AWS Solutions Architect Associate Certification
Designing for Security
Turning up Security on MigrationTransfer Services
Welcome Solutions Architects! In this article, we dive into the security measures for AWS migration and transfer services. Although these managed services require less extensive configuration compared to DIY solutions, proper security practices remain essential. This article provides an overview of key services including Migration Hub, Application Discovery, Application Migration Service, Database Migration Service (DMS), Elastic Disaster Recovery, Mainframe Modernization, Data Transfer Services, and the Snow Family, with a particular focus on ensuring robust security controls.
Migration Hub and Application Discovery
Migration Hub centralizes migration data from various tools and displays workflows from services such as application migration, Systems Manager, and database migration service. Its main concern is Identity and Access Management (IAM), so ensuring proper access controls is crucial due to the sensitive nature of migration data.
Security Best Practice
Only grant Migration Hub access to users who truly need it. While Migration Hub aggregates workflows, the underlying services are already highly secure.
Although Migration Hub displays workflows from different services, it provides minimal added security beyond what the source services already implement. For logging and monitoring, AWS CloudTrail tracks API calls, while CloudWatch is used sparingly for output display.
Application Discovery Service
The Application Discovery Service (ADS) collects metadata from your on-premises servers via agents, agentless methods, or vCenter outputs, and transfers the data securely to AWS. This service is focused on discovery rather than migration. Agents installed on your servers gather details about running applications and send them securely for analysis.
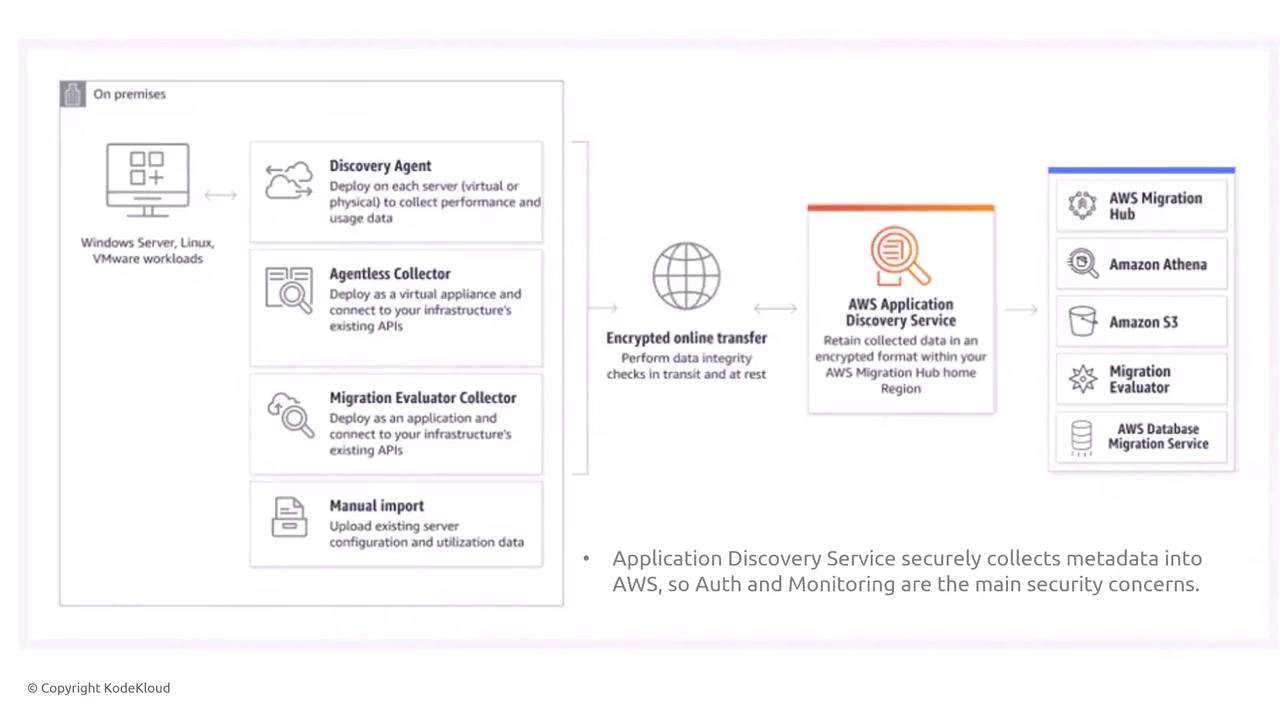
For large enterprises, understanding the functionality of these agents is essential. ADS manages access through IAM roles and policies, and logging via CloudTrail ensures that all API calls are recorded.
IAM integration within ADS enforces strict roles and policies. Enhanced logging using CloudTrail (and optionally CloudWatch) provides a comprehensive audit trail.
Application Migration and Database Migration Service (DMS)
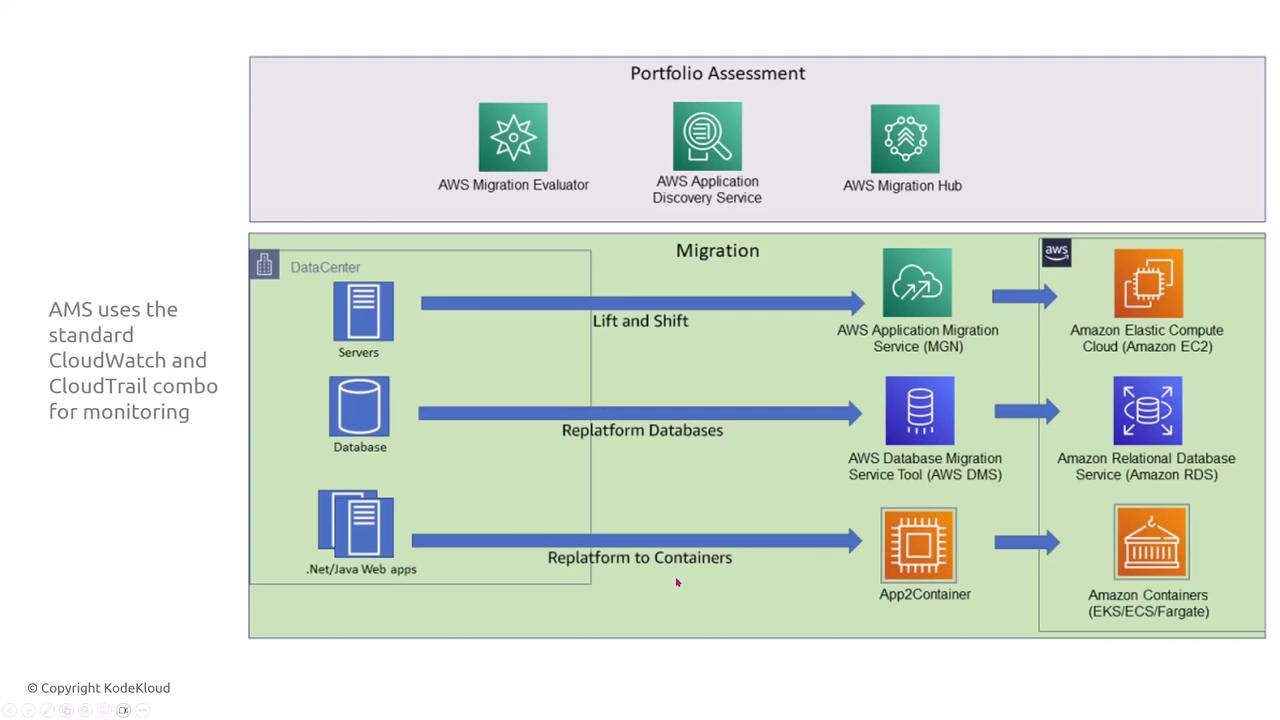
Application Migration Service (AMS)
The Application Migration Service (AMS) replicates and transitions your entire environment to AWS. Replace the retired Server Migration Service with Elastic Disaster Recovery. AMS installs an agent on your source environment, replicates the setup to AWS, and then conducts a cutover. It utilizes IAM for permission management and integrates with CloudWatch and CloudTrail for real-time logging.
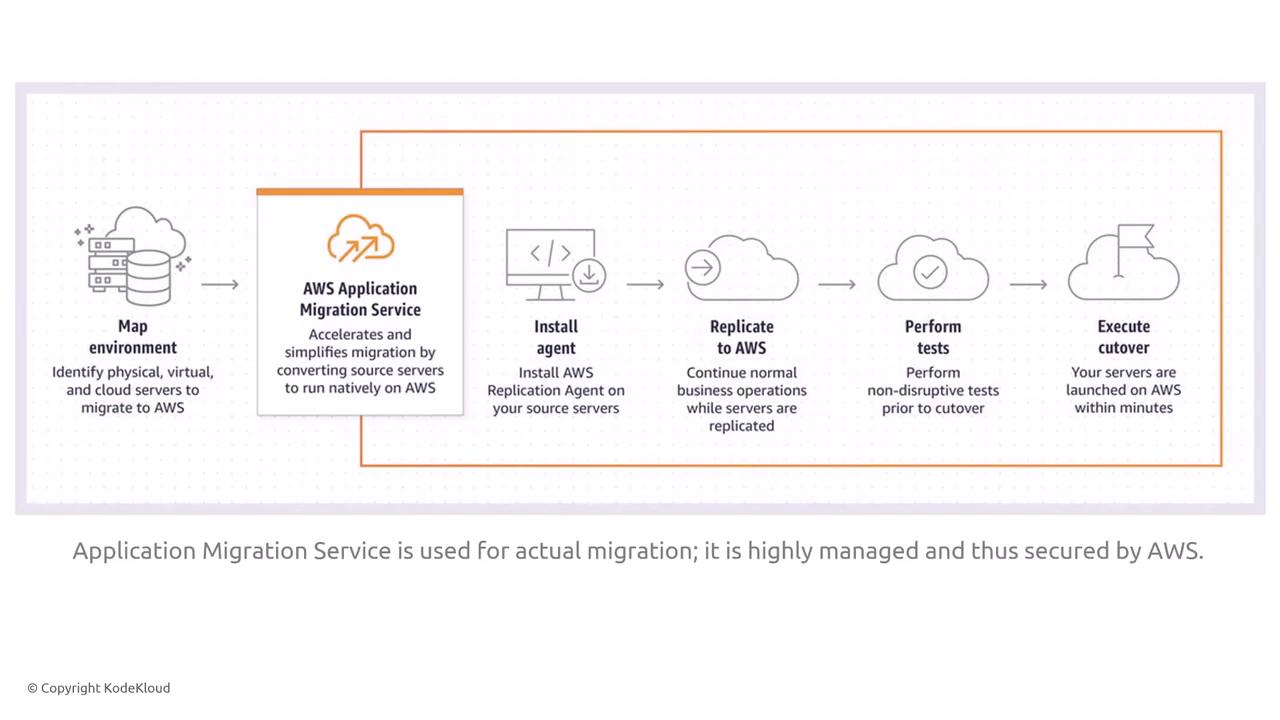
AMS supports both lift-and-shift and replatforming scenarios (for databases or containers) while logging all actions through CloudWatch logs in real time.
Database Migration Service (DMS)
DMS is designed for migrating large, sensitive database workloads. The security profile of the migration depends largely on the target destination. For example, using an encrypted Aurora cluster or an S3 bucket with server-side encryption ensures that the data remains secure.
Key DMS features include:
• Support for full copy loads and continuous data replication via change data capture (CDC)
• Comprehensive logging, capturing all DML commands and operations, with time travel logs to review historical changes
Consider the SQL command below, which reveals the structure of a migrated table:
MySQL [dmstarget]> SHOW CREATE TABLE product;
+---------+-------------------------------------------------+
| Table | Create Table |
+---------+-------------------------------------------------+
| product | CREATE TABLE `product` ( |
| | `product_id` bigint NOT NULL, |
| | `product_code` varchar(20) CHARACTER SET utf16 COLLATE utf16_general_ci NOT NULL, |
| | `product_name` varchar(50) CHARACTER SET utf16 COLLATE utf16_general_ci DEFAULT NULL, |
| | `product_price` decimal(28,6) DEFAULT NULL, |
| | PRIMARY KEY (`product_id`, `product_code`) |
| | ) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci |
+---------+-------------------------------------------------+
1 row in set (0.00 sec)
Troubleshooting Tip
Enabling CDC is vital for synchronization between source and target databases. Detailed logs assist in resolving replication issues.

DMS supports encryption at rest, SSL/TLS for in-transit security, and full encryption of replication streams. Multiple log types (task logs and time travel logs) provide robust oversight during migration.
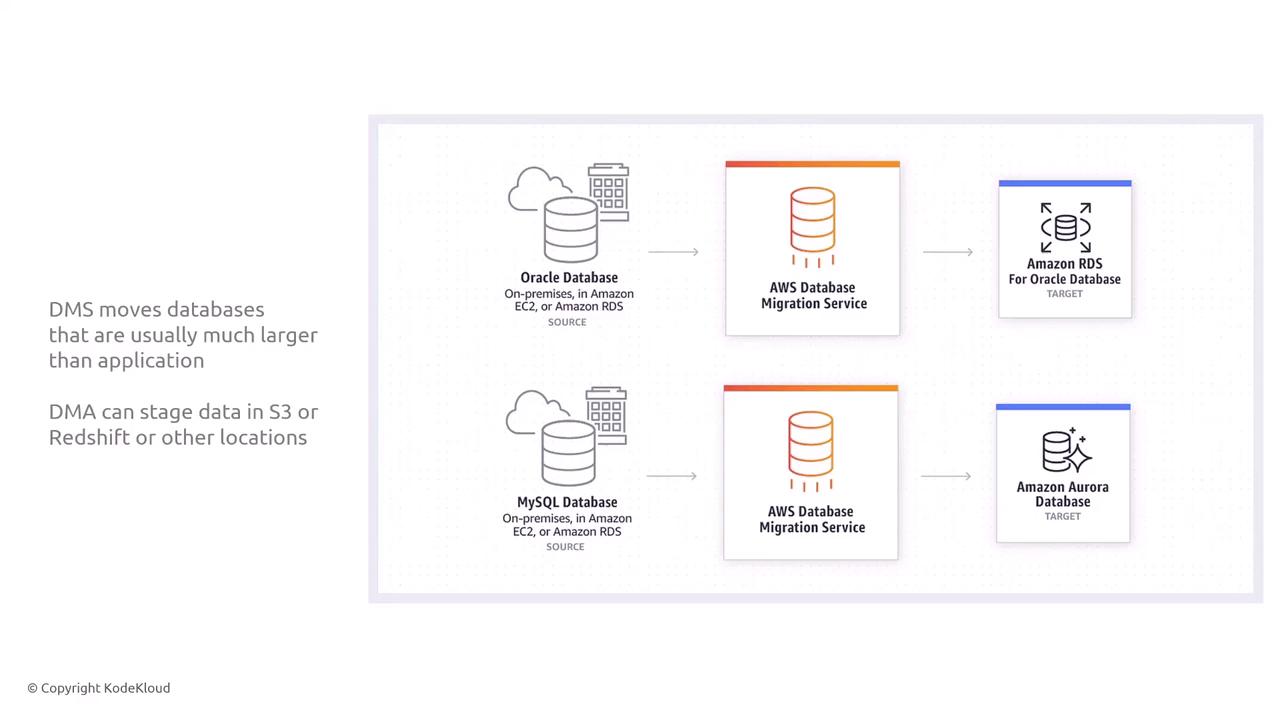
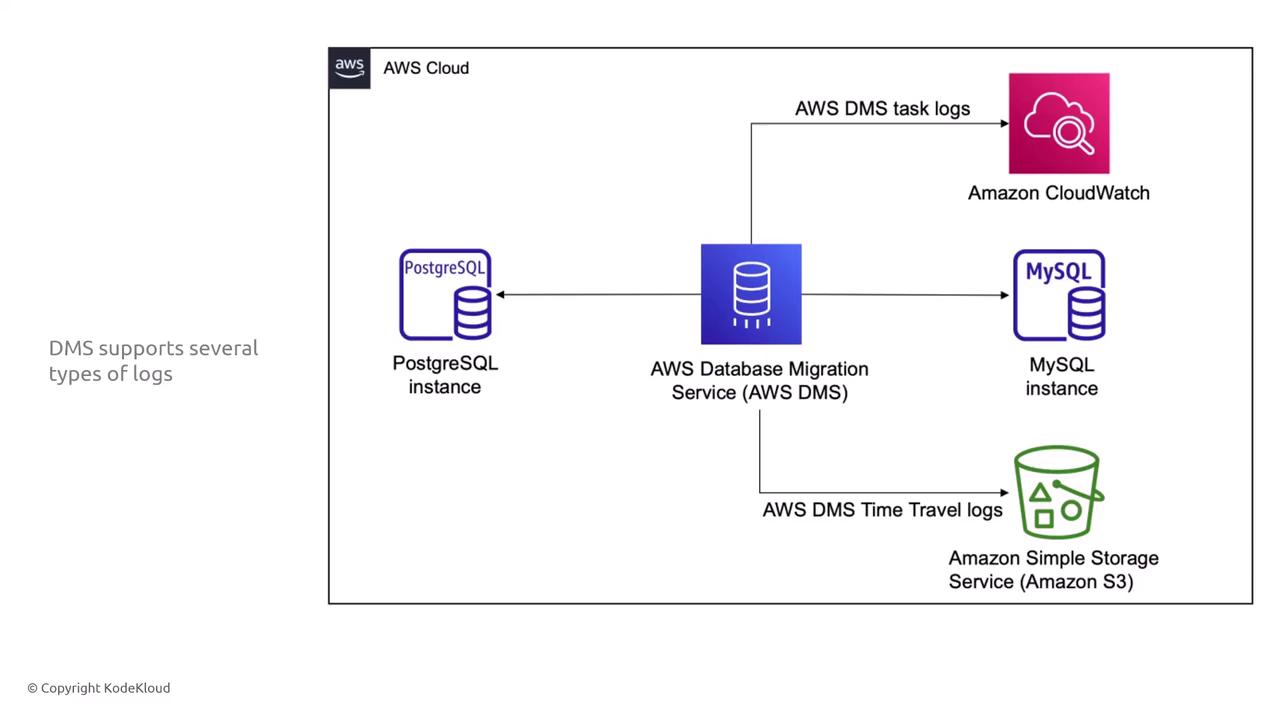

Furthermore, DMS ensures continuous replication of incremental data changes while maintaining robust encryption and detailed change logs.

Elastic Disaster Recovery Service
The Elastic Disaster Recovery Service replicates entire suites of virtual machines using block-level replication. It transfers data securely from a source to a target, inheriting encryption settings from the source instance. Network security is maintained by applying security groups during the transfer.
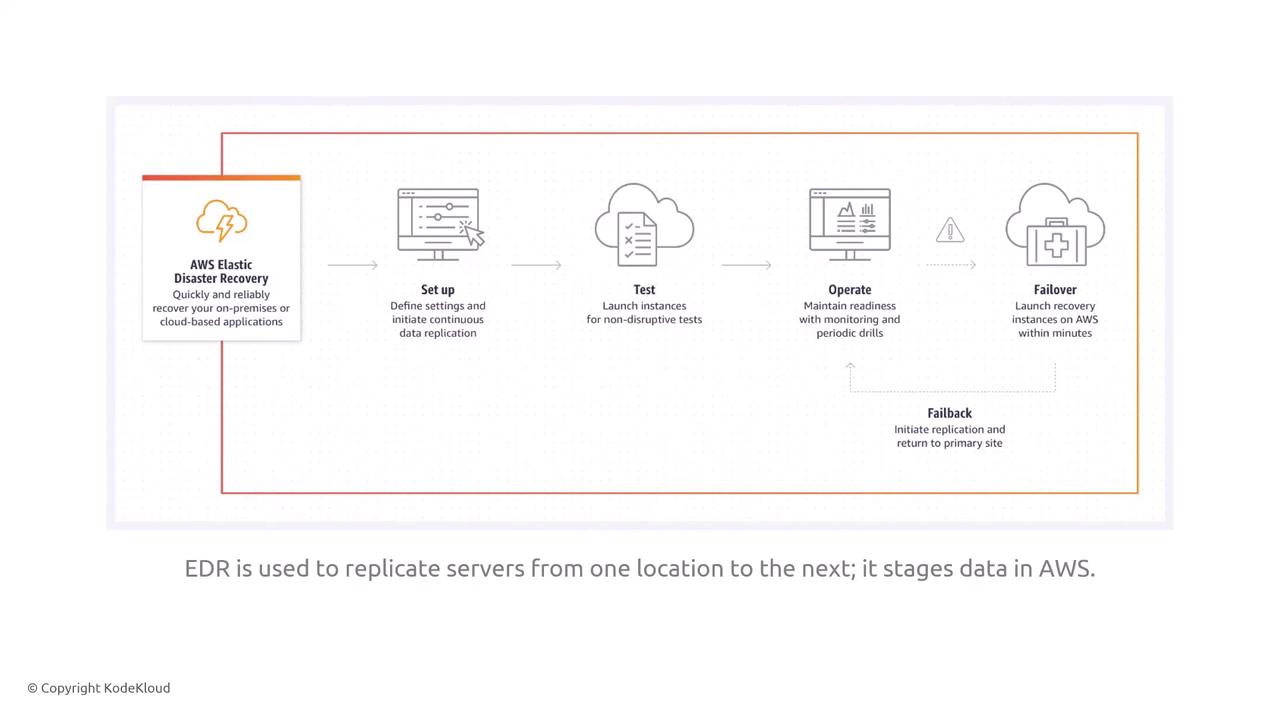
Replication agents extract data from disks, stage it on replication servers, and transfer it at a low level to recovery instances, preserving the configuration and security settings.
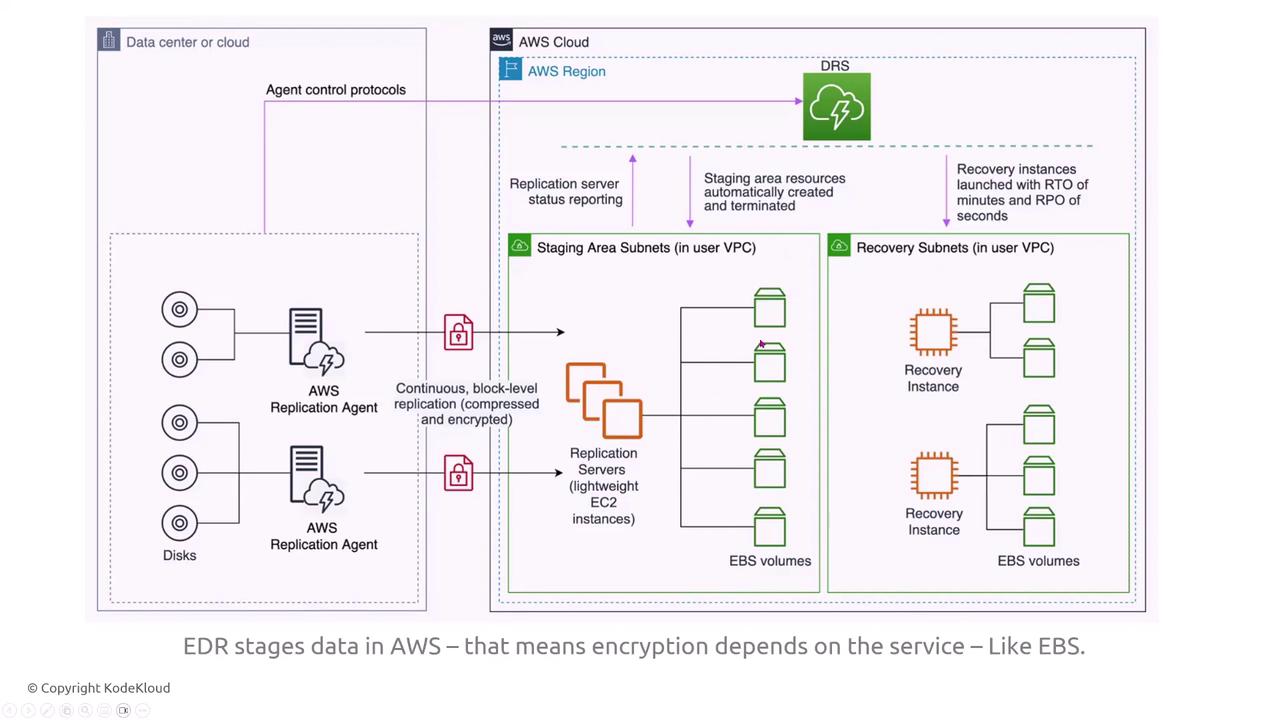
Encryption settings on the source are automatically applied to target EBS volumes. Network access continues to be enforced with security groups during the replication process.
Mainframe Modernization
Mainframe Modernization involves analyzing, refactoring, and replatforming legacy mainframe processes into an automated DevOps pipeline. Security best practices include implementing strong access policies, ensuring encryption at rest and in transit, and following best practices from the underlying services used during modernization.

Additional measures, such as enforcing perfect forward secrecy through TLS protocols with appropriate cipher suites, may be required in certain environments.
Data Transfer Services
AWS DataSync
AWS DataSync uses an on-premises agent to transfer storage data into AWS storage services such as S3, EFS, or FSx. As a serverless and managed service, DataSync leverages TLS to secure data in transit. However, when transferring data to an unencrypted S3 bucket, enable server-side encryption to maintain data security.
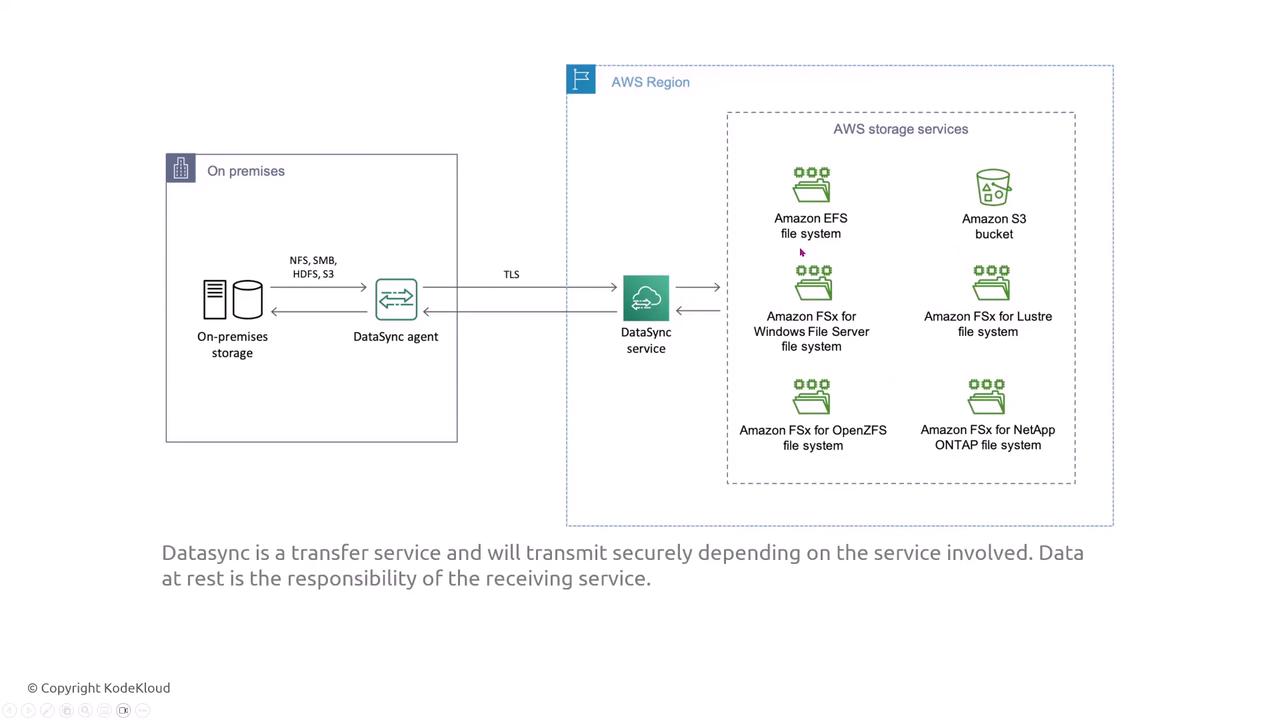
When transferring files from on-premises to EFS, DataSync can directly copy the data and logs can be monitored via CloudWatch.
AWS Transfer Family
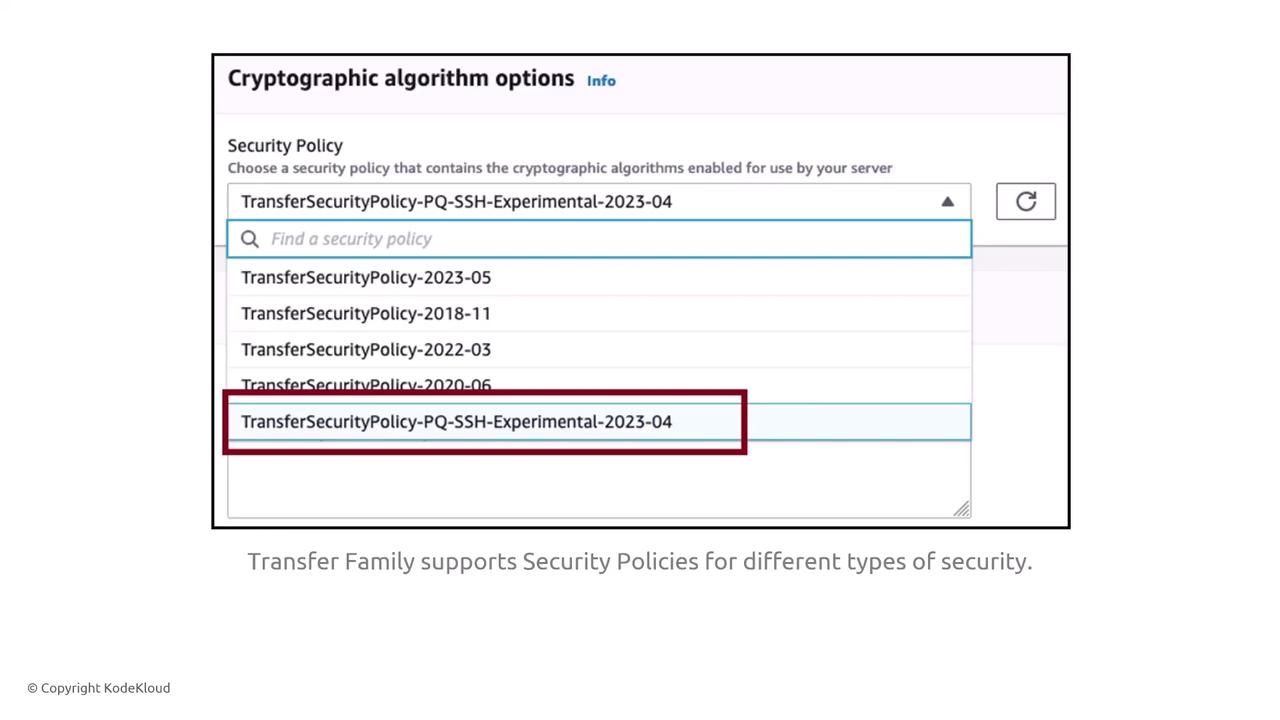
The AWS Transfer Family provides secure file transfers using protocols such as SFTP and FTPS, while excluding FTP due to its inherent security weaknesses. Custom security policies can be configured to meet specific organizational requirements. Exercise caution when setting cryptographic algorithm options; an overly strict policy might conflict with other security requirements.
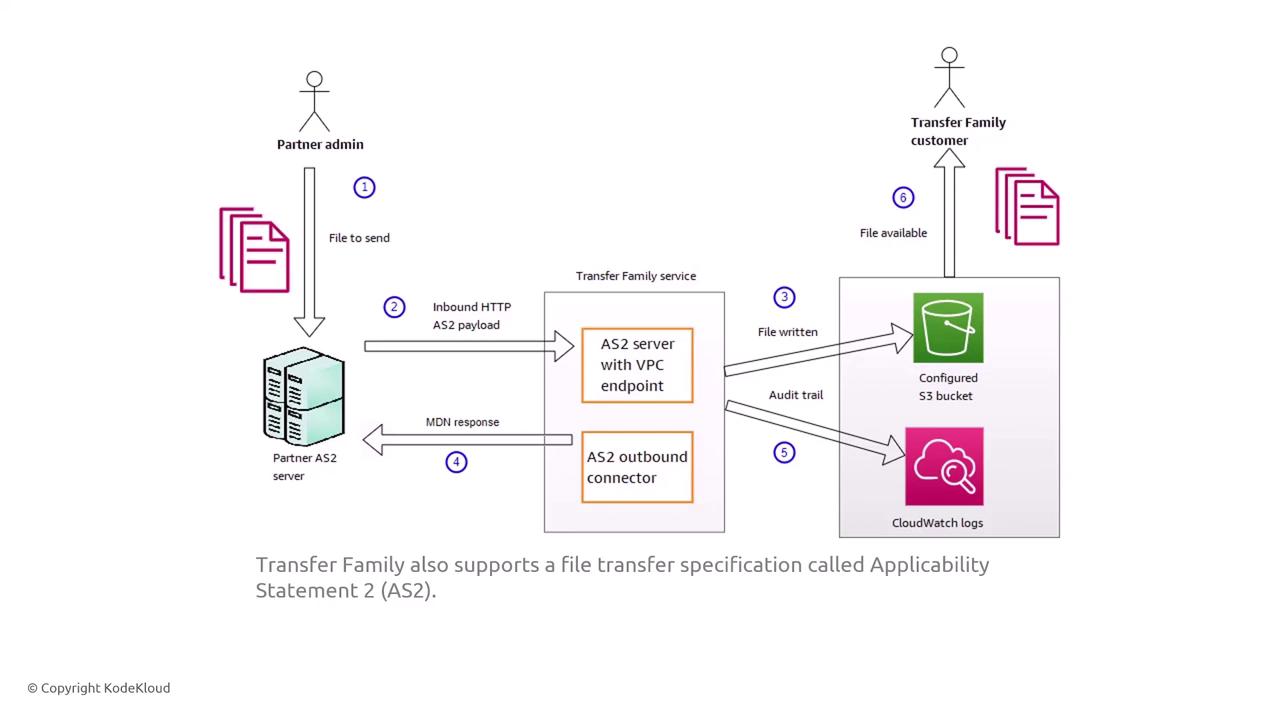
For legacy protocols like AS2, the AWS Transfer Family accepts the inbound HTTP payload, stores it in an S3 bucket, and creates an audit trail via CloudWatch.
Snow Family (Storage Perspective)
The Snow Family consists of rugged hardware devices designed for secure, local data transportation in harsh environments. The Snowball Edge, a key device in this family, utilizes AWS IAM for user access management. Data stored on these devices is automatically encrypted; in-transit encryption is also enforced.
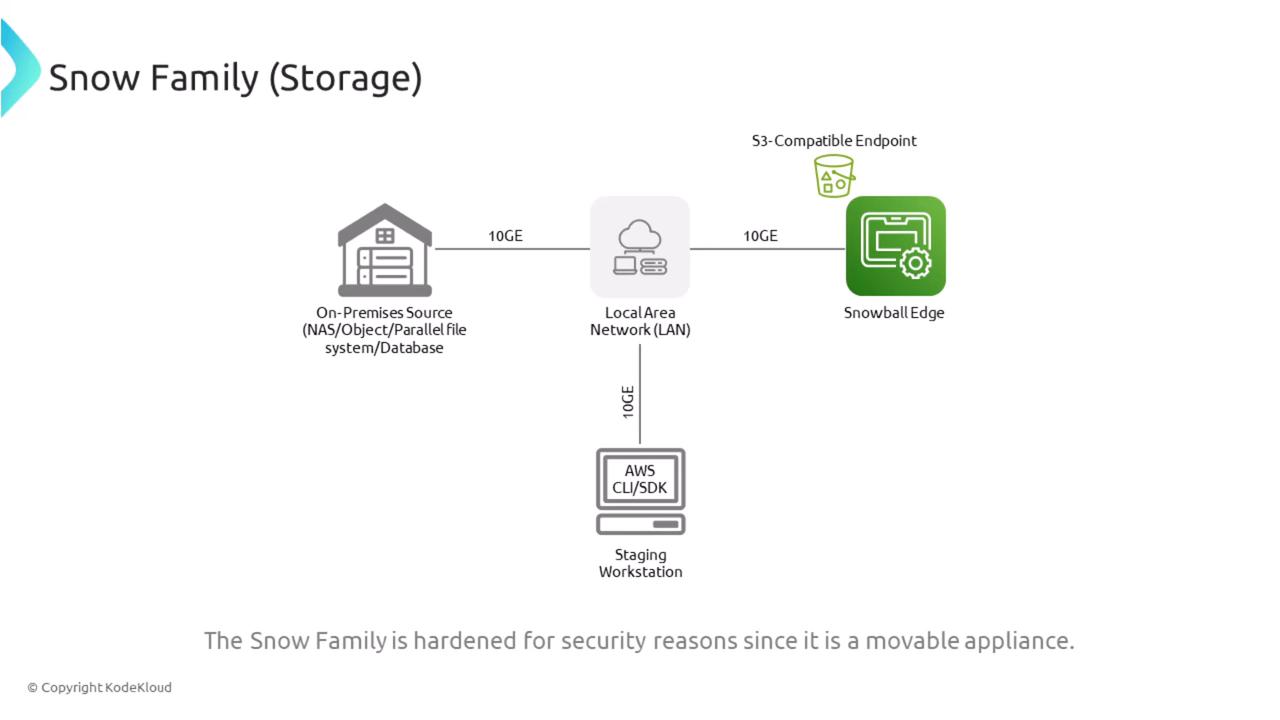
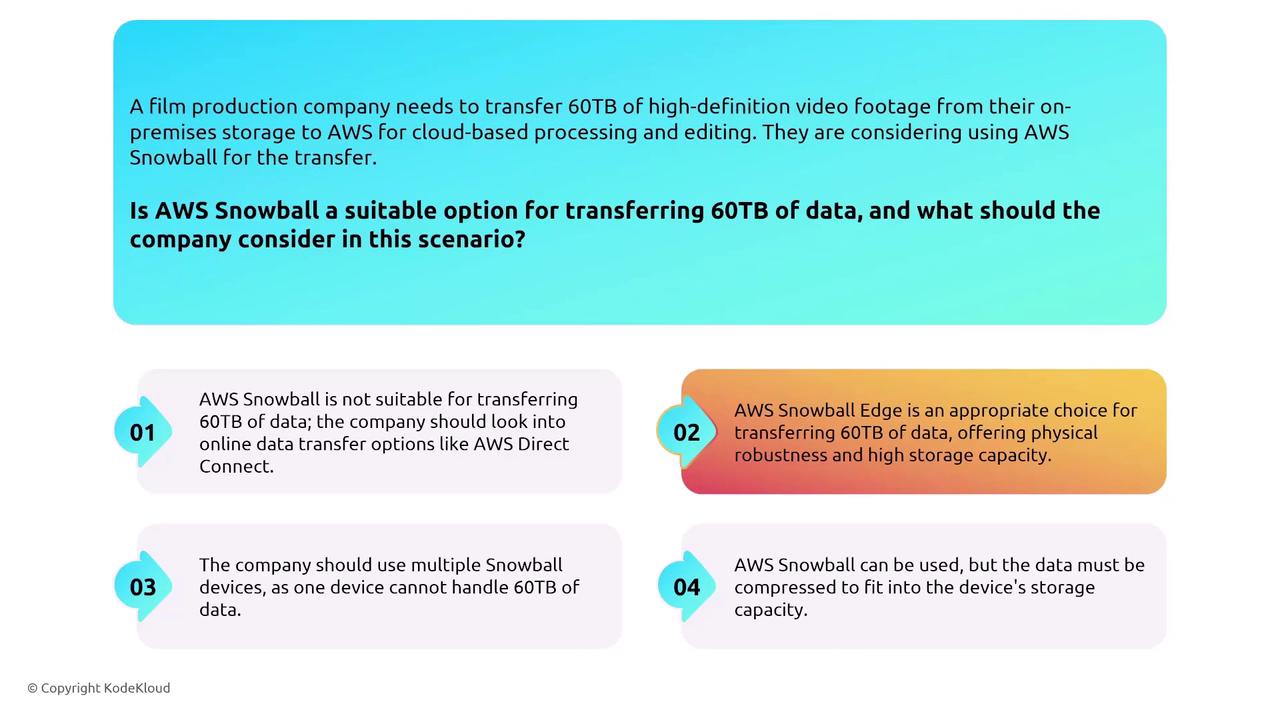
For large-scale data transfers (for example, transferring 60 terabytes), the Snowball Edge is a suitable solution. With support for up to 72 terabytes of usable transfer data, it emphasizes encryption and network controls alongside varying capacity and processing capabilities.
Summary
This article highlighted the key security considerations across AWS migration and transfer services. Below is a summary of the essential security themes:
| Security Theme | Description |
|---|---|
| IAM Controls & Access Policies | Strictly manage who can access these services with granular IAM roles. |
| Encryption (At Rest & In Transit) | Ensure continuous encryption for data stored or transmitted. |
| Comprehensive Logging | Use AWS CloudTrail and CloudWatch for complete audit trails and issue diagnosis. |
| Managed Services | Leverage AWS managed services that simplify security configurations. |
In summary, migration and transfer services in AWS—from Migration Hub and Application Discovery to AMS, DMS, Elastic Disaster Recovery, Mainframe Modernization, DataSync, Transfer Family, and the Snow Family—are designed with strong security features. Nevertheless, maintaining high awareness regarding configuration, encryption, logging, and access control is paramount to safeguard your data during migration.
Thank you for reading, and we look forward to seeing you in the next study session.
Watch Video
Watch video content