Certificate Management and AWS Private Certificate Authority
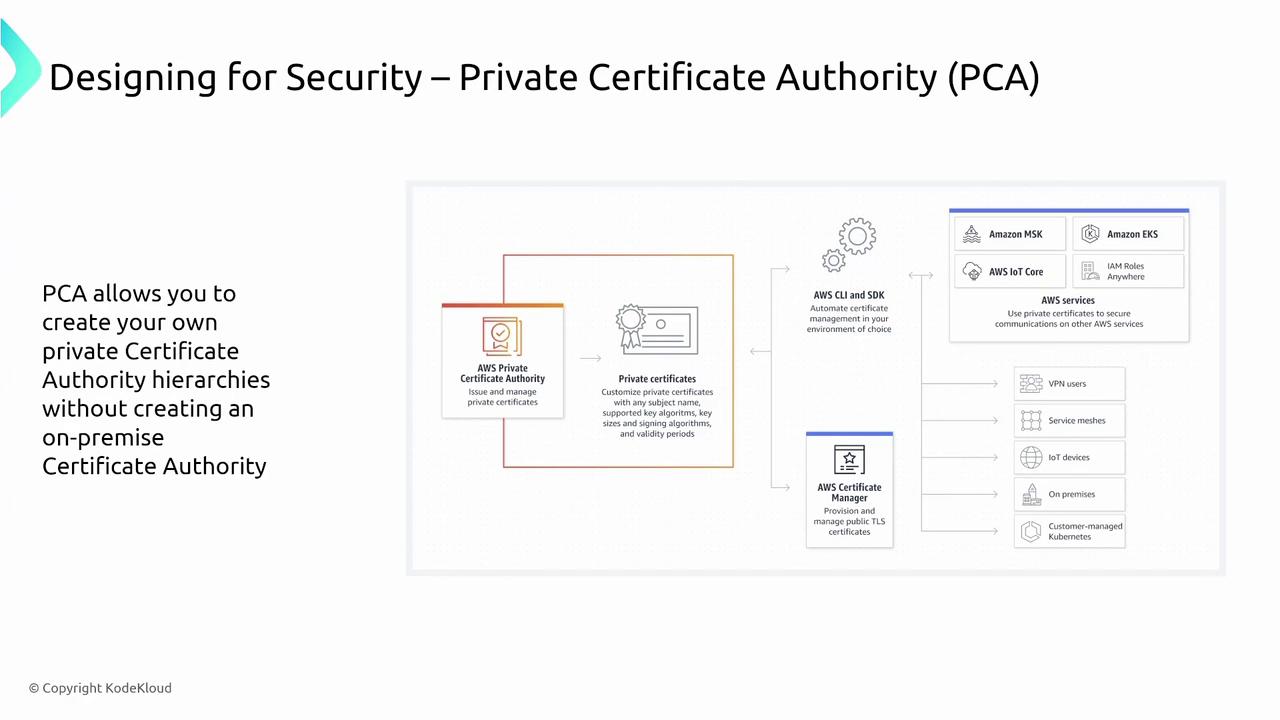
When protecting stored data, services like AWS Key Management Service (KMS) and AWS CloudHSM are commonly used. For data in transit, particularly with TLS/SSL certificates, AWS Certificate Manager (ACM) is the preferred choice. ACM not only manages public-private certificates but also supports importing certificates from external vendors. For certificates created within ACM, automatic renewal further simplifies the certificate lifecycle – a process similar to certificate management in Kubernetes. For organizations hosting websites where secure communications are critical, AWS Certificate Manager automatically provisions and renews certificates:
Secrets Management
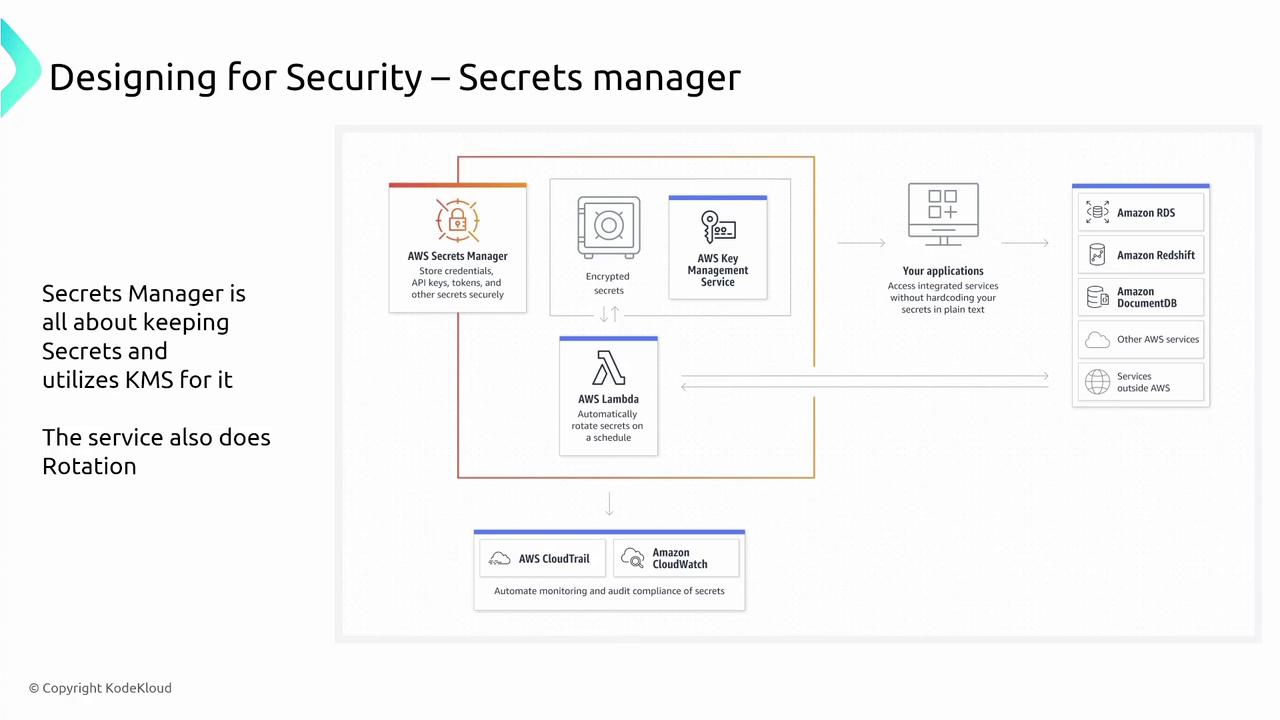
To securely manage credentials, API keys, and tokens, AWS Secrets Manager is the recommended service. It encrypts sensitive data and enforces access through appropriate IAM permissions. A standout feature of Secrets Manager is its automated credential rotation which is not available in the Systems Manager Parameter Store (which does offer secure strings but lacks auto-rotation).If automated credential rotation is a priority for your application, AWS Secrets Manager should be your go-to solution.
Network-Level Security: Security Groups and NACLs
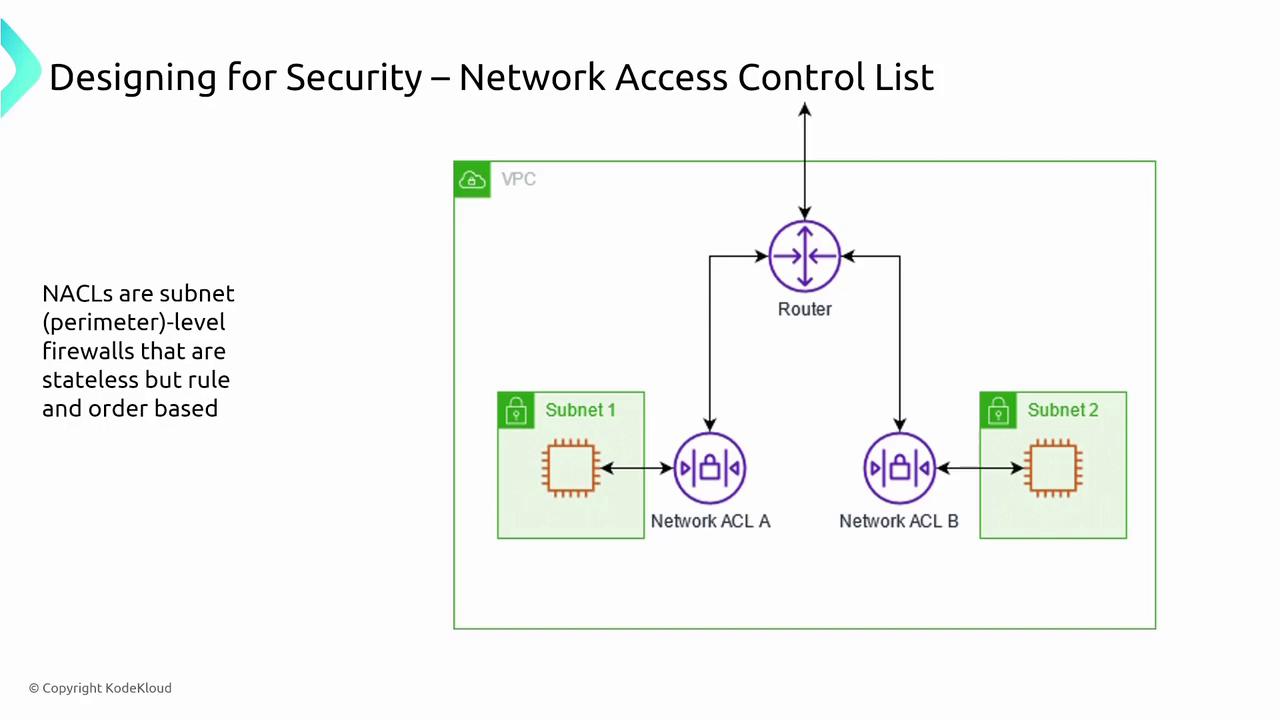
Within the AWS network, security groups and network access control lists (NACLs) act as built-in firewalls. Security groups provide stateful security at the network interface level by filtering both inbound and outbound traffic: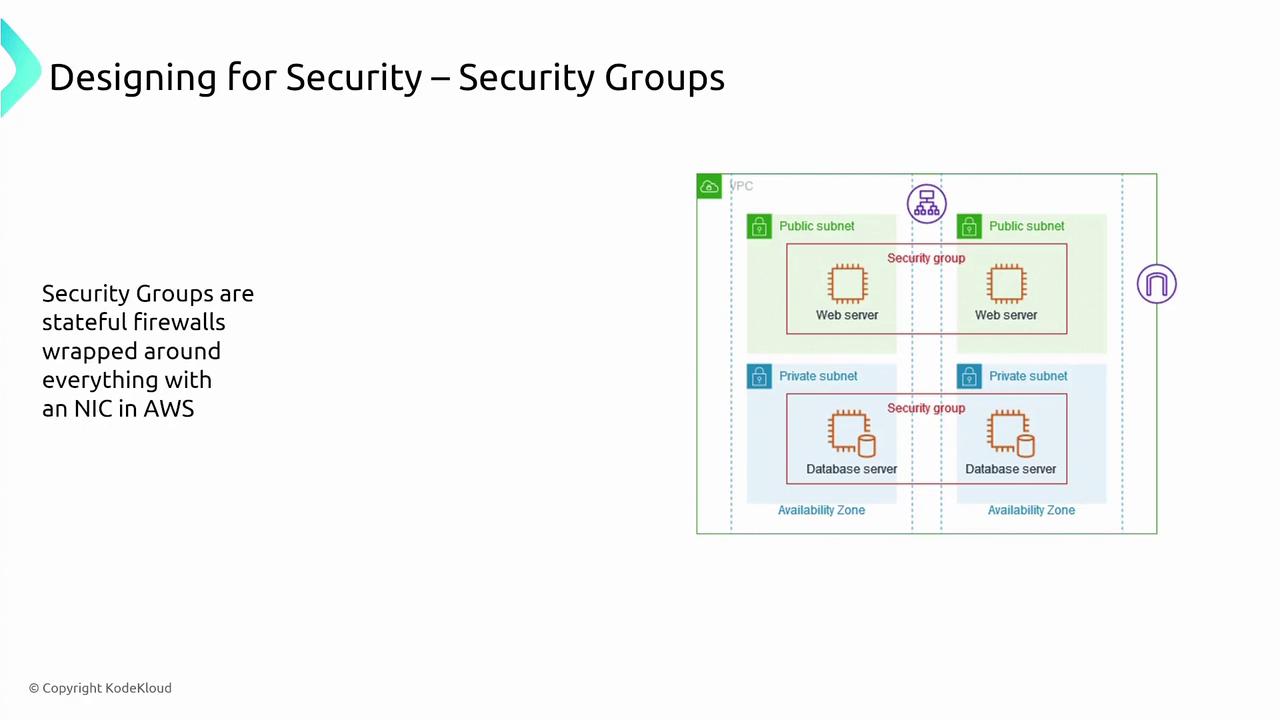
Centralizing Security Data with AWS Security Lake
AWS Security Lake serves as a centralized repository for collecting, normalizing, and analyzing security data from multiple AWS services. By aggregating information from services like IAM Access Analyzer, GuardDuty, Inspector, AWS Config, and CloudTrail, it enables advanced threat detection and continuous security monitoring.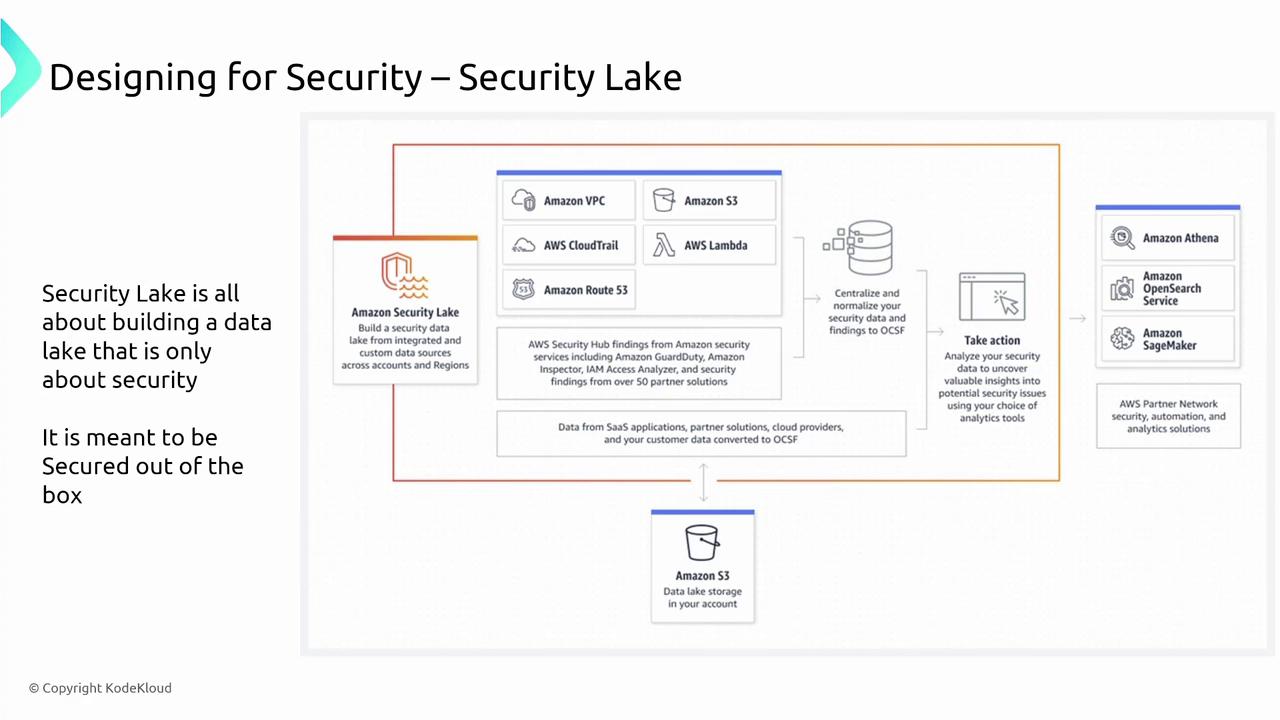
Web Application Firewall and DDoS Protection
AWS Web Application Firewall (WAF) protects your applications from common web exploits such as SQL injection and cross-site scripting. It integrates seamlessly with services like API Gateway and CloudFront, safeguarding your applications at the edge. Although WAF rules can be detailed, the AWS certification exam typically emphasizes its basic functionality. For DDoS attack protection, AWS Shield is available in both standard (free) and advanced (paid) versions. Shield Advanced offers enhanced integration with services like AWS Firewall Manager, providing deeper security controls: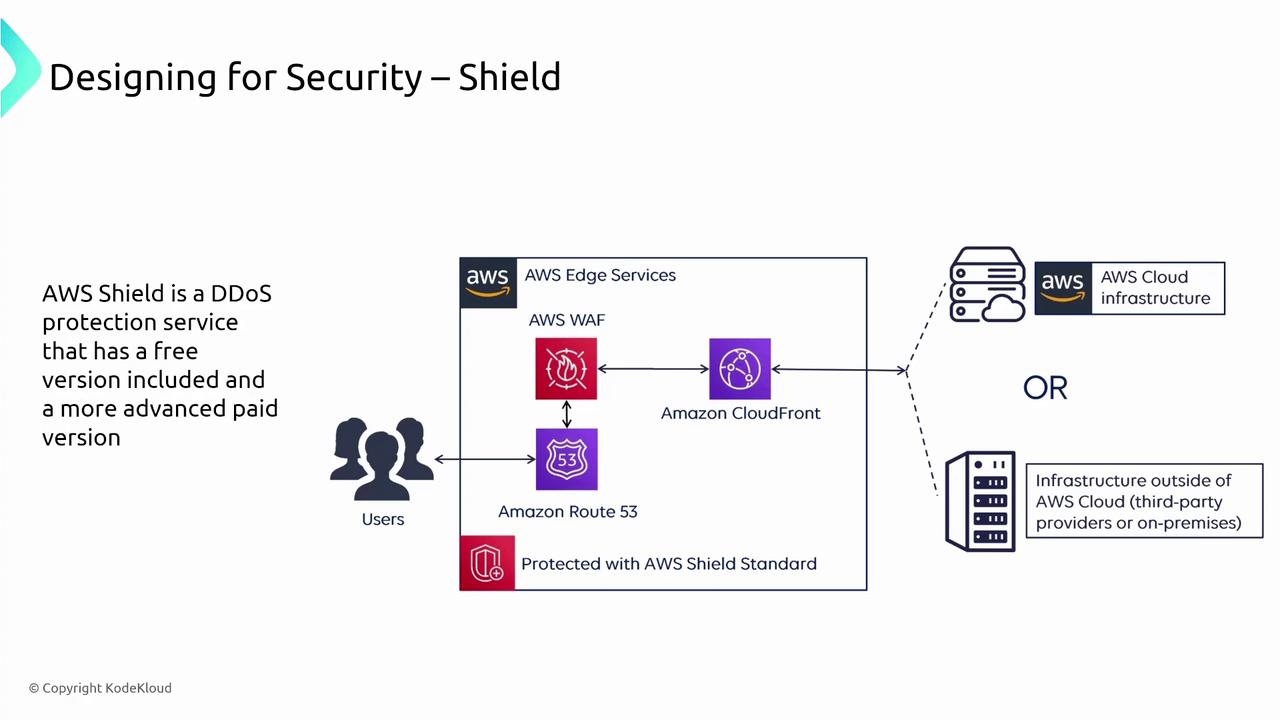
Combining Shield Advanced with WAF and using Firewall Manager enables real-time dynamic adjustment of firewall rules to combat sophisticated attacks.
Network Firewall and AWS Firewall Manager
AWS Network Firewall delivers traditional firewall capabilities at the VPC level. It includes features such as deep packet inspection, web filtering (including SNI filtering), and protocol detection, giving you granular control over inbound and outbound traffic:

Final Thoughts
In summary, we reviewed several AWS security services that are designed with robust security features enabled by default. Understanding how these services integrate—for instance, feeding logs into CloudWatch, recording API calls in CloudTrail, and tracking configuration changes with AWS Config—is essential for building a secure AWS environment. As you progress to topics like reliability, performance, and cost management, remember that many security services are optimized for ease of setup and operation. This foundational knowledge is a key step on your path toward AWS certification success.