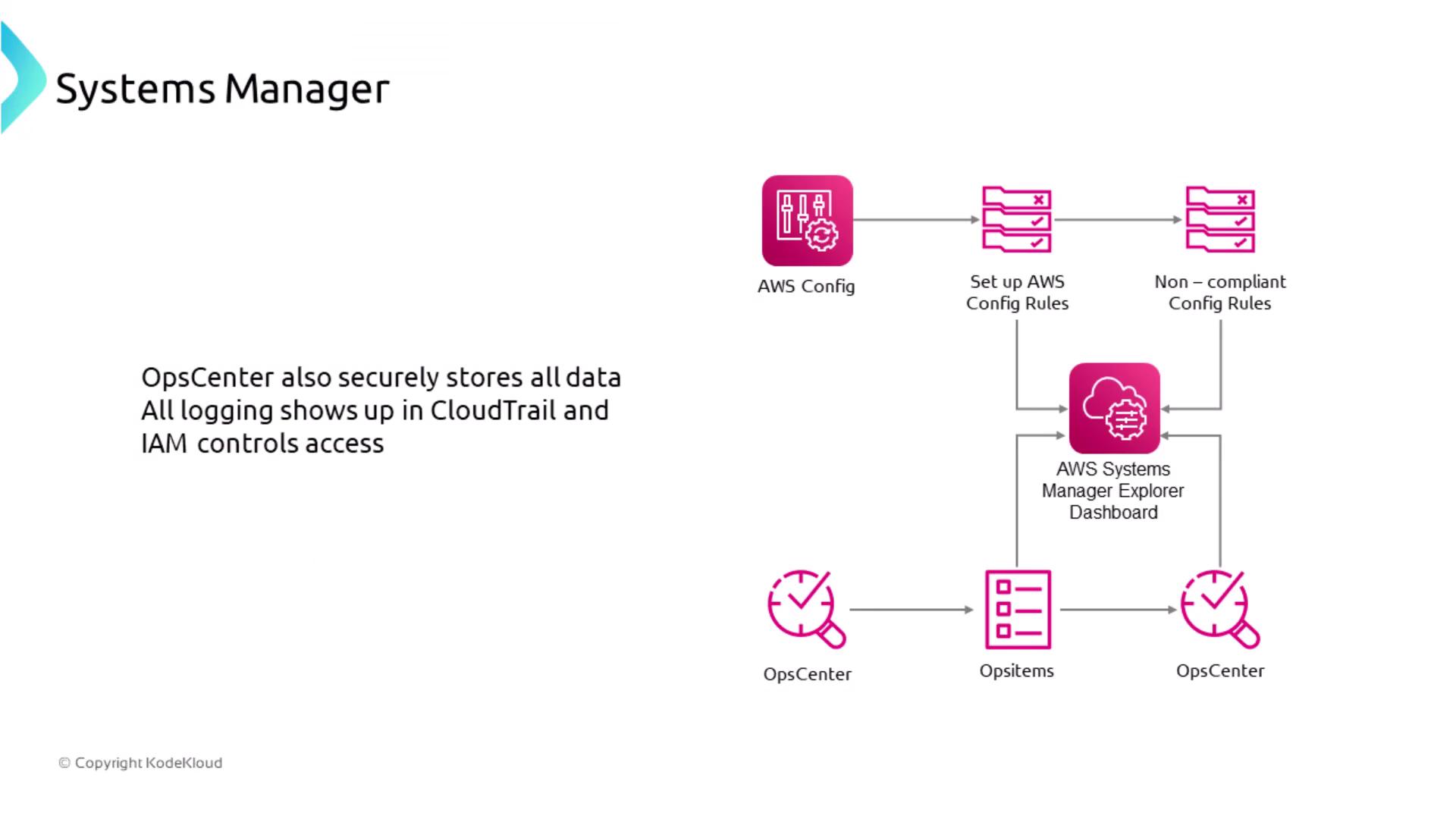
- Systems Manager Diagrams
Diagrams illustrate how several subservices, including AWS Config, OpsCenter, and Inventory, work together to provide secure logging and management.
- Incident Manager
Incident Manager enables the creation and management of response plans for operational events and failures, making it ideal for coordinating incident response efforts in complex environments.
- Application Manager and AppConfig
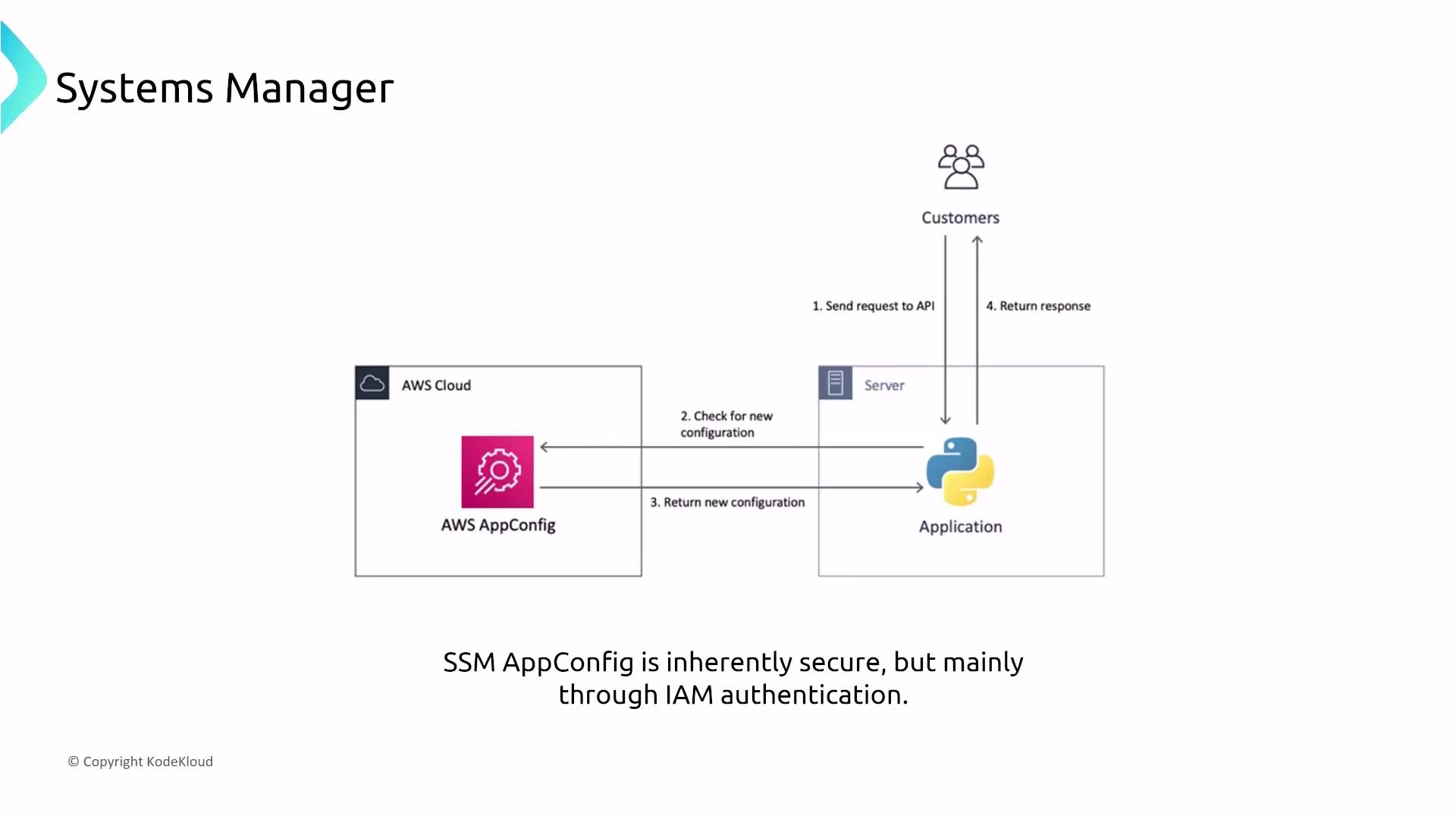
Application Manager provides alarms and operational insights for custom applications and services. AppConfig enables you to securely manage, validate, and deploy application configurations using IAM controls.
- Parameter Store
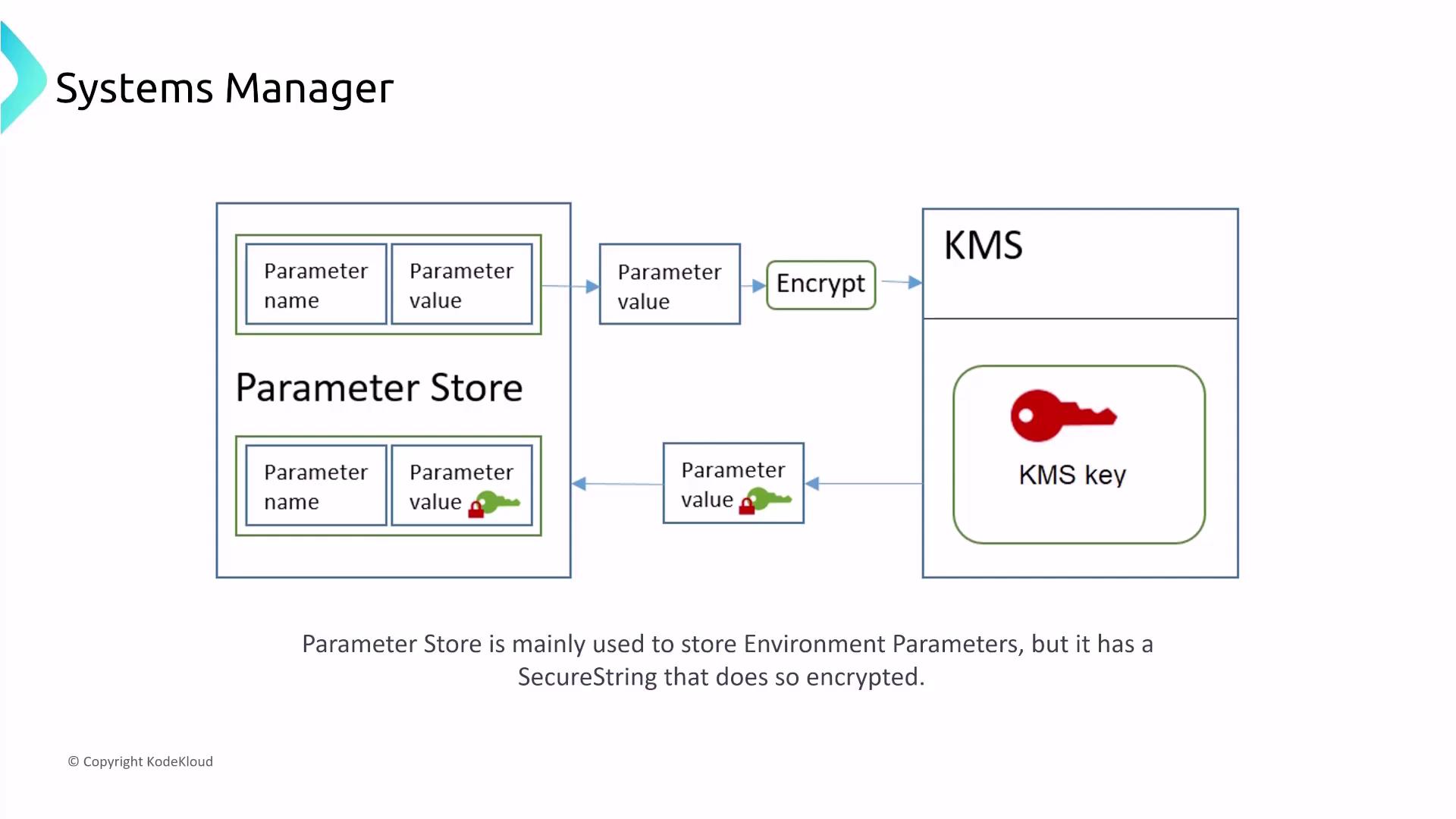
Parameter Store is a secure repository for environment variables, credentials, and configuration parameters. With native KMS encryption, sensitive data is protected using SecureString.
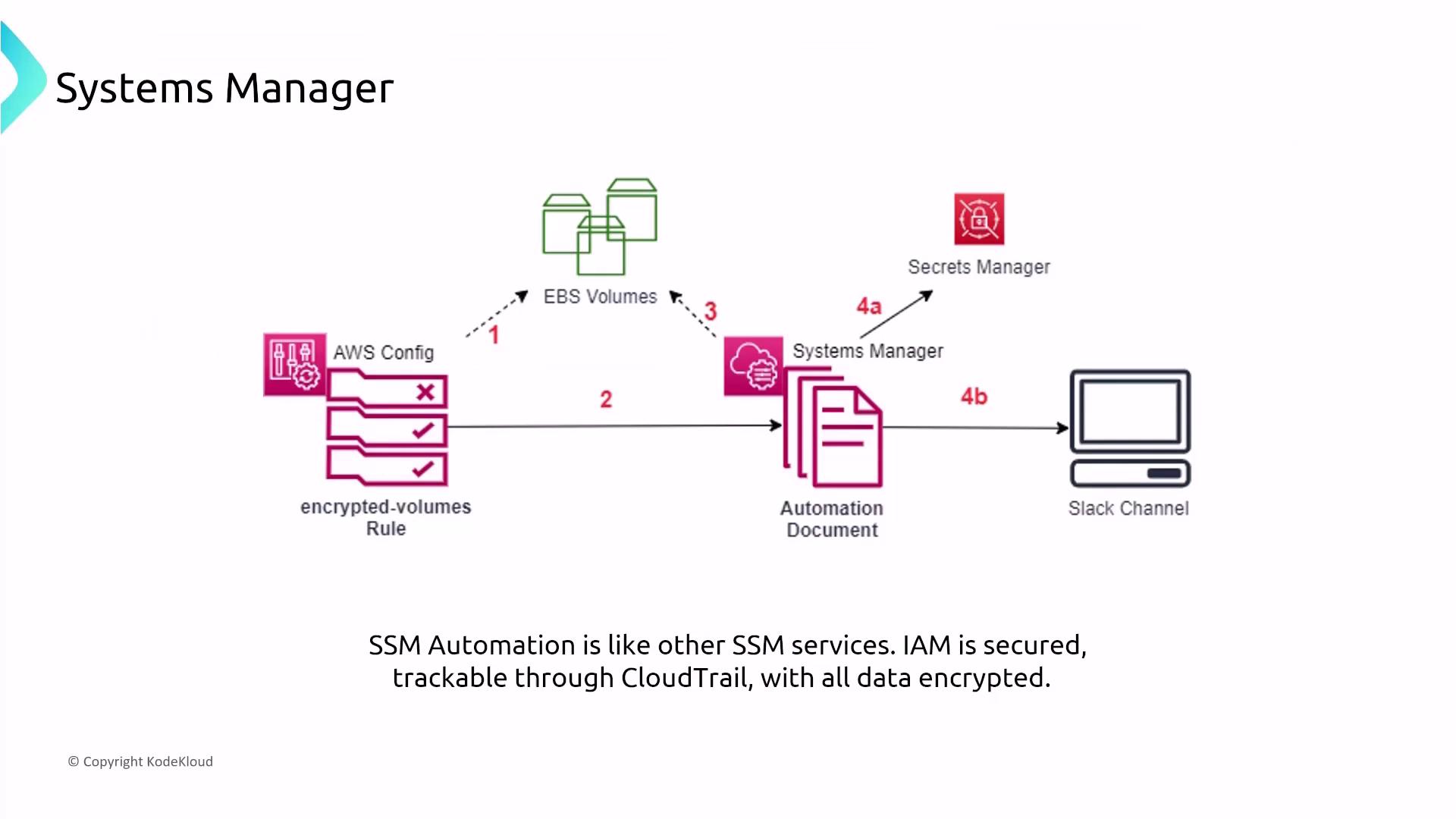
- Change Manager and Automation
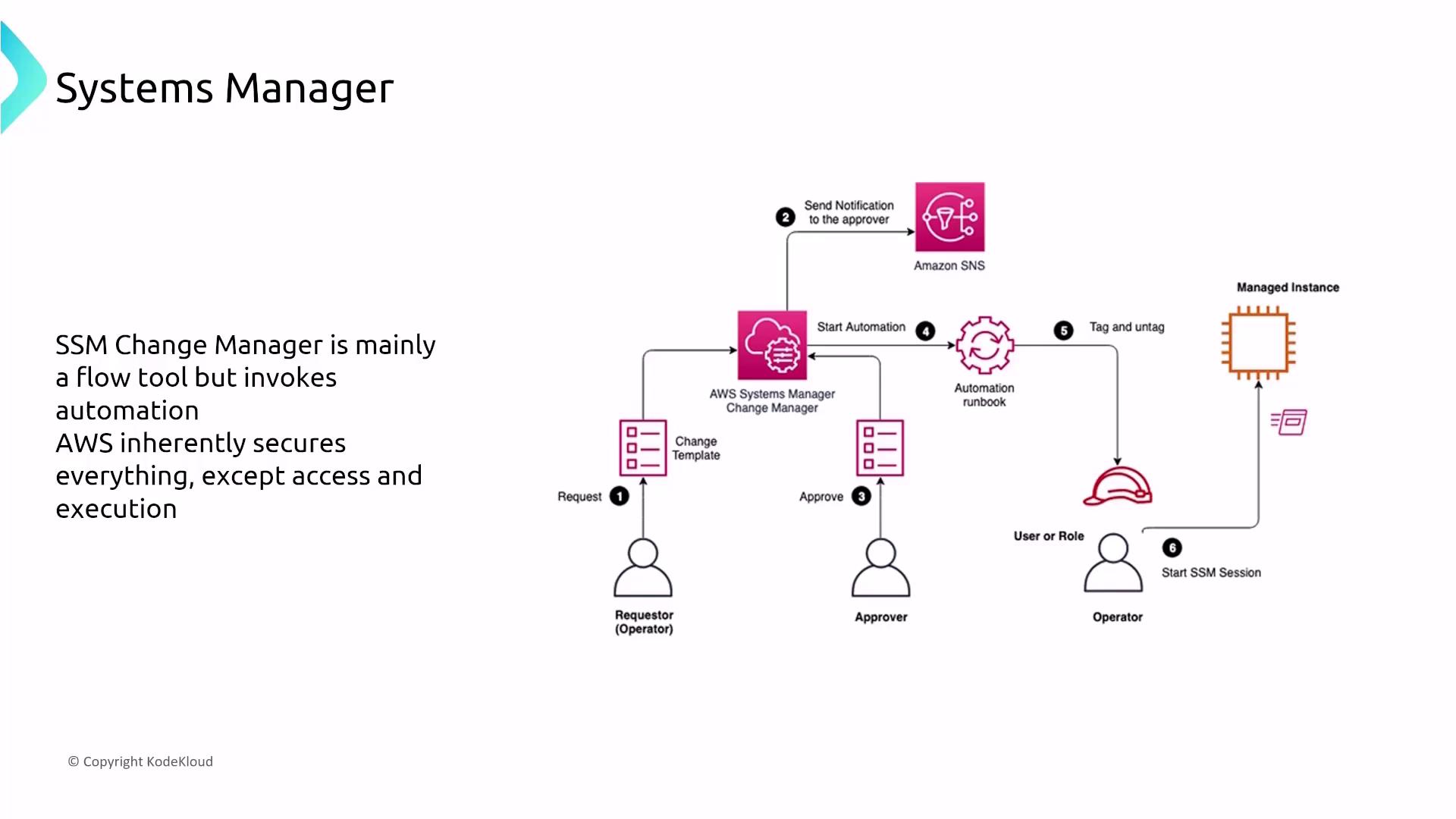
Change Manager allows you to define and automate operational workflows with runbooks, ensuring that changes are consistent and auditable. Its automation processes, secured by IAM and logged by CloudTrail, help streamline repetitive tasks such as patch updates and configuration changes.
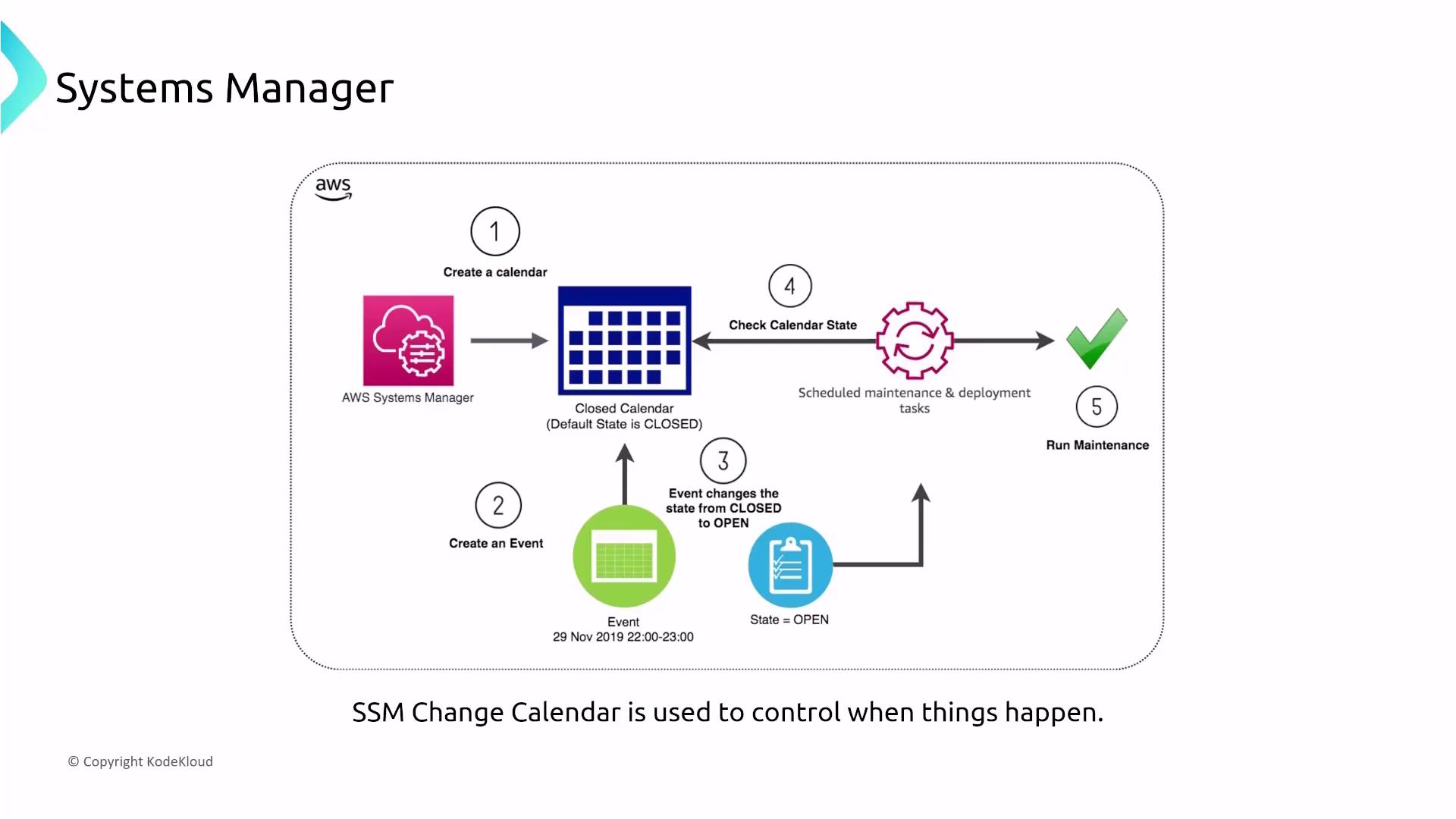
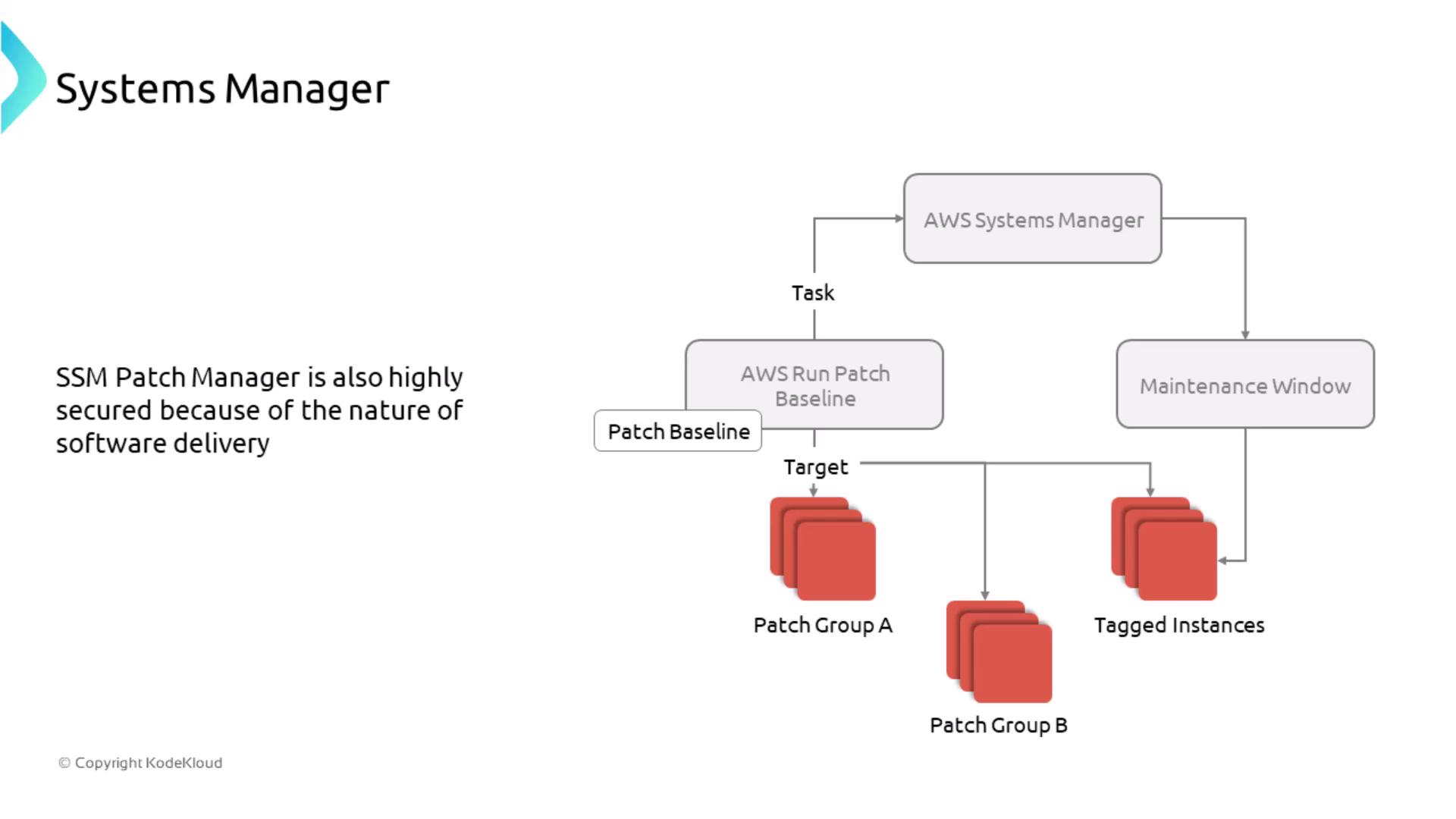
- Maintenance Windows
Maintenance Windows, in conjunction with Patch Manager, schedule patching during approved windows. This ensures that updates occur in a controlled and secure manner, grouping instances by tags regardless of the operating system.
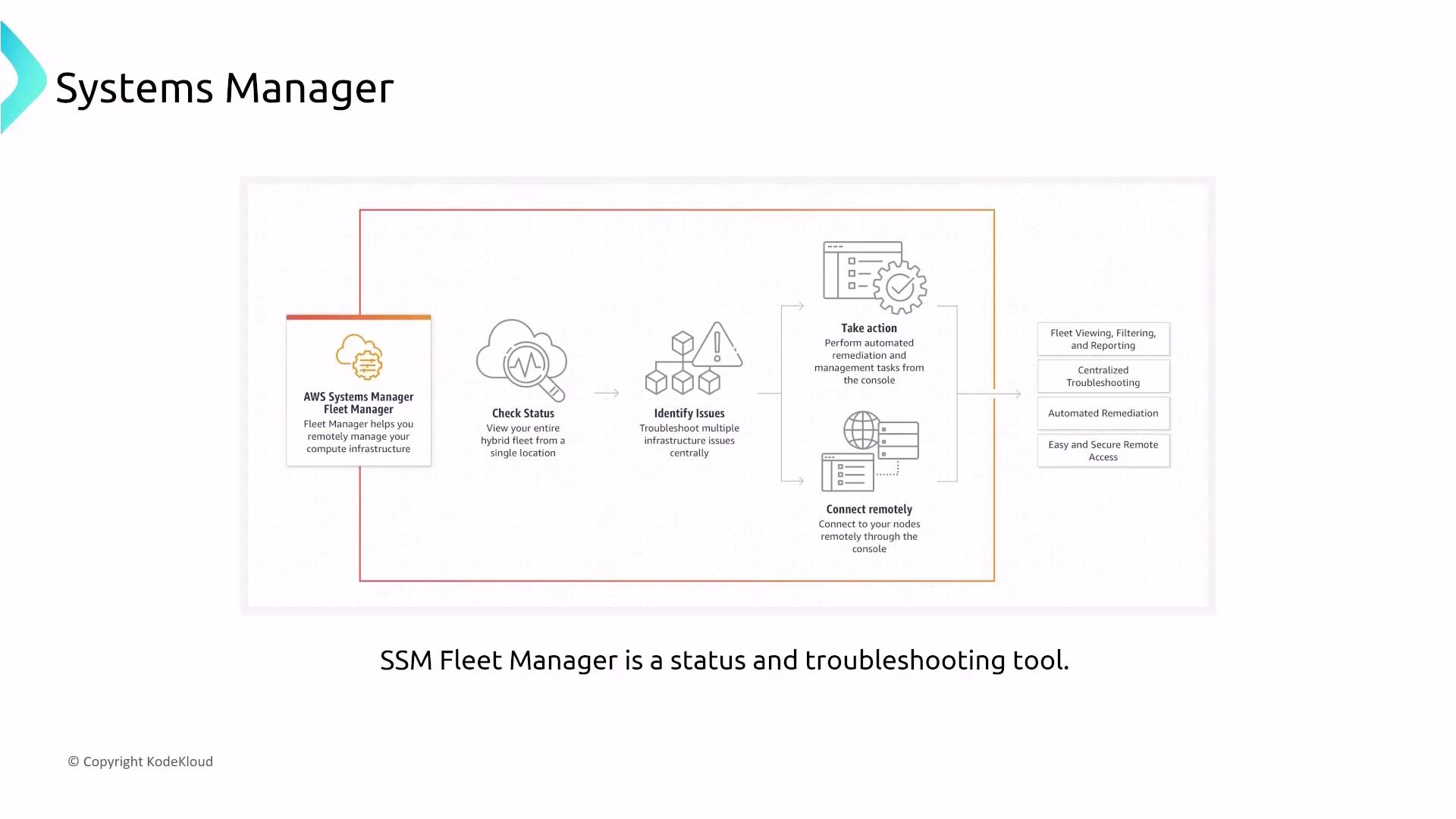
- Fleet Manager and Compliance
Fleet Manager provides a centralized console to monitor and troubleshoot a fleet of EC2 or on-premises servers. With Compliance and Inventory features, it reinforces security by tracking configuration and patch adherence.
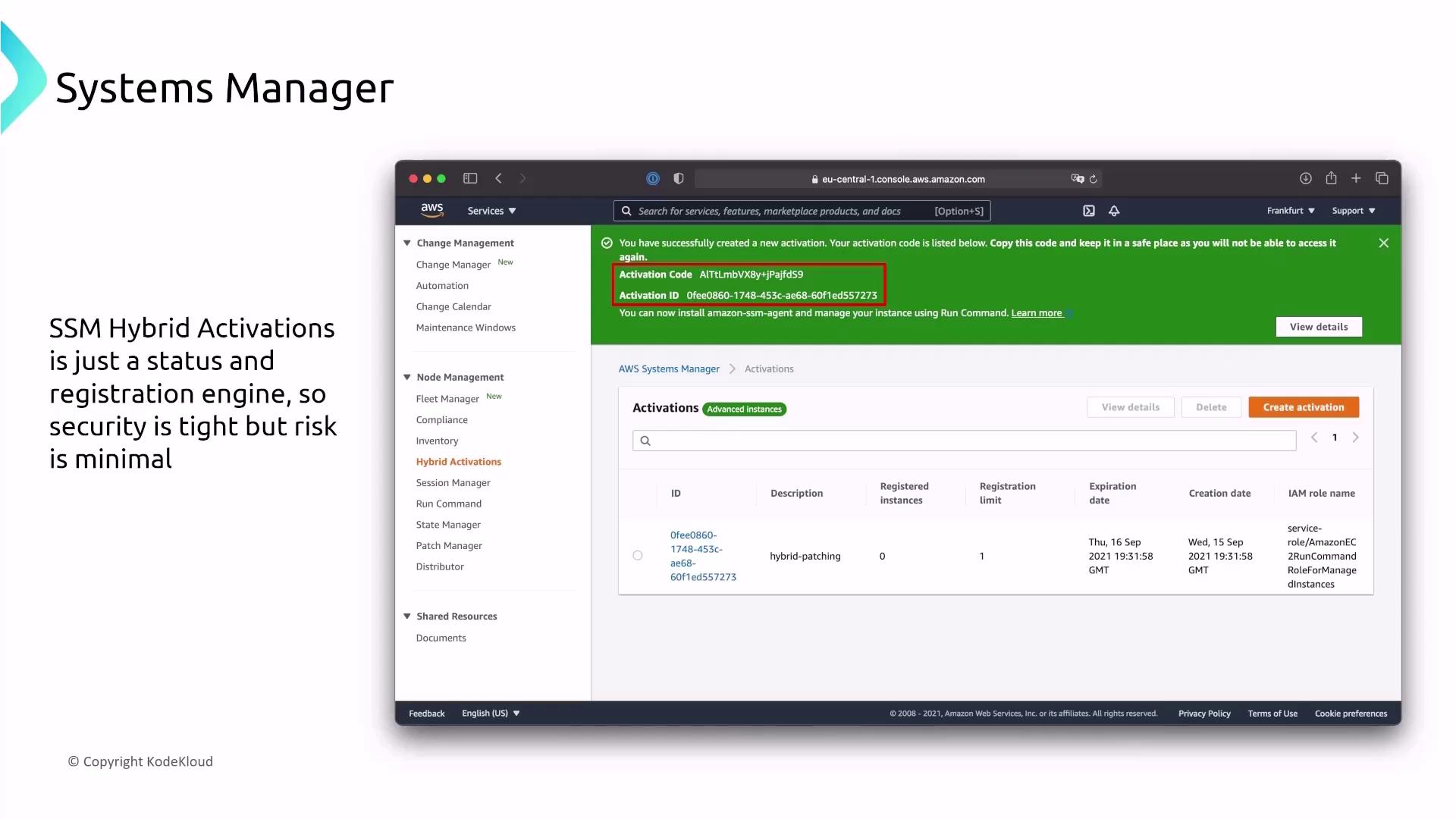
- Hybrid Activations
Hybrid Activations serve as a registration engine for on-premises servers, allowing them to securely register with AWS Systems Manager using activation codes.
- Session Manager and Run Command
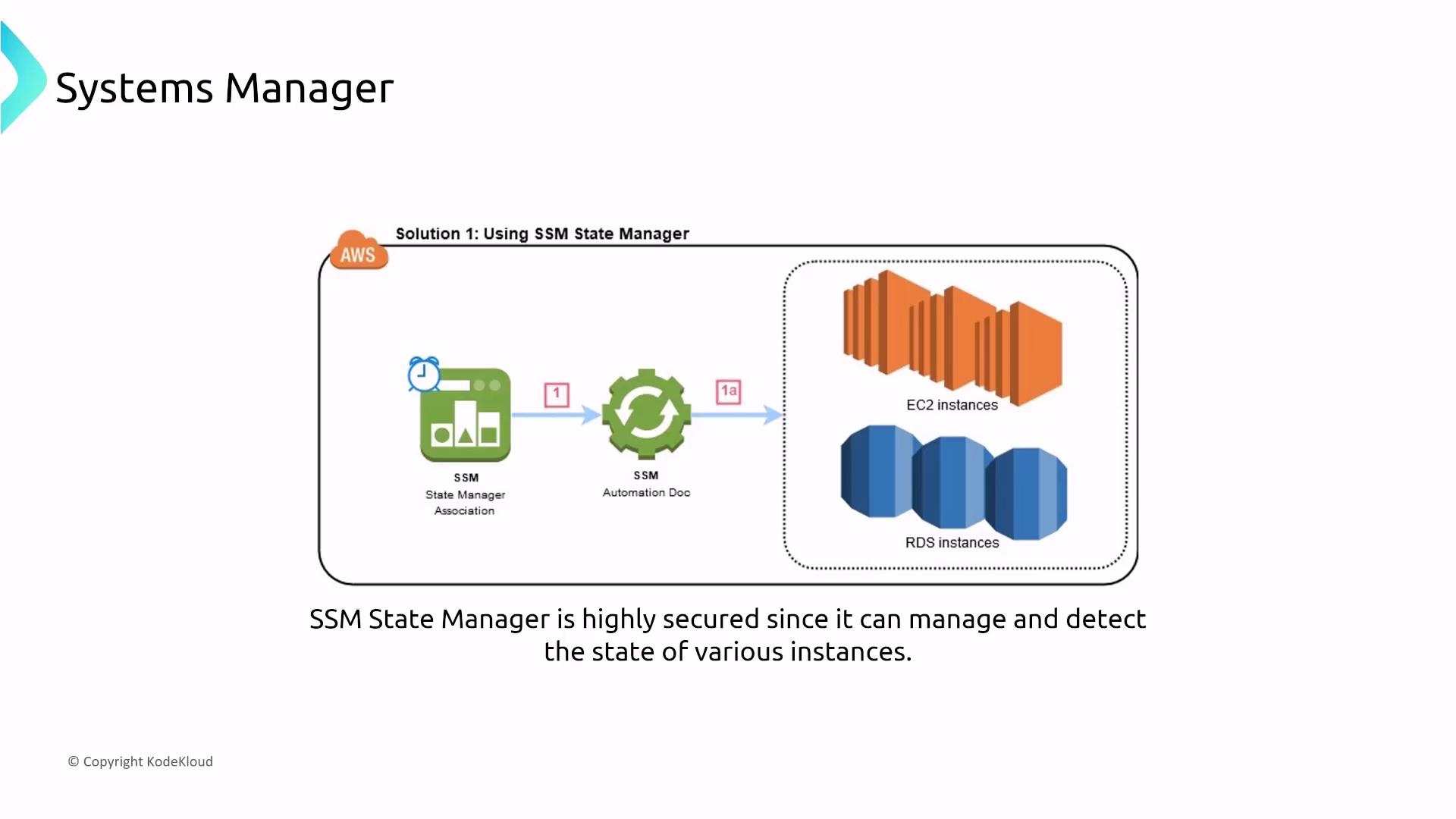
Session Manager enables secure remote access (via SSH or RDP) without public endpoints, while Run Command allows execution of one-off commands across multiple instances. Both integrate with IAM, CloudTrail, and CloudWatch for robust security and logging. Additionally, State Manager ensures that instances maintain their desired configuration state—for example, enforcing that a web server only listens on port 443.
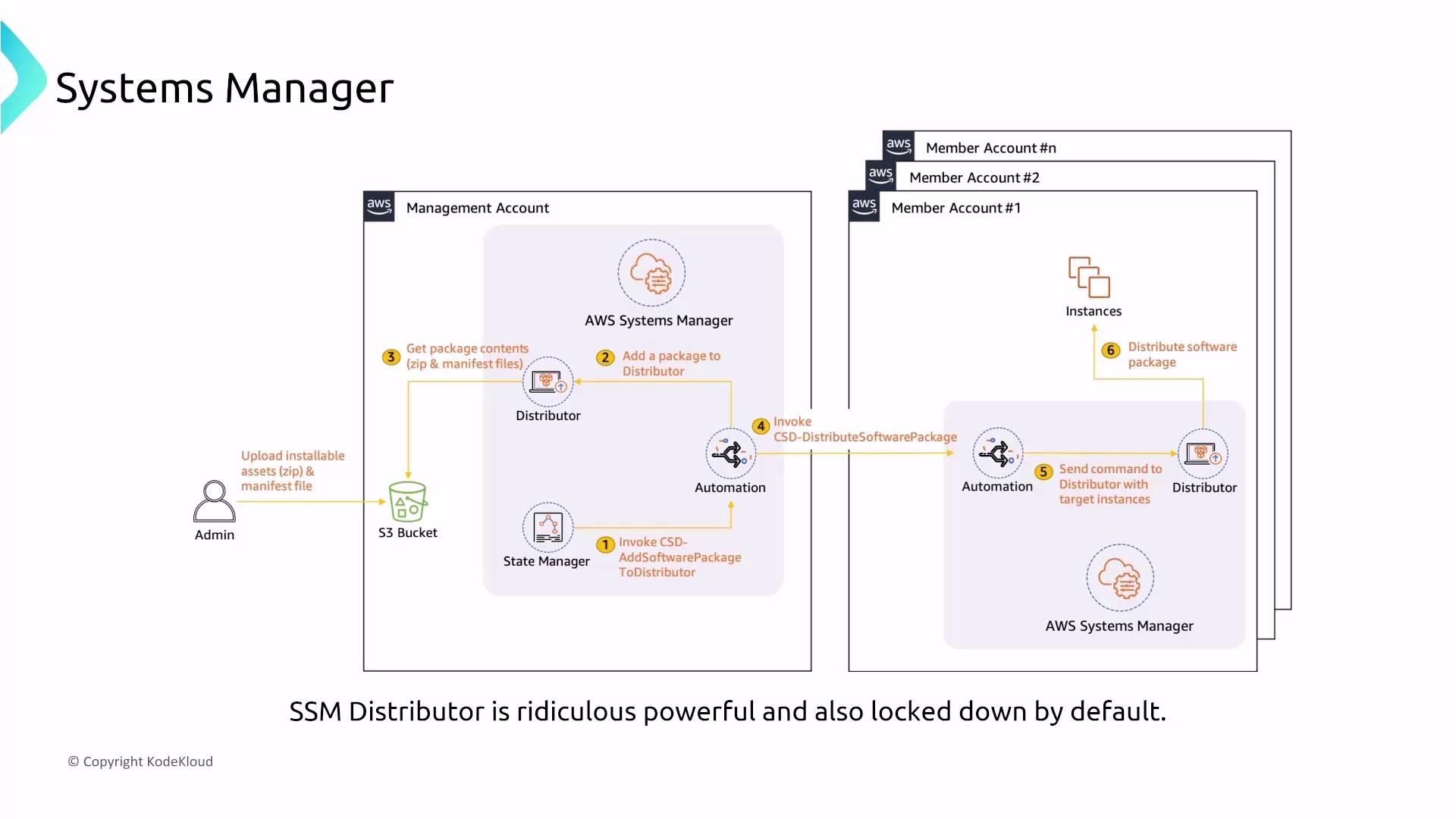
- Patch Manager and Distributor
Patch Manager automates system patching based on predefined baselines and maintenance windows. In parallel, SSM Distributor securely distributes custom software packages across your environment using controlled IAM permissions.
- SSM Documents
SSM Documents are AWS-hosted, encrypted scripts designed to standardize operational tasks. When used with the automation engine and State Manager, they help enforce consistent configurations and manage routine tasks across your environment.
AWS Service Catalog and License Manager
- Service Catalog
AWS Service Catalog allows you to offer pre-configured AWS resources packaged as CloudFormation or Terraform templates. You maintain security by managing access through strict IAM policies and roles.

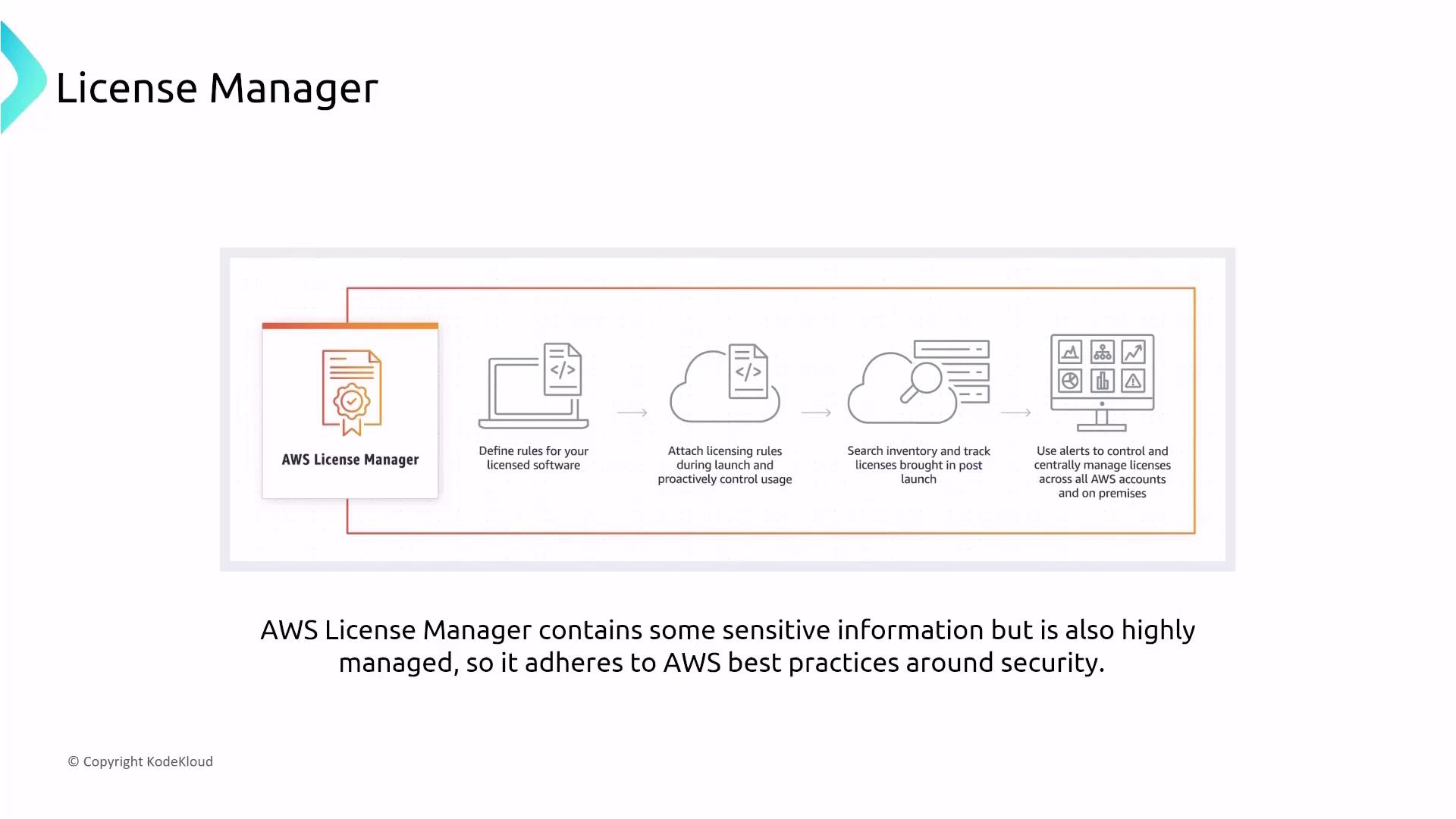
- License Manager
AWS License Manager helps track and manage licenses, including notifications for license overages or expirations while adhering to AWS security best practices to safeguard sensitive information.
AWS Proton
AWS Proton is designed for automated container and serverless deployments. While Proton abstracts much of the deployment process with limited direct security controls, it integrates CloudTrail for thorough logging. Secure deployments with Proton require ensuring that logs are stored in encrypted S3 buckets and that built-in security controls for environment templates are fully leveraged.
Additional Management Tools
Other management services such as Tag Editor, Resource Explorer, Resource Groups, Resource Access Manager, and Resilience Hub primarily rely on IAM for security. Typically, these services do not offer additional logging mechanisms beyond standard AWS managed security practices. All management and governance tools include encryption in transit and at rest by default, ensuring that sensitive operations remain protected.Conclusion
In summary, we reviewed a variety of AWS management services and examined how security is integrated across each. From AWS Organizations with SCPs and centralized CloudTrail logging to AWS Control Tower’s automated setup and the comprehensive feature set of AWS Systems Manager, AWS offers robust security and governance mechanisms primarily anchored by IAM, CloudTrail, and native encryption.
Stay tuned for our next article, where we continue to explore additional aspects of security and operational excellence. For more detailed guidance, refer to the AWS Documentation.