AWS Solutions Architect Associate Certification
Designing for Security
Turning up Security on Management Services Part 1
Welcome to this comprehensive lesson on Designing for Security. In this article, we delve into security measures for various AWS management and governance services. We focus on the importance of secure provisioning and observability, highlighting best practices and key considerations when working with these highly managed services.
Provisioning Services and CloudFormation Security
AWS CloudFormation, the leading infrastructure-as-code tool, allows you to create and manage AWS resources based on a template you author. Typically, you craft a CloudFormation template, store it locally or in an S3 bucket, load it into the CloudFormation engine, and then create the associated stack.
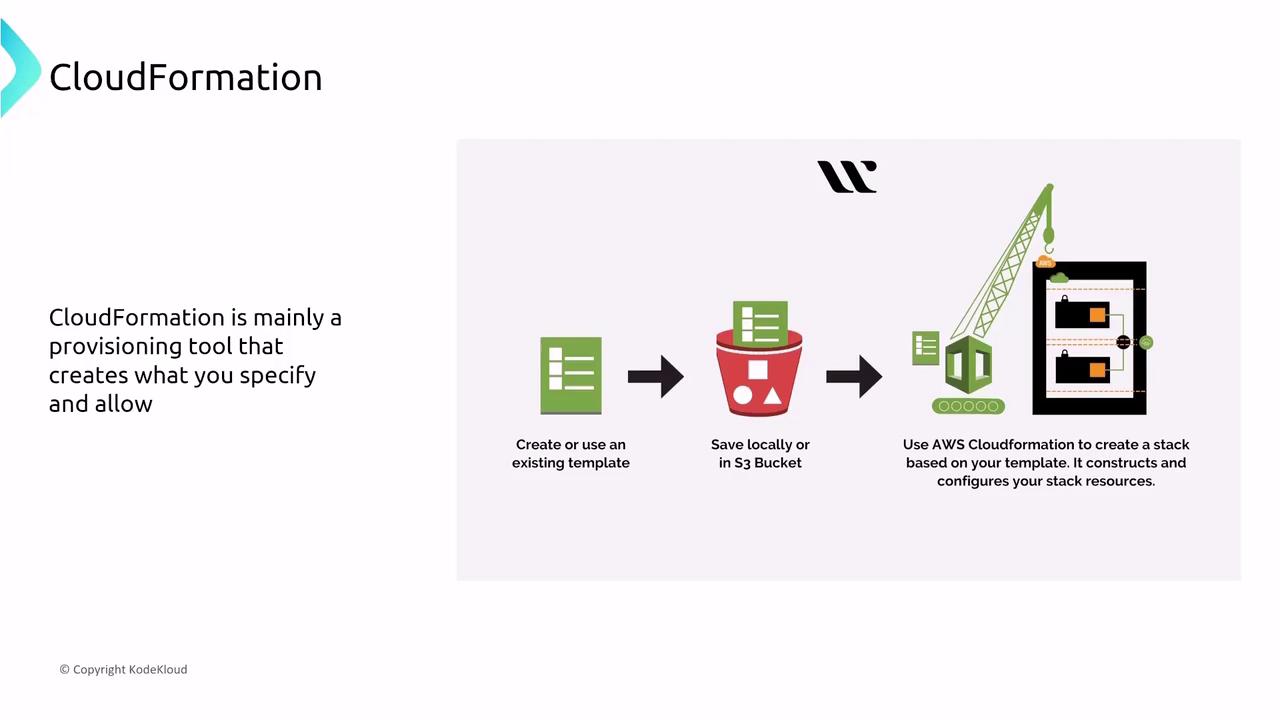
When deploying infrastructure with CloudFormation, pay close attention to the following security aspects:
- Secure storage of sensitive information.
- Assigning appropriate permissions to CloudFormation during execution.
For example, if CloudFormation is tasked with creating 15 resources but is granted permissions for only 14, the stack creation will fail. Ensure the IAM roles and policies specified in your template align with the minimum permissions required for each resource.
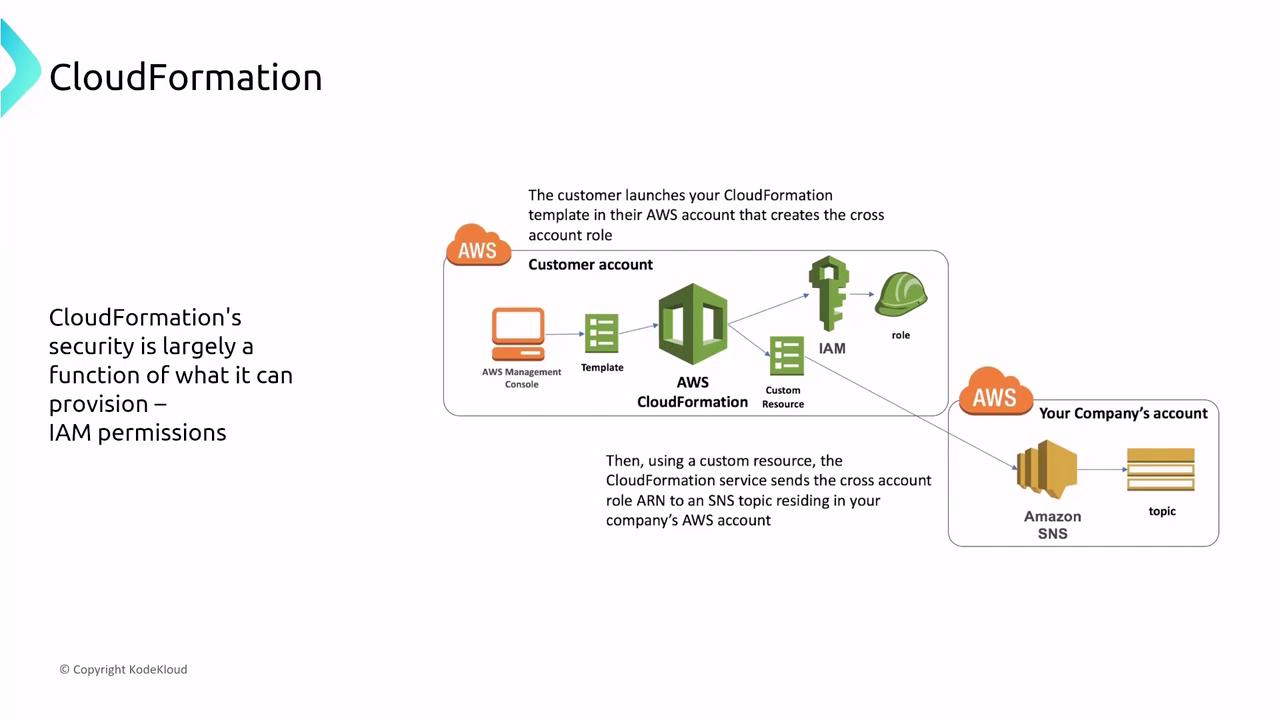
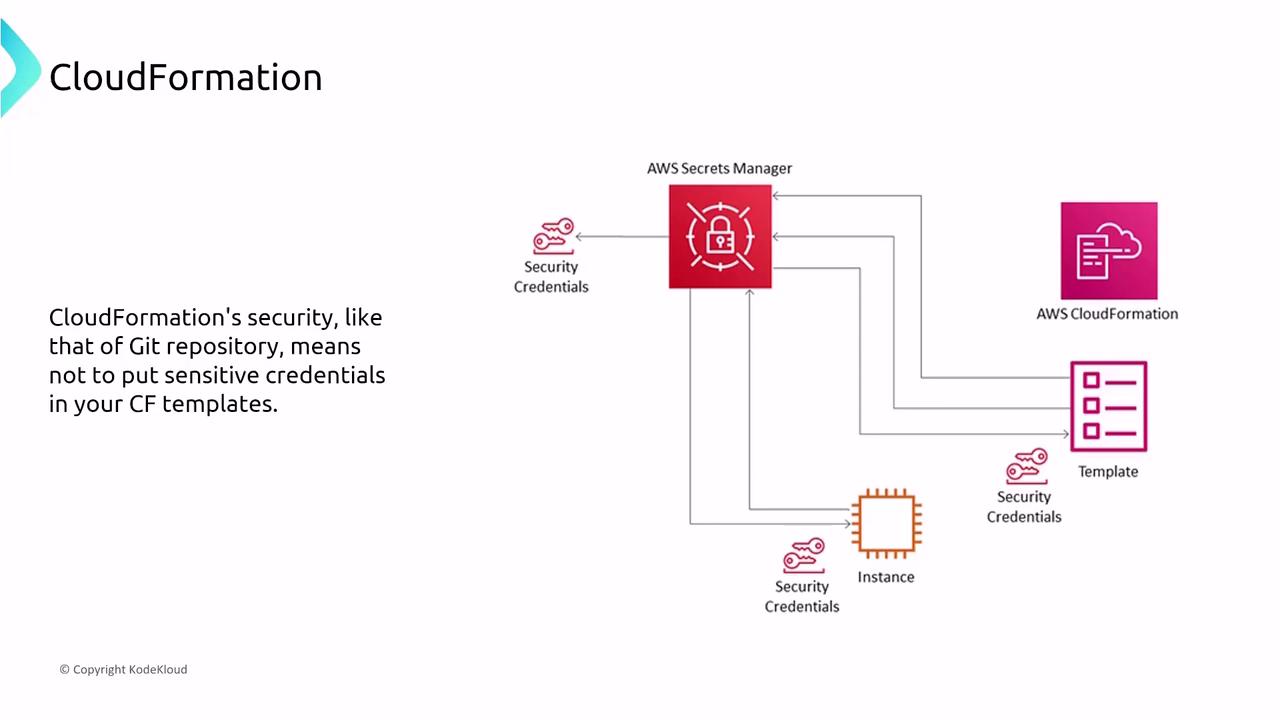
A best practice is to define a tailored IAM role (or a set of roles) that grants only the necessary permissions for each component of your template. Remember, if no specific user or role is provided, CloudFormation operates with the permissions of the initiating user. Also, avoid embedding sensitive credentials directly in your template; instead, utilize services like AWS Secrets Manager or the Systems Manager Parameter Store.
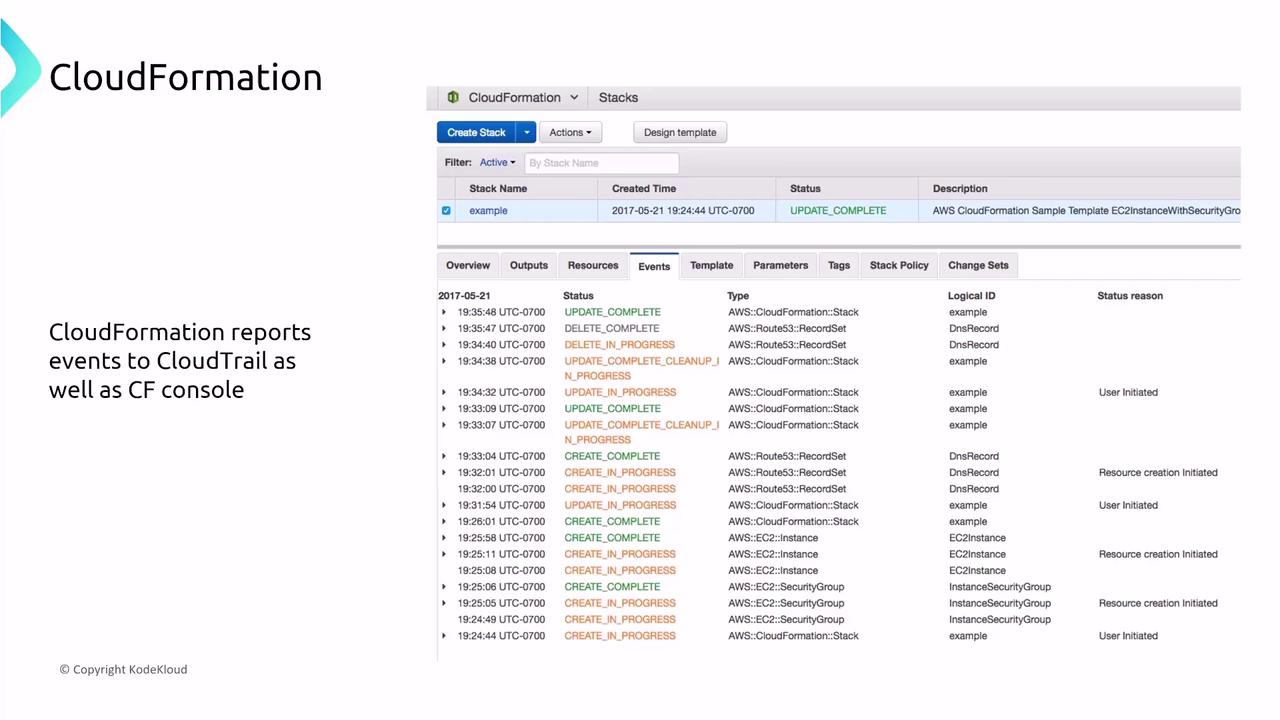
Sensitive data should be referenced using secure strings from the Parameter Store or managed via Secrets Manager with automatic rotation. Additionally, CloudFormation logs stack creation events in both its Events tab and AWS CloudTrail, making monitoring and review straightforward.
CloudWatch Events and CloudTrail further enhance security by tracking all stack-related changes.
Cloud Development Kit (CDK) and Its Security Considerations
AWS Cloud Development Kit (CDK) version 2 similarly transforms your code into CloudFormation templates. Security in the CDK framework hinges on the careful definition of roles and permission assignments within your constructs. When designing resources in languages such as TypeScript or Python, ensure that the IAM roles you define provide only the minimum necessary privileges.
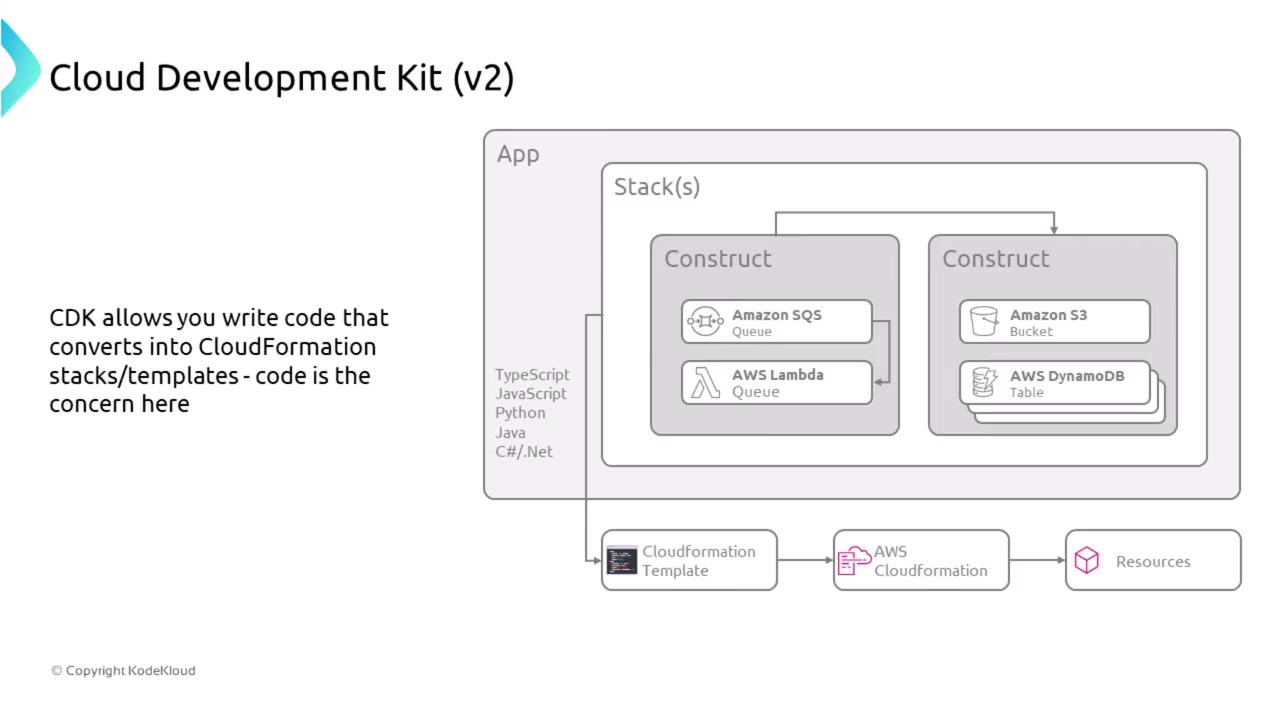
The CDK offers the flexibility to define resource roles and permissions as part of your application code. This approach not only streamlines infrastructure provisioning but also embeds security best practices from the onset.
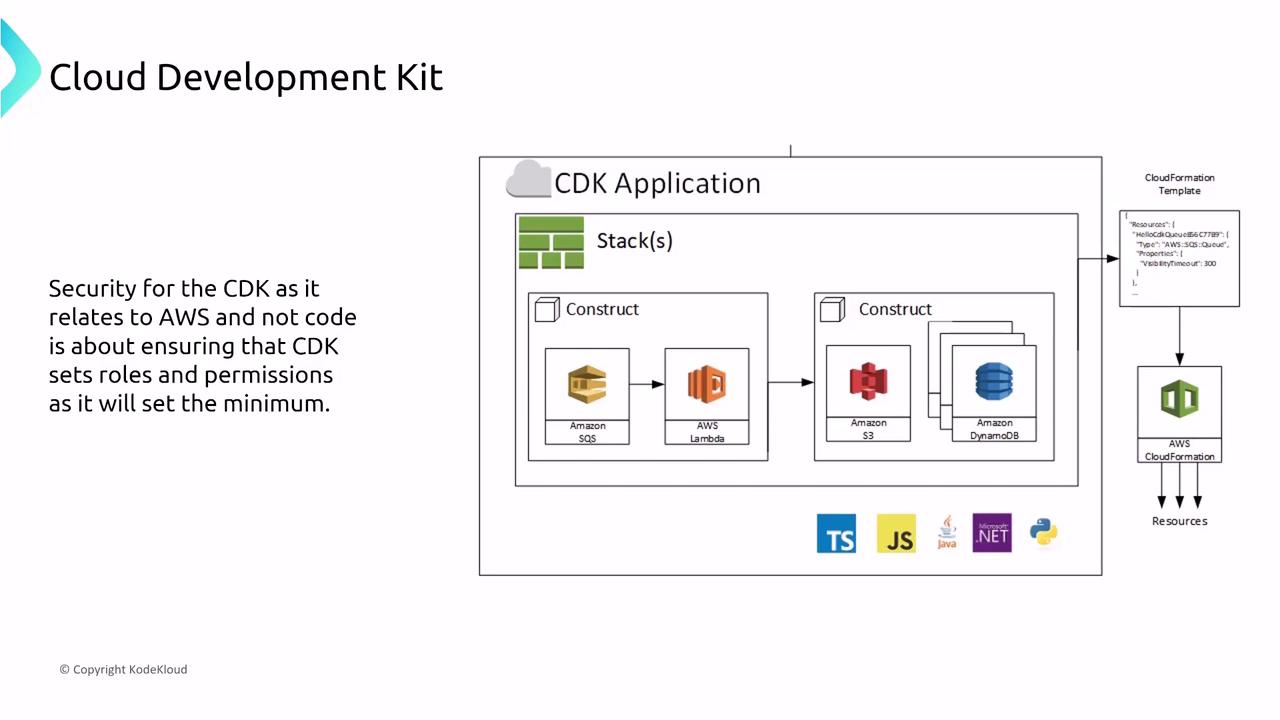
Furthermore, CDK allows you to associate roles for the deployed resources directly within your deployment script, ensuring that both the provisioning process and the running services adhere to defined permissions.
Observability: CloudWatch, X-Ray, and Data Protection
CloudWatch for Monitoring and Logging
AWS CloudWatch is central to collecting metrics, logs, alarms, events, X-Ray traces, and insights. It is essential for ensuring performance monitoring, health assessment, and timely alarm notifications. Although data is encrypted by default in CloudWatch, exercise caution to avoid unintentional exposure of sensitive information in logs or canaries. Data protection policies within log groups can help mask or filter sensitive elements such as email addresses, social security numbers, or credit card details.
Set up data identifiers and designate secure destinations for log data—such as S3, Kinesis Firehose, or CloudWatch Logs—to enforce filtering and masking rules.
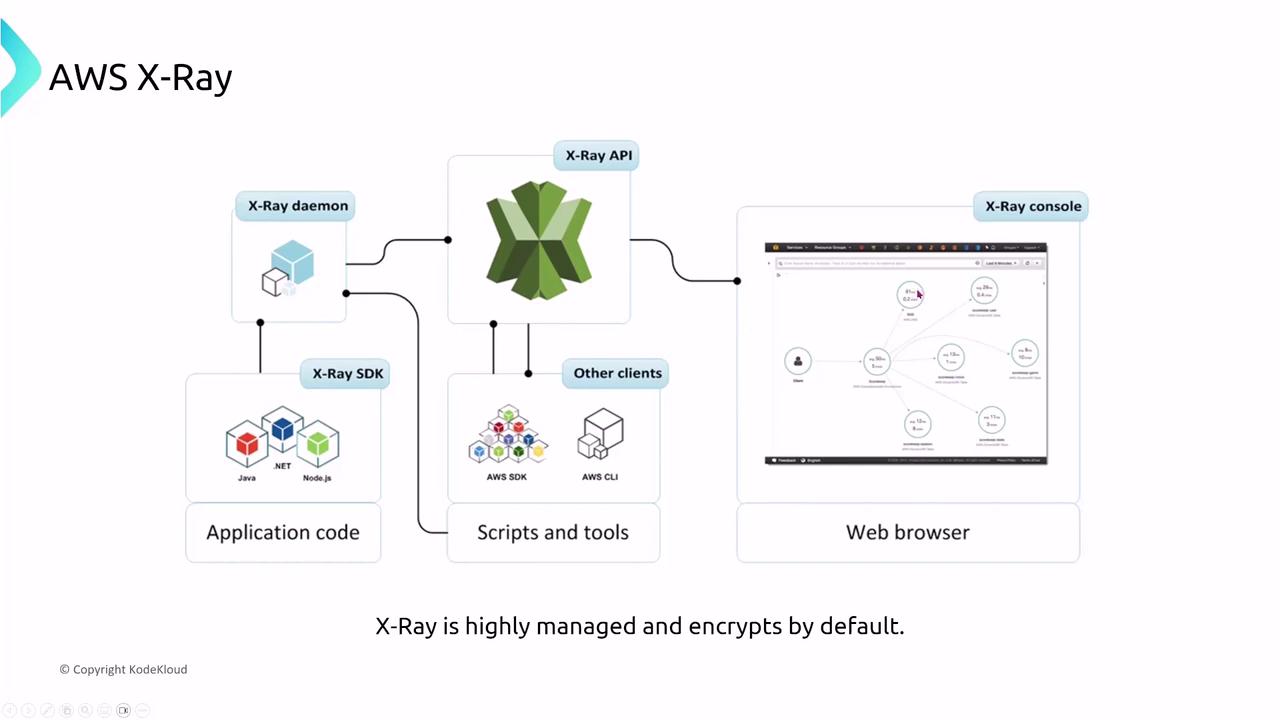
AWS X-Ray for Tracing
AWS X-Ray offers end-to-end tracing capabilities for monitoring user sessions across your AWS environment. With data encryption enabled by default via AWS KMS, secure access to trace data should only be granted to authorized users via well-defined IAM roles. If any trace segments contain sensitive information, configure sampling rules to exclude those segments as necessary.
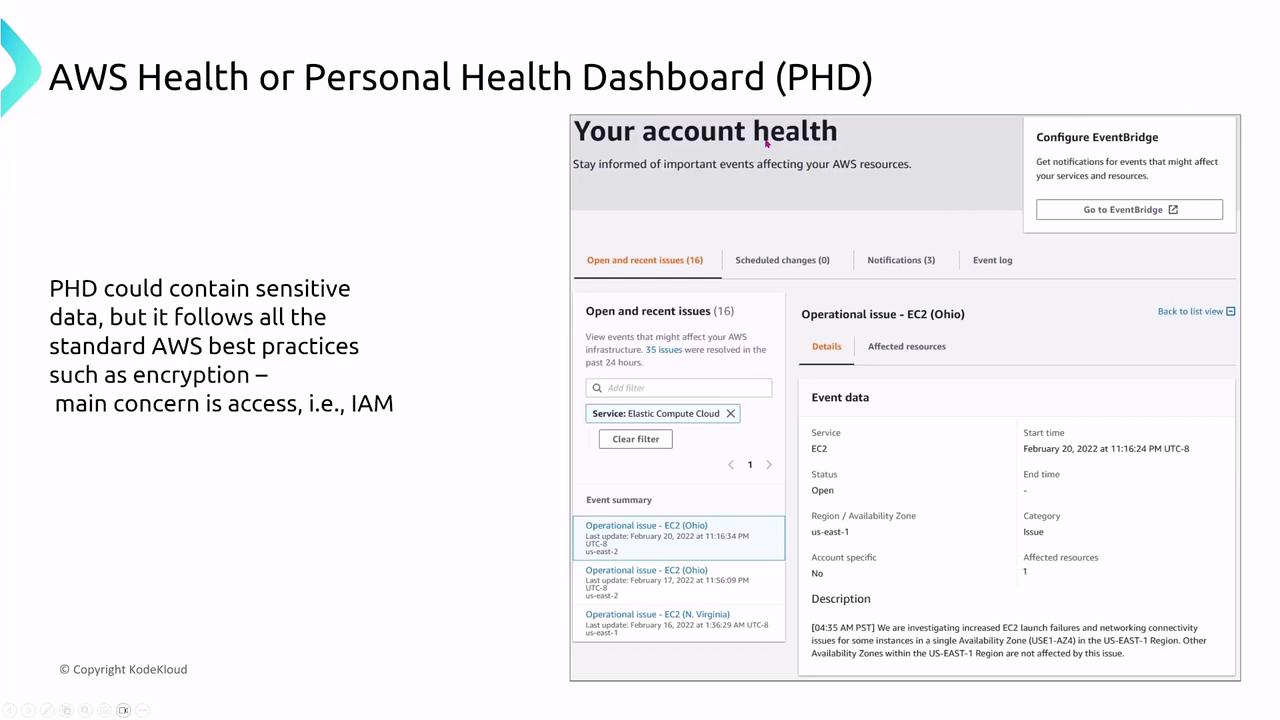
Personal Health Dashboard
The AWS Personal Health Dashboard (PHD), accessible via Systems Manager, provides a real-time status board for monitoring AWS service events that could impact your resources. Although the dashboard may display sensitive information, all data is encrypted and securely managed by AWS. Ensure that only users with specific permissions have access to this dashboard.
Managed Prometheus and Grafana
Amazon Managed Service for Prometheus
AWS recently introduced a managed service for Prometheus, which competes with CloudWatch by gathering metrics in a highly managed environment. Standard security measures—including encryption, logging, and IAM-based access—are in place. Access is secured via VPC endpoints, and integrating its API calls with CloudTrail enables comprehensive auditing.
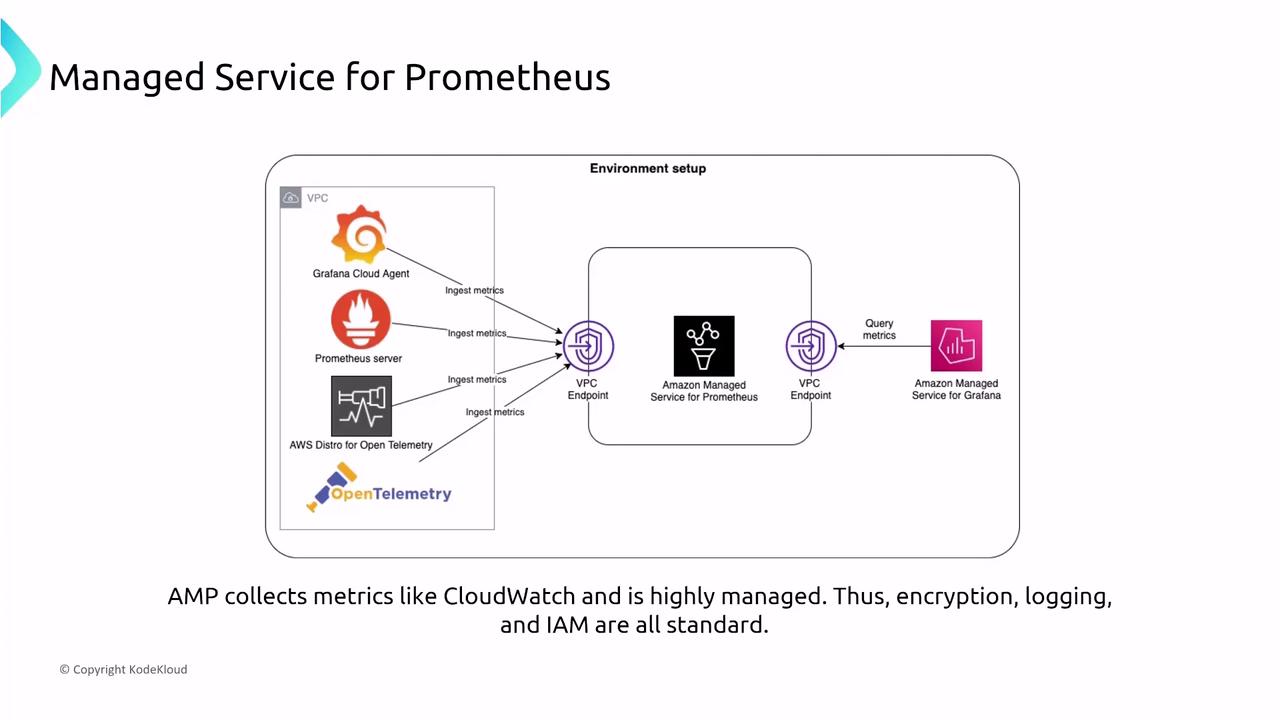
CloudTrail logs API calls made by Prometheus to ensure operational transparency and compliance.
Amazon Managed Grafana
Amazon Managed Grafana offers rich data visualization by integrating with multiple AWS services and data sources. Unlike other AWS services that depend on IAM for authorization, Managed Grafana uses Amazon Identity Center or third-party identity providers such as Okta. This model means that dashboard access is controlled externally from IAM policies, though AWS CloudTrail and CloudWatch still assist in auditing and monitoring access.
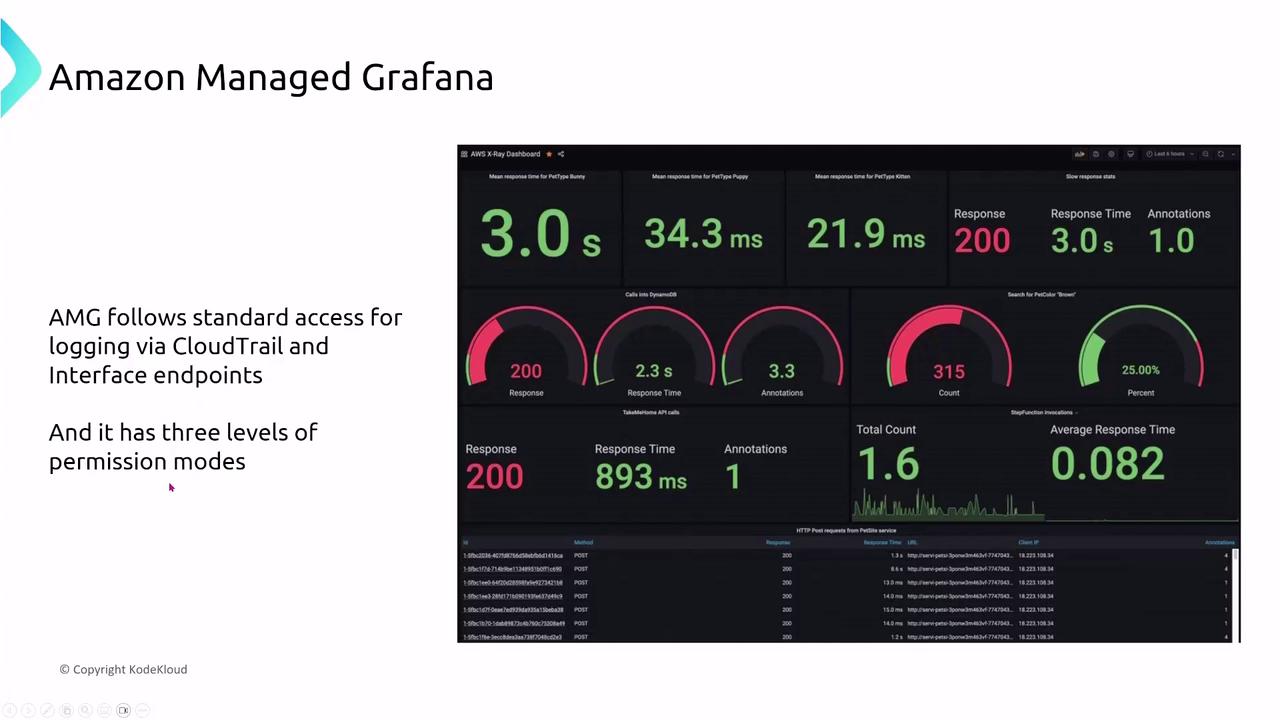
Managed Grafana supports multiple permission models, including service-managed and customer-managed permissions. For robust, fine-grained access control, customer-managed permissions are recommended.
Trusted Advisor, Launch Wizard, and Compute Optimizer
AWS Trusted Advisor
AWS Trusted Advisor offers proactive recommendations to help optimize cost, performance, fault tolerance, and security. For security-focused guidance, Trusted Advisor highlights issues like overly permissive IAM policies or the absence of multi-factor authentication. While it does not directly resolve these issues, it provides actionable insights that can help close security gaps.
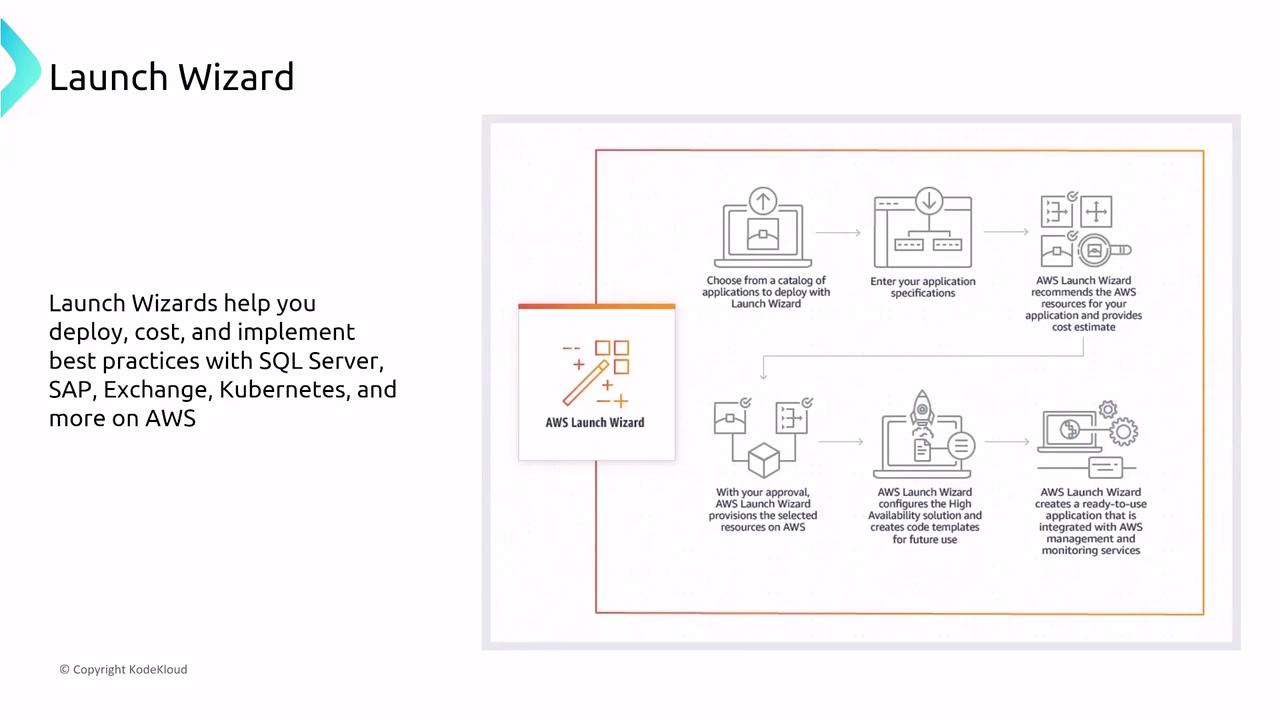
AWS Launch Wizard
AWS Launch Wizard guides you through the deployment of applications by providing a step-by-step setup for environments such as Kubernetes or SQL Server. When using Launch Wizard, verify that necessary IAM roles are either specified or created during the process, ensuring that deployments are performed securely.

AWS Compute Optimizer
AWS Compute Optimizer provides recommendations to optimize resource usage—including instance types and sizes—for both cost and performance improvements. Although Compute Optimizer carries minimal inherent security implications, proper IAM permissions are required for cross-account access via Trusted Access mode, which extends its recommendation capabilities.

Summary
In this lesson, we reviewed key elements to secure your AWS management services:
- Ensure proper IAM role management and safeguard sensitive data in CloudFormation templates.
- Use the AWS Cloud Development Kit (CDK) to embed security best practices directly into your code.
- Leverage observability tools like CloudWatch and X-Ray to monitor performance while enforcing data protection measures.
- Explore the security models of new services such as Amazon Managed Prometheus and Amazon Managed Grafana.
- Adopt AWS Trusted Advisor, Launch Wizard, and Compute Optimizer to gain actionable insights and optimize both security and efficiency.
Key Takeaway
By following these practices, you can design an AWS infrastructure that is secure, compliant, and resilient, ensuring that your cloud environment remains robust against potential threats.
Watch Video
Watch video content