AWS Solutions Architect Associate Certification
Designing for Security
Turning up Security on Data Services Part 2
In this lesson, we review the security aspects of several AWS data and machine learning services. We cover visualization tools, data warehousing solutions, and inference services, along with natural language processing, transcription, and translation. Each section describes the security features of the service, the encryption methods used, and complements the discussion with relevant diagrams.
Amazon QuickSight
Amazon QuickSight is a visualization tool that lets you build dashboards by pulling data from sources such as Lake Formation, Athena, and the AWS Glue Data Catalog. As a fully managed service, QuickSight natively encrypts data both at rest and in transit. This encryption covers stored data, temporary storage within its SPICE engine, and all data movement. In addition, QuickSight integrates with CloudWatch for monitoring execution flows and metrics without requiring extra configuration.
Amazon Redshift and Data Warehousing
Amazon Redshift is an SQL-based data warehousing solution that offers performance insights with automatic logging. Its tight integration with IAM and encryption mechanisms makes it a secure choice for managing large volumes of data. For more detailed aspects of its security features, refer to the dedicated sections later in this lesson.
Amazon SageMaker
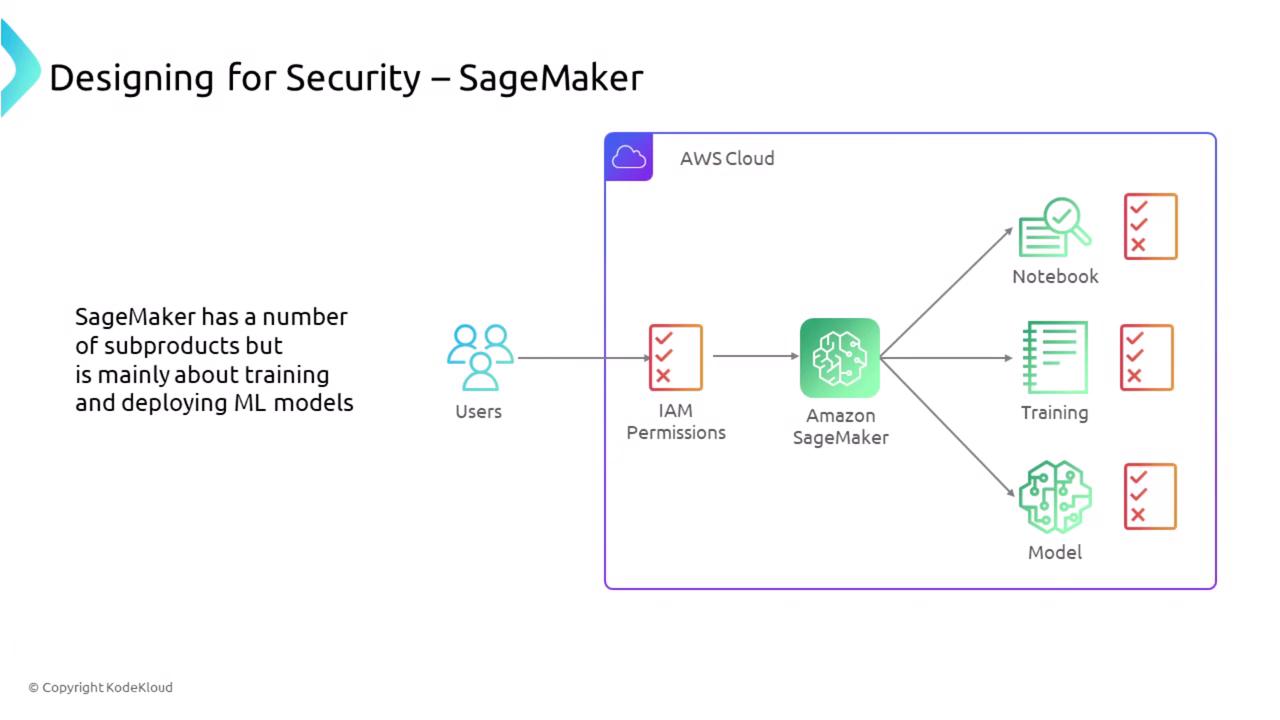
Amazon SageMaker provides a platform for building, training, and deploying machine learning models. Its security features are designed to protect sensitive data during the entire machine learning lifecycle. Key aspects include:
- Notebooks and Studio: SageMaker Notebooks (essentially EC2 instances running Jupyter) automatically encrypt data at rest and in transit.
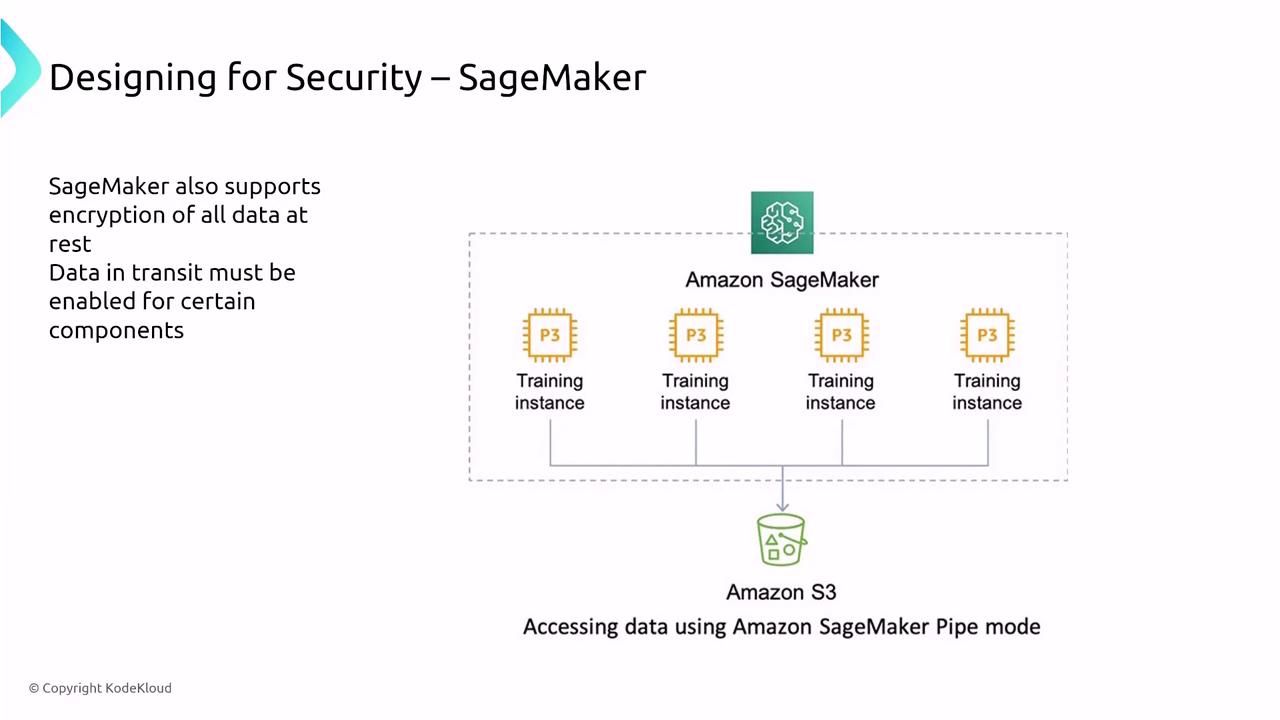
- Training Jobs: Enable inner-container traffic encryption during training by specifying the appropriate encryption parameter in the API.
- VPC Access and Storage Encryption: Deploy SageMaker within a VPC to restrict public Internet access, and enforce storage encryption using custom keys.
For secure configurations, ensure that:
- Inner container traffic encryption is set to true.
- SageMaker is deployed in a VPC to isolate instances from the Internet using security groups and specific VPC endpoints.
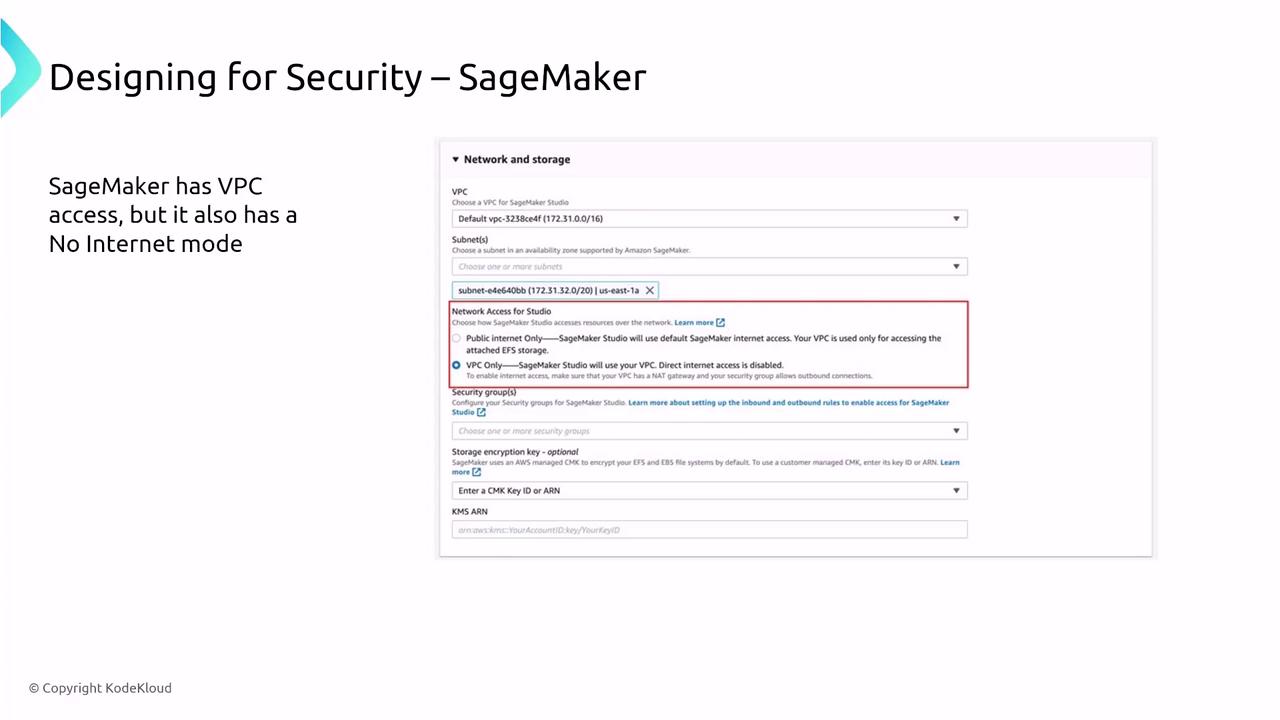
Monitoring SageMaker is integrated with CloudWatch for logging and metrics, and AWS CloudTrail provides comprehensive auditing.
Amazon Rekognition
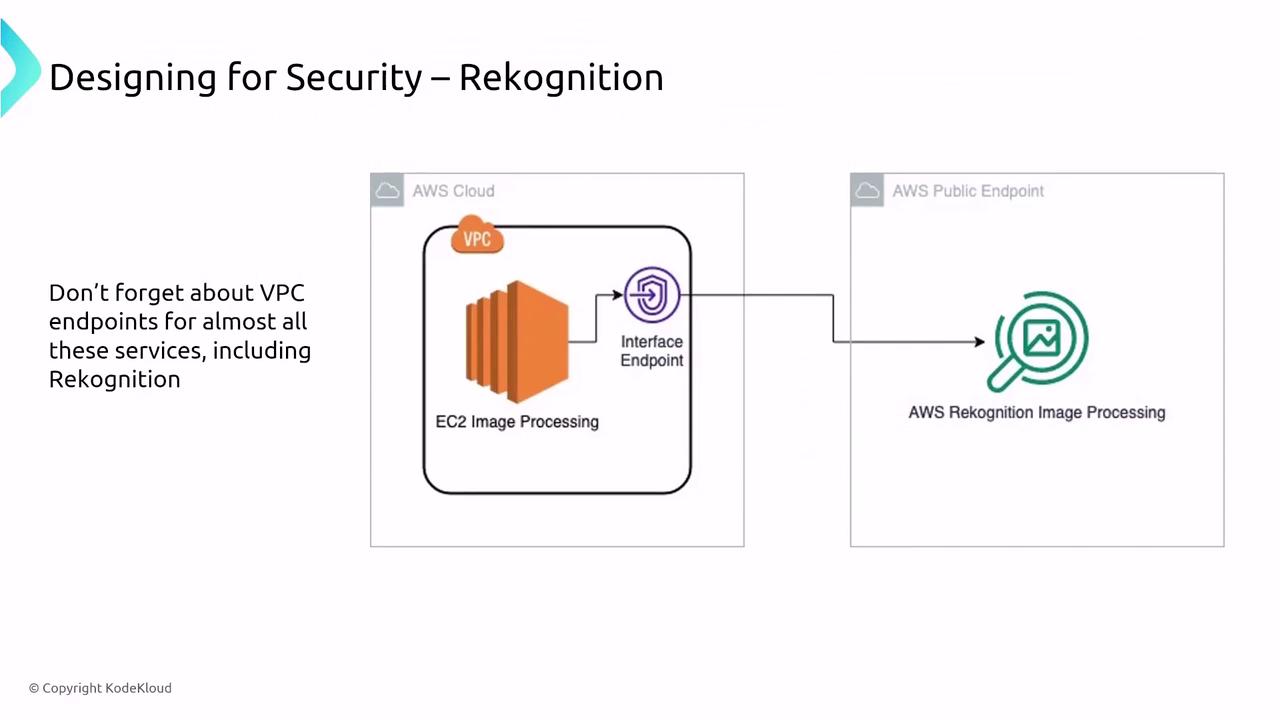
Amazon Rekognition analyzes and recognizes objects within images. This service encrypts input media and associated metadata by default. For additional security, client-side encryption is supported, though the data must be decrypted prior to processing. To maintain secure access, deploy VPC interface endpoints (PrivateLink).
Amazon Polly
Amazon Polly converts text to lifelike speech. As a managed service, its security largely relies on the backing storage used for audio outputs (usually Amazon S3). When evaluating Polly’s security, it is important to consider the encryption settings and access policies configured on S3, as well as logging through CloudWatch.
Amazon Lex
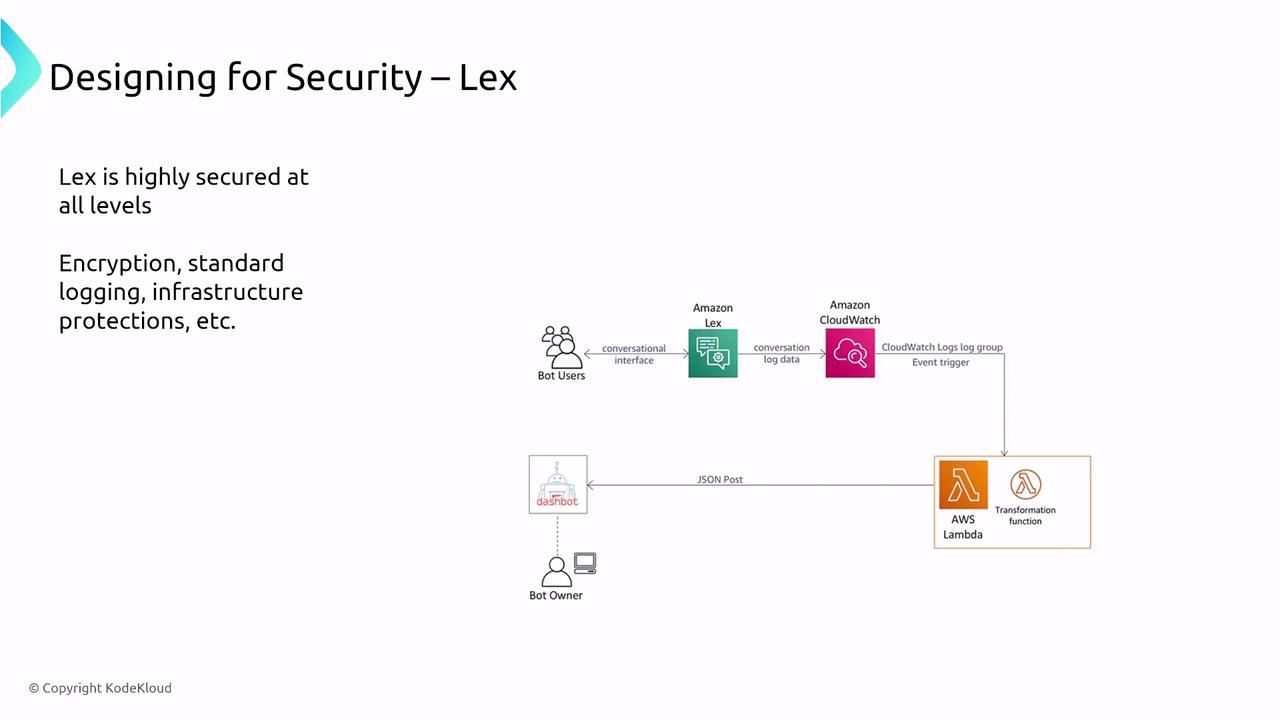
Amazon Lex, which powers conversational chatbots, combines automatic speech recognition (ASR) with natural language understanding (NLU) to convert speech to text and analyze intent. It encrypts data by default and uses IAM for fine-grained access control. Lex can also be accessed securely by leveraging VPC interface endpoints.
Note
When securing Lex interactions, be sure to employ PrivateLink to privatize traffic as needed.
Amazon Comprehend
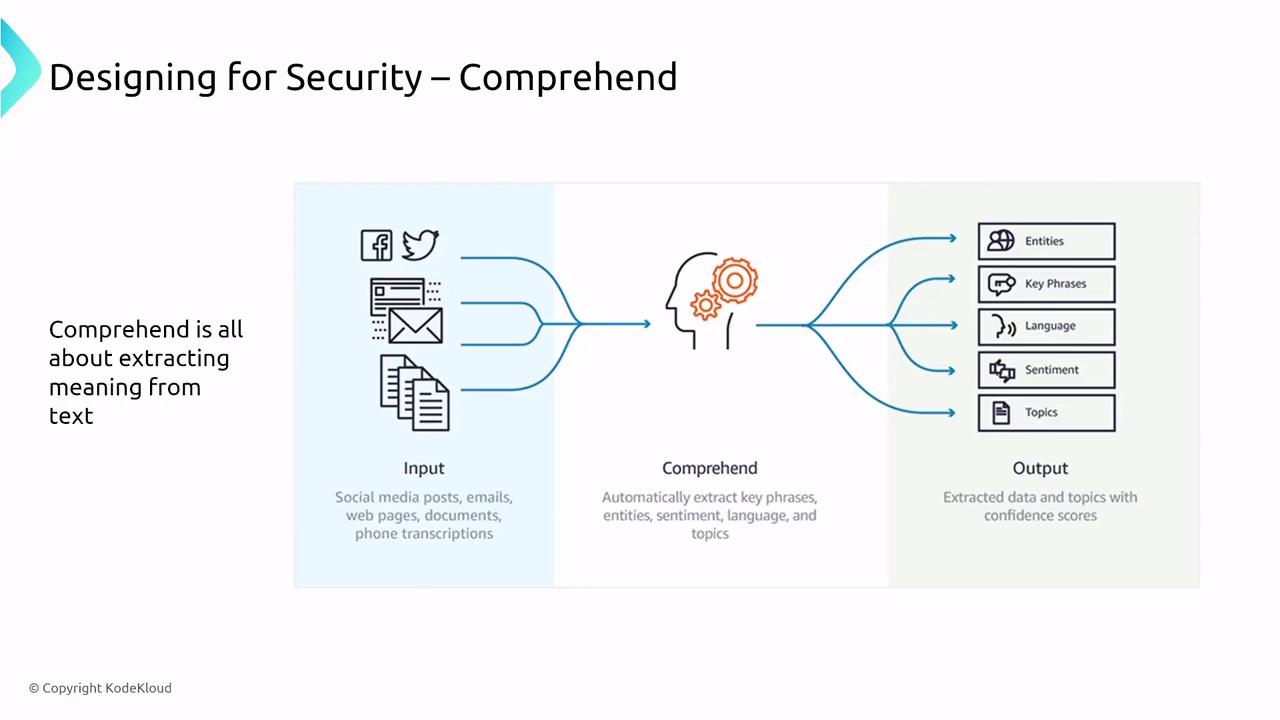
Amazon Comprehend is a natural language processing service that extracts key insights such as entities, key phrases, language, sentiment, and topics from text. Fully managed and leveraging pre-trained machine learning models, Comprehend simplifies NLP tasks. Users can enable encryption for both input data and outputs using AWS KMS.
Amazon Forecast
Amazon Forecast builds time-series forecasting models using historical data. While it remains a newer addition to AWS’s machine learning portfolio, its security practices align with standard AWS services: data at rest is encrypted (with options for user-managed keys) and access is controlled by IAM. Logging support is available via CloudTrail and CloudWatch.
Augmented AI (A2I)
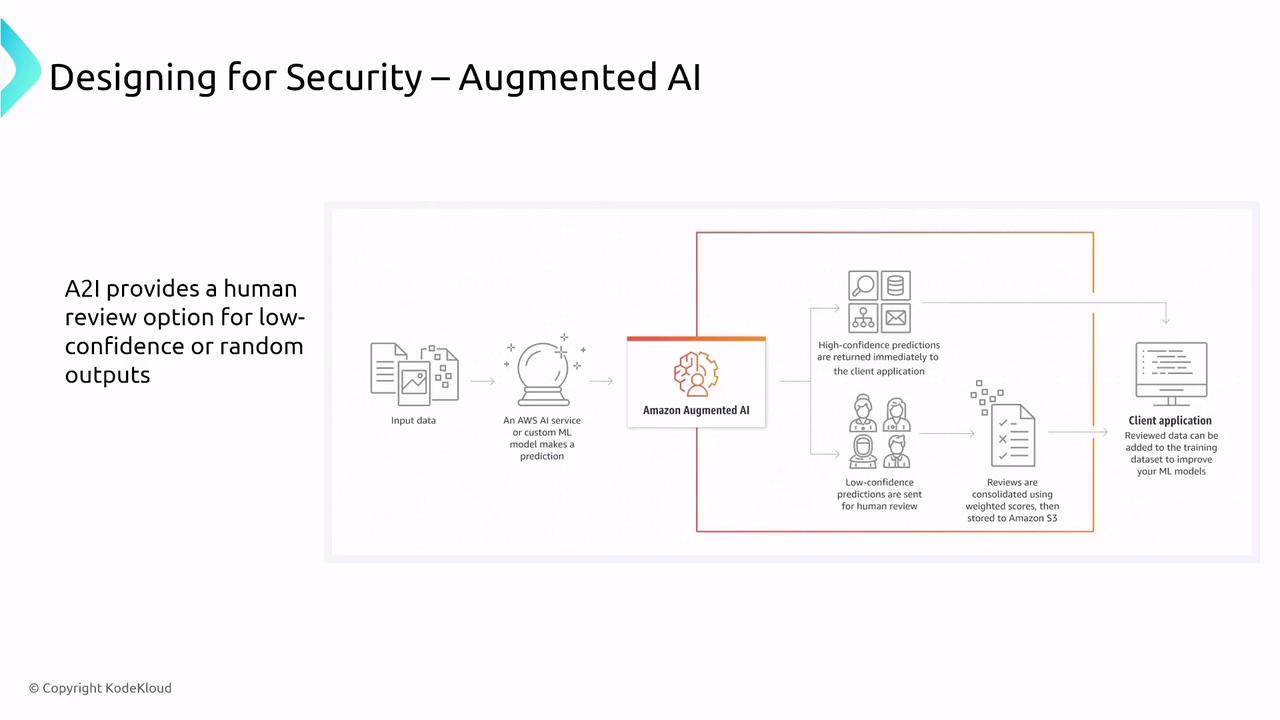
Amazon Augmented AI (A2I) adds a human review step to machine learning predictions when confidence is low. This helps improve the accuracy of results by integrating human verification via internal teams or AWS Mechanical Turk. Key security considerations include protecting submitted data and review processes with IAM policies and KMS encryption.
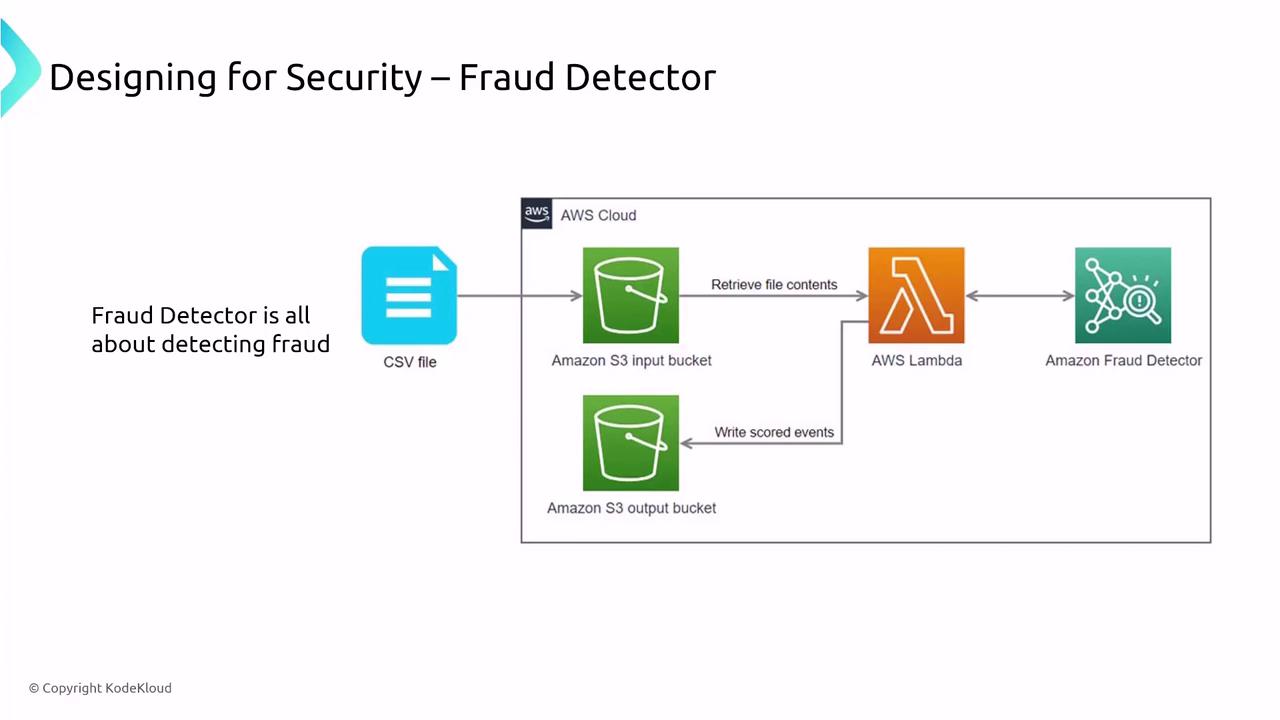
Amazon Fraud Detector
Amazon Fraud Detector identifies anomalous and potentially fraudulent activities within transactions. It integrates with IAM for secure access management and leverages AWS KMS for encryption of data at rest. Additionally, the service supports comprehensive logging and monitoring through CloudTrail and CloudWatch.
Transcription and Translation Services
Amazon Transcribe
Amazon Transcribe securely converts audio and video content into text. It encrypts data automatically in transit and at rest while also supporting customer-managed keys. Its security framework ensures that media files remain protected throughout the transcription process.
Amazon Translate
Amazon Translate provides language translation services with strong security measures. It encrypts data in transit using TLS and secures information at rest (typically using AES-256). Moreover, Amazon Translate complies with industry standards such as ISO 27001, PCI DSS, and HIPAA.
Amazon Textract
Amazon Textract extracts text and structured data from scanned documents while ensuring robust security. It leverages server-side encryption for data stored in S3 and relies on IAM for authenticated access and user management.
Note
Remember that ensuring the security of outputs from Textract also depends on the configurations of connected services such as the S3 buckets storing the document data.
Summary
This lesson covered the security features of an array of AWS data and machine learning services—from data ingestion and visualization to inference and transcription. Key themes include:
- Default encryption both at rest and in transit.
- Use of AWS KMS for customer-managed encryption.
- Robust access controls using AWS IAM.
- Monitoring and logging through AWS CloudWatch and CloudTrail.
While most of these services are designed to be highly secure by default, it remains essential for architects to apply additional settings—like inner container encryption in SageMaker or restricted access via VPC endpoints—to align with specific security requirements.
Thank you for following this lesson on AWS security considerations. In the next section, we will explore additional security topics and best practices.
For further reading, consider these resources:
- AWS Security Documentation
- Amazon Web Services – Compliance
- AWS Best Practices for Security, Identity, & Compliance
Watch Video
Watch video content
Practice Lab
Practice lab